Microsoft has just rolled out 79 updates across eleven product lines. Among these, seven critical issues related to Azure, SharePoint, and Windows have been identified by Microsoft. At the moment, three of these problems are currently being exploited, with a fourth issue possibly being targeted due to its association with other vulnerabilities. For more details on this unique scenario, please refer to the “Notable September updates” section below. Microsoft predicts that 11 vulnerabilities in Windows are highly likely to be exploited within the next 30 days. Sophos protections can identify eight of this month’s issues, and specific information on them is provided in a table below.
Alongside these patches, there is detailed advisory information concerning three CVEs that have been fixed by Adobe patches, affecting Reader and ColdFusion. One of the critical Reader vulnerabilities (CVE-2024-41869) involves a use-after-free exploit that is already in use by malicious entities. At the end of this post, comprehensive appendices are included, sorting all of Microsoft’s patches by severity, predicted exploitability, and product family.
Numerical Overview
- Total number of CVEs: 79
- Total Adobe advisories covered in this update: 3
- Publicly disclosed vulnerabilities: 1
- Exploited vulnerabilities detected: 4*
- Severity breakdown
- Critical: 7
- Important: 71
- Moderate: 1
- Impact categories
- Elevation of privilege: 30
- Remote code execution: 23
- Information disclosure: 11
- Denial of service: 8
- Security feature bypass: 4
- Spoofing: 3
- CVSS base score 9.0 or higher: 2
- CVSS base score 8.0 or higher: 24
* Further information regarding the fourth exploited-detected CVE of this month, CVE-2024-43491, can be found in the “Notable September updates” section below.
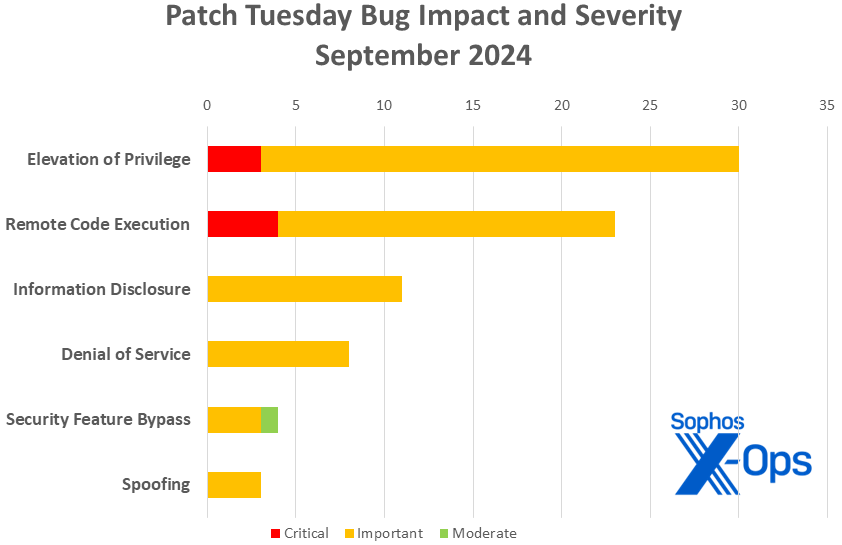
Figure 1: Among this month’s critical-severity patches, one has already been exploited, while exploitation is expected within the next 30 days for two others.
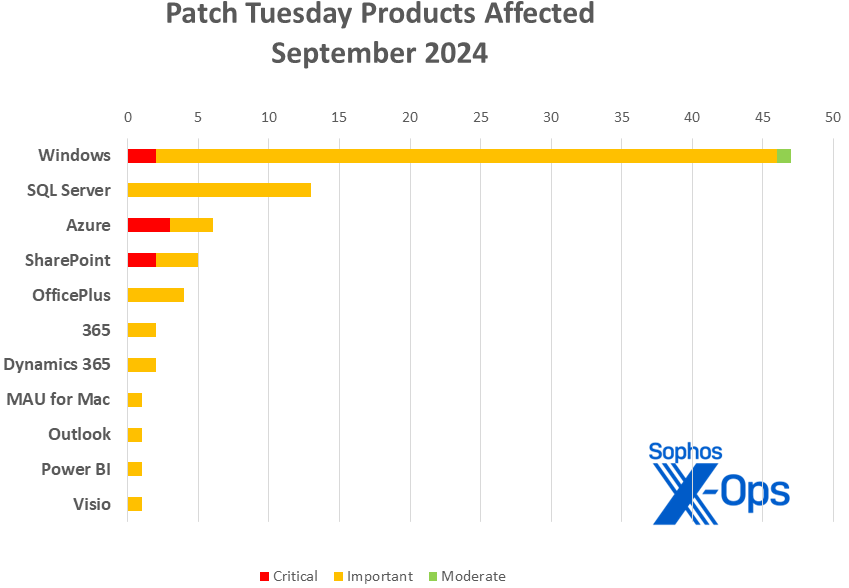
Product Varieties
- Windows: 47
- SQL Server: 13
- Azure: 6
- SharePoint: 5
- Office: 4
- 365: 2
- Dynamics 365: 2
- Microsoft AutoUpdate (MAU) for Mac: 1
- Outlook for iOS: 1
- Power BI: 1
- Visio: 1
As per our convention, CVEs affecting multiple product families are tallied individually for each family.
Figure 2: Although Windows dominates the list of impacted product lines as usual, a set of Native Scoring issues in SQL Server has contributed to 13 individual patches for that product.
Pivotal Updates for September
Aside from the above-mentioned issues, several specific matters deserve special attention.
CVE-2024-38217 — Windows Mark of the Web Security Feature Bypass Vulnerability
CVE-2024-43492 — Windows Mark of the Web Security Feature Bypass Vulnerability
This month’s updates address two Mark of the Web vulnerabilities, with one currently being actively exploited in the wild (CVE-2024-38217), while the other (CVE-2024-43492) is considered more likely to be exploited within the coming month according to Microsoft. The latter was internally discovered at Microsoft and is of moderate severity. The former was responsibly reported by Elastic Security’s Joe Desimone, who has shared details on the discovery and reporting process, which may interest those following code-signing certificate issues. It impacts all Windows versions, including Win 11H24, and has an important severity level.
CVE-2024-38014 — Windows Installer Elevation of Privilege Vulnerability
This specific issue is presently being exploited in the wild. It affects all versions of Windows, including Win 11H24.
CVE-2024-43491 – Microsoft Windows Update Remote Code Execution Vulnerability
Fortunately, this vulnerability only affects certain operational components of Windows 10, version 1507 (initially released in July 2015); supported versions are limited to Windows 10 Enterprise 2015 LTSB and Windows 10 IoT Enterprise 2015 LTSB. However, for users on these versions, there is a critical remote code execution flaw rated at a 9.8 CVSS base score, specifically within the Windows Servicing Stack. This issue is intriguing for those interested, as Microsoft explains that the problem arises from build version numbers that triggered a defect due to crossing a certain range, affecting the applicability of Optional Components since March 12, 2024 (KB5035858). Detailed guidance is available in KB5043083; a precise patch sequence is recommended for those affected. The page also lists the specific optional components impacted, aiding in understanding the potential exposure.
[29 CVEs] — Windows 11 24H2 patches
Although Windows 11 24H2 isn’t yet widely available, over a third of this month’s patches are earmarked for this platform, including two (CVE-2024-38014, CVE-2024-38217) with confirmed exploitation cases in the wild. Users of the new Copilot+ PCs who don’t receive automatic updates should ensure their devices are promptly updated.
[0 CVEs] — .NET, Visual Studio, Edge / Chromium, non-iOS Outlook
This month provides a rare break for .NET and Visual Studio, with no patches released for those product families. Similarly, there are no updates for Edge / Chromium and non-iOS Outlook.
time concerning Edge, or Outlook for operating systems excluding those from Apple.
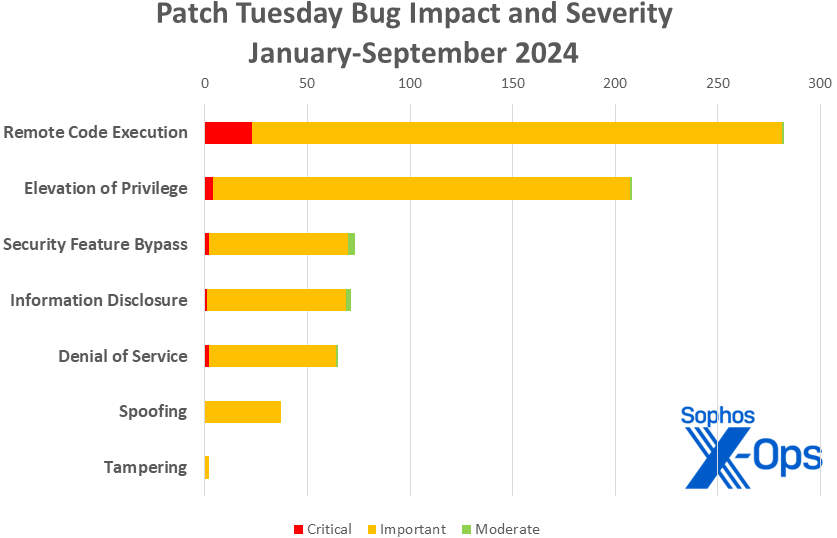
Figure 3: Despite the prevalence of Elevation of Privilege (EoP) concerns in recent periods, Remote Code Execution (RCE) remains at the forefront as we approach the end of the third quarter in 2024.
Sophos safeguards
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2024-38237 | Exp/2438237-A | Exp/2438237-A |
| CVE-2024-38238 | Exp/2438238-A | Exp/2438238-A |
| CVE-2024-38241 | Exp/2438241-A | Exp/2438241-A |
| CVE-2024-38242 | Exp/2438242-A | Exp/2438242-A |
| CVE-2024-38243 | Exp/2438243-A | Exp/2438243-A |
| CVE-2024-38244 | Exp/2438244-A | Exp/2438244-A |
| CVE-2024-38245 | Exp/2438245-A | Exp/2438245-A |
| CVE-2024-43461 | SID:2310127 | SID:2310126 |
If you prefer, on a monthly basis, to independently download Microsoft’s updates instead of relying on your system to do so, you can access them manually from the Windows Update Catalog website. Utilize the winver.exe utility to determine the specific Windows 10 or 11 build you are using, and then get the Cumulative Update package corresponding to your system’s architecture and build number.
Appendix A: Vulnerability Impact and Severity
This compilation showcases September patches categorized by impact, subsequentially sorted by severity, with further organization based on CVE identifiers.
Elevation of Privilege (30 CVEs)
| Critical severity | |
| CVE-2024-38194 | Azure Web Apps Elevation of Privilege Vulnerability |
| CVE-2024-38216 | Azure Stack Hub Elevation of Privilege Vulnerability |
| CVE-2024-38220 | Azure Stack Hub Elevation of Privilege Vulnerability |
| Important severity | |
| CVE-2024-37341 | Microsoft SQL Server Elevation of Privilege Vulnerability |
| CVE-2024-37965 | Microsoft SQL Server Elevation of Privilege Vulnerability |
| CVE-2024-37980 | Microsoft SQL Server Elevation of Privilege Vulnerability |
| CVE-2024-38014 | Windows Installer Elevation of Privilege Vulnerability |
| CVE-2024-38046 | PowerShell Elevation of Privilege Vulnerability |
| CVE-2024-38188 | Azure Network Watcher VM Agent Elevation of Privilege Vulnerability |
| CVE-2024-38225 | Microsoft Dynamics 365 Business Central Elevation of Privilege Vulnerability |
| CVE-2024-38237 | Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38238 | Kernel Streaming Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38239 | Windows Kerberos Elevation of Privilege Vulnerability |
| CVE-2024-38240 | Windows Remote Access Connection Manager Elevation of Privilege Vulnerability |
| CVE-2024-38241 | Kernel Streaming Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38242 | Kernel Streaming Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38243 | Kernel Streaming Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38244 | Kernel Streaming Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38245 | Kernel Streaming Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38246 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-38247 | Windows Graphics Component Elevation of Privilege Vulnerability |
| CVE-2024-38248 | Windows Storage Elevation of Privilege Vulnerability |
| CVE-2024-38249 | Windows Graphics Component Elevation of Privilege Vulnerability |
| CVE-2024-38250 | Windows Graphics Component Elevation of Privilege Vulnerability |
| CVE-2024-38252 | Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability |
| CVE-2024-38253 | Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability |
| CVE-2024-43457 | Windows Setup and Deployment Elevation of Privilege Vulnerability |
| CVE-2024-43465 | Microsoft Excel Elevation of Privilege Vulnerability |
| CVE-2024-43470 | Azure Network Watcher VM Agent Elevation of Privilege Vulnerability |
| CVE-2024-43492 | Microsoft AutoUpdate (MAU) Elevation of Privilege Vulnerability |
Remote Code Execution (23 CVEs)
| Critical severity | ||
| CVE-2024-38018 | Microsoft SharePoint Server Remote Code Execution Vulnerability | |
| CVE-2024-38119 | Windows Network Address Translation (NAT) Remote Code Execution Vulnerability | |
| CVE-2024-43464 | Microsoft SharePoint Server Remote Code Execution Vulnerability | |
| CVE-2024-43491 | Microsoft Windows Update Remote Code Execution Vulnerability | |
| Important severity | ||
| CVE-2024-21416 | Windows TCP/IP Remote Code Execution Vulnerability | |
| CVE-2024-26186 | Microsoft SQL Server Native Scoring Remote Code Execution Vulnerability | |
| CVE-2024-26191 | Vulnerability in Microsoft SQL Server Native Scoring Allows Remote Code Execution | |
| Identified as CVE-2024-37335 | Vulnerability in Microsoft SQL Server Native Scoring Allows Remote Code Execution | |
| Identified as CVE-2024-37338 | Vulnerability in Microsoft SQL Server Native Scoring Allows Remote Code Execution | |
| Identified as CVE-2024-37339 | Vulnerability in Microsoft SQL Server Native Scoring Allows Remote Code Execution | |
| Identified as CVE-2024-37340 | Vulnerability in Microsoft SQL Server Native Scoring Allows Remote Code Execution | |
| Identified as CVE-2024-38045 | Vulnerability in Windows TCP/IP Allows Remote Code Execution | |
| Identified as CVE-2024-38227 | Vulnerability in Microsoft SharePoint Server Allows Remote Code Execution | |
| Identified as CVE-2024-38228 | Vulnerability in Microsoft SharePoint Server Allows Remote Code Execution | |
| Identified as CVE-2024-38259 | Vulnerability in Microsoft Management Console Allows Remote Code Execution | |
| Identified as CVE-2024-38260 | Vulnerability in Windows Remote Desktop Licensing Service Allows Remote Code Execution | |
| Identified as CVE-2024-38263 | Vulnerability in Windows Remote Desktop Licensing Service Allows Remote Code Execution | |
| Identified as CVE-2024-43454 | Vulnerability in Windows Remote Desktop Licensing Service Allows Remote Code Execution | |
| Identified as CVE-2024-43463 | Vulnerability in Microsoft Office Visio Allows Remote Code Execution | |
| Identified as CVE-2024-43467 | Vulnerability in Windows Remote Desktop Licensing Service Allows Remote Code Execution | |
| Identified as CVE-2024-43469 | Vulnerability in Azure CycleCloud Allows Remote Code Execution | |
| Identified as CVE-2024-43479 | Vulnerability in Microsoft Power Automate Desktop Allows Remote Code Execution | |
| Identified as CVE-2024-43495 | Vulnerability in Windows libarchive Allows Remote Code Execution | |
Information Leakage (11 CVEs)
| Important seriousness | |
| Identified as CVE-2024-37337 | Information Leakage Vulnerability in Microsoft SQL Server Native Scoring |
| Identified as CVE-2024-37342 | Information Leakage Vulnerability in Microsoft SQL Server Native Scoring |
| Identified as CVE-2024-37966 | Information Leakage Vulnerability in Microsoft SQL Server Native Scoring |
| Identified as CVE-2024-38254 | Information Leakage Vulnerability in Windows Authentication |
| Identified as CVE-2024-38256 | Information Leakage Vulnerability in Windows Kernel-Mode Driver |
| Identified as CVE-2024-38257 | Information Leakage Vulnerability in Microsoft AllJoyn API |
| Identified as CVE-2024-38258 | Information Leakage Vulnerability in Windows Remote Desktop Licensing Service |
| Identified as CVE-2024-43458 | Information Leakage Vulnerability in Windows Networking |
| Identified as CVE-2024-43474 | Information Leakage Vulnerability in Microsoft SQL Server |
| Identified as CVE-2024-43475 | Information Leakage Vulnerability in Microsoft Windows Admin Center |
| Identified as CVE-2024-43482 | Information Leakage Vulnerability in Microsoft Outlook for iOS |
Service Unavailability (8 CVEs)
| Important seriousness | |
| Identified as CVE-2024-38230 | Denial of Service Vulnerability in Windows Standards-Based Storage Management Service |
| Identified as CVE-2024-38231 | Denial of Service Vulnerability in Windows Remote Desktop Licensing Service |
| Identified as CVE-2024-38232 | Denial of Service Vulnerability in Windows Networking |
| Identified as CVE-2024-38233 | Denial of Service Vulnerability in Windows Networking |
| Identified as CVE-2024-38234 | Denial of Service Vulnerability in Windows Networking |
| Identified as CVE-2024-38235 | Denial of Service Vulnerability in Windows Hyper-V |
| Identified as CVE-2024-38236 | Denial of Service Vulnerability in DHCP Server Service |
| Identified as CVE-2024-43466 | Denial of Service Vulnerability in Microsoft SharePoint Server |
Security Mechanism Circumvention (4 CVEs)
| Important seriousness | |
| Identified as CVE-2024-30073 | Security Mechanism Circumvention Vulnerability in Windows Security Zone Mapping |
| Identified as CVE-2024-38217 | Security Mechanism Circumvention Vulnerability in Windows Mark of the Web |
| Identified as CVE-2024-38226 | Security Mechanism Circumvention Vulnerability in Microsoft Publisher |
| Moderate seriousness | |
| Identified as CVE-2024-43487 | Security Mechanism Circumvention Vulnerability in Windows Mark of the Web |
Impersonation (3 CVEs)
| Important seriousness | |
| Identified as CVE-2024-43455 | Impersonation Vulnerability in Windows Remote Desktop Licensing Service |
| Identified as CVE-2024-43461 | Impersonation Vulnerability in Windows MSHTML Platform |
| Identified as CVE-2024-43476 | Cross-site Scripting Vulnerability in Microsoft Dynamics 365 (on-premises) |
Appendix B: Likelihood of Exploitation
This table provides details on the September CVEs that Microsoft believes are either actively being exploited in the wild or have a high potential for exploitation within the first month after release. The list is organized by CVE. For CVE-2024-43491, while the specific issue is not confirmed to be actively exploited, some of the problems addressed by the rejected servicing-stack updates are, so it is included in this list. (Please refer to the “Notable September updates” section above for additional context.)
| Active Exploitation Detected | |
| Identified as CVE-2024-38014 | Elevation of Privileges Vulnerability in Windows Installer |
| Identified as CVE-2024-38217 | Security Mechanism Circumvention Vulnerability in Windows Mark of the Web |
| Identified as CVE-2024-38226 | Security Mechanism Circumvention Vulnerability in Microsoft Publisher |
| Identified as CVE-2024-43491 | Remote Code Execution Vulnerability in Microsoft Windows Update |
| Likely to be Exploited in the Next 30 Days | |
| Identified as CVE-2024-38018 | Remote Code Execution Vulnerability in Microsoft SharePoint Server |
| Identified as CVE-2024-38227 | Remote Code Execution Vulnerability in Microsoft SharePoint Server | VUL-2024-38228 | Microsoft SharePoint Server Remote Code Execution Flaw |
| VUL-2024-38237 | Kernel Streaming WOW Thunk Service Driver Privilege Escalation Vulnerability |
| VUL-2024-38238 | Kernel Streaming Service Driver Privilege Escalation Vulnerability |
| VUL-2024-38241 | Kernel Streaming Service Driver Privilege Escalation Vulnerability |
| VUL-2024-38242 | Kernel Streaming Service Driver Privilege Escalation Vulnerability |
| VUL-2024-38243 | Kernel Streaming Service Driver Privilege Escalation Vulnerability |
| VUL-2024-38244 | Kernel Streaming Service Driver Privilege Escalation Vulnerability |
| VUL-2024-38245 | Kernel Streaming Service Driver Privilege Escalation Vulnerability |
| VUL-2024-38246 | Win32k Privilege Escalation Vulnerability |
| VUL-2024-38247 | Windows Graphics Component Privilege Escalation Vulnerability |
| VUL-2024-38249 | Windows Graphics Component Privilege Escalation Vulnerability |
| VUL-2024-38252 | Windows Win32 Kernel Subsystem Privilege Escalation Vulnerability |
| VUL-2024-38253 | Windows Win32 Kernel Subsystem Privilege Escalation Vulnerability |
| VUL-2024-43457 | Windows Setup and Deployment Privilege Escalation Vulnerability |
| VUL-2024-43461 | Windows MSHTML Platform Spoofing Flaw |
| VUL-2024-43464 | Microsoft SharePoint Server Remote Code Execution Flaw |
| VUL-2024-43487 | Windows Mark of the Web Security Feature Bypass Flaw |
Appendix C: Affected Products
Below is a compilation of patches released in September categorized by product families and sorted by severity. Each list is additionally organized by CVE. Patches applied across multiple product families are articulated separately for each family.
Windows (47 Vulnerabilities)
| Severity: Critical | |
| VUL-2024-38119 | Windows Network Address Translation (NAT) Remote Code Execution Flaw |
| VUL-2024-43491 | Microsoft Windows Update Remote Code Execution Flaw |
| Severity: Important | |
| VUL-2024-21416 | Windows TCP/IP Remote Code Execution Flaw |
| VUL-2024-30073 | Windows Security Zone Mapping Security Feature Bypass Flaw |
| VUL-2024-38014 | Windows Installer Privilege Escalation Vulnerability |
| VUL-2024-38045 | Windows TCP/IP Remote Code Execution Flaw |
| VUL-2024-38046 | PowerShell Privilege Escalation Vulnerability |
| VUL-2024-38217 | Windows Mark of the Web Security Feature Bypass Flaw |
| VUL-2024-38230 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability |
| VUL-2024-38231 | Windows Remote Desktop Licensing Service Denial of Service Vulnerability |
| VUL-2024-38232 | Windows Networking Denial of Service Vulnerability |
| VUL-2024-38233 | Windows Networking Denial of Service Vulnerability |
| VUL-2024-38234 | Windows Networking Denial of Service Vulnerability |
| VUL-2024-38235 | Windows Hyper-V Denial of Service Vulnerability |
| VUL-2024-38236 | DHCP Server Service Denial of Service Vulnerability |
| VUL-2024-38237 | Kernel Streaming WOW Thunk Service Driver Privilege Escalation Vulnerability |
| VUL-2024-38238 | Kernel Streaming Service Driver Privilege Escalation Vulnerability |
| VUL-2024-38239 | Windows Kerberos Privilege Escalation Vulnerability |
| VUL-2024-38240 | Windows Remote Access Connection Manager Privilege Escalation Vulnerability |
| VUL-2024-38241 | Kernel Streaming Service Driver Privilege Escalation Vulnerability |
| VUL-2024-38242 | Kernel Streaming Service Driver Privilege Escalation Vulnerability |
| VUL-2024-38243 | Kernel Streaming Service Driver Privilege Escalation Vulnerability |
| VUL-2024-38244 | Kernel Streaming Service Driver Privilege Escalation Vulnerability |
| VUL-2024-38245 | Kernel Streaming Service Driver Privilege Escalation Vulnerability |
| VUL-2024-38246 | Win32k Privilege Escalation Vulnerability |
| VUL-2024-38247 | Windows Graphics Component Privilege Escalation Vulnerability |
| VUL-2024-38248 | Windows Storage Privilege Escalation Vulnerability |
| VUL-2024-38249 | Windows Graphics Component Privilege Escalation Vulnerability |
| VUL-2024-38252 | Windows Win32 Kernel Subsystem Privilege Escalation Vulnerability |
| VUL-2024-38253 | Windows Win32 Kernel Subsystem Privilege Escalation Vulnerability |
| VUL-2024-38254 | Windows Authentication Information Disclosure Flaw |
| VUL-2024-38256 | Windows Kernel-Mode Driver Information Disclosure Flaw |
| VUL-2024-38257 | Microsoft AllJoyn API Information Disclosure Flaw |
| VUL-2024-38258 | Windows Remote Desktop Licensing Service Information Disclosure Flaw |
| VUL-2024-38259 | Microsoft Management Console Remote Code Execution Flaw |
| VUL-2024-38260 | Windows Remote Desktop Licensing Service Remote Code Execution Flaw |
| VUL-2024-38263 | Windows Remote Desktop Licensing Service Remote Code Execution Flaw |
| VUL-2024-43454 | Windows Remote Desktop Licensing Service Remote Code Execution Flaw |
| VUL-2024-43455 | Windows Remote Desktop Licensing Service Spoofing Flaw |
| VUL-2024-43457 | WindowsElevation of Privilege Vulnerability regarding Setup and Deployment |
| CVE-2024-43458 | Disclosure Vulnerability associated with Windows Networking |
| CVE-2024-43461 | Spoofing Vulnerability in the Windows MSHTML Platform |
| CVE-2024-43467 | Remote Code Execution Vulnerability in the Windows Remote Desktop Licensing Service |
| CVE-2024-43475 | Information Disclosure Vulnerability in Microsoft Windows Admin Center |
| CVE-2024-43495 | Remote Code Execution Vulnerability in Windows libarchive |
| Moderate risk level | |
| CVE-2024-43487 | Bypass Vulnerability in the Security Feature of Windows Mark of the Web |
SQL Server (13 Common Vulnerabilities and Exposures)
| Significant risk level | |
| CVE-2024-26186 | Remote Code Execution Vulnerability in Microsoft SQL Server Native Scoring |
| CVE-2024-26191 | Remote Code Execution Vulnerability in Microsoft SQL Server Native Scoring |
| CVE-2024-37335 | Remote Code Execution Vulnerability in Microsoft SQL Server Native Scoring |
| CVE-2024-37337 | Information Disclosure Vulnerability in Microsoft SQL Server Native Scoring |
| CVE-2024-37338 | Remote Code Execution Vulnerability in Microsoft SQL Server Native Scoring |
| CVE-2024-37339 | Remote Code Execution Vulnerability in Microsoft SQL Server Native Scoring |
| CVE-2024-37340 | Remote Code Execution Vulnerability in Microsoft SQL Server Native Scoring |
| CVE-2024-37341 | Elevation of Privilege Vulnerability in Microsoft SQL Server |
| CVE-2024-37342 | Information Disclosure Vulnerability in Microsoft SQL Server Native Scoring |
| CVE-2024-37965 | Elevation of Privilege Vulnerability in Microsoft SQL Server |
| CVE-2024-37966 | Information Disclosure Vulnerability in Microsoft SQL Server Native Scoring |
| CVE-2024-37980 | Elevation of Privilege Vulnerability in Microsoft SQL Server |
| CVE-2024-43474 | Information Disclosure Vulnerability in Microsoft SQL Server |
Azure (6 Common Vulnerabilities and Exposures)
| Urgent risk level | |
| CVE-2024-38194 | Elevation of Privilege Vulnerability in Azure Web Apps |
| CVE-2024-38216 | Elevation of Privilege Vulnerability in Azure Stack Hub |
| CVE-2024-38220 | Elevation of Privilege Vulnerability in Azure Stack Hub |
| Significant risk level | |
| CVE-2024-38188 | Elevation of Privilege Vulnerability in Azure Network Watcher VM Agent |
| CVE-2024-43469 | Remote Code Execution Vulnerability in Azure CycleCloud |
| CVE-2024-43470 | Elevation of Privilege Vulnerability in Azure Network Watcher VM Agent |
SharePoint (5 Common Vulnerabilities and Exposures)
| Urgent risk level | |
| CVE-2024-38018 | Remote Code Execution Vulnerability in Microsoft SharePoint Server |
| CVE-2024-43464 | Remote Code Execution Vulnerability in Microsoft SharePoint Server |
| Significant risk level | |
| CVE-2024-38227 | Remote Code Execution Vulnerability in Microsoft SharePoint Server |
| CVE-2024-38228 | Remote Code Execution Vulnerability in Microsoft SharePoint Server |
| CVE-2024-43466 | Denial of Service Vulnerability in Microsoft SharePoint Server |
Office (4 Common Vulnerabilities and Exposures)
| Significant risk level | |
| CVE-2024-38226 | Security Features Bypass Vulnerability in Microsoft Publisher |
| CVE-2024-38250 | Elevation of Privilege Vulnerability in Windows Graphics Component |
| CVE-2024-43463 | Remote Code Execution Vulnerability in Microsoft Office Visio |
| CVE-2024-43465 | Elevation of Privilege Vulnerability in Microsoft Excel |
365 (2 Common Vulnerabilities and Exposures)
| Significant risk level | |
| CVE-2024-43463 | Remote Code Execution Vulnerability in Microsoft Office Visio |
| CVE-2024-43465 | Elevation of Privilege Vulnerability in Microsoft Excel |
Dynamics 365 (2 Common Vulnerabilities and Exposures)
| Significant risk level | |
| CVE-2024-38225 | Elevation of Privilege Vulnerability in Microsoft Dynamics 365 Business Central |
| CVE-2024-43476 | Cross-site Scripting Vulnerability in Microsoft Dynamics 365 (on-premises) |
Microsoft AutoUpdate (MAU) for Mac (1 Common Vulnerabilities and Exposures)
| Significant risk level | |
| CVE-2024-43492 | Elevation of Privilege Vulnerability in Microsoft AutoUpdate (MAU) |
Outlook for iOS (1 Common Vulnerabilities and Exposures)
| Significant risk level | |
| CVE-2024-43482 | Information Disclosure Vulnerability in Microsoft Outlook for iOS |
PowerBI (1 Common Vulnerabilities and Exposures)
| Significant risk level | |
| CVE-2024-43479 | Remote Code Execution Vulnerability in Microsoft Power Automate Desktop |
Visio (1 Common Vulnerabilities and Exposures)
| Significant risk level | |
| CVE-2024-43463 | Remote Code Execution Vulnerability in Microsoft Office Visio |
Appendix D: Notifications and Other Products
This comprises notifications and data on different relevant CVEs released in September, arranged by product.
Associated with Adobe (non-Microsoft release) (3 Common Vulnerabilities and Exposures)
| CVE-2024-41869 | APSB24-70 | Use After Free (CWE-416) |
| CVE-2024-41874 | APSB24-71 | Deserialization of Untrusted Data (CWE-502) |
| CVE-2024-39420 | APSB24-70 | Time-of-check Time-of-use (TOCTOU) Race Condition (CWE-367) |