China-linked
Earth
Preta cyberespionage
group
has
been
observed
adopting
new
techniques
to
bypass
security
solutions.
Trend
Micro
researchers
reported
that
the
China-linked
Earth
Preta
group
(aka
Mustang
Panda)
is
actively
changing
its
tools,
tactics,
and
procedures
(TTPs)
to
bypass
security
solutions.
Earth
Preta,
also
known
as
“RedDelta”
or
“Bronze
President,”
has
been
active
since
at
least
2012,
it
targeted American and European entities
such
as
government
organizations,
think
tanks, NGOs,
and
even Catholic
organizations at
the
Vatican.
Past
campaigns
were
focused
on
Asian
countries,
including
Taiwan,
Hong
Kong, Mongolia,
Tibet, and
Myanmar.
In
recent
campaigns,
threat
actors
used
European
Union
reports
on
the
conflict
in
Ukraine
and
Ukrainian
government
reports
as
lures.
Upon
opening
the
reports,
the
infection
process
starts
leading
to
the
deployment
of
malware
on
the
victim’s
system.
In
a
recent
campaign
analyzed
by
Trend
Micro,
the
threat
actors
used
spear-phishing
emails
and
Google
Drive
links
as
attack
vectors.
A
deep
investigation
into
the
campaign
revealed
several
undisclosed
malware
and
interesting
data
exfiltration
tools
used
by
the
group.
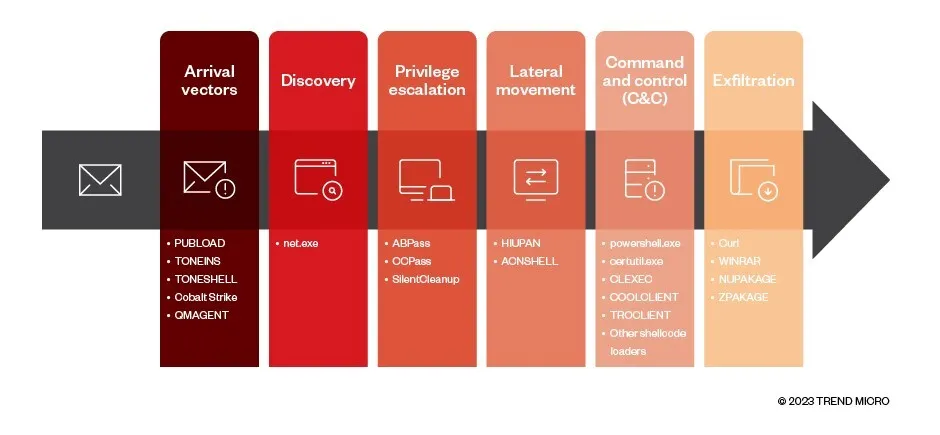
The
researchers
categorized
the
infection
chain
into
six
stages:
arrival
vectors,
discovery,
privilege
escalation,
lateral
movement,
command
and
control
(C&C)
and
exfiltration,
respectively.

full
infection
chain
(Trend
Micro)
The
attackers
used
DLL
sideloading,
shortcut
links,
and
fake
file
extensions
in
the
first
part
of
the
attacks,
the
researchers
noticed
that
starting
in
October
and
November
2022,
the
group
began
changing
their
TTPs
to
deploy
the
TONEINS,
TONESHELL,
and
PUBLOAD
malware.
TONEINS
and
TONESHELL
malware
was
downloaded
from
the
Google
Drive
link
embedded
in
the
body
of
spear-phishing
messages.
To
bypass
email-scanning
services,
the
threat
actors
started
embedding
the
Google
Drive
link
in
a
lure
document.
The
link
points
to
a
password-protected
archive,
the
document
also
includes
the
password.
“Based
on
our
observations,
Earth
Preta
tends
to
hide
malicious
payloads
in
fake
files,
disguising
them
as
legitimate
ones
—
a
technique
that
has
been
proven
effective
for
avoiding
detection.
As
for
privilege
escalation,
the
threat
actors
tend
to
reuse
codes
copied
from
open-source
repositories.”
states
the
report
published
by
Trend
Micro.
“Meanwhile,
they
developed
customized
toolsets
designed
to
collect
confidential
documents
in
the
exfiltration
stage.”
Once
gained
a
foothold
in
the
target
network,
the
attackers
start
the
discovery
and
privileges
escalation
phases.
In
the
privilege
escalation
phase
the
threat
actors
used
several
tools
for
UAC
bypass
in
Windows
10
such
as
ABPASS
and
CCPASS.
During
the
lateral
movement
phase,
Earth
Preta
used
malware
such
as
HIUPAN
and
ACNSHELL
being
used
to
install
themselves
to
removable
disks
and
create
a
reverse
shell.
The
group
used
several
tools
and
commands
for
the
C2
stage,
such
as
certutil.exe to
download
the
legitimate
WinRAR
binary
and
PowerShell
to
download
multiple
malicious
archives
from
a
remote
server
(103[.]159[.]132[.]181).
The
group
also
used
the
CLEXEC
backdoor,
the
COOLCLIENT
and
TROCLIENT
implants,
and
the PlugX
malware.
The
report
details
the
execution
flow
for
each
of
the
above
malware.
The
threat
actors
also
used
highly
customized
tools
for
exfiltration,
such
as
NUPAKAGE
and
ZPAKAGE,
both
used
to
steal
Office
documents.
“Earth
Preta
is
a
capable
and
organized
threat
actor
that
is
continuously
honing
its
TTPs,
strengthening
its
development
capabilities,
and
building
a
versatile
arsenal
of
tools
and
malware,”
concludes
the
report.
Follow
me
on
Twitter:
@securityaffairs
and
Facebook
and
Mastodon
(SecurityAffairs –
hacking,
Earth
Preta)






