The
threat
actors
behind
the
GOOTLOADER
malware
continues
to
improve
their
code
by
adding
new
components
and
implementing
new
obfuscation
techniques.
Mandiant
researchers
reported
that
the
UNC2565
group
behind
the
GOOTLOADER
malware
(aka
Gootkit)
continues
to
improve
their
code
by
adding
new
components
and
implementing
new
obfuscation
techniques.
Gootkit
runs
on
an access-a-as-a-service model,
it
is
used
by
different
groups
to
drop
additional
malicious
payloads
on
the
compromised
systems.
Gootkit
has
been
known
to
use
fileless
techniques
to
deliver
threats
such
as
the SunCrypt,
and REvil (Sodinokibi)
ransomware, Kronos trojans,
and
Cobalt
Strike.
In
the
past,
Gootkit
distributed
malware
masquerading
as
freeware
installers
and
it
used
legal
documents
to
trick
users
into
downloading
these
files.
The
attack
chain
starts
with
a
user
searching
for
specific
information
in
a
search
engine.
Attackers
use
black
SEO
technique
to
display
a
website
compromised
by
Gootkit
operators
among
the
results.
Upon
visiting
the
website,
the
victim
will
notice
that
it
is
presented
as
an
online
forum
directly
answering
his
query.
This
forum
hosted
a
ZIP
archive
that
contains
the
malicious
.js
file,
which
is
used
to
establish
persistence
and
drop
a
Cobalt
Strike
binary
in
the
memory
of
the
infected
system.
In
November
2022,
Mandiant
researchers
spotted
a
new
variant
of
GOOTLOADER,
tracked
as
GOOTLOADER.POWERSHELL,
that
used
a
new
infection
chain.
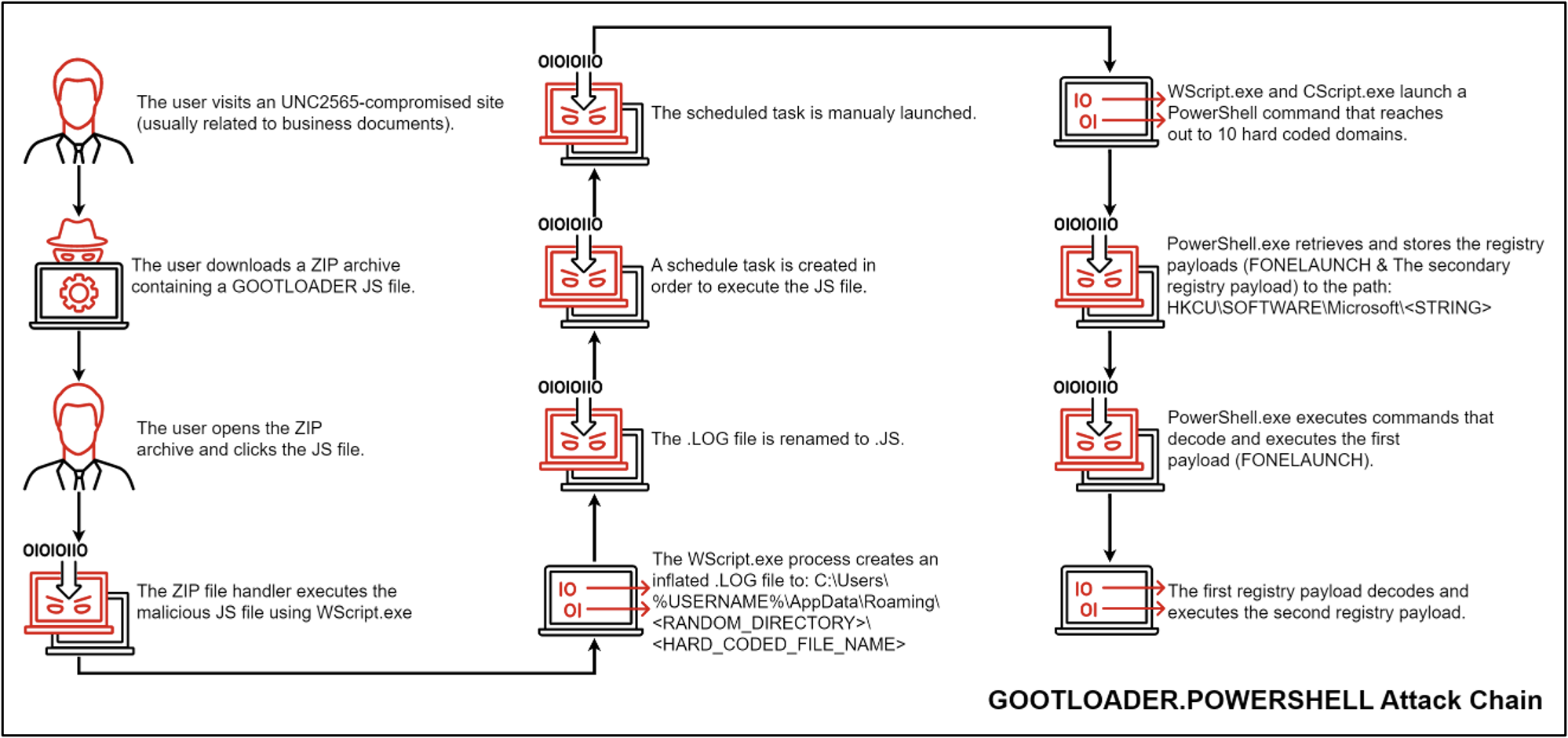
The
new
variant
writes
a
second
.JS
file
to
disk
and
creates
a
scheduled
task
to
execute
it.
Below
is
the
attack
chain
of
this
new
variant:
-
The
user
visits
an
UNC2565-compromised
site
(usually
related
to
business
documents)
and
downloads
a
malicious
ZIP
archive. -
The
malicious
ZIP
file
is
saved
to
the
user’s
Downloads
folder. -
The
user
opens
the
ZIP
file
and
clicks
the
.JS
file
inside.
This
is
a
trojanized
JavaScript
library
containing
an
obfuscated
JScript
file,
which
will
ultimately
execute
GOOTLOADER.POWERSHELL.
Recently
observed
trojanized
JavaScript
libraries
include
jQuery,
Chroma.js,
and
Underscore.js. -
The
JS
file
is
launched
using
WScript.exe. -
The
WScript.exe
process
creates
an
inflated
file
with
a
.LOG
extension
to C:Users%USERNAME%AppDataRoaming<RANDOM_DIRECTORY><HARD_CODED_FILE_NAME>.
The
dropper
writes
more
obfuscated
JScript
code
followed
by
a
padding
of
random
characters
to
increase
the
file
size. -
The
.LOG
file
is
renamed
with
a
.JS
file
extension. -
The
dropper
creates
a
scheduled
task
that
executes
the
new
JScript
file.
The
scheduled
task
is
executed
immediately
after
creation
but
also
serves
as
a
persistence
mechanism
to
run
the
second
JScript
file
at
the
next
logon. -
WScript.exe
and
CScript.exe
launch
a
PowerShell
process
that
reaches
out
to
10
hard
coded
domains.-
Victim
information
collected
includes
environment
variables,
Windows
OS
version,
filenames,
and
running
processes.
This
information
is
Gzip
compressed,
Base64
encoded,
and
sent
to
the
command
and
control
(C2)
server
in
the
Cookie
header.
-
Victim
-
The
C2
returns
a
payload,
which
is
executed
using
the
Invoke-Expression
PowerShell
cmdlet.
This
leads
to
the
download
of
two
payloads
into
registry
keys:
FONELAUNCH
and
a
secondary
payload
to
be
executed
by
FONELAUNCH
(mirroring
steps
6
through
10
of
the
previous
infection
chain).
Mandiant
researchers
observed
the
UNC2565
group
adopting
three
obfuscation
techniques,
such
as
hiding
the
code
within
altered
versions
of
legitimate
JavaScript
libraries
such
as
jQuery,
Chroma.js,
and
Underscore.js,
in
an
attempt
to
evade
detection.
|
Variant 1 |
Variant 2 |
Variant 3 |
|
|
First Observed |
Feb 2021 |
Oct 2021 |
Nov 2022 |
|
Malicious Code |
One obfuscated block of code, easily recognizable. |
Malicious code has been nested within the file. Early samples had all the variables in one block of code, later samples spread the code throughout the file. |
Malicious code has been nested throughout the file. Additional string variables added for the second deobfuscation iteration. |
|
Payload (See Infection Chain) |
GOOTLOADER | GOOTLOADER | GOOTLOADER.POWERSHELL |
“Beginning
in
November
2022,
Managed
Defense
observed
a
new
obfuscation
variant,
tracked
as
variant
3,
with
modified
infection
that
is
more
complex
than
the
previous
variants.
This
new
variant
contains
additional
string
variables
that
are
used
in
a
second
deobfuscation
stage.”
reads
the
report
published
by
Mandiant.
“This
new
variant
has
been
observed
trojanizing
several
legitimate
JavaScript
libraries,
including
jQuery,
Chroma.js,
and
Underscore.js”
Upon
successful
execution
of
the
GOOTLOADER
file,
additional
payloads
are
downloaded,
including
FONELAUNCH
and
Cobalt
Strike
BEACON
or
SNOWCONE
that
will
be
stored
in
the
registry.
Then
the
payloads
are
executed
via
PowerShell
in
the
later
stages.
FONELAUNCH
is
a
.NET-based
launcher,
it
loads
an
encoded
payload
from
the
registry
into
memory.
Since
May
2021,
the
researchers
have
observed
threat
actors
using
three
different
variants
of
FONELAUNCH
that
differ
in
their
loading
mechanism:
-
FONELAUNCH.FAX
reads
and
decodes
data
from
the HKCUSOFTWAREMicrosoftFax%USERNAME% registry
key.
The
returned
content
is
expected
to
be
a
.NET
assembly,
which
is
loaded
at
runtime
into
memory. -
FONELAUNCH.PHONE
mainly
reads
and
decodes
data
placed
in
a
specific
registry
key.
The
returned
data
is
expected
to
be
a
DLL,
which
is
loaded
via
a
publicly
available
DynamicDllLoader
project. -
FONELAUNCH.DIALTONE
reads
and
decodes
data
from
the HKCUSOFTWAREMicrosoft%USERNAME% registry
key.
The
returned
content
is
expected
to
be
a
PE
file,
which
is
injected
into
a
separate
process
and
executed.
The
report
published
by
Mandiant
also
includes
Indicators
of
Compromise
(IoCs)
and
YARA
rules
associated
with
these
threats.
Follow
me
on
Twitter:
@securityaffairs
and
Facebook
and
Mastodon
(SecurityAffairs –
hacking,
GOOTLOADER)