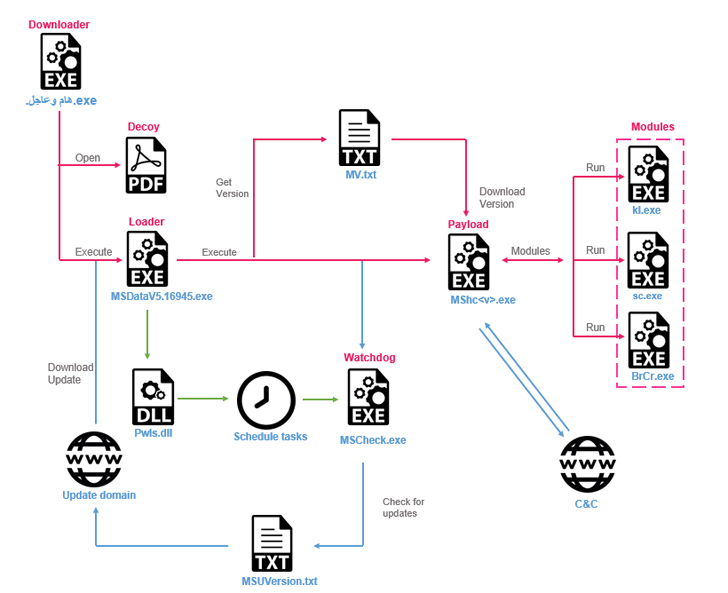
A
new
custom
backdoor
dubbed
Stealth
Soldier
has
been
deployed
as
part
of
a
set
of
highly-targeted
espionage
attacks
in
North
Africa.
“Stealth
Soldier
malware
is
an
undocumented
backdoor
that
primarily
operates
surveillance
functions
such
as
file
exfiltration,
screen
and
microphone
recording,
keystroke
logging
and
stealing
browser
information,”
cybersecurity
company
Check
Point
said
in
a
technical
report.
The
ongoing
operation
is
characterized
by
the
use
of
command-and-control
(C&C)
servers
that
mimic
sites
belonging
to
the
Libyan
Ministry
of
Foreign
Affairs.
The
earliest
artifacts
associated
with
the
campaign
date
back
to
October
2022.
The
attacks
commence
with
potential
targets
downloading
bogus
downloader
binaries
that
are
delivered
via
social
engineering
attacks
and
act
as
a
conduit
for
retrieving
Stealth
Soldier,
while
simultaneously
displaying
a
decoy
empty
PDF
file.
The
custom
modular
implant,
which
is
believed
to
be
used
sparingly,
enables
surveillance
capabilities
by
gathering
directory
listings
and
browser
credentials,
logging
keystrokes,
recording
microphone
audio,
taking
screenshots,
uploading
files,
and
running
PowerShell
commands.
“The
malware
uses
different
types
of
commands:
some
are
plugins
that
are
downloaded
from
the
C&C
and
some
are
modules
inside
the
malware,”
Check
Point
said,
adding
the
discovery
of
three
versions
of
Stealth
Soldier
indicates
that
it’s
being
actively
maintained
by
its
operators.
Some
of
the
components
are
no
longer
available
for
retrieval,
but
the
screen
capture
and
browser
credential
stealer
plugins
are
said
to
have
been
inspired
by
open
source
projects
available
on
GitHub.
UPCOMING
WEBINAR
🔐
Mastering
API
Security:
Understanding
Your
True
Attack
Surface
Discover
the
untapped
vulnerabilities
in
your
API
ecosystem
and
take
proactive
steps
towards
ironclad
security.
Join
our
insightful
webinar!
What’s
more,
the
Stealth
Soldier
infrastructure
exhibits
overlaps
with
infrastructure
associated
with
another
phishing
campaign
dubbed
Eye
on
the
Nile,
which
targeted
Egyptian
journalists
and
human
rights
activists
in
2019.
The
development
signals
the
“first
possible
re-appearance
of
this
threat
actor”
since
then,
suggesting
the
group
is
geared
towards
surveillance
against
Egyptian
and
Libyan
targets.
“Given
the
modularity
of
the
malware
and
the
use
of
multiple
stages
of
infection,
it
is
likely
that
the
attackers
will
continue
to
evolve
their
tactics
and
techniques
and
deploy
new
versions
of
this
malware
in
the
near
future,”
Check
Point
said.