Security
vulnerabilities
discovered
in
Honda’s
e-commerce
platform
could
have
been
exploited
to
gain
unrestricted
access
to
sensitive
dealer
information.
“Broken/missing
access
controls
made
it
possible
to
access
all
data
on
the
platform,
even
when
logged
in
as
a
test
account,”
security
researcher
Eaton
Zveare
said
in
a
report
published
last
week.
The
platform
is
designed
for
the
sale
of
power
equipment,
marine,
lawn
and
garden
businesses.
It
does
not
impact
the
Japanese
company’s
automobile
division.
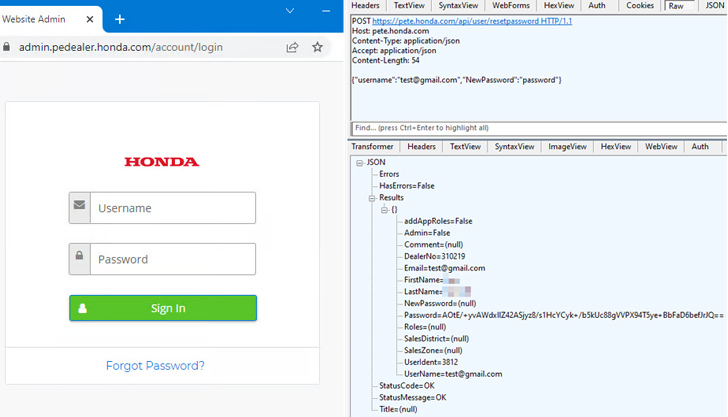
The
hack,
in
a
nutshell,
exploits
a
password
reset
mechanism
on
one
of
Honda’s
sites,
Power
Equipment
Tech
Express
(PETE),
to
reset
the
password
associated
with
any
account
and
obtain
full
admin-level
access.
This
is
made
possible
due
to
the
fact
that
the
API
allows
any
user
to
send
a
password
reset
request
simply
by
just
knowing
the
username
or
email
address
and
without
having
to
enter
a
password
tied
to
that
account.
Armed
with
this
capability,
a
malicious
actor
could
sign
in
and
takeover
another
account,
and
subsequently
take
advantage
of
the
sequential
nature
of
the
dealer
site
URLs
(i.e.,
“admin.pedealer.honda[.]com/dealersite/<ID>/dashboard)
to
gain
unauthorized
access
to
a
different
dealer’s
admin
dashboard.
“Just
by
incrementing
that
ID,
I
could
gain
access
to
every
dealers’
data,”
Zveare
explained.
“The
underlying
JavaScript
code
takes
that
ID
and
uses
it
in
API
calls
to
fetch
data
and
display
it
on
the
page.
Thankfully,
this
discovery
rendered
the
need
to
reset
any
more
passwords
moot.”
To
make
matters
worse,
the
design
flaw
could
have
been
used
to
access
a
dealer’s
customers,
edit
their
website
and
products,
and
worse,
elevate
privileges
to
the
administrator
of
the
entire
platform
–
a
feature
restricted
to
Honda
employees
–
by
means
of
a
specially
crafted
request
to
view
details
of
the
dealer
network.
UPCOMING
WEBINAR
🔐
Mastering
API
Security:
Understanding
Your
True
Attack
Surface
Discover
the
untapped
vulnerabilities
in
your
API
ecosystem
and
take
proactive
steps
towards
ironclad
security.
Join
our
insightful
webinar!
In
all,
the
weaknesses
allowed
for
illegitimate
access
to
21,393
customer
orders
across
all
dealers
from
August
2016
to
March
2023
1,570
dealer
websites
(of
which
1,091
are
active),
3,588
dealer
accounts,
1,090
dealer
emails,
and
11,034
customer
emails.
Threat
actors
could
also
leverage
access
to
these
dealer
websites
by
planting
skimmer
or
cryptocurrency
mining
code,
thereby
allowing
them
to
reap
illicit
profits.
The
vulnerabilities,
following
responsible
disclosure
on
March
16,
2023,
have
been
addressed
by
Honda
as
of
April
3,
2023.
The
disclosure
comes
months
after
Zveare
detailed
security
issues
in
Toyota’s
Global
Supplier
Preparation
Information
Management
System
(GSPIMS)
and
C360
CRM
that
could
have
been
leveraged
to
access
a
wealth
of
corporate
and
customer
data.