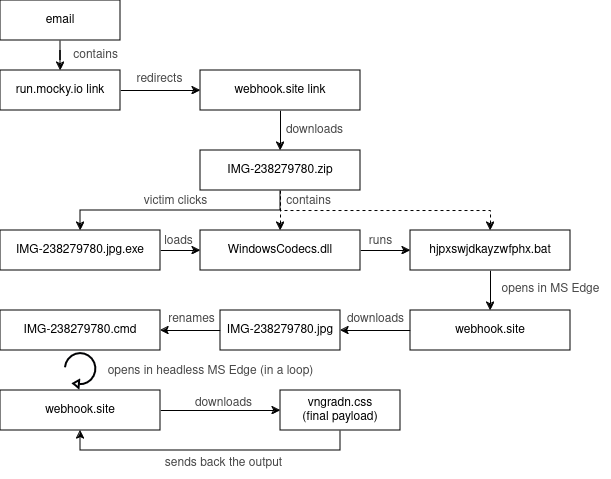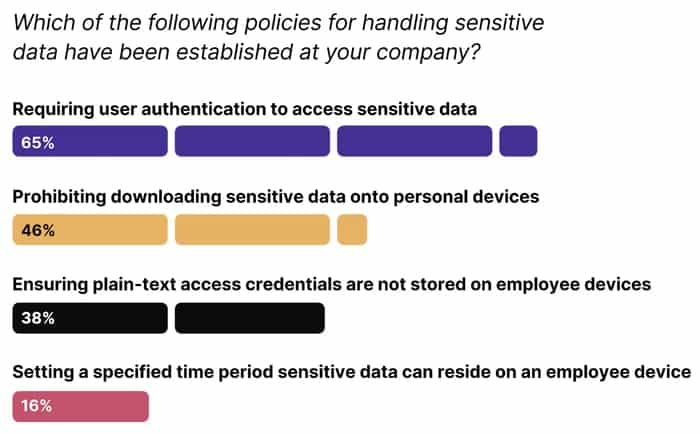


Graham
Cluley
Security
News
is
sponsored
this
week
by
the
folks
at
Kolide.
Thanks
to
the
great
team
there
for
their
support!
Here’s
an
uncomfortable
fact:
at
most
companies,
employees
can
download
sensitive
company
data
onto
any
device,
keep
it
there
forever,
and
never
even
know
that
they’re
doing
something
wrong.
Kolide’s
new
report,
“The
State
of
Sensitive
Data”,
shines
a
light
on
an
area
of
security
that
is
often
ignored,
but
is
nevertheless
a
massive
hole
in
many
companies’
Zero
Trust
fortress.


These
findings
are
particularly
alarming
given
the
overall
state
of
device
security.
IT
teams
routinely
struggle
to
enforce
timely
OS
updates
and
patch
management,
meaning
that
end
users
are
storing
your
most
sensitive
data–things
like
customer
records,
confidential
IP,
and
plain-text
access
credentials–on
devices
that
are
vulnerable
to
attack.
This
problem
has
gone
unaddressed
because
until
now
there
hasn’t
been
a
good
solution
for
it.
MDM
solutions
are
too
blunt
an
instrument
for
dealing
with
sensitive
data,
and
DLP
tools
are
too
extreme
and
invasive
for
most
companies.
After
all,
you’re
not
trying
to
ban
downloads
together,
nor
regard
every
download
as
suspicious.
You’re
just
trying
to
make
sure
employees
aren’t
keeping
data
for
longer
than
they
need
or
keeping
it
on
an
unmanaged
or
unsecure
device.
Kolide
offers
a
more
nuanced
approach
to
setting
and
enforcing
sensitive
data
policies.
Our
premise
is
simple:
if
an
employee’s
device
is
out
of
compliance,
it
can’t
access
your
apps.
Kolide
lets
admins
run
queries
to
detect
sensitive
data,
flag
devices
that
have
violated
policies,
and
enforce
OS
and
browser
updates
so
vulnerable
devices
aren’t
accessing
data.
Our
unique
approach
makes
device
compliance
part
of
the
authentication
process.
If
a
device
isn’t
compliant,
users
can’t
log
in
to
their
cloud
apps
until
they’ve
fixed
the
problem.
But
instead
of
creating
more
work
for
IT,
Kolide
provides
instructions
so
users
can
get
unblocked
on
their
own.
To
learn
more
and
see
our
product
in
action,
visit
kolide.com.
If
you’re
interested
in
sponsoring
my
site
for
a
week,
and
reaching
an
IT-savvy
audience
that
cares
about
computer
security,
you
can
find
more
information
here.