State-Sponsored Cyber Espionage by China Aims at Government Entities in Southeast Asia
A Southeast Asian government entity, unnamed but of high profile, has become the target of a sophisticated and prolonged state-backed cyber espionage campaign known as Crimson Palace.
A report shared with The Hacker News by Sophos researchers Paul Jaramillo, Morgan Demboski, Sean Gallagher, and Mark Parsons revealed that the primary objective of the operation was to ensure ongoing access to the target network for cyberespionage in alignment with Chinese state objectives.
The operation involved activities such as breaching critical IT systems, gathering intelligence on specific users, acquiring sensitive military and technological data, and deploying various malware implants for command-and-control (C2) communications.
Although the identity of the government entity was not disclosed, the researchers hinted at the likelihood of it being the Philippines, a country with historical territorial disputes with China in the South China Sea, and also a past target of Chinese state-sponsored threat actors like Mustang Panda.
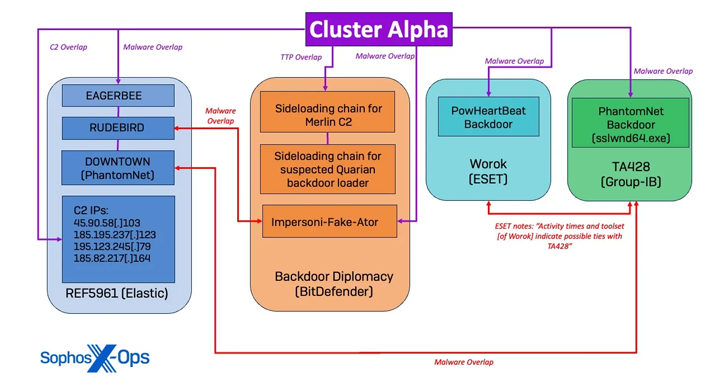
Cluster Alpha, Cluster Bravo, and Cluster Charlie are the three intrusion clusters making up the Crimson Palace campaign, each displaying unique characteristics with ties to other known threat actors like BackdoorDiplomacy, REF5961, Worok, TA428, and more.
The researchers suspect that these cluster activities are part of an orchestrated effort led by a single entity.
Distinctive features of the attack include the use of previously undocumented malware such as PocoProxy, an updated version of EAGERBEE, and the presence of known malware families like NUPAKAGE, PowHeartBeat, RUDEBIRD, DOWNTOWN (PhantomNet), and EtherealGh0st (also known as CCoreDoor).
The campaign’s tactics included extensive use of DLL side-loading and innovative methods to fly under the radar, such as manipulating AV software for sideloading and experimenting with evasion tactics to enhance payload execution efficiency.
Further examination indicated that Cluster Alpha focused on mapping server subnets and gathering Active Directory infrastructure information, while Cluster Bravo emphasized leveraging valid accounts for lateral movement and deploying EtherealGh0st.
Actions linked with Group Charlie, conducted over an extended duration, involved utilizing PocoProxy to establish continuity on compromised systems and deploying HUI Loader, a bespoke loader employed by several actors associated with China, to distribute Cobalt Strike.
“The identified clusters indicate the activities of more than one distinct entity collaborating with shared goals,” as per the findings. “The observed clusters demonstrate the operations of a single unit having a wide range of tools, varied infrastructure, and multiple operators.”
This revelation coincides with cybersecurity company Yoroi outlining assaults orchestrated by the APT41 actor (also known as Brass Typhoon, HOODOO, and Winnti) targeting entities in Italy with a version of the PlugX (also known as Destroy RAT and Korplug) malware referred to as KEYPLUG.
“Developed in C++ and operational since at least June 2021, KEYPLUG has versions for both Windows and Linux platforms,” Yoroi stated. “It supports multiple network protocols for command and control (C2) communication, including HTTP, TCP, KCP over UDP, and WSS, making it a powerful asset in APT41’s cyber attack toolbox.”
This development follows a warning from the Canadian Centre for Cyber Security regarding escalating intrusions from Chinese state-affiliated hacking aimed at penetrating government, critical infrastructure, and research and development sectors.
“[People’s Republic of China] cyber threat operations surpass those of other state-backed cyber threats in quantity, complexity, and the scope of targets,” the agency highlighted, noting their use of compromised small office and home office (SOHO) routers and living-off-the-land techniques for cyber threat actions while evading detection.










