Microsoft has rolled out 117 patches across 15 product families this Tuesday. The company has identified three critical issues affecting Configuration Manager, Visual Studio, and Windows. At the time of release, two of the addressed problems have been actively exploited, with an additional eight CVEs at risk of exploitation within the next 30 days. Sophos protections can detect three of the issues this month, and details are provided in the table below.
Aside from the patches, the release contains advisory information related to four Edge-associated CVEs and one concerning curl (impacting CBL Mariner and Windows). Additionally, standard servicing stack updates have been included. At the conclusion of this post, we have appended lists categorizing all of Microsoft’s patches based on severity, predicted exploitability, and product family.
Statistics Breakdown
- Total CVEs: 117
- Publicly disclosed: 4
- Exploitation detected: 2
- Severity
- Critical: 3
- Important: 110
- Moderate: 3
- Low: 1
- Impact
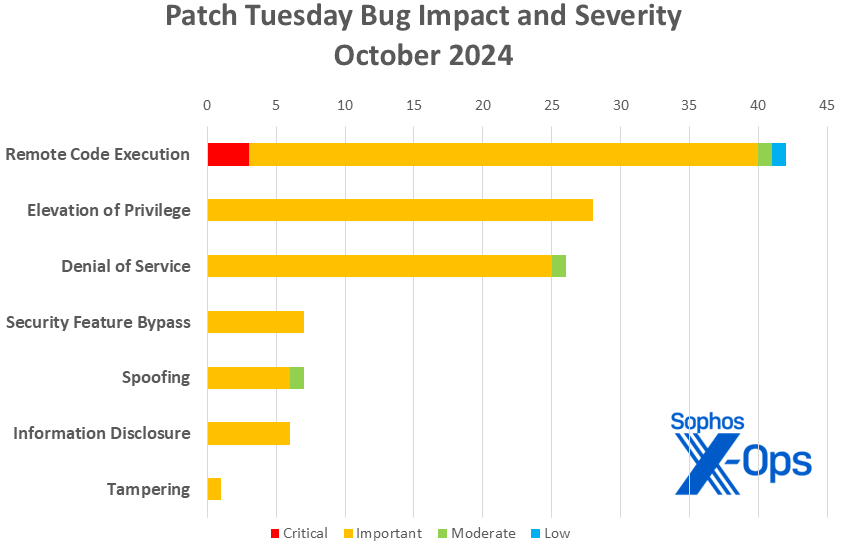
- Remote Code Execution: 42
- Elevation of Privilege: 28
- Denial of Service: 26
- Security Feature Bypass: 7
- Spoofing: 7
- Information Disclosure: 6
- Tampering: 1
- CVSS base score 9.0 or above: 2
- CVSS base score 8.0 or above: 25
Figure 1: Denial of service issues take the spotlight this month due in part to numerous Windows Mobile broadband-driver patches; further details to follow shortly
Product Overview
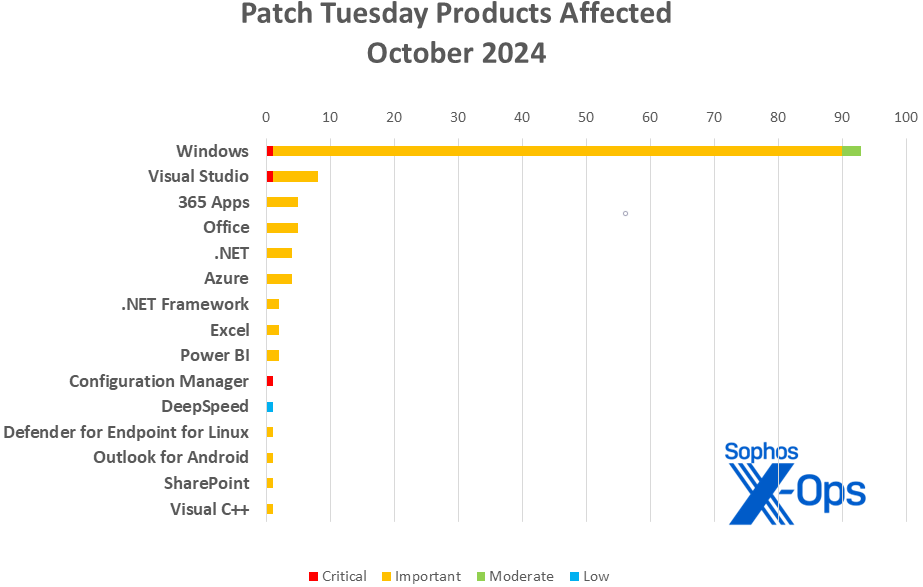
- Windows: 93
- Visual Studio: 8
- 365 Apps: 5
- Office: 5
- .NET: 4
- Azure: 4
- .NET Framework: 2
- Excel: 2
- Power BI: 2
- Configuration Manager: 1
- DeepSpeed: 1
- Defender for Endpoint for Linux: 1
- Outlook for Android: 1
- SharePoint: 1
- Visual C++: 1
In line with our practice, CVEs affecting multiple product families are counted once per impacted family.
Figure 2: Some rare product families are highlighted in this month’s chart, with Windows dominating
Highlighted Updates in October
In the midst of the discussed issues, various specific items deserve mention.
CVE-2024-38124 – Windows Netlogon Elevation of Privilege Vulnerability
CVE-2024-43468 — Microsoft Configuration Manager Remote Code Execution Vulnerability
Both of this month’s CVEs with CVSS base scores of 9.0 or higher come with suggested countermeasures. The Configuration Manager problem (CVE-2024-43468), deemed more severe with a CVSS of 9.8, also comes with specific guidelines. For the Netlogon vulnerability (CVE-2024-38124), the following mitigation strategies are advised (excerpt from Microsoft’s suggestions):
- Avoid Predictable Naming Conventions: Steer clear of predictable domain controller naming to prevent attackers from renaming their machines to match upcoming domain controller names.
- Validate Secure Channel: Ensure robust validation of the secure channel beyond just the delivered machine’s computer name. This can deter attackers from impersonating the domain controller by seizing control and waiting for the proper time.
- Monitor Renaming Activities: Set up surveillance for suspicious renaming operations involving network computers. This enhances early detection capabilities and prevents potential attacks.
- Opt for Enhanced Authentication Mechanisms: Contemplate utilizing advanced authentication methods that surpass the current validation protocols to validate the domain controller and secure channel legitimacy.
Regarding the Configuration Manager issue, administrators are required to follow additional steps (text provided by Microsoft):
Users employing a specified Configuration Manager version from the CVE’s Security Updates table need to install an in-console update for protection. Detailed instructions for installing Configuration Manager in-console updates are accessible here: Install in-console updates for Configuration Manager.
Furthermore, the guidance for mitigating the Configuration Manager issue recommends administrators to specify an alternative service account instead of the Computer account. Additional information can be found here.
[15 CVEs] – Windows Mobile Broadband Driver Denial of Service and Remote Code Execution issues
Though not as alarming as the Critical CVE-2024-38161 mobile broadband driver flaw patched back in July, the sheer number of these issues is noteworthy. It should be highlighted that physical access (via USB drive insertion) or proximity (radio transmission range) is required for exploitation.
CVE-2024-43485 — .NET and Visual Studio Denial of Service Vulnerability
This Important-severity Denial of Service vulnerability extends its reach to .NET not only on Windows but also on Linux and macOS platforms.
CVE-2024-43497 — DeepSpeed Remote Code Execution Vulnerability
Although it’s uncommon for a Low-severity problem to be mentioned in the Patch Tuesday rollout, this issue is intriguing for another reason—it impacts DeepSpeed, Microsoft’s deep-learning training speed-and-scale enhancer. This bug marks the first-ever Patch Tuesday vulnerability affecting DeepSpeed and the initial discovery by Microsoft’s AI-oriented bug bounty program.
CVE-2024-43527 — Windows Kernel Elevation of Privilege Vulnerability
CVE-2024-43571 — Sudo for WindowsSpoofing Security Flaw
The significance of these two patches lies not in their content, but rather in the specific version of Windows they impact. These patches, categorized as Important, exclusively address vulnerabilities in Windows 11 24H2, the latest operating system version released this week.
CVE-2024-43573 — Deception Bug in Windows MSHTML Platform
Among the vulnerabilities actively exploited in the wild, this Moderately-severe Spoofing flaw playfully references Internet Explorer’s legacy. Users receiving Security Only updates are advised to install the IE Cumulative updates to mitigate this vulnerability effectively.
Figure 3: Denial of Service issues surge to third place on the board as we near the end of the year, while the Low-severity DeepSpeed glitch introduces a new patch in 2024
Security Measures by Sophos
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2024-43502 | Exp/2443502-A | Exp/2443502-A |
| CVE-2024-43572 | SID: 2310213; Troj/XML-AA, Troj/PastaLdr-A | SID: 2310213 |
| CVE-2024-43573 | SID: 2310220, 2310222; Exp/2443573-A | SID: 2310220, 2310221 |
Each month, if you prefer not to wait for automatic Microsoft updates, you can manually download them from the Windows Update Catalog website. Utilize the winver.exe tool to determine your specific Windows 10 or 11 build, then download the Cumulative Update tailored to your system’s architecture and build.
Appendix A: Severity of Vulnerabilities
Below is a list of October patches organized by impact and subsequently by severity, further sorted by CVE codes.
Remote Code Execution (42 CVEs)
| Critical severity | |||
| CVE-2024-43468 | Vulnerability in Microsoft Configuration Manager allowing Remote Code Execution | ||
| CVE-2024-43488 | Remote Code Execution Vulnerability in Visual Studio Code’s Arduino extension | ||
| CVE-2024-43582 | Remote Code Execution Flaw in Remote Desktop Protocol Server | ||
| Important severity | |||
| CVE-2024-30092 | Critical Remote Code Execution Vulnerability in Windows Hyper-V | ||
| CVE-2024-38029 | Remote Code Execution Vulnerability in Microsoft OpenSSH for Windows | ||
| CVE-2024-38212 | Remote Code Execution Vulnerability in Windows Routing and Remote Access Service (RRAS) | ||
| CVE-2024-38229 | Remote Code Execution Vulnerability in .NET and Visual Studio | ||
| CVE-2024-38261 | Remote Code Execution Vulnerability in Windows Routing and Remote Access Service (RRAS) | ||
| CVE-2024-38262 | Remote Code Execution Vulnerability in Windows Remote Desktop Licensing Service | ||
| CVE-2024-38265 | Remote Code Execution Vulnerability in Windows Routing and Remote Access Service (RRAS) | ||
| CVE-2024-43453 | Remote Code Execution Vulnerability in Windows Routing and Remote Access Service (RRAS) | ||
| CVE-2024-43480 | Azure Service Fabric for Linux Remote Code Execution Vulnerability | ||
| CVE-2024-43504 | Remote Code Execution Vulnerability in Microsoft Excel | ||
| CVE-2024-43505 | Remote Code Execution Vulnerability in Microsoft Office Visio | ||
| CVE-2024-43517 | Remote Code Execution Vulnerability in Microsoft ActiveX Data Objects | ||
| CVE-2024-43518 | Remote Code Execution Vulnerability in Windows Telephony Server | ||
| CVE-2024-43519 | Remote Code Execution Vulnerability in Microsoft WDAC OLE DB provider for SQL Server | ||
| CVE-2024-43523 | Remote Code Execution Vulnerability in Windows Mobile Broadband Driver | ||
| CVE-2024-43524 | Remote Code Execution Vulnerability in Windows Mobile Broadband Driver | ||
| CVE-2024-43525 | Remote Code Execution Vulnerability in Windows Mobile Broadband Driver | ||
| CVE-2024-43526 | Remote Code Execution Vulnerability in Windows Mobile Broadband Driver | ||
| CVE-2024-43533 | Remote Code Execution Vulnerability in Remote Desktop Client | ||
| CVE-2024-43536 | Remote Code Execution Vulnerability in Windows Mobile Broadband Driver | ||
| CVE-2024-43543 | Remote Code Execution Vulnerability in Windows Mobile Broadband Driver | ||
| CVE-2024-43549 | Remote Code Execution Vulnerability in Windows Routing and Remote Access Service (RRAS) | ||
| CVE-2024-43552 | Remote Code Execution Vulnerability in Windows Shell | ||
| CVE-2024-43564 | Remote Code Execution Vulnerability in Windows Routing and Remote Access Service (RRAS) | ||
| CVE-2024-43574 | Remote Code Execution Vulnerability in Microsoft Speech Application Programming Interface (SAPI) | ||
| CVE-2024-43576 | Remote Code Execution Vulnerability in Microsoft Office | ||
| CVE-2024-43581 | Remote Code Execution Vulnerability in Microsoft OpenSSH for Windows | ||
| CVE-2024-43589 | Remote Code Execution Vulnerability in Windows Routing and Remote Access Service (RRAS) | ||
| CVE-2024-43592 | Remote Code Execution Vulnerability in Windows Routing and Remote Access Service (RRAS) | ||
| CVE-2024-43593 | Remote Code Execution Vulnerability in Windows Routing and Remote Access Service (RRAS) | ||
| CVE-2024-43599 | Remote Code Execution Vulnerability in Remote Desktop Client | ||
| Remote Command Execution Vulnerability | |
| CVE-2024-43601 | Visual Studio Code for Linux Remote Command Execution Vulnerability |
| CVE-2024-43607 | Windows Routing and Remote Access Service (RRAS) Remote Command Execution Vulnerability |
| CVE-2024-43608 | Windows Routing and Remote Access Service (RRAS) Remote Command Execution Vulnerability |
| CVE-2024-43611 | Windows Routing and Remote Access Service (RRAS) Remote Command Execution Vulnerability |
| CVE-2024-43615 | Microsoft OpenSSH for Windows Remote Command Execution Vulnerability |
| CVE-2024-43616 | Microsoft Office Remote Command Execution Vulnerability |
| CVE-2024-30092 | Windows Hyper-V Remote Command Execution Vulnerability |
| CVE-2024-38029 | Microsoft OpenSSH for Windows Remote Command Execution Vulnerability |
| CVE-2024-38212 | Windows Routing and Remote Access Service (RRAS) Remote Command Execution Vulnerability |
| CVE-2024-38229 | .NET and Visual Studio Remote Command Execution Vulnerability |
| CVE-2024-38261 | Windows Routing and Remote Access Service (RRAS) Remote Command Execution Vulnerability |
| Medium Risk | |
| CVE-2024-43572 | Microsoft Management Console Remote Command Execution Vulnerability |
Privilege Escalation (28 CVEs)
| Significant threat level | |
| CVE-2024-37979 | Windows Kernel Privilege Escalation Vulnerability |
| CVE-2024-38097 | Azure Monitor Agent Privilege Escalation Vulnerability |
| CVE-2024-38124 | Windows Netlogon Privilege Escalation Vulnerability |
| CVE-2024-38129 | Windows Kerberos Privilege Escalation Vulnerability |
| CVE-2024-38179 | Azure Stack Hyperconverged Infrastructure (HCI) Privilege Escalation Vulnerability |
| CVE-2024-43501 | Windows Common Log File System Driver Privilege Escalation Vulnerability |
| CVE-2024-43502 | Windows Kernel Privilege Escalation Vulnerability |
| CVE-2024-43503 | Microsoft SharePoint Privilege Escalation Vulnerability |
| CVE- 2024-43604 |
Outlook for Android Privilege Escalation Vulnerability |
Service Interruption (26 CVEs)
| Significant threat level | |
| CVE-2024-38149 | BranchCache Service Interruption Vulnerability |
| CVE-2024-43483 | .NET, .NET Framework, and Visual Studio Service Interruption Vulnerability |
| CVE-2024-43484 | .NET, .NET Framework, and Visual Studio Service Interruption Vulnerability |
| CVE-2024-43485 | .NET and Visual Studio Service Interruption Vulnerability |
| CVE-2024-43506 | BranchCache Service Interruption Vulnerability |
| CVE-2024-43512 | Windows Standards-Based Storage Management Service Interruption Vulnerability |
| CVE-2024-43515 | Internet Small Computer Systems Interface (iSCSI) Service Interruption Vulnerability |
| CVE-2024-43521 | Windows Hyper-V Service Interruption Vulnerability |
| CVE-2024-43537 | Windows Mobile Broadband Driver Service Interruption Vulnerability |
| CVE-2024-43538 | Windows Mobile Broadband Driver Service Interruption Vulnerability |
| CVE-2024-43540 | Windows Mobile Broadband Driver Service Interruption Vulnerability |
| CVE-2024-43541 | Microsoft Simple Certificate Enrollment Protocol Service Interruption Vulnerability |
| CVE-2024-43542 | Windows Mobile Broadband Driver Service Interruption Vulnerability |
| CVE-2024-43544 | Microsoft Simple Certificate Enrollment Protocol Service Interruption Vulnerability |
| CVE-2024-43545 | Windows Online Certificate Status Protocol (OCSP) Server |
| Unavailability of Service Weakness | |
| CVE-2024-43555 | Imperfection in Windows Mobile Broadband Driver causing Unavailability of Service |
| CVE-2024-43557 | Window Mobile Broadband Driver Vulnerability leading to Unavailability of Service |
| CVE-2024-43558 | Windows Mobile Broadband Driver Flaw contributing to Unavailability of Service |
| CVE-2024-43559 | Weakness in Windows Mobile Broadband Driver causing Unavailability of Service |
| CVE-2024-43561 | Vulnerability in Windows Mobile Broadband Driver resulting in Unavailability of Service |
| CVE-2024-43562 | Unavailability of Service Vulnerability in Windows Network Address Translation (NAT) |
| CVE-2024-43565 | Unavailability of Service Vulnerability in Windows Network Address Translation (NAT) |
| CVE-2024-43567 | Window Hyper-V Vulnerability leading to Unavailability of Service |
| CVE-2024-43575 | Window Hyper-V Weakness causing Unavailability of Service |
| CVE-2024-43603 | Unavailability of Service Vulnerability in Visual Studio Collector Service |
| Intermediate magnitude | |
| CVE-2024-43520 | Imperfection in Windows Kernel resulting in Unavailability of Service |
Security Aspect Circumvention (7 CVEs)
| Key magnitude | |
| CVE-2024-20659 | Window Hyper-V Circumvention Vulnerability |
| CVE-2024-37976 | Window Resume Extensible Firmware Interface Circumvention Vulnerability |
| CVE-2024-37982 | Window Resume Extensible Firmware Interface Circumvention Vulnerability |
| CVE-2024-37983 | Window Resume Extensible Firmware Interface Circumvention Vulnerability |
| CVE-2024-43513 | BitLocker Circumvention Vulnerability |
| CVE-2024-43584 | Window Scripting Engine Circumvention Vulnerability |
| CVE-2024-43585 | Code Integrity Guard Circumvention Vulnerability |
Camouflage (7 CVEs)
| Key magnitude | |
| CVE-2024-43481 | Power BI Report Server Camouflage Vulnerability |
| CVE-2024-43550 | Window Secure Channel Camouflage Vulnerability |
| CVE-2024-43571 | Sudo for Window Camouflage Vulnerability |
| CVE-2024-43609 | Microsoft Office Camouflage Vulnerability |
| CVE-2024-43612 | Power BI Report Server Camouflage Vulnerability |
| CVE-2024-43614 | Microsoft Defender for Endpoint for Linux Camouflage Vulnerability |
| Intermediate magnitude | |
| CVE-2024-43573 | Window MSHTML Platform Camouflage Vulnerability |
Data Leakage (6 CVEs)
| Key magnitude | |
| CVE-2024-43500 | Window Resilient File System (ReFS) Data Leakage Vulnerability |
| CVE-2024-43508 | Window Graphics Component Data Leakage Vulnerability |
| CVE-2024-43534 | Window Graphics Component Data Leakage Vulnerability |
| CVE-2024-43546 | Window Cryptographic Data Leakage Vulnerability |
| CVE-2024-43547 | Window Kerberos Data Leakage Vulnerability |
| CVE-2024-43554 | Window Kernel-Mode Driver Data Leakage Vulnerability |
Tinkering (1 CVE)
| Key magnitude | |
| CVE-2024-43456 | Window Remote Desktop Services Tinkering Vulnerability |
Appendix B: Vulnerability of Exploitation
This is a register of the October CVEs appraised by Microsoft to be either under current exploitation in the natural habitat or more plausible to be exploited in the natural habitat within the first month post disseminate. The record is organized by CVE.
| Exploitation identified | |
| CVE-2024-43572 | Microsoft Management Console Remote Code Execution Vulnerability |
| CVE-2024-43573 | Window MSHTML Platform Camouflage Vulnerability |
| Exploitation more probable within the forthcoming 30 days | |
| CVE-2024-43502 | Window Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43509 | Window Graphics Component Elevation of Privilege Vulnerability |
| CVE-2024-43556 | Window Graphics Component Elevation of Privilege Vulnerability |
| CVE-2024-43560 | Microsoft Windows Storage Port Driver Elevation of Privilege Vulnerability |
| CVE-2024-43581 | Microsoft OpenSSH for Window Remote Code Execution Vulnerability |
| CVE-2024-43583 | Winlogon Elevation of Privilege Vulnerability |
| CVE-2024-43609 | Microsoft Office Spoofing Vulnerability |
| CVE-2024-43615 | Microsoft OpenSSH for Window Remote Code Execution Vulnerability |
Appendix C: Affected Products
This is a register of October’s patches classified by product family, then reclassified by severity. Each register is additionally cataloged by CVE. Patches that are shared among numerous product families are cataloged multiple times, one for each product family.
Windows (93 CVEs)
| Critical severity | |
| CVE-2024-43582 | Remote Desktop Protocol Server Remote Code Execution Vulnerability |
| Key magnitude | |
| CVE-2024-20659 | Windows Hyper-V Circumvention Vulnerability |
| CVE-2024-30092 | Windows Hyper-V Remote Code Execution Vulnerability |
| CVE-2024-37976 | Window Resume Extensible Firmware Interface Circumvention Vulnerability |
| CVE-2024-37979 | Window Kernel Elevation of Privilege Vulnerability |
| CVE-2024-37982 | Window Resume Extensible Firmware Interface Circumvention Vulnerability |
Security Loophole Vulnerability
.NET Framework (2 Common Vulnerabilities and Exposures)
| Significant severity level | |
| CVE-2024-43483 | .NET, .NET Framework, and Visual Studio Vulnerability causing Denial of Service |
| CVE-2024-43484 | .NET, .NET Framework, and Visual Studio Vulnerability causing Denial of Service |
Excel (2 Common Vulnerabilities and Exposures)
| Significant severity level | |
| CVE-2024-43504 | Microsoft Excel Vulnerability Leading to Remote Code Execution |
| CVE-2024-43609 | Microsoft Office Vulnerability leading to Spoofing |
Power BI (2 Common Vulnerabilities and Exposures)
| Significant severity level | |
| CVE-2024-43481 | Power BI Report Server Vulnerability leading to Spoofing |
| CVE-2024-43612 | Power BI Report Server Vulnerability leading to Spoofing |
Configuration Manager (1 Common Vulnerability and Exposure)
| Critical severity level | |
| CVE-2024-43468 | Microsoft Configuration Manager Vulnerability Leading to Remote Code Execution |
DeepSpeed (1 Common Vulnerability and Exposure)
| Low severity level | |
| CVE-2024-43497 | DeepSpeed Vulnerability Leading to Remote Code Execution |
Defender for Endpoint for Linux (1 Common Vulnerability and Exposure)
| Significant severity level | |
| CVE-2024-43614 | Microsoft Defender for Endpoint for Linux Vulnerability leading to Spoofing |
Outlook for Android (1 Common Vulnerability and Exposure)
| Significant severity level | |
| CVE-2024-43604 | Outlook for Android Vulnerability leading to Elevation of Privileges |
SharePoint (1 Common Vulnerability and Exposure)
| Significant severity level | |
| CVE-2024-43503 | Microsoft SharePoint Vulnerability leading to Elevation of Privileges |
Visual C++ (1 Common Vulnerability and Exposure)
| Significant severity level | |
| CVE-2024-43590 | Visual C++ Redistributable Installer Vulnerability leading to Elevation of Privileges |
Appendix D: Alerts and Other Products
This section provides a catalog of alerts and details on other relevant Common Vulnerabilities and Exposures in the recent release.
| ADV990001 | Most Recent Servicing Stack Updates | |
| CVE-2024-6197 | CBL Mariner, Windows | curl: CVE-2024-6197: releasing stack buffer in utf8asn1str |
| CVE-2024-7025 | Edge | Microsoft Edge Chromium: CVE-2024-7025 Integer overflow in Layout |
| CVE-2024-9369 | Edge | Microsoft Edge Chromium: CVE-2024-9369 Insufficient data validation in Mojo |
| CVE-2024-9370 | Edge | Microsoft Edge Chromium: CVE-2024-9370 Improper implementation in V8 |
| CVE-2024-43566 | Edge | Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability |