
With
Ransomware
attacks
surging
dramatically
over
the
past
year,
and
reports
pegging
it
as
25%
of
the
total
Cyberthreats
in
2022,
the
question
is,
how
is
it
escalating
to
admin
level
to
perform
encryption
at
such
a
scale?
In
this
blog,
researchers
at
Quick
Heal
decrypt
one
probable
technique
used
by
malware
to
encrypt
all
the
files
in
the
system.
So,
let’s
get
started.
Introduction:
Ransomware
is
not
only
one
of
the
most
common
form
of
cyber-attacks,
but
it
is
also
one
of
the
most
destructive
malware
type.
It
typically
encrypts
the
victim’s
system
with
an
encryption
key
and
demands
a
ransom
for
the
decryption
key
from
attackers.
However,
what
is
interesting
to
ponder
upon
is
its
ability
to
encrypt
the
system
root
drive
(“C”
drive),
which
has
system
privileges
available
only
with
the
administrator.
This
is
a
mystery
until
due
analysis
and
incidence
response
is
conducted.
Usually,
malwares
use
different
techniques
to
enter
the
system,
get
privileges,
and
make
changes
in
the
system’s
normal
state.
While
Ransomware
is
just
an
example,
this
applies
to
all
malware
families
as
well.
In
this
blog,
we
are
going
to
discuss
a
crucial
step
in
the
attack
chain,
i.e.,
how
is
the
malware
able
to
achieve
administrative
privileges
to
perform
changes
in
the
system.
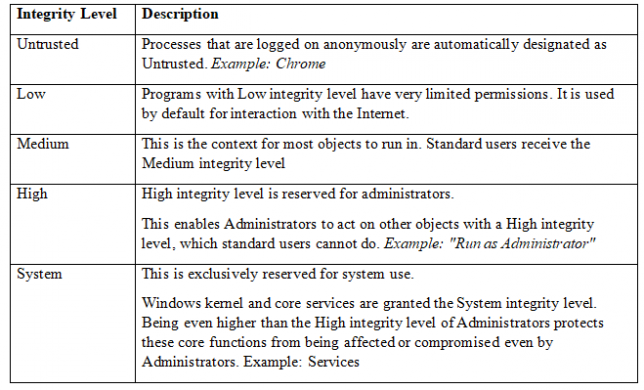
The
programs
running
on
our
system
run
with
different
level
of
permissions
as
indicated
by
the
table
below.
This
shows
the
integrity
levels
that
grant
certain
level
of
permissions
for
programs
to
execute:
–
We
can
find
the
integrity
level
of
any
given
process
using
the
Process
Explorer
tool
from
Sysinternals
suite.
UAC
(User
Account
Control)
plays
a
major
role
in
differentiating
the
program
execution
levels.
User
Account
Control
is
a
program
that
allows
the
running
program
to
get
administrative-level
permissions.
It
is
an
inbuilt
security
mechanism,
that
displays
a
prompt
to
the
user,
asking
whether
to
elevate
the
program
to
an
admin
or
not.
This
is
something
most
of
us
would
have
encountered,
as
illustrated
in
the
figure
below.
A
UAC
prompt
asks
the
user
whether
they
want
to
run
this
program
as
an
administrator
or
not:-
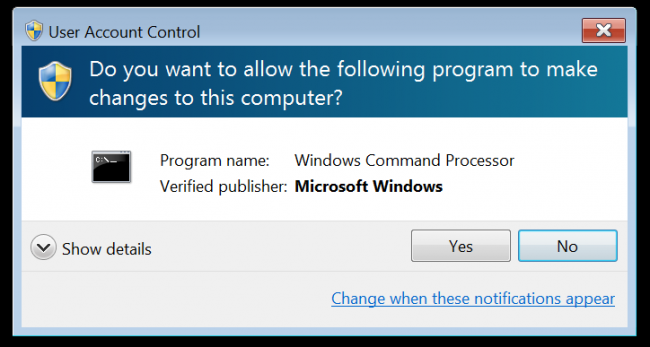
Fig
1
:
Usual
UAC
Prompt
So,
are
you
now
wondering
how
the
malware
is
getting
admin
privileges
without
displaying
any
UAC
prompt
to
the
user?
As
per
our
analysis,
this
is
done
by
bypassing
the
UAC
to
get
admin
access.
Yes,
it
is
possible
to
bypass
UAC
without
the
victim’s
knowledge,
and
there
are
several
techniques
to
do
so
and
attain
high-level
permissions:-
Possible
UAC
Bypass
techniques:
-
Registry
key:
A
small
change
in
the
registry
key
will
elevate
the
program
to
the
admin
level.
The
most
commonly
changed
key
is
shell/open/command.
Trickbot
uses
this
technique
to
bypass
UAC -
DLL
Hijack:
When
an
auto-elevated
program
is
running
and
requesting
to
load
a
legitimate
DLL,
a
malicious
DLL
will
be
loaded
that
takes
over
the
process
when
one
of
its
functions
is
called.
Popular
groups
like
chaes,
FinFisher,
Melcoz,
etc
use
this
technique. -
COM
Interface:
This
technique
is
used
by
some
malware
families.
It
is
a
bit
different
because
it
is
very
easy
to
get
and
very
complex
to
detect.
This
is
because,
instead
of
changing
the
key
or
loading
malicious
DLL,
it
targets
a
genuine
windows
application
program
COM
interface
which
usually
operates
at
the
admin
level.
This
makes
the
job
of
a
malicious
program
easier.
Groups
like
Cobalt,
Muddy
water,
etc.
use
this
technique.
COM
(component
Object
Model)
is
a
method
introduced
by
Microsoft
to
help
the
programs
distribute
binaries
between
other
programs
irrespective
of
the
language
in
which
it
was
written.
Any
application
can
use
another
application’s
COM
object
to
get
that
functionality
in
it.
COM
objects
could
be
an
EXE
or
a
DLL.
The
application
uses
any
of
the
COM
objects
to
get
its
services.
A
globally
unique
identifier
which
is
128-bit
known
as
CLSID
(Class
Identifier)
is
associated
with
it.
The
registry
key
-
ComputerHKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows
NTCurrentVersionUACCOMAutoApprovalList.
It
contains
a
list
of
COM
interfaces
that
can
be
elevated.
Any
COM
interface
can
be
used
by
malware
to
elevate
its
running
level.
In
this
blog,
we
are
discussing
one
common
method
that
is
used
by
popular
ransomware
like
Lock
bit
3.0
and
BlackCat.
That
is
How
CMSTP
COM
objects
are
used
for
UAC
bypass.
CMSTP:
CMSTP
stands
for
Microsoft
Connection
Manager
Profile
Installer.
This
binary
is
used
to
install
the
connection
manager
service
profile.
It
is
a
command
line
tool.
It
accepts
INF
files
as
input
and
installs
the
profile
that
is
mentioned
in
the
INF
file.
The
user
can
install
any
profile
using
CMSTP
with
just
one
command.
The
service
profile
can
be
installed
silently
without
prompting
the
user.
It
is
mostly
used
to
install
VPN
profiles.
It
is
a
signed
file
normally
located
in
the
below
locations.
- C:WindowsSystem32cmstp.exe
- C:WindowsSysWOW64cmstp.exe
Many
APT
groups
are
targeting
CMSTP
COM
objects
for
UAC
Bypass.
As
it
is
a
genuine
windows
application,
it
can
be
used
easily
to
get
admin
privileges.
Plus,
it
is
a
Microsoft-signed
file,
which
can
be
easily
bypassed
by
the
Antivirus
engine
also.
There
are
three
popular
techniques
that
can
be
used
for
UAC
bypass
with
CMSTP
COM
objects.
-
Using
Malicious
INF
files
as
input -
Using
CLSIDs
of
CMLUA,
CMSTPLUA -
Linking
CMLUA.dll
at
runtime
-
Using
Malicious
INF
Files
as
input:
CMSTP.exe
usually
accepts
.INF
file.
INF
file:
is
the
file
name
extension
for
an
information
file.
Every
service
profile
has
one
.inf
file.
The
.inf
file
specifies
installation
information
for
service
profiles.
But
these
days
adversaries
use
malicious
INF
files
with
malicious
commands
in
order
to
execute
arbitrary
code.
Syntax:
cmstp.exe
[/nf]
[/s]
[/u]
[drive:][path]
serviceprofilefilename.inf
/nf:
Specifies
that
the
support
files
should
not
be
installed.
/s:
Specifies
that
the
service
profile
should
be
installed
or
uninstalled
silently
/u:
Specifies
that
the
service
profile
should
be
uninstalled.
/q:a
:
Specifies
that
the
profile
should
be
installed
without
prompting
the
user.
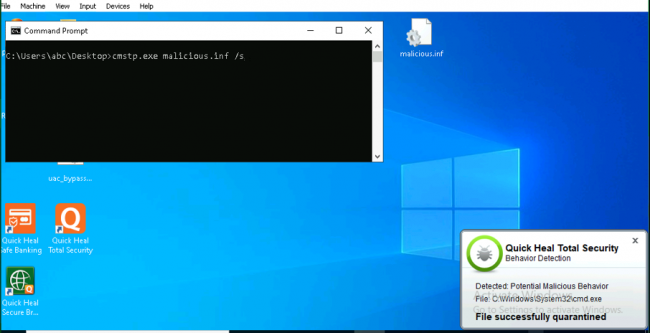
Example:
A
malicious
INF
file
is
passed
to
the
CMSTP
to
get
administrative
privileges
for
the
command
prompt.
This
INF
file
will
give
us
an
elevated
command
prompt
for
the
user
when
they
install
the
malicious
inf.
-
exe
malicious.inf
/s
As
we
can
see,
after
running
the
command
with
/s
(Ref:Fig
2)
it
means
installing
the
file
silently
without
prompting
the
user.
Thereby
which,
we
immediately
get
a
command
prompt
as
Administrator
(Ref:
Fig
3).
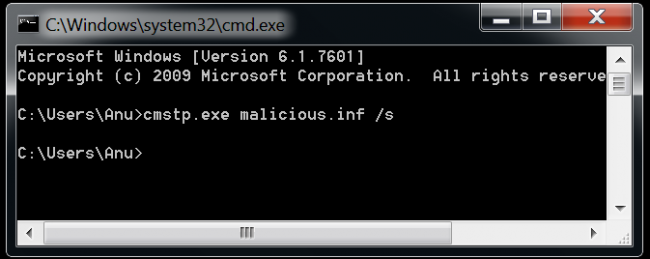
Fig
2
Command
prompt
with
CMSTP
command
input
as
malicious
inf
file
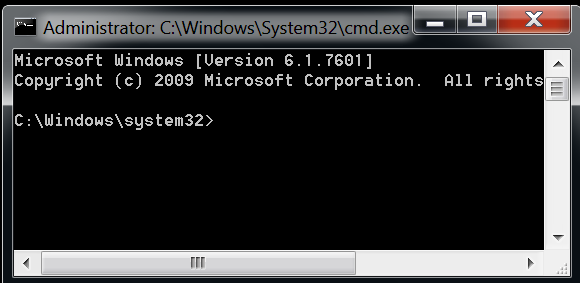
Fig
3
:
Command
Prompt
as
Administrator
after
executing
Malicious
inf
file
APT
Groups:
Cobalt
Group,
Muddy
water,
Evilnum
uses
this
technique
to
bypass
UAC
-
Using
CLSIDs
of
CMLUA,
CMSTPLUA
A
CLSID
is
a
globally
unique
identifier
that
identifies
a
COM
class
object.
If
your
server
or
container
allows
linking
to
its
embedded
objects,
you
need
to
register
a
CLSID
for
each
supported
class
of
objects.
CMSTP
also
has
two
CLSIDs
(Ref:
Fig
4
and
Fig
5)
for
two
dlls.
Registry
location
for
both
the
CLSID:
- ComputerHKEY_LOCAL_MACHINESOFTWAREClassesCLSID{3E5FC7F9-9A51-4367-9063-A120244FBEC7}
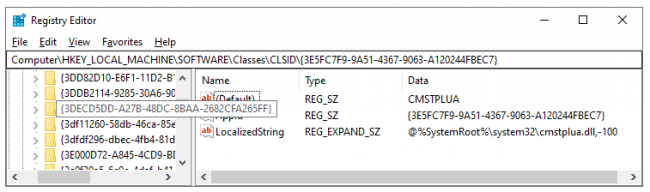
Fig
4
:
CLSID
of
CMSTPLUA
from
registry
- ComputerHKEY_LOCAL_MACHINESOFTWAREClassesCLSID{3E000D72-A845-4CD9-BD83-80C07C3B881F}
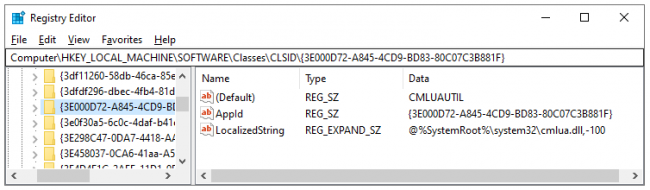
Fig
5:
CLSID
of
CMLUAUTIL
from
registry
-
They
can
also
use
IID
(the
Interface
ID)
in
combination
with
any
of
the
two
CLSIDs
“{6EDD6D74-C007-4E75-B76A-E5740995E24C}”
Example:
Let’s
take
an
example
of
BlackCat
Ransomware:
IOC
–
MD5
–
097cc44444c6733bc6b32cb1c4c87ddd
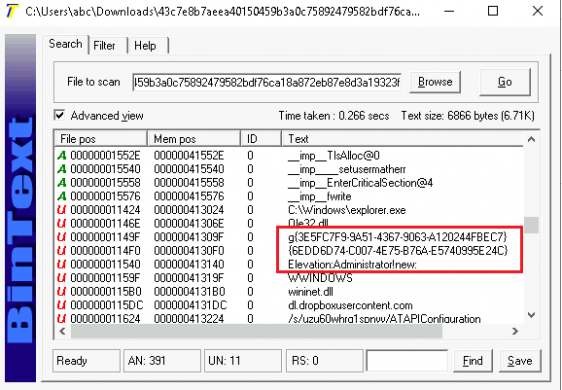
Fig
6:
Examining
strings
in
malware
with
BinText
By
observing
strings,
we
can
see
CLSID
and
IID
(mentioned
above)
with
the
string
Elevation:
Administrator.
It
means
it
is
using
the
CLSID
of
CMSTPLUA
for
getting
admin
access
(Ref:
Fig
6
highlighted
part).
APT
Groups:
Avaddon
-
Linking
CMLUA.dll
at
runtime:
Normally,
CMLUA.dll
and
CMSTPLUA.dll
will
be
loaded
by
CMSTP.exe
or
CMMGR32.exe.
But,
in
recent
cases
ransomware
are
loading
CMLUA.dll
to
get
administrative
privileges.
This
is
more
complicated
than
the
other
two
types
because
the
malware
loads
DLL
(Ref:
Fig
7
and
Fig
8)
at
runtime.
Runtime
Linking:
It
is
commonly
used
in
malware,
especially
when
packed
or
obfuscated.
Exe
which
has
this
linking
connects
to
libraries
only
when
it
is
needed.,
instead
of,
at
the
starting
of
the
program,
as
with
dynamically
linked
programs.
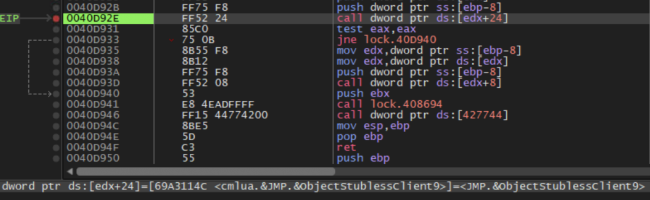
Fig
7:
From
Debugger
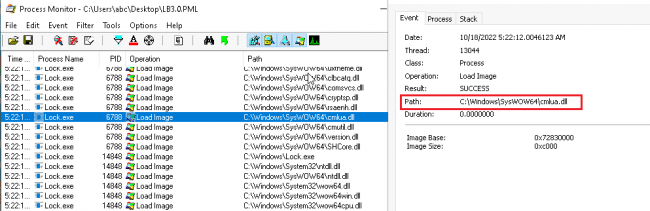
Fig
8:
From
Procmon
Most
of
the
recent
ransomware
including
Lockbit-3.0
uses
this
technique
for
UAC
bypass.
It
is
calling
cmlua
for
getting
admin
privileges.
Ransomware
Groups:
Lock
bit,
Black
matter
IOCs:
- 097CC44444C6733BC6B32CB1C4C87DDD
- 7E37F198C71A81AF5384C480520EE36E
Detections
Quick
heal
with
its
advanced
detection
technologies
is
able
to
detect
these
attacks
through
different
modules
- BlackCat.S28938776
- Lockbit3.S28401281
-
HEUR:
Ransom.Win32.InP
Suspicious
Indicators:
-
Execution
of
cmstp.exe
with
inf
file
without
a
VPN
case. -
CMLUA,
CMLUAUTIL
without
CMSTP.exe
or
CMMGR32.exe. -
CLSIDs
of
CMLUA,
CMLUAUTIL
with
Elevation:
Administrator
in
strings.
Conclusion:
Adversaries
are
now
using
inbuilt
system
applications
to
gain
higher-level
permissions,
as
changes
in
registry
keys
are
easily
detected
by
Antivirus
engines.
These
User
Access
Control
bypass
techniques
gives
them
hassle-free
execution
of
malware
because
they
are
hard
to
detect
and
easy
to
implement.
However,
CMSTP
is
just
one
method,
and
there
are
other
genuine
applications
as
well
that
could
be
getting
abused
to
get
high
privileges.
At
this
point,
we
at
Quick
Heal
strongly
recommend
users
to
exercise
caution,
maintain
strict
user
access
controls
and
keep
their
Anti-Virus
updated
at
all
times.
Subject
Matter
Experts:
-
Aravind
Raj -
Sathwik
Ram
Prakki -
Rayapati
Lakshmi
Prasanna
Sai









