This supplementary section of our Annual Threat Report presents additional data and insights into the tools utilized by hackers targeting small and medium-sized enterprises (SMEs). To get a comprehensive view of the threat landscape confronting SMEs, refer to our primary report.
Appendix Details:
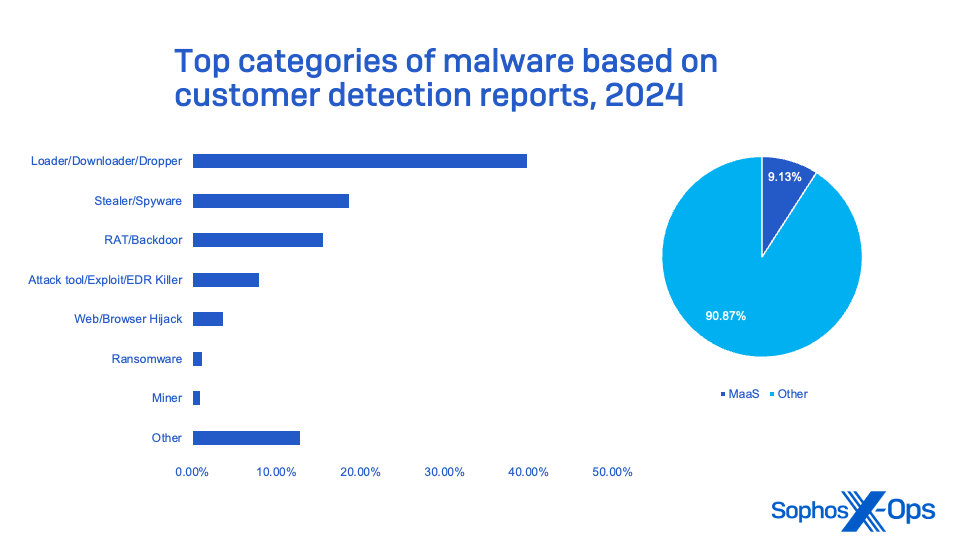
Most commonly-seen types of malware
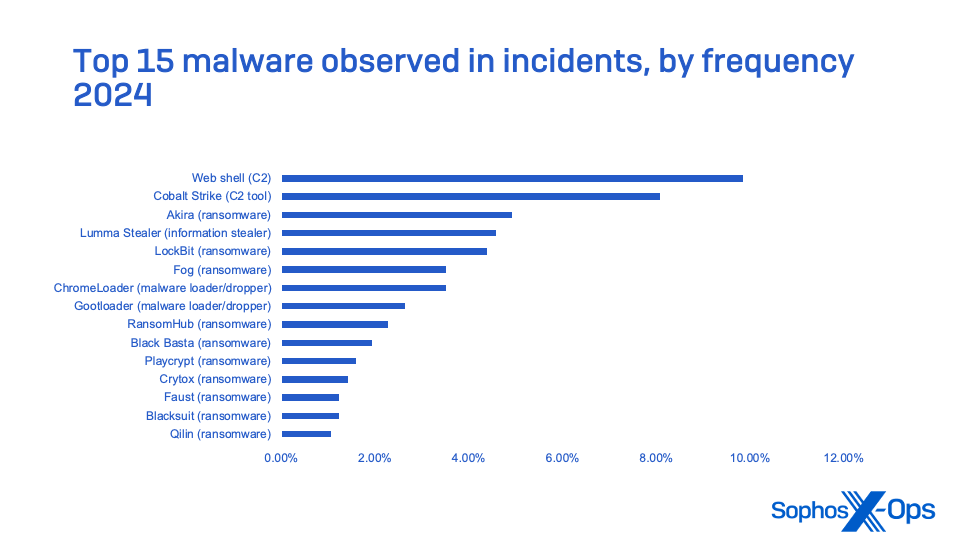
SMEs encounter a wide array of data security threats, some of which could serve as precursors to ransomware assaults or lead to other compromises of confidential data. Ransomware stands out as the predominant form of malware identified in Sophos MDR and Sophos Incident Response cases dating back to 2024, with the top 10 types comprising more than 25% of all incidents recorded by MDR and IR during the year. However, these did not encompass the complete scenario, as nearly 60% of MDR incidents featured threats unrelated to ransomware.
Figure 13: Breakdown of the most frequently observed malware categories in 2024, sourced from customer detection reports
Tools such as command-and-control systems, malware loaders, remote administration software, and information-stealing malware constitute the majority of the malevolent programs aimed at small businesses (apart from ransomware). These tools, some of which do not fall under the strict definition of malware, are employed in facilitating ransomware and other cybercriminal assaults.
Among the top 10 tools and malware identified in Sophos MDR and IR incidents, only one does not align with this trend: XMRig. This cryptocurrency-mining malware is commonly utilized to passively generate profits prior to its access being sold or exploited by a ransomware perpetrator.


Multipurpose tools
A consistent trend from earlier years is the widespread adoption of commercially available, freeware, and open-source software by hackers to execute ransomware attacks and other illicit activities. In Sophos MDR, these tools are termed as “multipurpose tools,” as they could legitimately exist on networks but are frequently abused by cybercriminals for nefarious ends.
These multipurpose tools differ from “living-off-the-land binaries” (LOLBins) by virtue of being complete applications that are deployed and leveraged as intended by cyber malefactors, as opposed to system-supplied components and scripting engines. Among the tools falling into this category, some are explicitly designed for security testing and are part of red teaming activities—Impacket and Mimikatz being open-source tools created specifically for security researchers. Others, like SoftPerfect Network Scanner and Advanced IP Scanner, are crafted as utilities for network administrators but are misused by cybercriminals for identifying networked devices and open network ports.



Aggression utilities
Data pilferers

The playbook of a middleman, providing keys, biscuits, and other details that can be utilized for financial deceit, corporate email manipulation, and malware assaults, amid alternative strategies.
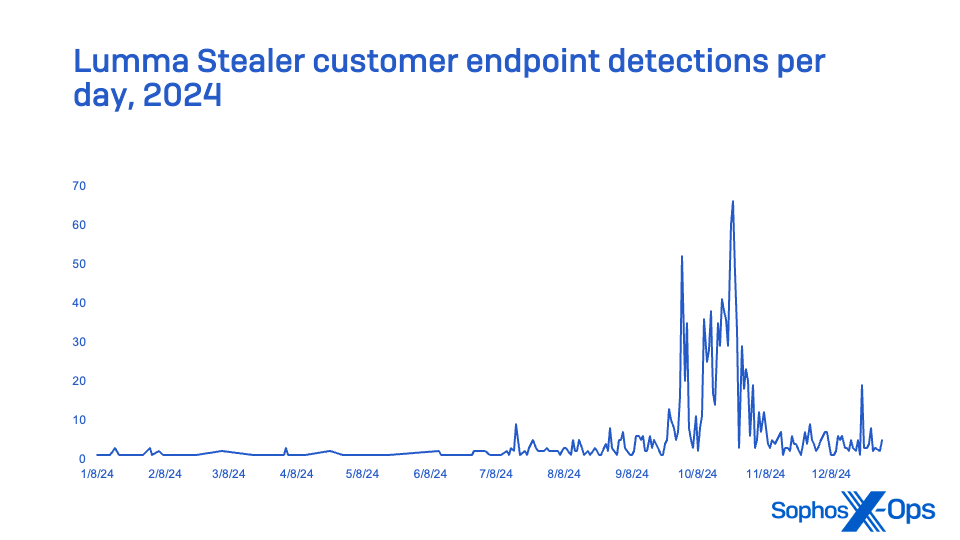
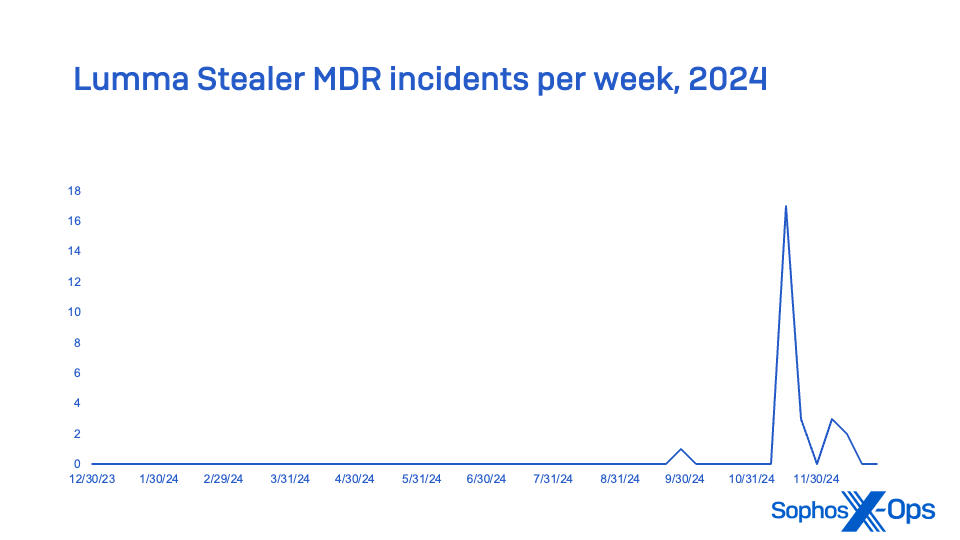
Lumma Stealer, traded on Russian-speaking channels as a Malware-as-a-Service (MaaS), emerged as the most prevalent information snatcher in MDR occurrences and second in comprehensive endpoint detection notifications. A significant Lumma Stealer campaign that commenced in October resulted in it becoming the most documented snatcher in the final quarter of 2024, surpassing last year’s MaaS snatcher champion RaccoonStealer (which unveiled a fresh edition in 2024 post its framework disturbance) and overshadowing Strela Stealer by the conclusion of the year (which skyrocketed through the ranks in 2023; hitting its peak early in 2024 but waning in the latter part of the year). No MDR incidents monitored in 2024 involved Strela Stealer.
Figure 21: Lumma Stealer behavior in 2024 as seen in client endpoint identifications

Initially traced in August 2022, Lumma Stealer is speculated to be a descendant of Mars Stealer, another data snatcher allegedly of Russian lineage. This snatcher predominantly aims at cryptocurrency wallets, browser session biscuits, browser dual-factor authentication extensions, stored File Transfer Protocol server addresses and credentials, alongside additional user and system details.
Similar to some other data snatchers (such as Raccoon Stealer), Lumma Stealer can also be employed to distribute additional malware—either through initiating executables or PowerShell scripts, or by loading malevolent DLLs from its particular process. Typically, Lumma Stealer is dispensed from a compromised website (frequently a counterfeit CAPTCHA web page) as a download that victims are redirected to via malvertising.
Lumma Stealer is usually related to broader cybercriminal actions. Another MaaS snatcher retailed on Russian-language forums, StealC, displayed a significantly higher correlation to ransomware occurrences. Launched in January 2023, it has been tagged by investigators as a RaccoonStealer and Vidar replica.
Conspicuous regionally is Mispadu Stealer, which persists in targeting Latin America (specifically Mexico). In the second quarter of 2024, it ranked as the second-most noticed snatcher, trailing right behind Strela Stealer, with 74% of those detections originating from Mexico. It has been observed utilizing malicious web and search ads, predominantly masquerading as web promotions for McDonald’s.
Top encrypting threat actors


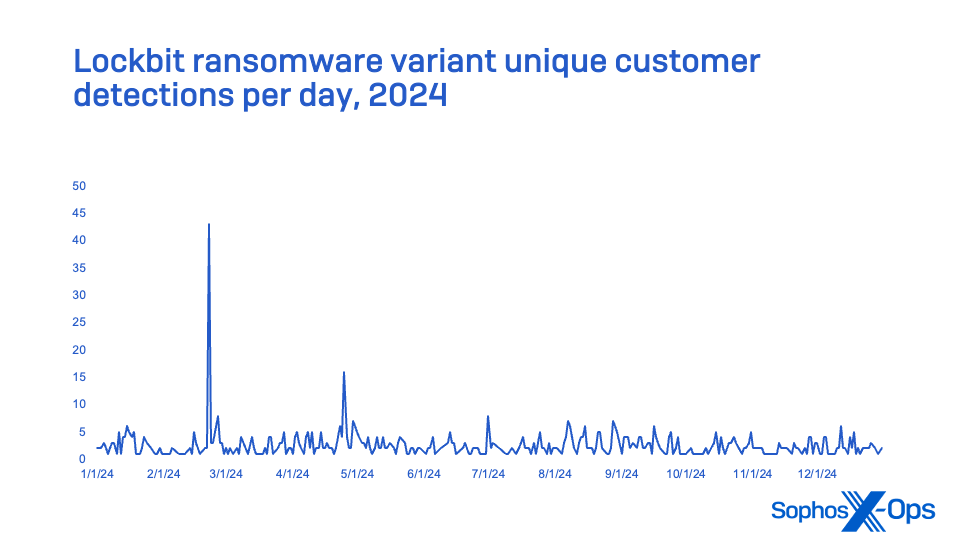
LockBit, in a way
The most-noticed ransomware group in 2024 was LockBit, however-Due to the ransomware gang that gave rise to it. In February 2024, law enforcement authorities from the US and UK stated they had disrupted the LockBit gang by taking control of the ransomware-as-a-service gang’s servers, detaining two of its members, and bringing charges against another in an indictment. Following this disruption, several offshoots based on the exposed LockBit 3.0 code surfaced in the wild, resulting in a surge of LockBit identifications in early 2024. Nonetheless, by March, detections decreased significantly with a minor uptick in April and early May (although the LockBit syndicate may potentially resurface).
The factions employing LockBit 3.0 frequently utilized EDR terminators and other malware tactics in an effort to deactivate endpoint protection. Often, their initial entry was secured through compromised VPN accounts (partly due to vulnerabilities in the VPN devices themselves), or through the exploitation of credentials acquired from unmanaged devices for remote access.
Akira and Fog
In terms of actual occurrences, the Akira ransomware-as-a-service took the lead in 2024, eventually filling the gap left by LockBit. Initially detected in 2022, Akira assaults intensified later in 2023. Throughout 2024, the group and its affiliates remained consistently operational, peaking in August when Akira represented 17% of the ransomware incidents reported by Sophos clients—doubling from its standing in the initial two quarters of the year. By the end of the year, it still made up 9% of the ransomware detection reports.
There were instances where affiliates linked to Akira were observed by Sophos also deploying other ransomware variations, such as Fog, Frag and Megazord. These attackers (like those mentioned in STAC5881) frequently concentrated on exploiting VPNs for initial access. Typically, Akira’s targets had VPNs lacking multifactor authentication, or had improperly configured VPN gateways that allowed the attackers to gain entry with pilfered credentials or brute force attacks.
While Akira continues to be active, Fog ransomware has at times been utilized as a substitute by affiliates previously associated with Akira, attributing to its position among the top three ransomware families encountered in MDR and IR incidents.
RansomHub
RansomHub emerged as another prominent player in ransomware events in 2024. Despite tying for sixth place in overall identifications, RansomHub was the fourth most frequently observed ransomware variant in actual MDR and IR incidents.
Between February and August 2024, as outlined in a StopRansomware advisory by the Cybersecurity and Infrastructure Security Agency, RansomHub had “encrypted and exfiltrated data from at least 210 victims.” A significant portion of Sophos MDR and IR cases linked to RansomHub surfaced in the latter part of the year, intensifying in November.
A majority of RansomHub attacks involved the misuse of RDP alongside other authorized remote desktop tools, such as AnyDesk. In specific reported cases, initial access was achieved through the exploitation of the seven-year-old Windows SMB Remote Code Execution Vulnerability (CVE-2017-1444), although this was not observed in the Sophos MDR and IR cases reflected in our statistics. Initial access vectors identified by Sophos X-Ops in RansomHub cases comprised of abusing externally facing Microsoft SQL Servers for command execution, exploiting open RDP and Remote Desktop Web access, and compromising unmanaged devices.