
A
new
version
of
the
Prilex
POS
malware
has
found
a
novel
way
to
steal
your
credit
card
information.

WhataWin/Adobe
Stock
According
to
Kaspersky,
Prilex
is
a
Brazilian
threat
actor
that
initially
began
in
2014
as
an
ATM-related
malware
and
later
switched
to
modular
point-of-service
malware.
The
threat
actor
was
responsible
for
one
of
the
biggest
attacks
on
ATMs
in
Brazil,
infecting
and
jackpotting
more
than
1,000
machines
and
cloning
more
than
28,000
credit
cards
used
in
the
ATMs.
SEE:
Mobile
device
security
policy
(TechRepublic
Premium)
Prilex
is
particularly
experienced
with
payment
markets,
electronic
funds
transfer
software
and
protocols,
and
the
threat
actor
has
recently
updated
its
POS
malware
to
block
contactless
transactions
to
steal
your
credit
card
information.
Jump
to:
What’s
new
in
the
latest
Prilex
malware
Contactless
payment
methods
have
become
incredibly
popular,
especially
since
the
COVID-19
pandemic
when
people
wished
to
touch
as
public
surfaces
as
possible.
Such
payments
require
the
credit
card
to
be
really
close
to
the
payment
device,
which
is
typically
a
POS
terminal.
As
contactless
payments
are
not
handled
by
the
POS
terminal
in
the
same
way
as
usual
payments,
it’s
not
possible
for
cybercriminals
to
abuse
and
make
fraudulent
use
of
the
system.
This
resulted
in
cybercriminals’
POS
malware
seeing
a
huge
decrease
in
the
number
of
transactions
it
could
abuse.
Prilex
malware
developers
have
found
a
way
to
deal
with
this
problem:
The
malware,
once
it
sees
a
contactless
transaction
happen,
blocks
it.
The
PIN
pad
then
tells
the
user
that
there
is
a
contactless
error
and
that
the
payment
needs
to
be
done
by
inserting
the
credit
card.
Once
the
victim
pays
by
card,
a
GHOST
transaction
fraud
can
be
operated
by
Prilex.
In
GHOST
transactions,
the
malware
sits
on
the
device,
intercepting
all
communications
between
the
POS
software
and
the
PIN
pad.
Once
a
transaction
is
ongoing,
the
malware
intercepts
the
transaction
content
and
modifies
it
in
order
to
capture
the
credit
card
information
and
request
new
EMV
cryptograms
to
the
victims
card.
The
new
EMV
cryptogram
enables
the
attacker
to
initiate
a
new
fraudulent
transaction
from
a
POS
device
they
own
(Figure
A).
Figure
A
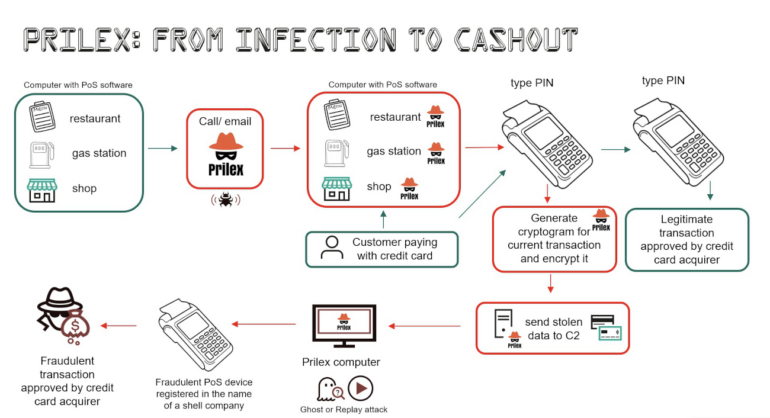
Kaspersky.
GHOST
transaction
attack
scheme
as
executed
by
the
Prilex
threat
actor.
How
do
POS
malware
infections
work?
POS
malware
is
not
your
average
malware.
Developing
it
requires
a
deep
understanding
of
the
whole
payment
market
as
well
as
its
protocols,
tools
and
deployment.
As
such
malware
is
useless
on
usual
endpoints,
it
needs
to
be
executed
on
the
computers
who
actually
run
the
POS
software
and
deal
with
payments.
The
cybercriminals
behind
advanced
POS
malware
cannot
just
send
phishing
emails
to
infect
computers;
they
need
to
target
specific
people
and
use
social
engineering
schemes
to
entice
the
victim
to
install
a
legitimate
remote
desktop
application
before
infecting
it.
This
explains
why
the
fraudsters
generally
pretend
to
be
technicians
who
need
to
update
the
legitimate
POS
software.
How
to
protect
your
organization
from
this
threat
The
end
customer
can
not
do
anything
against
the
threat,
as
it
happens
on
infected
devices
that
they
can’t
control.
All
protection
must
come
from
administrators
of
POS
software.
As
a
company
using
POS
systems,
establish
a
detailed
process
with
the
POS
provider
in
order
to
avoid
any
social
engineering
scams.
All
contacts
between
the
POS
software
customer
and
the
POS
software
provider
need
to
follow
specific
rules
that
should
be
discussed
over
a
secure
channel
and
known
by
anyone
who
could
access
the
devices
running
the
POS
software.
Should
any
cybercriminal
call
and
pretend
to
be
an
employee
of
the
POS
software
supplier,
this
would
help
to
immediately
discover
them.
Security
solutions
should
be
deployed
on
all
devices
running
POS
software
to
try
to
detect
malware
infection.
As
information
is
sent
from
an
infected
POS
device
to
an
attacker
owned
C2,
network
communications
should
also
be
monitored
in
order
to
detect
any
suspicious
activity
that
could
be
a
communication
between
a
malware
and
a
C2
server.
Finally,
all
software
and
operating
systems
should
always
be
up
to
date
and
patched
in
order
to
avoid
compromise
by
common
vulnerabilities.
Disclosure:
I
work
for
Trend
Micro,
but
the
views
expressed
in
this
article
are
mine.









