Russian Electrical Power Entities, Tech Companies, and Government Departments Impacted by Deceptive Dog Trojan
Russian entities are currently facing cyber offensives that have been detected to distribute a Windows version of a malicious software known as Decoy Dog.
The cybersecurity firm Positive Technologies is monitoring the cluster of activities under the title Operation Lahat, attributing it to a sophisticated persistent threat (APT) faction identified as HellHounds.
“The Hellhounds faction infiltrates chosen organizations and establishes a foothold in their networks, eluding detection for extended durations,” security analysts Aleksandr Grigorian and Stanislav Pyzhov stated. “In this process, the faction exploits primary avenues of infiltration, from vulnerable web services to trusted connections.”
HellHounds were initially identified by the organization in late November 2023 subsequent to the infiltration of an unnamed power company with the Decoy Dog trojan. The group has managed to infiltrate 48 targets in Russia so far, including information technology firms, governmental institutions, space industry companies, and telecommunications providers.
There are indications suggesting that the threat actor has been directing attacks at Russian establishments since at least 2021, with the development of the malicious software commencing as early as November 2019.
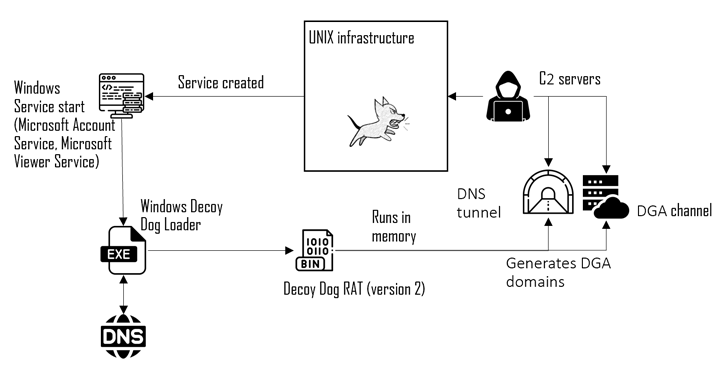
Information about Decoy Dog, a customized variant of the open-source Pupy RAT, surfaced in April 2023, when Infoblox exposed the malware’s utilization of DNS tunneling for communication with its command-and-control (C2) server to remotely manage infected hosts.
An exceptional feature of the malware is its capability to transition victims from one handler to another, enabling the threat actors to uphold communication with infiltrated machines and remain concealed for prolonged periods.
Incursions involving the sophisticated toolkit have primarily been limited to Russia and Eastern Europe, specifically focusing on individual Linux systems, although Infoblox hinted at the possibility of a Windows version.
“References to Windows within the code suggest the existence of an updated Windows client integrating the new capabilities of Decoy Dog, even though all current samples are aimed at Linux,” stated Infoblox back in July 2023.
The latest discoveries from Positive Technologies practically affirm the existence of an identical version of Decoy Dog for Windows, which is transmitted to critical hosts through a loader using a dedicated framework to obtain the key for decrypting the payload.
Further examination has unveiled HellHounds’ use of a modified edition of another open-source software known as 3snake to procure credentials on machines operating on the Linux platform.
Positive Technologies revealed that in at least two cases, the attacker successfully acquired initial entry to the organization’s infrastructure through a contractor utilizing compromised Secure Shell (SSH) access credentials.
“The intruders have managed to persist within vital establishments based in Russia for a significant duration,” stated the analysts.
“Despite virtually all components of the Hellhounds toolkit being grounded in open-source projects, the attackers have adeptly altered it to evade malware detection systems and ensure prolonged inconspicuous presence within the compromised organizations.”












