
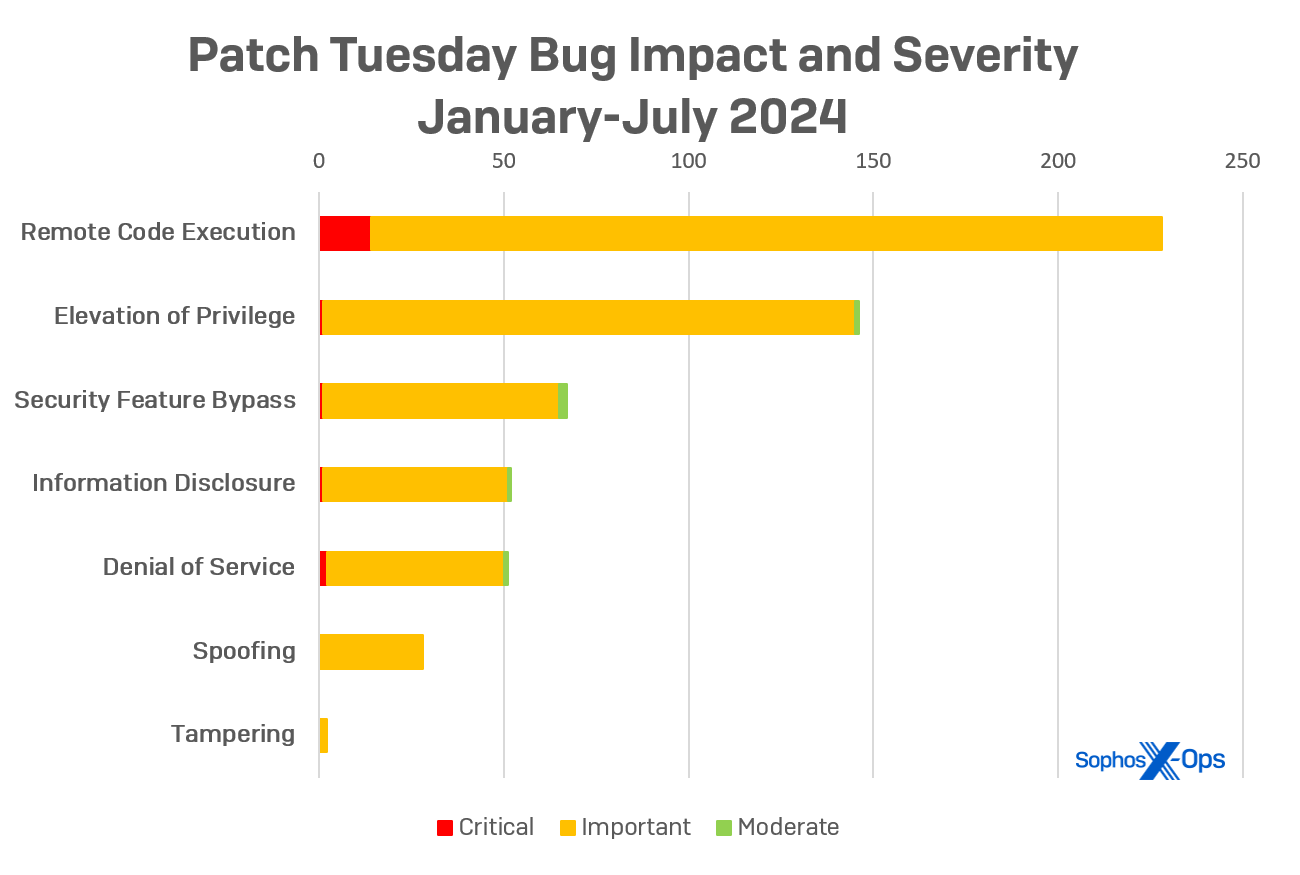
As the information security sector’s leading conferences, Black Hat Briefings and Def Con, draw near, Microsoft has gone all out for July by significantly increasing the number of updates compared to June. The updates address issues found in Windows, Office, and various server and cloud software platforms.
One of the key components receiving extensive fixes in this month’s updates is Microsoft SQL Server. Among the updates is a patch for 38 distinct remote code execution vulnerabilities in the OLE database driver. These vulnerabilities could be exploited if an authenticated account is deceived into connecting to a malicious SQL Server database. When the malicious database returns data that triggers arbitrary code execution on the client, the attack occurs.
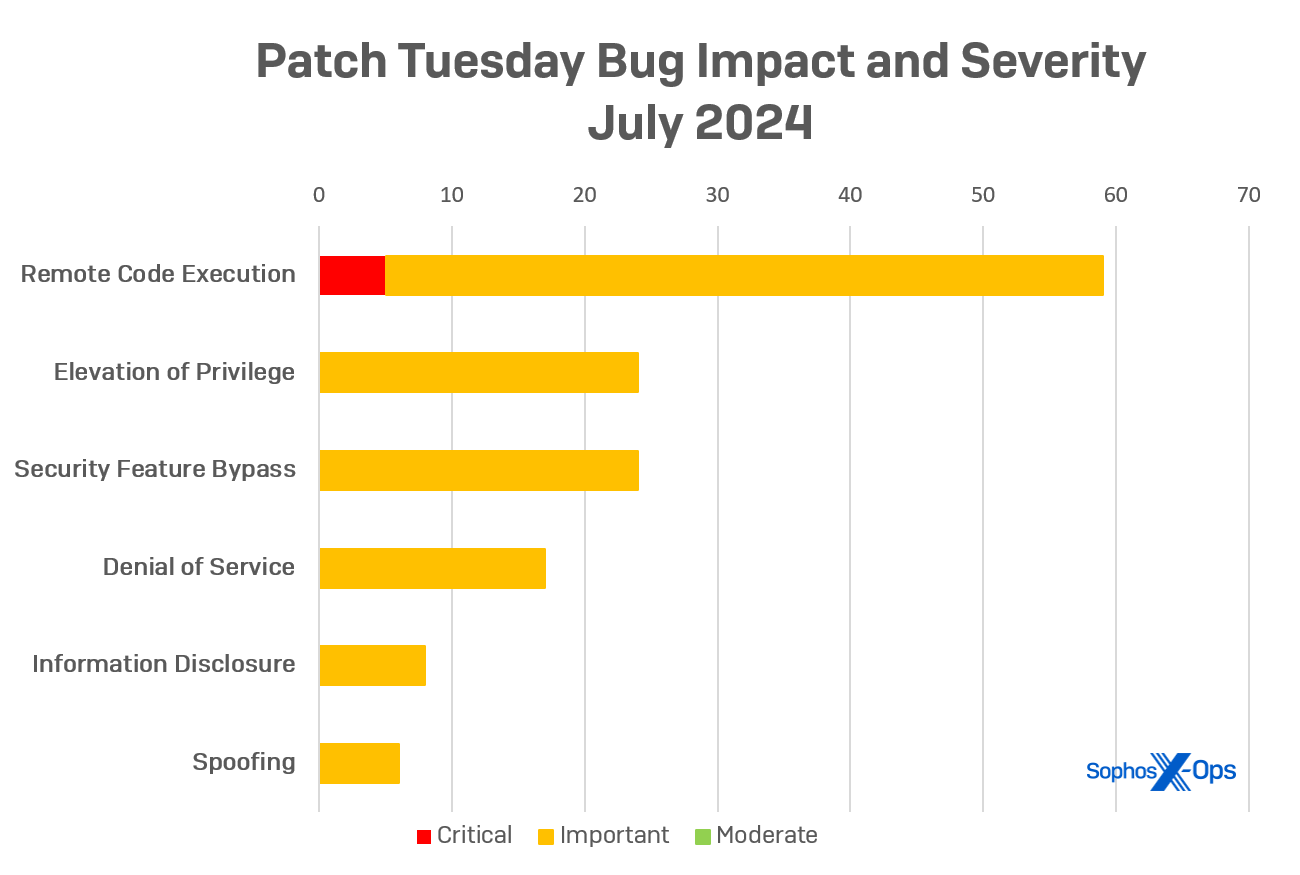
This month’s updates primarily focus on remote code execution vulnerabilities, with 59 RCEs accounting for over 43% of the total issues resolved in the cumulative update. Five of the RCE vulnerabilities are rated as “critical” by Microsoft, affecting SharePoint Server, Windows Remote Desktop Licensing Service, and the Windows Codec library.
July’s list of vulnerabilities includes 13 considered to be more exploitable than others by Microsoft, including critical bugs in SharePoint Server and the Windows Codec library. Fortunately, only one of the fixed bugs has been exploited or made public so far—CVE-2024-38080, a privilege escalation exploit in the Windows Hyper-V hypervisor for virtual machines. Six of this month’s bugs can be detected through Sophos IPS rules in the XGS Firewall, details of which are provided in a table at the end of this document.
While most of the vulnerabilities were reported directly to Microsoft, some bug reports came from external organizations that responsibly disclosed the information. For instance, Adobe reported CVE-2024-34122, an unexploited remote code execution vulnerability in the Chromium version of the Edge browser, which was resolved before Patch Tuesday with the release of version 126.0.2592.81 on June 27.
Statistics Summary
- Total Microsoft CVEs: 138
- Total Edge / Chrome advisory issues covered in the update: 1
- Total non-Microsoft advisory issues covered in the update: 4
- Total Adobe issues covered in the update: 1
- Publicly disclosed: 1
- Exploited: 1
- Severity:
- Critical: 5
- Important: 132
- Moderate: 1
- Impact:
- Remote Code Execution: 59
- Elevation of Privilege: 24
- Security Feature Bypass: 24
- Denial of Service: 17
- Information Disclosure: 8
- Spoofing: 7
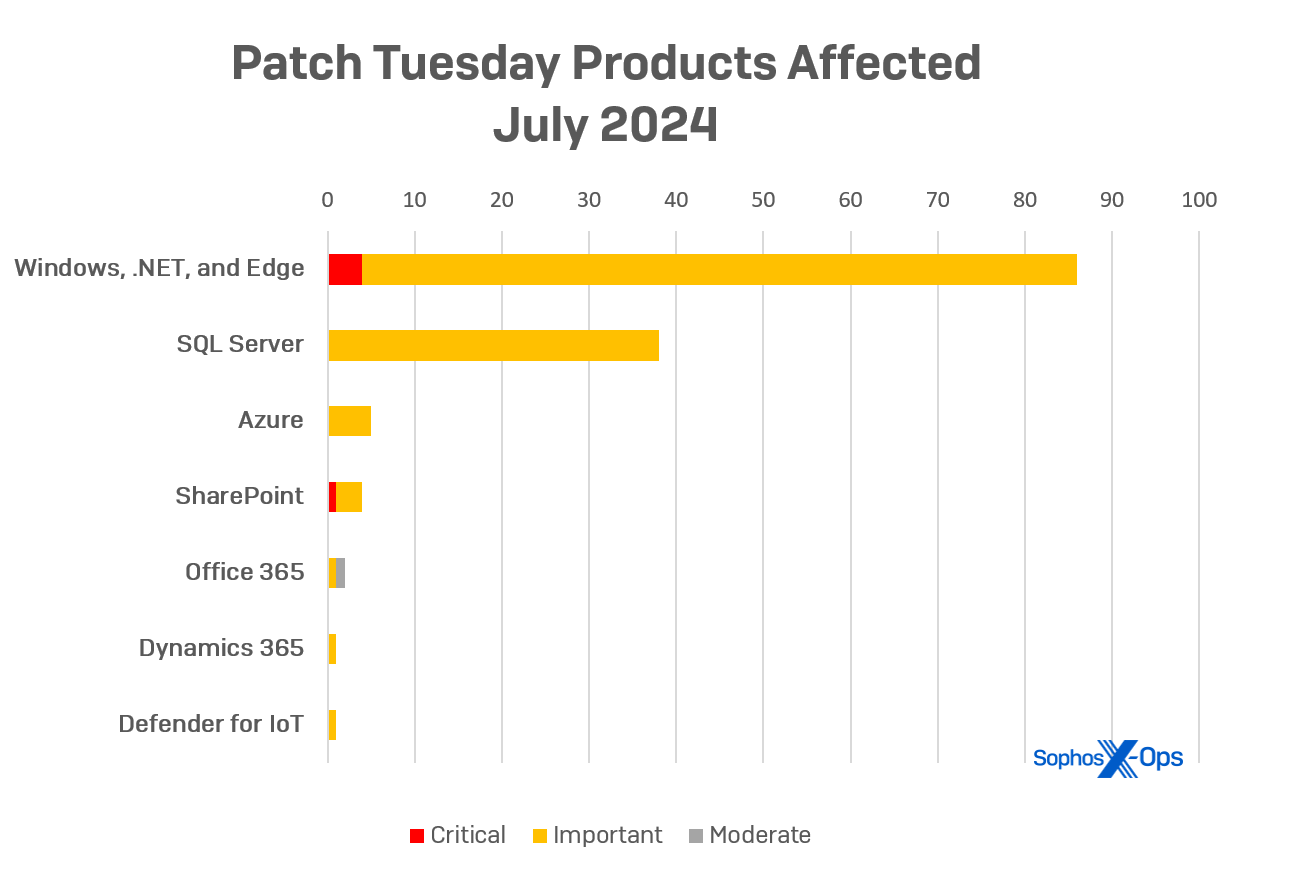
Highlighted Products
- Windows (including .NET and ASP.NET): 87
- Microsoft SQL Server: 38
- Azure: 5
- SharePoint: 4
- Office: 2
- Dynamics 365: 1
- Microsoft Defender for IoT: 1
Updates to Note in July
While many issues have been addressed, some specific updates deserve special mention.
Microsoft SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability
This month, Microsoft has resolved 38 CVEs in its extensive database lineup. The patches target various aspects of a common exploit scenario: If an attacker can convince an authenticated user of a legitimate MS-SQL database server to connect to their malicious MS-SQL Server, malicious code residing on the server can then travel to and execute on the client.
The complex exploit demands preparatory work from attackers, involving setting up a database server with malicious content in its tables. Additionally, it requires the targeted user to have not updated their SQL Server client software with this month’s all-encompassing update, as well as for the attackers to identify and target a database administrator successfully. Avoid being the perfect target.
CVE-2024-38060 – Microsoft Windows Codecs Library Remote Code Execution Vulnerability
In 1986, as the world was mesmerized by the on-screen exploits of daring fighter pilots, the TIFF image file format emerged, introduced by Aldus Corporation, now Adobe. This CVE tackles a critical vulnerability exclusive to this format that is easily exploitable. A specially crafted malicious TIFF file can lead to…
Uploaded onto a susceptible server, may have activated the server to execute malicious code hidden in the TIFF file. Make sure to secure your servers to remove this risk.
Microsoft Xbox Remote Code Execution Vulnerability (CVE-2024-38032)
Players of the Xbox gaming console with a wireless adapter, who connect wirelessly to their local network, need to be cautious of potential intruders on their network who could target these devices. There is a potential threat where an individual connected to your wireless network could send a harmful network packet to the Xbox, potentially executing unauthorized commands. To prevent such risks, avoid allowing unknown parties onto your WLAN.
Measures by Sophos
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2024-38021 | sid:2309849, sid:2309850 | sid:2309849, sid:2309850 |
| CVE-2024-38052 | Exp/2438052-A | |
| CVE-2024-38054 | Exp/2438054-A | |
| CVE-2024-38059 | Exp/2438059-A | |
| CVE-2024-38080 | Exp/2438080-A | |
| CVE-2024-38085 | Exp/2438085-A |
If you prefer not to wait for your system to automatically fetch Microsoft’s updates every month, you can manually download them from the Microsoft Update Catalog website. Use the winver.exe tool to identify your Windows build, then download the appropriate Cumulative Update package for your system’s architecture and build.
Vulnerability Impact and Severity: Appendix A
This categorizes July patches based on impact and severity, arranged by CVE.
Denial of Service (17 CVEs)
| Important severity | |
| CVE-2024-30105 | .NET Denial of Service Vulnerability |
| CVE-2024-35270 | Windows iSCSI Service Denial of Service Vulnerability |
| CVE-2024-38015 | Windows Remote Desktop Gateway (RD Gateway) Denial of Service Vulnerability |
| CVE-2024-38027 | Windows Line Printer Daemon Service Denial of Service Vulnerability |
| CVE-2024-38031 | Windows Online Certificate Status Protocol (OCSP) Server Denial of Service Vulnerability |
| CVE-2024-38048 | Windows Network Driver Interface Specification (NDIS) Denial of Service Vulnerability |
| CVE-2024-38067 | Windows Online Certificate Status Protocol (OCSP) Server Denial of Service Vulnerability |
| CVE-2024-38068 | Windows Online Certificate Status Protocol (OCSP) Server Denial of Service Vulnerability |
| CVE-2024-38071 | Windows Remote Desktop Licensing Service Denial of Service Vulnerability |
| CVE-2024-38072 | Windows Remote Desktop Licensing Service Denial of Service Vulnerability |
| CVE-2024-38073 | Windows Remote Desktop Licensing Service Denial of Service Vulnerability |
| CVE-2024-38091 | Microsoft WS-Discovery Denial of Service Vulnerability |
| CVE-2024-38095 | .NET Denial of Service Vulnerability |
| CVE-2024-38099 | Windows Remote Desktop Licensing Service Denial of Service Vulnerability |
| CVE-2024-38101 | Windows Layer-2 Bridge Network Driver Denial of Service Vulnerability |
| CVE-2024-38102 | Windows Layer-2 Bridge Network Driver Denial of Service Vulnerability |
| CVE-2024-38105 | Windows Layer-2 Bridge Network Driver Denial of Service Vulnerability |
Elevation of Privileges (24 CVEs)
| Important severity | |
| CVE-2024-21417 | Windows CoreMessaging Elevation of Privileges Vulnerability |
| CVE-2024-30079 | Windows Remote Access Connection Manager Elevation of Privilege Vulnerability |
| CVE-2024-35261 | Azure Network Watcher VM Extension Elevation of Privilege Vulnerability |
| CVE-2024-38013 | Microsoft Windows Server Backup Elevation of Privilege Vulnerability |
| CVE-2024-38022 | Windows Image Acquisition Elevation of Privilege Vulnerability |
| CVE-2024-38033 | PowerShell Elevation of Privilege Vulnerability |
| CVE-2024-38034 | Windows Filtering Platform Elevation of Privilege Vulnerability |
| CVE-2024-38043 | PowerShell Elevation of Privilege Vulnerability |
| CVE-2024-38047 | PowerShell Elevation of Privilege Vulnerability |
| CVE-2024-38050 | Windows Workstation Service Elevation of Privilege Vulnerability |
| CVE-2024-38052 | Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38054 | Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38057 | Microsoft Streaming Service Elevation of Privilege Vulnerability | Win32k Security Elevation Vulnerability |
| CVE-2024-38061 | Active Directory Certificate Services Security Elevation Vulnerability |
| CVE-2024-38062 | Windows Clip Service Security Elevation Vulnerability |
| CVE-2024-38066 | Windows Win32k Security Elevation Vulnerability |
| CVE-2024-38079 | Windows Graphics Component Security Elevation Vulnerability |
| CVE-2024-38080 | Windows Hyper-V Security Elevation Vulnerability |
| CVE-2024-38081 | .NET, .NET Framework, and Visual Studio Security Elevation Vulnerability |
| CVE-2024-38085 | Windows Win32 Kernel Subsystem Security Elevation Vulnerability |
| CVE-2024-38089 | Microsoft Defender for IoT Security Elevation Vulnerability |
| CVE-2024-38092 | Azure CycleCloud Security Elevation Vulnerability |
| CVE-2024-38100 | Windows File Explorer Security Elevation Vulnerability |
Data Leakage (9 CVEs)
| Significant severity | |
| CVE-2024-30061 | Microsoft Dynamics 365 (On-Premises) Data Leakage Vulnerability |
| CVE-2024-30071 | Windows Remote Access Connection Manager Data Leakage Vulnerability |
| CVE-2024-32987 | Microsoft SharePoint Server Data Leakage Vulnerability |
| CVE-2024-37985 | Intel ARM: Systematic Identification and Characterization of Proprietary Prefetchers |
| CVE-2024-38017 | Microsoft Message Queuing Data Leakage Vulnerability |
| CVE-2024-38041 | Windows Kernel Data Leakage Vulnerability |
| CVE-2024-38055 | Microsoft Windows Codecs Library Data Leakage Vulnerability |
| CVE-2024-38056 | Microsoft Windows Codecs Library Data Leakage Vulnerability |
| CVE-2024-38064 | Windows TCP/IP Data Leakage Vulnerability |
Code Execution Remotely (59 CVEs)
| Urgent severity | ||
| CVE-2024-38023 | Microsoft SharePoint Server Remote Code Execution Vulnerability | |
| CVE-2024-38060 | Microsoft Windows Codecs Library Remote Code Execution Vulnerability | |
| CVE-2024-38074 | Windows Remote Desktop Licensing Service Remote Code Execution Vulnerability | |
| CVE-2024-38076 | Windows Remote Desktop Licensing Service Remote Code Execution Vulnerability | |
| CVE-2024-38077 | Windows Remote Desktop Licensing Service Remote Code Execution Vulnerability | |
| Significant severity | ||
| CVE-2024-20701 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-21303 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-21308 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-21317 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-21331 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-21332 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-21333 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-21335 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-21373 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-21398 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-21414 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-21415 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-21425 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-21428 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-21449 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-28928 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-30013 | Windows MultiPoint Services Remote Code Execution Vulnerability | |
| CVE-2024-35256 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-35264 | .NET and Visual Studio Remote Code Execution Vulnerability | |
| CVE-2024-35271 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-35272 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-37318 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-37319 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-37320 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-37321 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-37322 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-37323 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-37324 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-37326 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-37327 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-37328 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-37329 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-37330 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-37331 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-37332 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-37333 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | |
| CVE-2024-37334 | Microsoft | Microsoft Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-38102 | Microsoft Windows Remote Desktop Protocol Remote Code Execution Vulnerability | |
| CVE-2024-38108 | Microsoft Windows Scripting Engine Memory Corruption Vulnerability | |
| CVE-2024-38109 | Windows Digital Media Control Panel Elevation of Privilege Vulnerability | |
| CVE-2024-38111 | Microsoft Word Memory Corruption Vulnerability | |
| CVE-2024-38115 | Microsoft Outlook Elevation of Privilege Vulnerability | |
| CVE-2024-38116 | Microsoft Windows SMBv2 Share Elevation of Privilege Vulnerability | |
| CVE-2024-38117 | Windows Wireless Networking Driver Elevation of Privilege Vulnerability | |
| CVE-2024-38118 | Windows Update Stack Elevation of Privilege Vulnerability | |
| CVE-2024-38120 | Internet Explorer Memory Corruption Vulnerability | |
| CVE-2024-38124 | Microsoft Windows Store Elevation of Privilege Vulnerability | |
| CVE-2024-38125 | Windows Graphics Component Memory Corruption Vulnerability | |
| CVE-2024-38127 | Microsoft Windows Text Services Framework Remote Code Execution Vulnerability | |
| CVE-2024-38128 | Microsoft Windows Media Feature Pack Remote Code Execution Vulnerability | |
| CVE-2024-38130 | Windows DirectX Remote Code Execution Vulnerability | |
| CVE-2024-38131 | Microsoft Windows DirectX Graphics Kernel Subsystem Remote Code Execution Vulnerability | |
| CVE-2024-38133 | Windows D3D12 Remote Code Execution Vulnerability | |
| CVE-2024-38135 | Microsoft Windows Domain Controller Remote Code Execution Vulnerability | |
| CVE-2024-38137 | Windows Error Reporting Service Remote Code Execution Vulnerability | |
| CVE-2024-38139 | Windows Kernel Local Elevation of Privilege Vulnerability | |
| CVE-2024-38140 | Windows USB Mass Storage Class Driver Elevation of Privilege Vulnerability | |
| CVE-2024-38142 | Windows AppX Deployment Service Elevation of Privilege Vulnerability | |
| CVE-2024-38145 | Windows Kernel Remote Code Execution Vulnerability | |
| CVE-2024-38149 | Windows Management Infrastructure Remote Code Execution Vulnerability | |
| CVE-2024-38152 | Microsoft Windows Bluetooth Remote Code Execution Vulnerability | |
| CVE-2024-38154 | Microsoft Windows Media Player Remote Code Execution Vulnerability | |
| CVE-2024-38157 | Windows SMB Server Remote Code Execution Vulnerability | |
| CVE-2024-38159 | Microsoft Windows Kernel Remote Code Execution Vulnerability | |
| CVE-2024-38163 | Windows Network Data Usage Monitoring Helper Remote Code Execution Vulnerability | |
| CVE-2024-38167 | Microsoft Windows ALPC Remote Code Execution Vulnerability | |
Appendix C: Affected Products
Here is a compilation of July’s patches categorized by product families and arranged by severity levels. The lists are also categorized by CVE numbers. For patches that impact multiple product families, they are listed individually for each relevant family.
Windows (86 CVEs)
| Critical Impact | |||
| CVE-2024-38060 | Microsoft Windows Codecs Library Remote Code Execution Vulnerability | ||
| CVE-2024-38074 | Windows Remote Desktop Licensing Service Remote Code Execution Vulnerability | ||
| CVE-2024-38076 | Windows Remote Desktop Licensing Service Remote Code Execution Vulnerability | ||
| CVE-2024-38077 | Windows Remote Desktop Licensing Service Remote Code Execution Vulnerability | ||
| Significant Impact | |||
| CVE-2024-21417 | Windows Text Services Framework Elevation of Privileges Vulnerability | ||
| CVE-2024-26184 | Secure Boot Security Feature Bypass Vulnerability | ||
| CVE-2024-28899 | Secure Boot Security Feature Bypass Vulnerability | ||
| CVE-2024-30013 | Windows MultiPoint Services Remote Code Execution Vulnerability | ||
| CVE-2024-30071 | Windows Remote Access Connection Manager Information Disclosure Vulnerability | ||
| CVE-2024-30079 | Windows Remote Access Connection Manager Elevation of Privilege Vulnerability | ||
| CVE-2024-30081 | Windows NTLM Spoofing Vulnerability | ||
| CVE-2024-30098 | Windows Cryptographic Services Security Feature Bypass Vulnerability | ||
| CVE-2024-30105 | .NET Denial of Service Vulnerability | ||
| CVE-2024-35264 | ASP.NET Remote Code Execution Vulnerability | ||
| CVE-2024-35270 | Windows iSCSI Service Denial of Service Vulnerability | ||
| CVE-2024-37969 | Secure Boot Security Feature Bypass Vulnerability | ||
| CVE-2024-37970 | Secure Boot Security Feature Bypass Vulnerability | ||
| CVE-2024-37971 | Secure Boot Security Feature Bypass Vulnerability | ||
| CVE-2024-37972 | Secure Boot Security Feature Bypass Vulnerability | ||
| CVE-2024-37973 | Secure Boot Security Feature Bypass Vulnerability | ||
| CVE-2024-37974 | Secure Boot Security Feature Bypass Vulnerability | ||
| CVE-2024-37975 | Secure Boot Security Feature Bypass Vulnerability | ||
| CVE-2024-37977 | Secure Boot Security Feature Bypass Vulnerability | ||
| CVE-2024-37978 | Secure Boot Security Feature Bypass Vulnerability | ||
| CVE-2024-37981 | Secure Boot Security Feature Bypass Vulnerability | ||
| CVE-2024-37984 | Secure Boot Security Feature Bypass Vulnerability | ||
| CVE-2024-37986 | Secure Boot Security Feature Bypass Vulnerability | ||
| CVE-2024-37987 | Secure Boot Security Feature Bypass Vulnerability | ||
| CVE-2024-37988 | Secure Boot Security Feature Bypass Vulnerability | ||
| CVE-2024-37989 | Secure Boot Security Feature Bypass Vulnerability | ||
| CVE-2024-38010 | Secure Boot Security Feature Bypass Vulnerability | ||
| CVE-2024-38011 | Secure Boot Security Feature Bypass Vulnerability | ||
| CVE-2024-38013 | Microsoft Windows Server Backup Elevation of Privilege Vulnerability | ||
| CVE-2024-38015 | Windows Remote Desktop Gateway (RD Gateway) Denial of Service Vulnerability | ||
| CVE-2024-38017 | Microsoft Message Queuing Information Disclosure Vulnerability | ||
| CVE-2024-38019 | Microsoft Windows Performance Data Helper Library Remote Code Execution Vulnerability | ||
| CVE-2024-38022 | Windows Image Acquisition Elevation of Privilege Vulnerability | ||
| CVE-2024-38025 | Windows Performance Monitor Remote Code Execution Vulnerability | ||
| CVE-2024-38027 | Windows Line Printer Daemon Service Denial of Service Vulnerability | ||
| CVE-2024-38028 | Windows Performance Monitor Remote Code Execution Vulnerability | ||
| CVE-2024-38030 | Windows Themes Spoofing Vulnerability | ||
| CVE-2024-38031 | Windows Online Certificate Status Protocol (OCSP) Server Denial of Service Vulnerability | ||
| CVE-2024-38032 | Windows Graphics Component Remote Code Execution Vulnerability | ||
| CVE-2024-38033 | PowerShell Elevation of Privilege Vulnerability | ||
| CVE-2024-38034 | Windows Filtering Platform Elevation of Privilege Vulnerability | ||
| CVE-2024-38041 | Windows Kernel Information Disclosure Vulnerability | ||
| CVE-2024-38043 | PowerShell Elevation of Privilege Vulnerability | ||
| CVE-2024-38044 | DHCP Server Service Remote Code Execution Vulnerability | ||
| CVE-2024-38047 | PowerShell Elevation of Privilege Vulnerability | ||
| CVE-2024-38048 | Windows Network Driver Interface Specification (NDIS) Denial of Service Vulnerability | ||
| CVE-2024-38049 | Windows Distributed Transaction Coordinator Remote Code Execution Vulnerability | ||
| CVE-2024-38050 | Windows Workstation Service Elevation of Privilege Vulnerability | ||
| CVE-2024-38051 | Windows Graphics Component Remote Code Execution Vulnerability | ||
| CVE-2024-38052 | Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability | ||
| CVE-2024-38053 | Windows Layer-2 Bridge Network Driver Remote Code Execution Vulnerability | ||
| CVE-2024-38054 | Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability | ||
| CVE-2024-38055 | Microsoft Windows Codecs Library Information Disclosure Vulnerability | ||
| CVE-2024-38056 | Exposed Vulnerability in Microsoft Windows Codecs Library | ||
| Identifier: CVE-2024-38057 | Security Flaw Leading to Elevation of Privileges in Microsoft Streaming Service | ||
| Identifier: CVE-2024-38058 | Weakness in BitLocker Security Feature Allowing Bypass | ||
| Identifier: CVE-2024-38059 | Flaw Allowing Elevation of Privileges in Win32k System | ||
| Identifier: CVE-2024-38061 | Security Vulnerability Enabling Privilege Escalation in Active Directory Certificate Services | ||
| Identifier: CVE-2024-38062 | Potential Elevation of Privileges in Windows Clip Service | ||
| Identifier: CVE-2024-38064 | Information Disclosure Vulnerability in Windows TCP/IP System | ||
| Identifier: CVE-2024-38065 | Method to Bypass Secure Boot Feature | ||
| Identifier: CVE-2024-38066 | Elevation of Privileges Flaw in Windows Win32k System | ||
| Identifier: CVE-2024-38067 | Denial of Service Vulnerability in Windows Online Certificate Status Protocol (OCSP) Server | ||
| Identifier: CVE-2024-38068 | Denial of Service Vulnerability Found in Windows Online Certificate Status Protocol (OCSP) Server | ||
| Identifier: CVE-2024-38069 | Feature Bypass Vulnerability in Windows Enroll Engine | ||
| Identifier: CVE-2024-38070 | Security Feature Bypass Vulnerability in Windows LockDown Policy (WLDP) | ||
| Identifier: CVE-2024-38071 | Denial of Service Vulnerability in Windows Remote Desktop Licensing Service | ||
| Identifier: CVE-2024-38072 | Denial of Service Vulnerability Discovered in Windows Remote Desktop Licensing Service | ||
| Identifier: CVE-2024-38073 | Windows Remote Desktop Licensing Service Affected by Denial of Service Vulnerability | ||
| Identifier: CVE-2024-38078 | Vulnerability Allowing Remote Code Execution in XBox Wireless Adapter | ||
| Identifier: CVE-2024-38079 | Elevation of Privileges Vulnerability in Windows Graphics Component | ||
| Identifier: CVE-2024-38080 | Potential Elevation of Privileges in Windows Hyper-V System | ||
| Identifier: CVE-2024-38081 | Security Vulnerability Leading to Elevation of Privileges in .NET, .NET Framework, and Visual Studio | ||
| Identifier: CVE-2024-38085 | Elevation of Privileges Vulnerability in Windows Win32 Kernel Subsystem | ||
| Identifier: CVE-2024-38091 | Den… | VUL-2024-37328 | Vulnerability in Microsoft OLE DB Driver for SQL Server allowing Remote Code Execution |
| VUL-2024-37329 | Vulnerability in Microsoft OLE DB Driver for SQL Server allowing Remote Code Execution | ||
| VUL-2024-37330 | Vulnerability in Microsoft OLE DB Driver for SQL Server allowing Remote Code Execution | ||
| VUL-2024-37331 | Vulnerability in Microsoft OLE DB Driver for SQL Server allowing Remote Code Execution | ||
| VUL-2024-37332 | Vulnerability in Microsoft OLE DB Driver for SQL Server allowing Remote Code Execution | ||
| VUL-2024-37333 | Vulnerability in Microsoft OLE DB Driver for SQL Server allowing Remote Code Execution | ||
| VUL-2024-37334 | Vulnerability in Microsoft OLE DB Driver for SQL Server allowing Remote Code Execution | ||
| VUL-2024-37336 | Vulnerability in Microsoft OLE DB Driver for SQL Server allowing Remote Code Execution | ||
| VUL-2024-38087 | Vulnerability in Microsoft OLE DB Driver for SQL Server allowing Remote Code Execution | ||
| VUL-2024-38088 | Vulnerability in Microsoft OLE DB Driver for SQL Server allowing Remote Code Execution | ||
Azure (5 Vulnerabilities)
| Severity level: Important | |
| VUL-2024-35261 | Vulnerability in Azure Network Watcher VM Extension allowing Elevation of Privilege |
| VUL-2024-35266 | Vulnerability in Azure DevOps Server allowing Spoofing |
| VUL-2024-35267 | Vulnerability in Azure DevOps Server allowing Spoofing |
| VUL-2024-38086 | Vulnerability in Azure Kinect SDK allowing Remote Code Execution |
| VUL-2024-38092 | Vulnerability in Azure CycleCloud allowing Elevation of Privilege |
SharePoint (4 Vulnerabilities)
| Severity level: Critical | |
| VUL-2024-38023 | Vulnerability in Microsoft SharePoint Server allowing Remote Code Execution |
| Severity level: Important | |
| VUL-2024-32987 | Vulnerability in Microsoft SharePoint Server allowing Information Disclosure |
| VUL-2024-38024 | Vulnerability in Microsoft SharePoint Server allowing Remote Code Execution |
| VUL-2024-38094 | Vulnerability in Microsoft SharePoint allowing Remote Code Execution |
Office 365 (2 Vulnerabilities)
| Severity level: Important | |
| VUL-2024-38021 | Vulnerability in Microsoft Office allowing Remote Code Execution |
| Severity level: Moderate | |
| VUL-2024-38020 | Vulnerability in Microsoft Outlook allowing Spoofing |
Microsoft Dynamics 365 (on-premises)
| Severity level: Important | |
| VUL-2024-30061 | Vulnerability in Microsoft Dynamics 365 (On-Premises) allowing Information Disclosure |
Microsoft Defender for IoT (1 Vulnerability)
| Severity level: Important | |
| VUL-2024-38089 | Vulnerability in Microsoft Defender for IoT allowing Elevation of Privilege |





