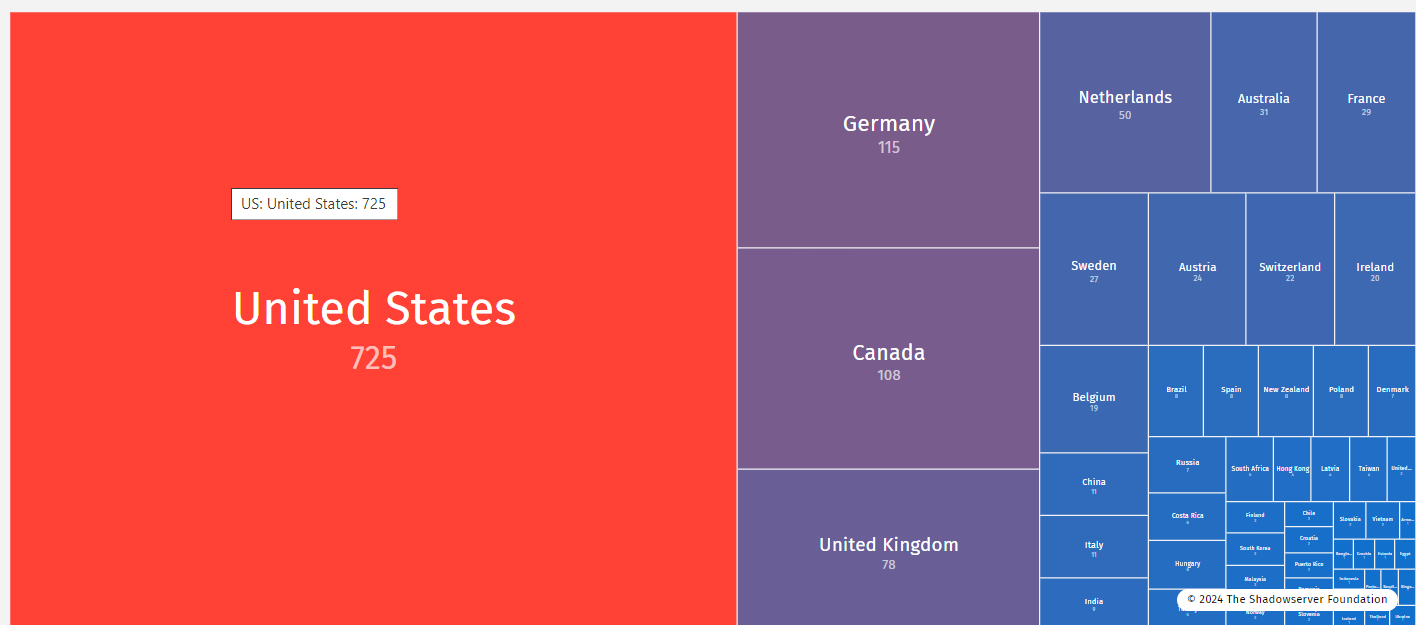
Why
ransomware
matters
in
today’s
threat
landscape
Cybercrime
is
becoming
increasingly
sophisticated
and
broader
in
scope.
Phishing
attacks
may
have
been
around
since
the
dawn
of
email,
but
they
persist.
Those
carrying
out
attacks
are
searching
for
the
smallest
of
openings
to
break
into
an
organizations’
infrastructure
to
facilitate
enormous
financial
rewards.
Today,
75
percent
of
cyber
attacks
originate
from
email,
and
attackers
are
working
together
to
launch
joint
attacks
on
large
organizations.
Once
malware
threat
actors
have
used
phishing
emails
to
infect
organizations’
machines
and
networks,
attacks
spread
laterally,
with
access
sold
to
ransomware
brokers.
According
to
Verizon’s
Data
Breach
Investigation’s
report
2022,
web
applications
and
email
remain
the
top
two
vectors
for
breaches.
Meanwhile,
Cyber
Security
Hub’s
own
survey
on
the
top
cyber-security
trends
in
2022
shows
that
phishing
and
social
engineering
attacks
are
among
the
greatest
threats
facing
organizations
today,
with
more
than
70
percent
of
respondents
citing
it
as
one
of
their
top
three
cyber-security
threats
(see
Figure
1).
Ransomware
groups
are
conscious
to
the
fact
that
large
corporations
are
more
likely
to
pay
multi-million-dollar
ransoms,
but
national
governments
cannot
rest
on
their
laurels
either;
in
2021,
Cyber
Research
Labs
documented
48
government
agencies
spanning
21
countries
that
were
affected
by
ransomware.
Figure
1:
What
are
the
three
most
dangerous
cyber
security
threats
your
organization
faces
today?

Threat
actor’s
tactics
are
becoming
ever
more
sinister.
When
combined
with
the
migration
to
cloud
email
access
–
which
comes
with
its
own
security
implications
–
it
is
more
important
than
ever
to
detect
and
block
malicious
actors
from
compromising
businesses
data
and
information
via
email
attacks.
Also
read:
Five
biggest
ransomware
attacks
you
need
to
know
about
In
this
Cyber
Security
Hub
article
you
will
learn
where
the
key
vulnerabilities
lie
for
those
without
sufficient
email
security,
how
to
successfully
detect
a
security
breach
before
it
leads
to
data
loss,
information
loss
and
email
fraud,
and
how
to
block
threat
actors
from
carrying
out
successful
attacks.
It
will
delve
into
today’s
best
practices
and
solutions
to
ensure
your
email
security.
Ignore
email
security
at
your
peril
As
the
ransomware-as-a-service
(RaaS)
economy
matures,
ransomware
gangs
are
demonstrating
supreme
confidence
in
their
debilitating
actions.
Recently,
Costa
Rica’s
government
was
held
hostage
by
the
Conti
Group,
which
demanded
a
US$20m
ransom
and
threatened
to
overthrow
the
government
if
their
demands
were
not
met.
Other
types
of
attacks
using
email
as
a
vector
include
business
email
compromise
(BEC),
spam
and
botnets.
According
to
a
US
Federal
Bureau
of
Investigation
(FBI)
report
from
May
2022,
BEC
scams
represented
a
$43bn
loss
across
both
international
and
domestic
US
organizations
between
June
2016
and
December
2022.
During
that
timeframe
the
FBI
was
alerted
to
more
than
240,000
BEC
incidents.
Verizon
has
also
noted
a
13
percent
increase
in
ransomware
breaches
in
2022.
Despite
these
facts,
email
remains
an
area
much
ignored
by
many
organizations
around
the
globe.
In
terms
of
the
data
that
is
being
targeted,
during
the
early
phase
of
an
attack,
low-level
data
may
be
the
target.
Ultimately,
however,
groups
are
looking
to
steal
more
sensitive
data
which
influences
who
they
are
targeting.
One
example
lies
with
human
resources
(HR),
as
hackers
may
pose
as
job
seekers
in
the
hope
that
HR
personnel
will
open
emails
and
attachments
from
unknown
senders,
allowing
the
ransomware
to
spread.
Attackers
then
have
access
to
confidential
and
sensitive
company
information.
While
it
is
important
to
implement
security
measures
that
are
offered
by
email
providers,
for
example,
there
are
additional
tactics
you
should
consider
beyond
the
traditional
security
stack
which
we
will
consider
further
in
this
article.
Employing
a
strategy
to
overcome
evolving
ransomware
threats
To
overcome
changing
defensive
tactics,
attackers
will
always
look
for
new
avenues
in
which
to
exhibit
their
criminal
abilities.
One
such
method,
telephone-oriented
attack
delivery
(TOAD),
does
not
have
a
payload
but
uses
a
phone
number
that
when
called,
a
bad
actor
will
answer
and
direct
their
victim
to
manually
download
malicious
content,
thus
infecting
their
computer
with
ransomware.
As
the
challenges
change,
organizations
need
to
treat
the
playing
field
as
if
it
will
never
be
fair
to
them.
By
adding
layers
to
their
security
strategies,
however,
they
stand
a
good
chance
of
deterring
ransomware
gangs.
There
is
no
silver
bullet
for
the
challenge,
however,
with
email
compromises
growing
exponentially
due
to
ever
more
sophisticated
methods
and
automation
that
goes
beyond
scanning,
blocking
and
identifying
bad
actors
sending
messages.
Adding
layers
such
as
DMARC
email
authentication
to
have
a
better
chance
of
stopping
email
fraud
or
BEC
in
its
tracks,
implementing
isolation
training
for
at-risk
users
that
aligns
with
their
email
risk,
or
isolation
of
URLs
clicked
on
from
email.
Other
methods
include
mSOAR
–
the
automatic
remediation
of
malicious
messages
post-delivery;
abuse
mailbox
automation;
and
enhanced
data
protection
such
as
email
DLP
and
encryption.
Everyone
is
a
target
Everyone
within
a
company,
from
interns
to
the
CEO,
are
prime
targets
for
threat
actors
seeking
access
to
deploy
ransomware.
Even
gaining
access
to
a
small
foothold
in
a
business
using
a
compromised
employee
account
can
have
devastating
consequences.
Malicious
actors
can
move
laterally,
escalating
the
priviledges
they
have
access
to
until
they
have
the
ability
to
take
over
a
company’s
entire
enterprise
network.
Best
practices
for
alert
organizations
A
comprehensive
email
security
strategy
can
easily
be
implemented,
but
it
will
require
employees
to
use
strong
passwords
and
utilize
email
encryption
for
both
email
content
and
attachments.
Security
best
practices
for
BYOD
should
also
be
employed
by
companies
that
allow
their
employees
access
to
corporate
email
on
personal
devices.
To
protect
employees
against
advanced
threats,
organizations
should
use
malware
sandbox
analysis
inline
and
to
not
forward
emails
until
they
have
been
checked.
Companies
should
also
implement
software
to
scan
incoming
communications
and
block
those
that
contain
malicious
software.
When
an
email
account
is
compromised
it
has
the
potential
to
cause
a
huge
amount
of
damage
in
potential
data
loss
or
attacks
launched
from
a
compromised
email
account
to
other
internal
or
third-party
users.
In
these
cases,
having
a
cloud
access
security
broker
(CASB)
solution
can
help
identify
and
remediate
potentially
suspicious
logins.
Organizations
can
also
benefit
from
joint
integration
with
identity
access
management
vendors
to
automatically
reset
passwords
in
cases
where
credentials
have
been
potentially
compromised.
Proofpoint’s
experts
recommend
enforcing
stricter
authentication
for
users
who
receive
targeted
attacks.
Firms
can
additionally
implement
a
data
protection
solution
to
identify
sensitive
data
and
prevent
it
from
being
lost
via
email.
This
is
because
malware
developers
are
leasing
out
their
skills
to
affiliates
who
use
turn-key
solutions
to
infect
victims.
In
turn,
it
is
becoming
easier
and
more
profitable
for
less-skilled
criminals
to
seize
enterprise
networks
with
military-grade
encryption
and
demand
millions
for
the
key
to
the
files.
A
crucial
part
of
defense
against
malware
are
secure
backups,
as
threat
actors
may
attempt
to
poison
or
delete
backups
during
their
operations.
With
multi-layered
intrusions
the
new
normal,
organizations
should
always
assume
all
systems
are
important
enough
to
be
patched,
protected
and
monitored.
Conclusion:
understand
the
risks
and
act
Organizations
need
to
achieve
stronger
visibility
of
the
ransomware
threats
they
face,
but
also
ensure
their
workforces
are
alert
to
the
risks
they
are
exposed
to
through
education,
support
and
network
protections.
By
understanding
ransomware
risk
and
details
organizations
will
be
able
to
effectively
shift
their
approach
and
prevent
an
attack
from
happening.
The
solutions
exist
and
selecting
the
right
partners
helps
organizations
maintain
their
focus
on
their
own
goals
and
aims.
Solutions
such
as
Proofpoint’s
TAP
Dashboard
help
organizations
to
understand
their
security
postures
within
their
industries,
who
within
their
organizations
is
being
specifically
targeted,
and
with
what
type
of
malware
threats.
Most
threat
actors
are
motivated
by
financial
reward,
so
protecting
data
and
ensuring
staff
are
educated
should
never
be
up
for
debate.
Organizations
should
focus
on
behaviour
rather
than
artifacts
to
have
a
stronger
defence
against
ever-evolving
threats.
Finally,
a
people-centric
approach
to
ransomware
may
not
be
typical,
but
it
is
necessary
given
the
risks.
While
endpoints
and
other
technology
can
help
stop
ransomware
after
activated,
it
is
always
easier
to
stop
attacks
before
they
start.