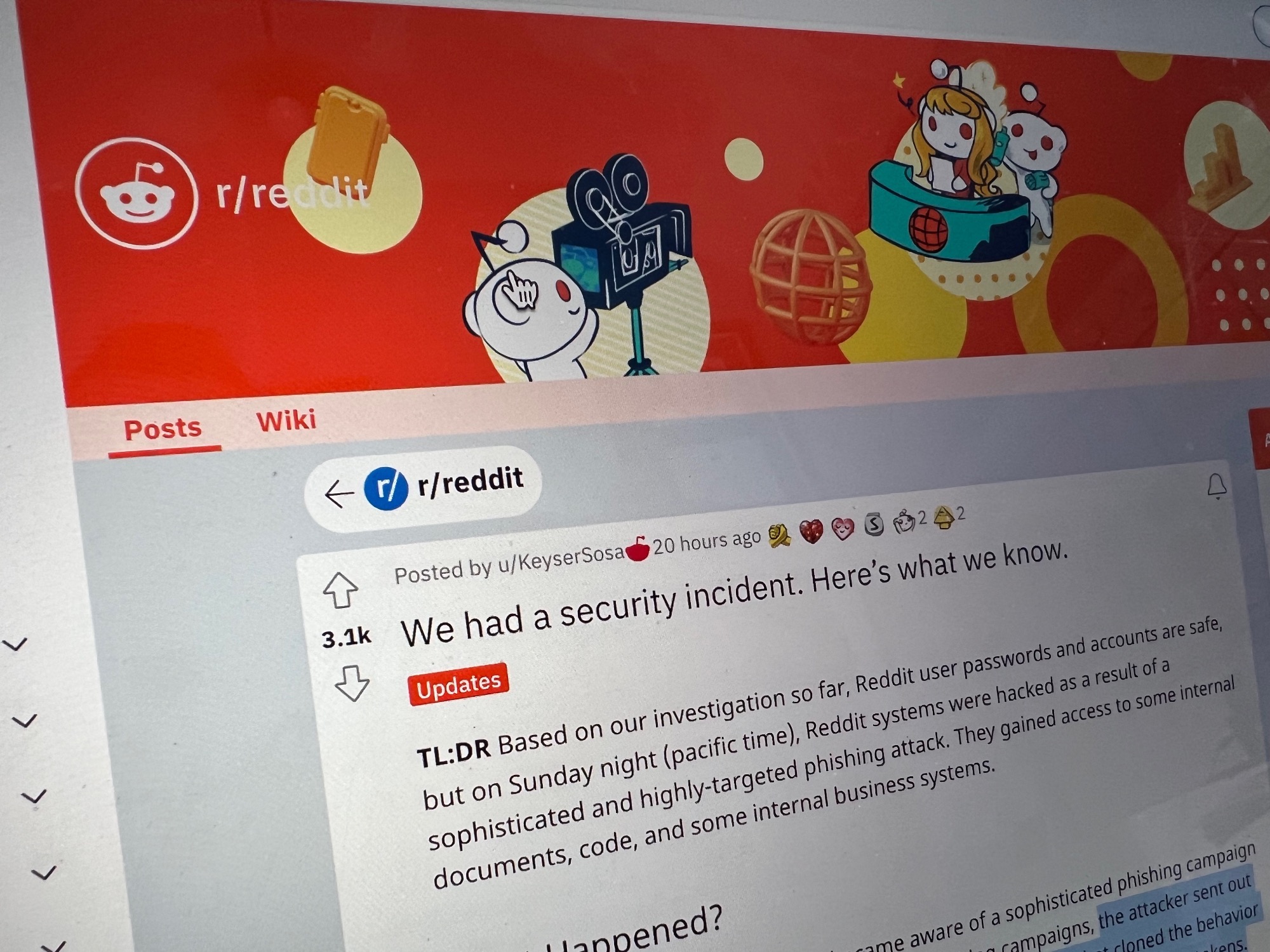
The
latest
hack
of
a
well-known
company
highlights
that
attackers
are
increasingly
finding
ways
around
multifactor
authentication
(MFA)
schemes
—
so
employees
continue
to
be
an
important
last
line
of
defense.
On
Jan.
9,
Reddit
notified
its
users
that
a
threat
actor
had
successfully
convinced
an
employee
to
click
on
a
link
in
an
email
sent
out
as
part
of
a
spearphishing
attack,
which
led
to
“a
website
that
cloned
the
behavior
of
our
intranet
gateway,
in
an
attempt
to
steal
credentials
and
second-factor
tokens.”
The
compromise
of
the
employee’s
credentials
allowed
the
attacker
to
sift
through
Reddit’s
systems
for
a
few
hours,
accessing
internal
documents,
dashboards,
and
code,
Reddit
stated
in
its
advisory.
The
company
continues
to
investigate,
but
there’s
no
evidence
yet
that
the
attacker
gained
access
to
user
data
or
production
systems,
Reddit
CTO Chris
Slowe
(aka KeyserSosa) stated
on
a
follow-up
AMA.
“It
is
extremely
difficult
to
prove
a
negative,
and
also
why,
as
mentioned,
we
are
continuing
investigating,”
he
said.
“The
burden
of
proof
right
now
supports
that
access
was
limited
to
outside
of
the
main
production
stack.”
Reddit
is
the
latest
software
company
to
fall
prey
to
a
social
engineering
attack
that
harvested
workers’
credentials
and
led
to
a
breach
of
sensitive
systems.
In
late
January,
Riot
Games,
the
maker
of
the
popular
League
of
Legends
multiplayer
game,
announced
it
had
suffered
a
compromise
“via
a
social
engineering
attack,”
with
the
threat
actors
stealing
code
and
delaying
the
company’s
ability
to
release
updates.
Four
months
earlier,
attackers
successfully
compromised
and
stole
source
code
from
Take
Two
Interactive’s
Rockstar
Games
studio,
the
maker
of
the
Grand
Theft
Auto
franchise,
using
compromised
credentials.
The
cost
of
even
minor
breaches
caused
by
phishing
attacks
and
credential
theft
continues
to
be
high.
In
a
survey
of
1,350
IT
professionals
and
IT
security
managers,
three-quarters
(75%)
said
that
their
company
had
suffered
a
successful
email
attack
in
the
past
year,
according
to
the
“2023
Email
Security
Trends”
report
published
by
Barracuda
Networks,
a
provider
of
application
and
data
protection.
In
addition,
the
average
firm
saw
its
most
expensive
such
attack
cause
more
than
$1
million
in
damages
and
recovery
costs.
Still,
companies
feel
prepared
to
deal
with
both
phishing
and
spear-phishing,
with
only
26%
and
21%
of
respondents
fearing
they
were
unprepared.
That’s an
improvement
from
the
47%
and
36%,
respectively,
who
worried
their
firms
were
unprepared
in
2019.
Concerns
over
account
takeover
have
become
more
common
though,
the
report
found.
“[W]hile
organizations
may
feel
better
equipped
to
prevent
phishing
attacks,
they
are
not
as prepared
to
deal
with
account
takeover,
which
is
usually
a
by-product
of
a
successful
phishing
attack,”
the
report
stated.
“Account
takeover
is
also
a
bigger
concern
for
organizations
with
the
majority
of
their
employees
working
remotely.”
More
Proof
That
2FA
is
Not
Enough
To
head
off
credential-based
attacks,
companies
are
moving
to
MFA,
usually
in
the
form
of two-factor
authentication
(2FA),
where
a
one-time
password
is
sent
via
text
or
email. Reddit’s
Slowe,
for
example,
confirmed
that
the
company
required
2FA.
“Yup.
It’s
required
for
all
employees,
both
for
use
on
Reddit
as
well
for
all
internal
access,”
he
said
during
the
AMA.
But
techniques
like
MFA
fatigue
or
“bombing”
—
as
seen
with
last
fall’s
Uber
attack
—
make getting
around
2FA
a
simple
numbers
game.
In
that
scenario,
the
attackers
send
out
repeated
targeted
phishing
attacks
to
employees
until
someone
gets
tired
of
the
notifications
and gives
up
their
credentials
and
the
one-time
password
token.
Moving
to
the
next
level
beyond
2FA
is
starting
to
happen. Providers
of
identity
and
access
management
technologies,
for
instance, are
adding
more
information
around
access
requests,
such
as
the
user’s
location,
to
add
context
that
can
be
used
to
help
determine
whether
access
should
be
authenticated,
says
Tonia
Dudley,
CISO
at
Cofense,
a
phishing
protection
firm.
“Threat
actors
will
always
look
for
ways
to
navigate
around
the
technical
controls
we
implement,”
she
says. “Organizations
should
still
implement
the
use
of
MFA
and
continue
to
tune
the
control
to
protect
employees.”
Employees
Are
Key
to
Cyber
Defense
Ironically,
the
Reddit
hack
also
demonstrates
the
advantages
that
employee
training
can
deliver.
The
employee
suspected
something
was
wrong
after
entering
credentials
into
the
phishing
site,
and
soon
after
contacted
Reddit’s
IT
department.
That reduced
the
attacker’s
window
of
opportunity
and
limited
the
damage.
“It’s
time
we
stop
looking
as
employees
as
a
weakness
and
instead
looking
at
them
as
the
strength
they
are,
or
can
be,
for
organizations,”
Dudley says.
“Organizations
can
only
tune
the
technical
controls
so
far
…
employees
can
offer
that
additional
context
of,
‘this
just
doesn’t
seem
right.'”
The
employee
at
the
center
of
the
Reddit
breach
will
not
face
long-term,
punitive
action,
but
did
have
all
access
revoked
until
the
problem
was
resolved,
Reddit’s
Slowe
said
in
the
follow-up
AMA.
“The
problem,
as
ever,
is
that
it
only
takes
one
person
to
fall
for
[a
phish],”
he
said,
adding,
“I’m
exceedingly
grateful
the
employee,
in
this
case,
reported
that
it
happened
when
they
realized
it
happened.”








