Russia-linked
threat
actor
Gamaredon employed
new
spyware
in
cyber
attacks
aimed
at
public
authorities
and
critical
information
infrastructure
in
Ukraine.
The
State
Cyber
Protection
Centre
(SCPC)
of
Ukraine
warns
of
a
new
wave
of
targeted
attacks
conducted
by
the
Russia-linked
APT
group
Gamaredon
(aka Shuckworm, Actinium, Armageddon, Primitive
Bear, UAC-0010,
and Trident
Ursa).
The
attacks
aimed
at
public
authorities
and
critical
information
infrastructure
in
Ukraine.
The
government
experts
pointed
out
that
the
threat
actor
continues
to
evolve
its
TTPs
to
avoid
detection.
Currently,
the
Gamaredon
group
is
using
the
GammaLoad
and
GammaSteel
SPZs
in
their
campaigns.
The
former
is
a
VBScript
used
to
download
next-stage
VBScript
from
a
remote
server.
GammaSteel
is
a
PowerShell
script
used
to
conduct
reconnaissance
and
execute
additional
commands.
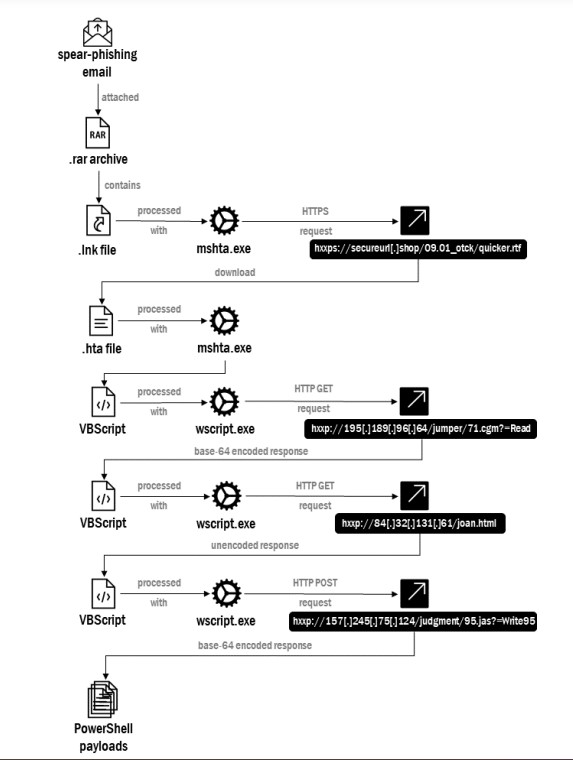
The
attack
chain
starts
with
spear-phishing
messages
with
a
.RAR
attachment
named
“12-1-125_09.01.2023.”
The
.RAR
archive
contains
the
.LNK
file
named
“Запит
Служба
безпеки
України
12-1-125
від
09.01.2023.lnk”
(“Request
of
the
Security
Service
of
Ukraine
12-1-125
dated
09.01.2023.lnk”).
Upon
opening
the
.LNK
file,
it
uses
the
System
Binary
Proxy
Execution
technique
through
the
execution
of
Windows-native
binary
(designed
to
execute
Microsoft
HTML
Application
(HTA)
files
(mshta.exe))
to
download
a
file
via
the
URL
hxxps://secureurl[.]shop/09.01_otck/quicker[.]rtf
.
The
government
experts
noticed
that
access
to
the
file
is
allowed
only
from
IP
addresses
in
the
Ukrainian
address
space.
“The
current
activity
of
the
UAC-0010
group
is
characterized
by
an
approach
to
the
multi-stage
loading
and
execution
of
payloads
of
WPS,
which
is
used
to
maintain
control
over
infected
hosts. Such
payloads
are
similar
types
of
malware,
which
are
developed
by
attackers
to
perform
similar
behavioral
patterns.”
reads
the
alert
published
by
the
SCPC. “Currently,
the
UAC-0010
group
uses
the
GammaLoad
and
GammaSteel
SPZs
in
their
campaigns.”
One
of
the
methods
of
getting
the
C2
IP
address
relies
on
the
usage
of
legitimate
third-party
services,
such
as
Telegram
and
cloudflare-dns[.]com.
Another
method
consists
of
pinging
the
subdomain
Write[.]mohsengo[.]shop
with
WMI
query
and
retrieving
the
ProtocolAddress
value
to
obtain
the
C2
IP
address.
The
State
Cyber
Protection
Centre
published
a
technical
report
that
provides
details
for
each
stage
of
the
attack
chain.
Follow
me
on
Twitter:
@securityaffairs
and
Facebook
and
Mastodon
(SecurityAffairs –
hacking,
Gamaredon)






