ScarCruft’s Evolving Arsenal: Researchers Reveal New Malware Distribution Techniques
The
North
Korean
advanced
persistent
threat
(APT)
actor
dubbed
ScarCruft
is
using
weaponized
Microsoft
Compiled
HTML
Help
(CHM)
files
to
download
additional
malware.
According
to
multiple
reports
from
AhnLab
Security
Emergency
response
Center
(ASEC),
SEKOIA.IO,
and
Zscaler,
the
findings
are
illustrative
of
the
group’s
continuous
efforts
to
refine
and
retool
its
tactics
to
sidestep
detection.
“The
group
is
constantly
evolving
its
tools,
techniques,
and
procedures
while
experimenting
with
new
file
formats
and
methods
to
bypass
security
vendors,”
Zscaler
researchers
Sudeep
Singh
and
Naveen
Selvan
said
in
a
new
analysis
published
Tuesday.
ScarCruft,
also
tracked
under
the
names
APT37,
Reaper,
RedEyes,
and
Ricochet
Chollima,
has
exhibited
an
increased
operational
tempo
since
the
start
of
the
year,
targeting
various
South
Korean
entities
for
espionage
purposes.
It
is
known
to
be
active
since
at
least
2012.
Last
month,
ASEC
disclosed
a
campaign
that
employed
HWP
files
that
take
advantage
of
a
security
flaw
in
the
Hangul
word
processing
software
to
deploy
a
backdoor
referred
to
as
M2RAT.
But
new
findings
reveal
the
threat
actor
is
also
using
other
file
formats
such
as
CHM,
HTA,
LNK,
XLL,
and
macro-based
Microsoft
Office
documents
in
its
spear-phishing
attacks
against
South
Korean
targets.
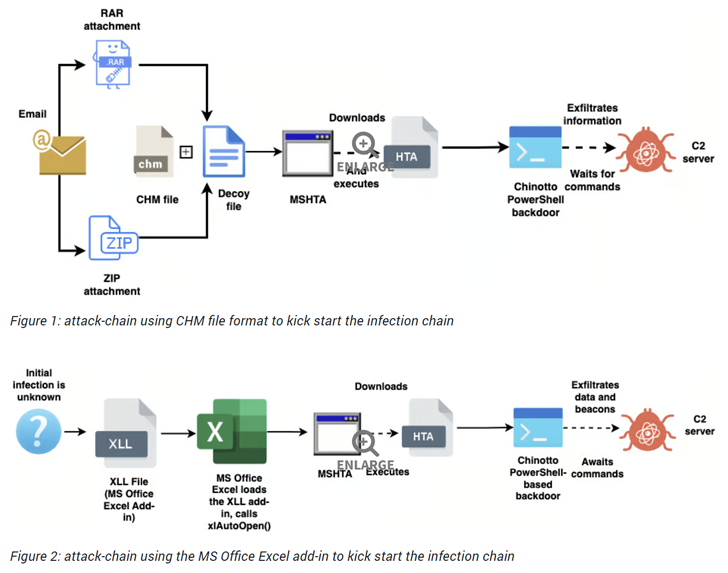
These
infection
chains
often
serve
to
display
a
decoy
file
and
deploy
an
updated
version
of
a
PowerShell-based
implant
known
as
Chinotto,
which
is
capable
of
executing
commands
sent
by
a
server
and
exfiltrating
sensitive
data.
Some
of
the
new
capabilities
of
Chinotto
include
capturing
screenshots
every
five
seconds
and
logging
keystrokes.
The
captured
information
is
saved
in
a
ZIP
archive
and
sent
to
a
remote
server.
WEBINAR
Discover
the
Hidden
Dangers
of
Third-Party
SaaS
Apps
Are
you
aware
of
the
risks
associated
with
third-party
app
access
to
your
company’s
SaaS
apps?
Join
our
webinar
to
learn
about
the
types
of
permissions
being
granted
and
how
to
minimize
risk.
The
insights
about
ScarCruft’s
various
attack
vectors
come
from
a
GitHub
repository
maintained
by
the
adversarial
collective
to
host
malicious
payloads
since
October
2020.
“The
threat
actor
was
able
to
maintain
a
GitHub
repository,
frequently
staging
malicious
payloads
for
more
than
two
years
without
being
detected
or
taken
down,”
Zscaler
researchers
said.
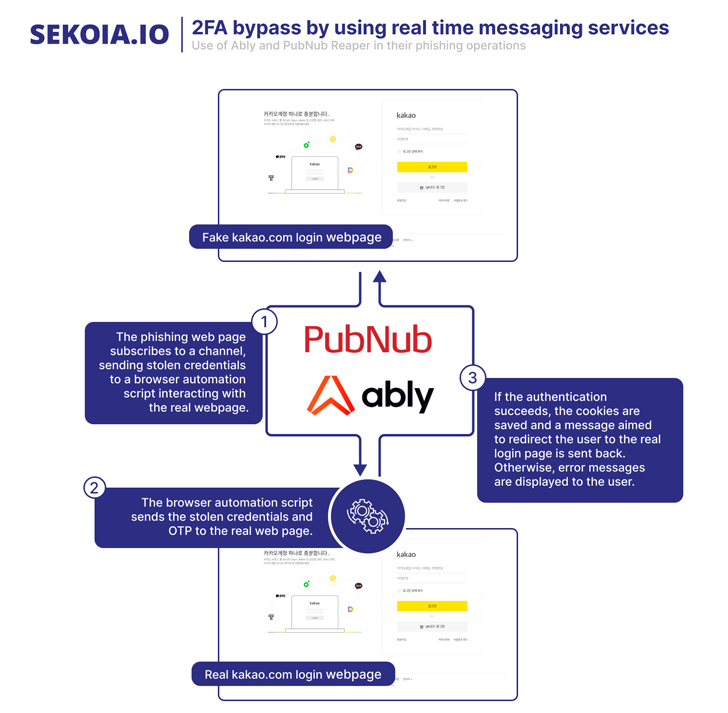
Outside
of
malware
distribution,
ScarCruft
has
also
been
observed
serving
credential
phishing
webpages
targeting
multiple
email
and
cloud
services
such
as
Naver,
iCloud,
Kakao,
Mail.ru,
and
163.com.
It’s
however
not
clear
how
these
pages
are
accessed
by
the
victims,
raising
the
possibility
that
they
may
have
been
embedded
inside
iframes
on
websites
controlled
by
the
attacker
or
sent
as
HTML
attachments
via
email.
Also
discovered
by
SEKOIA.IO
is
a
piece
of
malware
named
AblyGo,
a
backdoor
written
in
Go
that
utilizes
the
Ably
real-time
messaging
framework
to
receive
commands.
The
use
of
CHM
files
to
smuggle
malware
appears
to
be
catching
on
with
other
North
Korea-affiliated
groups
as
well,
with
ASEC
uncovering
a
phishing
campaign
orchestrated
by
Kimsuky
to
distribute
a
backdoor
responsible
for
harvesting
clipboard
data
and
recording
keystrokes.