Researchers
observed
threat
actors
deploying
PlugX
malware
by
exploiting
flaws
in
Chinese
remote
control
programs
Sunlogin
and
Awesun.
Researchers
at
ASEC
(AhnLab
Security
Emergency
response
Center)
observed
threat
actors
deploying
the
PlugX
malware
by
exploiting
vulnerabilities
in
the
Chinese
remote
control
software
Sunlogin
and
Awesun.
Sunlogin
RCE
vulnerability
(CNVD-2022-10270
/
CNVD-2022-03672)
is
known
to
be
exploited
by
threat
actors
since
an
exploit
code
was
disclosed.
In
the
past,
the
issue
was
exploited
in
attacks
to
deliver
Sliver
C2,
XMRig
CoinMiner,
and
Gh0st
RAT.
“The
same
threat
actors
performed
an
RCE
vulnerability
exploitation
on
both
Sunlogin
and
AweSun
to
install
Sliver
C2.”
reads
the
analysis
published
by
ASEC.
The
PlugX
backdoor
has
been
used
since
2008
by
multiple
China-linked
APT
groups,
including
Mustang
Panda,
Winnti,
and
APT41
In
the
attacks
observed
by
ASEC,
once
exploited
the
vulnerability,
threat
actors
executed
a
PowerShell
command
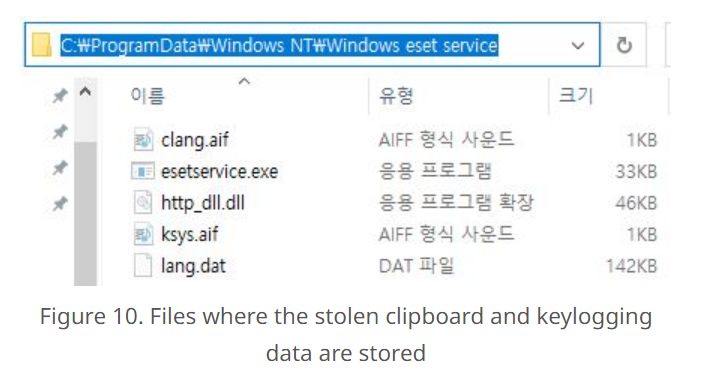
to
create
a
file
named
esetservice.exe.
esetservice.exe
is
actually
a
legitimate
HTTP
Server
Service
program
made
by
the
security
firm
ESET.
Attackers
also
downloaded
a
file
named
http_dll.dll
aside
from
esetservice.exe.
The
http_dll.dll
is
invoked
by
the
esetservice.exe
when
placed
in
the
same
directory,
in
a
classic
DLL
side-loading
attack.
The
DLL
acts
as
the
loader
for
the
PlugX
malware,
the
data
file
contains
the
actual
encoded
malware.
Experts
pointed
out
that
new
features
are
being
added
to
the
PlugX
malware,
threat
actors
use
it
to
gain
full
control
over
the
infected
system.
Attackers
uses
the
backdoor
to
conduct
a
broad
range
of
malicious
activities,
including
logging
key
inputs,
taking
screenshots,
and
installing
additional
malware.
“Therefore,
users
must
update
their
installed
software
to
the
latest
version
to
preemptively
prevent
vulnerability
exploitations.
Also,
V3
should
be
updated
to
the
latest
version
so
that
malware
infection
can
be
prevented.”
concludes
the
report
that
also
provides
Indicators
of
Compromise
(IoCs).
Follow
me
on
Twitter:
@securityaffairs
and
Facebook
and
Mastodon
(SecurityAffairs –
hacking,
malware)