Protecting
yourself
form
Cyber
Attacks
If
you
have
a
Digital
Presence
and
you
want
to
learn
to
secure
yourself
and
your
organization
then
don’t
miss
out
this
session.
When:
28
January
10
;00
AEST
(Sydney
)
27
January
18;00
EST
(New
York)
Registration:
Click
Here
Protect
Yourself
from
Cyber
Attacks
In
this
digital
age,
we
are
all
possible
victims
of
cyber-attacks
.
A
cyber-attack
is
an
attempt
to
steal,
destroy,
alter,
or
perform
other
malicious
acts
by
obtaining
unauthorized
access
to
a
computer
and
its
system
or
network.
In
other
words,
someone’s
trying
to
steal
your
stuff.
Cyber-attacks
can
come
in
many
different
forms,
putting
your
computer,
devices,
and
the
home
network
they’re
connected
to
at
risk.
This
is
a
session
that
everyone
should
watch!
If
you
are
a
member
of
any
Social
Network
web
site,
then
this
session
is
for
you.
When
I
say
social
media,
it
does
not
just
include
Facebook,
but
also
LinkedIn
or
any
Social
media
web
site
that
you
can
think
of.

Yourself
from
Cyber
Attacks
Did
you
say
you
are
not
a
member
of
any
Social
Media
web
site?
No
problem,
but
what
about
your
loved
ones?
Are
they,
do
they
share
your
photos
or
your
common
information,
then
guess
what
you
are
part
of
the
network,
so
there
is
still
something
for
you
in
this
session
This
session
is
built
to
show
you
the
basics
and
let
you
understand
how
bad
guys
work
on
collecting
information.
If
you
listen
to
us
then
you
can
be
more
secure…
We
have
arrived
in
a
time
where
social
networks
have
become
an
essential
part
of
our
lives.
People
are
spending
a
great
deal
of
time
connecting
with
organizations,
businesses,
and
individuals
all
over
the
world.
But
there
is
a
dark
side
to
social
networks!
How
do
you
protect
your
business
or
yourself
from
zombies,
bullies,
hackers,
scammers,
stalkers,
and
other
cyber-criminals?
In
this
eye
opening
and
sometime
surprising
journey
we
venture
down
the
dark
path
into
the
very
heart
of
Facebook
and
other
platforms
to
discover
how
they
really
work,
as
well
as
offer
tips,
tricks,
and
practical
advice
on
Social
Networking
Security.
For
more
free
events
,
click
here
What
are
the
different
types
of
cyber-attacks?
Source:
Microsoft
There’s
no
one-size-fits-all
way
to
steal
information.
If
this
were
the
case,
we’d
have
figured
out
a
fool-proof
way
to
protect
ourselves
long
ago.
Hackers
will
use
various
methods
to
illegally
access
your
private
information—either
to
use
for
themselves—or
to
sell
to
the
highest
bidder
on
the dark
web.
Below
you’ll
find
some
common
types
of
cyber-attacks
and
how
they
work,
so
you
know
what
you’re
up
against:
-
Malware. Malware
in
and
of
itself
is
a
diverse
method
of
cyber-attack,
as
there
are
many
types.
The
term
“malware”
is
short
for
“malicious
software”
and
is
one
of
the
most
common
types
of
attacks
you’ll
encounter.
Viruses
from
worms,
spyware,
adware,
Trojans,
and
ransomware
each
work
a
little
bit
differently
but
will
accomplish
the
criminal’s
final
goal
of
accessing
information
stored
on
your
computer
or
others
connected
to
your
network. -
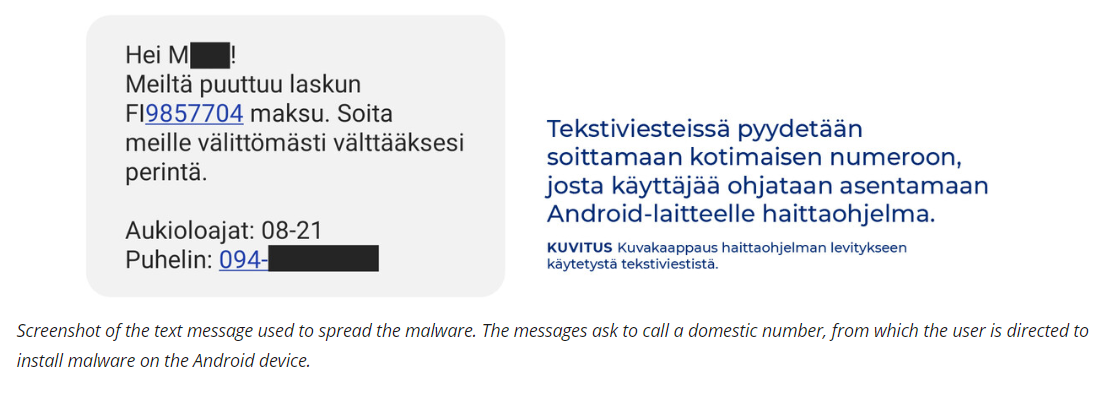
Phishing It’s
not
uncommon
to
get
dozens
to
hundreds
of
emails
every
day,
many
of
which
are
quickly
deleted
without
a
second
thought
because
they’re
often
promotional
emails
or
other
forms
of
spam.
When
it
comes
down
to
it,
it’s
not
a
bad
idea
to
send
many
of
those
emails
to
your
trash
folder
throughout
the
day
because
many
of
those
emails
could
be
a
message
with
a
link
to
a
website
ready
to
install
malware
onto
your
computer
or
mobile
device
as
soon
as
you
enter.
This
practice
is
called
phishing,
and
there
are approximately
80,000
people
who
are
victims
of
it
every
day. -
Zero-day
exploit. Software
developers
and
service
providers
are
made
aware
of
a
vulnerability
and
then
will
often
work
tirelessly
to
come
up
with
a
solution
to
the
problem.
However,
it’s
not
uncommon
for
them
to
make
you
aware
of
the
weakness
in
their
system
to
ensure
they’re
taking
preventative
measures
until
the
weakness
is
addressed.
The
problem
with
letting
you
know
is
that
cybercriminals
are
also
made
aware
of
their
weaknesses.
When
they
attack
these
weak
links,
it’s
known
as
a
zero-day
exploit
because
it
happens
before
a
new
security
measure
is
rolled
out.
Learn
how
to
prepare
for
a
cyber-attack.
Cyber-attacks
happen
so
frequently
these
days
that
the
general
consensus
among
the
cyber
security
community
is
that
it’s
not
a
matter
of
if
you’re
the
victim
of
an
attack
but
when.
The
inevitability
of
a
cyber-attack
means
that
you
need
to
be
prepared.
You
can
do
several
things
to
prepare
your
computer
to
protect
your
personal
information
from
an
attack.
-
Use
multi-factor
authentication (MFA). Multi-factor
authentication
is
a
system
that
requires
users
to
combine
two
or
more
credentials
to
log
into
a
system.
The
credentials
for
logging
in
can
include
something
the
user
knows,
like
a
password,
something
the
user
has,
like
a
dynamic
security
code,
or
biometric
verification
with
a
facial
scan,
fingerprint,
or
something
else.
The
use
of
two
or
more
of
these
credentials
makes
it
more
difficult
for
cybercriminals
to
compromise
protected
information. -
Install
antivirus
software and
a
firewall. Antivirus
software
and
a
firewall
are
useful
in
identifying
threats
when
they’re
inbound
to
your
network.
Whether
it
be
malware
you’ve
accidentally
downloaded
from
a
website,
or
a
hacker
is
trying
to
access
your
password
by
infiltrating
your
computer
network,
antivirus
software
and
a
firewall
are
designed
to
protect
you.
An
essential
part
of
having
antivirus
software
is
ensuring
that
it
stays
up
to
date
because
cyber-attacks
are
always
evolving
to
try
to
beat
the
latest
and
greatest
protection
measures. -
Educate
yourself. Antivirus
software
can
only
do
so
much
to
keep
your
computer
safe
from
a
cyber-attack,
so
one
of
the
best
ways
to
protect
yourself
from
cyber-attacks
is
by
knowing
what
puts
you
at
risk
of
an
attack.
Practice
and teach
your
kids
about
healthy
tech
habits and
avoid
doing
things
like
clicking
links
from
random
websites
or
messages
on
your
smartphone,
visiting
websites
you’re
not
familiar
with,
leaving
your
computer
unlocked
when
you
step
away
from
the
keyboard,
and
other
behaviors
can
put
you
at
risk
of
a
data
breach.
Knowing
how
to
avoid
a
cyber-attack
can
go
a
long
way
toward
protecting
yourself.
Protecting
yourself
form
Cyber
Attacks
–
Free
webinar
Protect
Yourself
from
Cyber
Attacks
10
ways
to
prevent
cyber
attacks
–
how
to
prevent
cyber
attacks
at
home
–
how
to
prevent
cyber
attacks
on
businesses
–
how
to
prevent
cyber
attacks
pdf
–
how
can
you
protect
yourself
and
your
computer
data
from
cyber
attacks
or
hackers
How
will
you
protect
yourself
from
cyber-attacks?
What
are
the
five
5
basic
principles
of
cyber
security?