Sharp Panda Using New Soul Framework Version to Target Southeast Asian Governments

High-profile
government
entities
in
Southeast
Asia
are
the
target
of
a
cyber
espionage
campaign
undertaken
by
a
Chinese
threat
actor
known
as
Sharp
Panda
since
late
last
year.
The
intrusions
are
characterized
by
the
use
of
a
new
version
of
the
Soul
modular
framework,
marking
a
departure
from
the
group’s
attack
chains
observed
in
2021.
Israeli
cybersecurity
company
Check
Point
said
the
“long-running”
activities
have
historically
singled
out
countries
such
as
Vietnam,
Thailand,
and
Indonesia.
Sharp
Panda
was
first
documented
by
the
firm
in
June
2021,
describing
it
as
a
“highly-organized
operation
that
placed
significant
effort
into
remaining
under
the
radar.”
Interestingly,
the
use
of
the
Soul
backdoor
was
detailed
by
Broadcom’s
Symantec
in
October
2021
in
connection
to
an
unattributed
espionage
operation
targeting
defense,
healthcare,
and
ICT
sectors
in
Southeast
Asia.
The
implant’s
origins,
according
to
research
published
by
Fortinet
FortiGuard
Labs
in
February
2022,
date
as
far
back
as
October
2017,
with
the
malware
repurposing
code
from
Gh0st
RAT
and
other
publicly
available
tools.
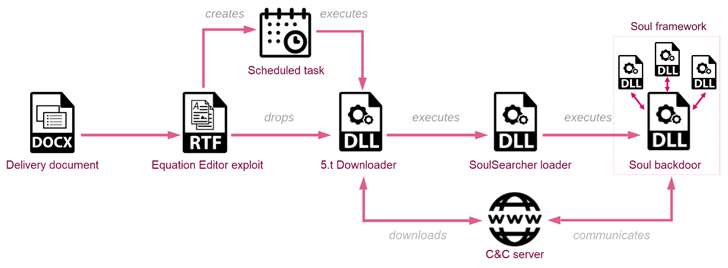
The
attack
chain
detailed
by
Check
Point
begins
with
a
spear-phishing
email
containing
a
lure
document
that
leverages
the
Royal
Road
Rich
Text
Format
(RTF)
weaponizer
to
drop
a
downloader
by
exploiting
one
of
several
vulnerabilities
in
the
Microsoft
Equation
Editor.
The
downloader,
in
turn,
is
designed
to
retrieve
a
loader
known
as
SoulSearcher
from
a
geofenced
command-and-control
(C&C)
server
that
only
responds
to
requests
originating
from
IP
addresses
corresponding
to
the
targeted
countries.
The
loader
is
then
responsible
for
downloading,
decrypting,
and
executing
the
Soul
backdoor
and
its
other
components,
thereby
enabling
the
adversary
to
harvest
a
wide
range
of
information.
“The
Soul
main
module
is
responsible
for
communicating
with
the
C&C
server
and
its
primary
purpose
is
to
receive
and
load
in
memory
additional
modules,”
Check
Point
said.
Discover
the
Latest
Malware
Evasion
Tactics
and
Prevention
Strategies
Ready
to
bust
the
9
most
dangerous
myths
about
file-based
attacks?
Join
our
upcoming
webinar
and
become
a
hero
in
the
fight
against
patient
zero
infections
and
zero-day
security
events!
“Interestingly,
the
backdoor
configuration
contains
a
‘radio
silence’-like
feature,
where
the
actors
can
specify
specific
hours
in
a
week
when
the
backdoor
is
not
allowed
to
communicate
with
the
C&C
server.”
The
findings
are
yet
another
indication
of
the
tool
sharing
that’s
prevalent
among
Chinese
advanced
persistent
threat
(APT)
groups
to
facilitate
intelligence
gathering.
“While
the
Soul
framework
has
been
in
use
since
at
least
2017,
the
threat
actors
behind
it
have
been
constantly
updating
and
refining
its
architecture
and
capabilities,”
the
company
said.
It
further
noted
that
the
campaign
is
likely
“staged
by
advanced
Chinese-backed
threat
actors,
whose
other
tools,
capabilities
and
position
within
the
broader
network
of
espionage
activities
are
yet
to
be
explored.”