An
unknown
threat
actor
is
targeting
government
organizations
with
the
PureCrypter
downloader,
Menlo
Security
firm
reported.
Menlo
Labs
researchers
uncovered
an
unknown
threat
actor
is
using
the
PureCrypter
downloader
in
attacks
aimed
at
government
entities.
The
campaign
relies
on
the
domain
of
a
compromised
non-profit
organization
as
a
C2
server
to
deliver
a
second-stage
payload.
The
malware
campaign
delivers
multiple
malware,
including
Redline
Stealer,
AgentTesla,
Eternity,
Blackmoon
and
Philadelphia
Ransomware.
The
experts
spotted
multiple
attempts
of
delivering
malware
to
several
government
customers
in
the
Asia-Pacific
(APAC)
and
North
America.
PureCrypter is
an
sophisticated
downloader
that
is
used
to
downloads
Remote
Access
Trojans
(RATs)
and
Infostealers.
It
is
available
for
sale
since
March
2021
on“hxxps[://]purecoder.sellix.io/.”
“Menlo
Labs
has
uncovered
an
unknown
threat
actor
that’s
leveraging
an
evasive
threat
campaign
distributed
via
Discord
that
features
the
PureCrypter
downloader
and
targets
government
entities.”
reads
the
analysis
published
by
Menlo
Labs.
“In
our
investigation,
we
found
that
AgentTesla
establishes
a
connection
to
an
FTP
server
where
it
stores
the
stolen
victim’s
credentials.
The
FTP
server
appears
to
have
been
taken
over
and
the
leaked
credentials
for
the
domain
were
found
online,
thus
suggesting
that
the
threat
actors
used
these
credentials
to
gain
access
to
the
server.”
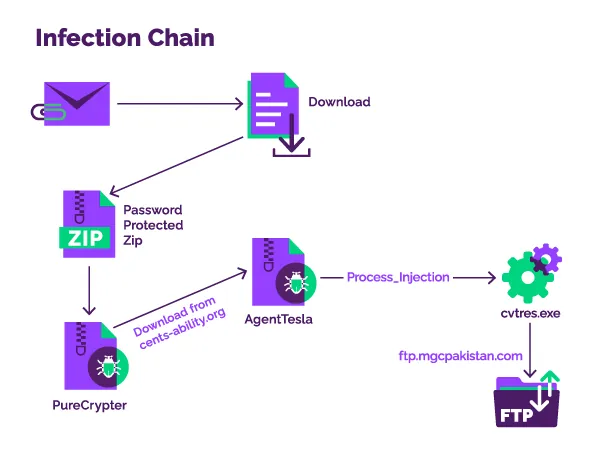
The
attack
chain
starts
with
spear
phishing
emails
containing
Discord
app
URL
that
points
to
a
password-protected
ZIP
archive
containing
the
PureCrypter
malware.
Upon
executing
the
downloader,
it
fetches
the
second-stage
payload
from
the
C2,
which
was
a compromised
server
of
a
non-profit
organization
in
the
attack
observed
by
the
researchers.
In
the
attack
analyzed
by
Menlo
Security,
the
final
payload
was
AgentTesla.
Agent
Tesla is
a
“commodity
malware”.
It
is
a
fully
customizable
password
info-stealer
and
many
cyber
criminals
are
choosing
it
as
their
preferred
recognition
tool.
Once
executed,
the
AgentTesla
sample
employed
in
the
attack
detailed
by
Menlo
researchers
connects
to
a
Pakistan-based
FTP
server
that
is
used
to
receive
the
stolen
data.
AgentTesla
version
used
by
the
attackers
supports
a process
hollowing technique
to
inject
its
payload
into
cvtres.exe,
which
is
a
standard
windows
process.
The
malware
uses
an
XOR
algorithm
to
encrypt
its
config
file.
The
good
news
is
that
the
experts
were
able
to
decrypt
the
file
which
contains
the
CnC
details
of
the
FTP
server
to
which
AgentTesla
uploads
the
victim
data.
“This
threat
actor
doesn’t
appear
to
be
a
major
player
in
the
threat
landscape,
but
the
targeting
of
government
entities
is
surely
a
reason
to
watch
out
for
them.”
concludes
the
report.
Follow
me
on
Twitter:
@securityaffairs
and
Facebook
and
Mastodon
(SecurityAffairs –
hacking,
PureCrypter)