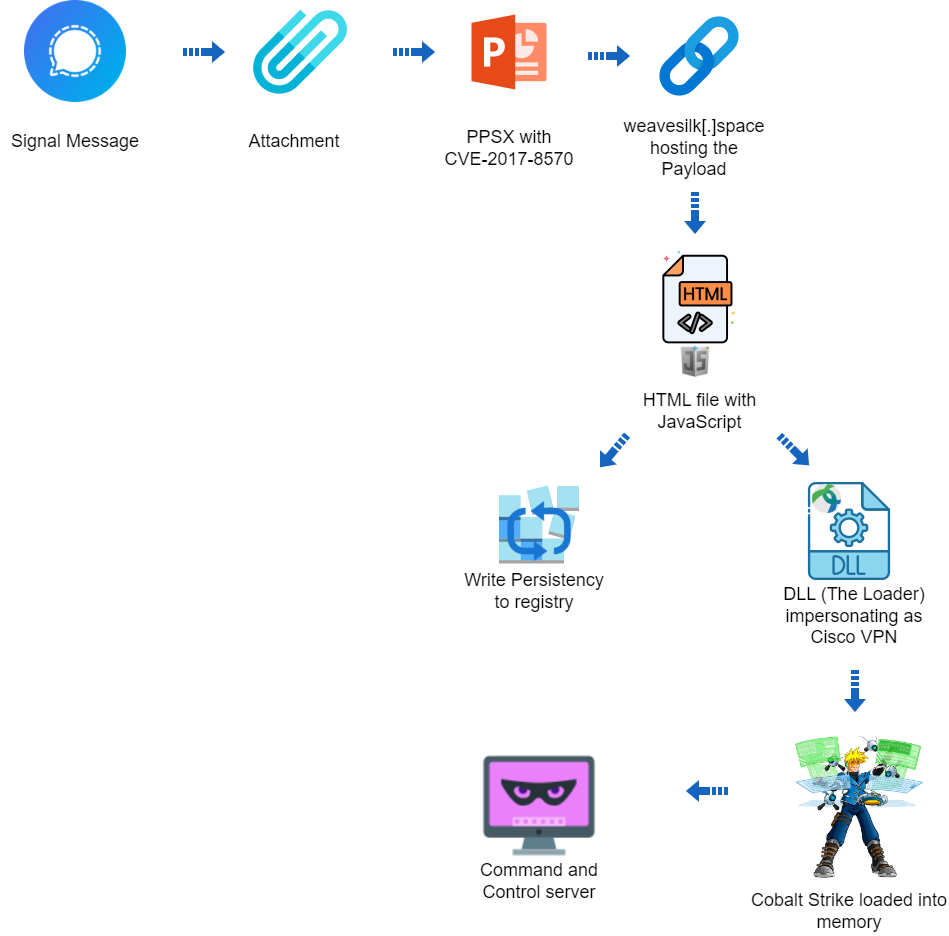

Anyone who works in computer security knows that they should have two-factor authentication (2FA) enabled on their accounts.
2FA provides an additional layer of security. A hacker might be able to guess, steal, or brute force the password on your accounts – but they won’t be able to gain access unless they also have a time-based one-time password.
So, how come Mandiant didn’t have 2FA protecting its Twitter account, which was hacked last week to promote a cryptocurrency scam?
Mandiant promised in the wake of the hack that it would share details of what had happened, and – true to its word – it’s done just that.

But Mandiant’s explanation of how it was hacked raises some more questions.
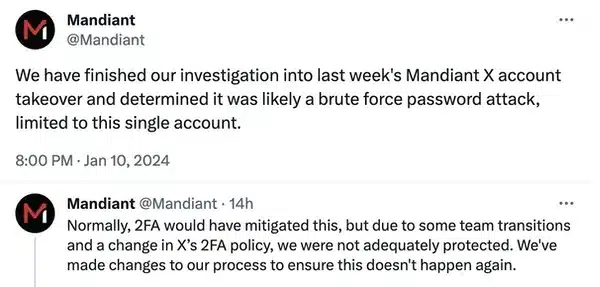
We have finished our investigation into last week’s Mandiant X account
takeover and determined it was likely a brute force password attack,
limited to this single account.
What they seem to be saying is that someone tried over-and-over-and-over-and-over again again to break into Mandiant’s Twitter account, or rather used a computer to do it for them… and eventually they got lucky.
You have to wonder just how long and complicated Mandiant’s Twitter password was if that really was the case.
Presumably Mandiant has now changed the password, so why don’t they tell us what it was? Maybe we could all learn something if we knew just how much effort the hackers had to go to to bruteforce Mandiant’s password, and how long it might have taken them.
PS. “likely”? Sounds like Mandiant isn’t really sure.
My guess had been that perhaps Mandiant’s Twitter account was compromised in a similar way to that of another firm hacked around the same time – CertiK.
In that case the hackers contacted CertiK posing as a Forbes journalist, and tricked an employee into clicking on a link that posed as a calendar scheduling link for an interview.
Anyway, lets look further at what Mandiant has to say about its security breach:
Normally, 2FA would have mitigated this, but due to some team transitions and a change in X’s 2FA policy, we were not adequately protected. We’ve made changes to our process to ensure this doesn’t happen again.
Well, there’s a carefully worded sentence! Mandiant seems to be going out of its way to avoid saying that it didn’t have 2FA enabled on its Twitter account, but it’s the only way I can interpret it.
I guess it’s pretty embarrassing for a cybersecurity company to admit it doesn’t have 2FA enabled.
But then there’s the part about “a change in X’s 2FA policy” (X is the daft name we’re supposed to use for Twitter these days, but I’m not playing that game right now…).
My guess is that Mandiant is referring to is the change Twitter announced regarding 2FA last February. Twitter said that it would be removing SMS-based 2FA for all but paid-up Twitter Blue subscribers in March 2023, and that anyone who didn’t want to lose access to Twitter would have to disable 2FA in advance.
At the time I criticised Twitter’s decision, believing that it would reduce security for some users.
SMS-based 2FA is one of the weakest ways to implement 2FA (because of SIM swap attacks), but it’s still better than no 2FA at all.
It sounds to me like Mandiant removed SMS-based 2FA protection from its account (presumably out of fear that it would be locked out when Twitter made the feature premium-only), but never replaced it with a stronger alternative, such as a hardware-based security key or app-based authenticator.
I know that when you’re dealing with accounts that are used by a team of people rather than an individual that there can be additional complexities in setting up multi-factor authentication, but there are ways around this. The truth is that there is no reasonable excuse for any company (especially a security firm) to have no 2FA at all protecting its accounts.
Mandiant has published a blog post about the hackers and CLINKSLINK wallet-draining malware that it was linked to the attack.