The
NuGet
repository
is
the
target
of
a
new
“sophisticated
and
highly-malicious
attack”
aiming
to
infect
.NET
developer
systems
with
cryptocurrency
stealer
malware.
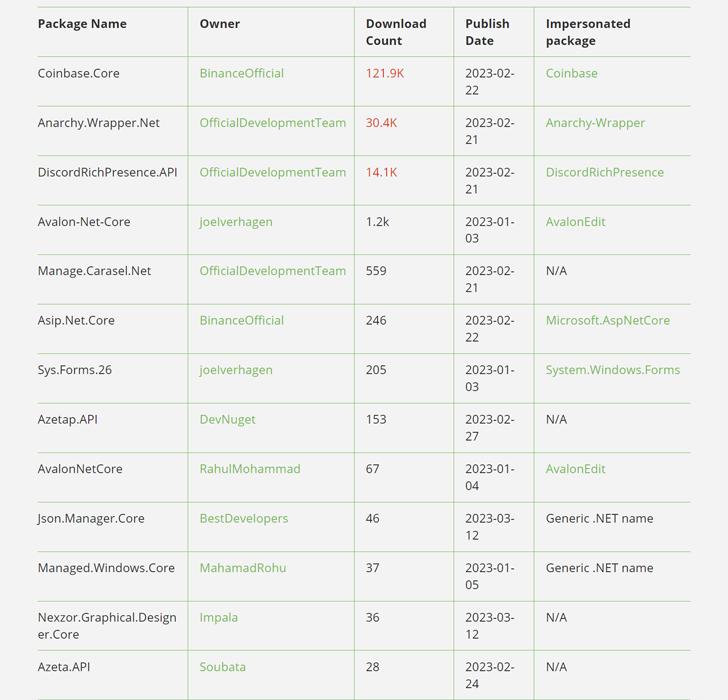
The
13
rogue
packages,
which
were
downloaded
more
than
160,000
times
over
the
past
month,
have
since
been
taken
down.
“The
packages
contained
a
PowerShell
script
that
would
execute
upon
installation
and
trigger
a
download
of
a
‘second
stage’
payload,
which
could
be
remotely
executed,”
JFrog
researchers
Natan
Nehorai
and
Brian
Moussalli
said.
While
NuGet
packages
have
been
in
the
past
found
to
contain
vulnerabilities
and
be
abused
to
propagate
phishing
links,
the
development
marks
the
first-ever
discovery
of
packages
with
malicious
code.
Three
of
the
most
downloaded
packages
–
Coinbase.Core,
Anarchy.Wrapper.Net,
and
DiscordRichPresence.API
–
alone
accounted
for
166,000
downloads,
although
it’s
also
possible
that
the
threat
actors
artificially
inflated
the
download
counts
using
bots
to
make
them
appear
more
legitimate.
The
use
of
Coinbase
and
Discord
underscores
the
continued
reliance
on
typosquatting
techniques,
in
which
fake
packages
are
assigned
names
that
are
similar
to
legitimate
packages,
in
order
to
trick
developers
into
downloading
them.
The
malware
incorporated
within
the
software
packages
functions
as
a
dropper
script
and
is
designed
to
automatically
run
a
PowerShell
code
that
retrieves
a
follow-on
binary
from
a
hard-coded
server.
As
an
added
obfuscation
mechanism,
some
packages
did
not
embed
a
malicious
payload
directly,
instead
fetching
it
via
another
booby-trapped
package
as
a
dependency.
Even
more
troublingly,
the
connection
to
the
command-and-control
(C2)
server
occurs
over
HTTP
(as
opposed
to
HTTPS),
rendering
it
vulnerable
to
an
adversary-in-the-middle
(AiTM)
attack.
The
second-stage
malware
is
what
JFrog
describes
as
a
“completely
custom
executable
payload”
that
can
be
dynamically
switched
at
will
since
it’s
retrieved
from
the
C2
server.
WEBINAR
Discover
the
Hidden
Dangers
of
Third-Party
SaaS
Apps
Are
you
aware
of
the
risks
associated
with
third-party
app
access
to
your
company’s
SaaS
apps?
Join
our
webinar
to
learn
about
the
types
of
permissions
being
granted
and
how
to
minimize
risk.
The
second-stage
delivers
several
capabilities
that
include
a
crypto
stealer
and
an
auto-updater
module
that
pings
the
C2
server
for
an
updated
version
of
the
malware.
The
findings
come
as
the
software
supply
chain
has
become
an
increasingly
lucrative
pathway
to
compromise
developers’
systems
and
stealthily
propagate
backdoored
code
to
downstream
users.
“This
proves
that
no
open
source
repository
is
safe
from
malicious
actors,”
Shachar
Menashe,
senior
director
at
JFrog
Security
Research,
said
in
a
statement
shared
with
The
Hacker
News.
“.NET
developers
using
NuGet
are
still
at
high
risk
of
malicious
code
infecting
their
environments
and
should
take
caution
when
curating
open-source
components
for
use
in
their
builds
–
and
at
every
step
of
the
software
development
lifecycle
–
to
ensure
the
software
supply
chain
remains
secure.”