Experts
warn
of
a
new
wave
of
attacks
against
cryptocurrency
entities,
threat
actors
are
using
a
RAT
dubbed
Parallax
RAT
for
Infiltration.
Researchers
from
cybersecurity
firm
Uptycs warns
of
attacks
targeting
cryptocurrency
organizations
with
the
Parallax
remote
access
Trojan
(RAT).
Parallax
RAT
has
been
distributed
through
malvertising
and
phishing
campaigns
since
December
2019.
The
malware
supports
common
RAT
features,
such
as
keylogging,
capturing
login
credentials,
accessing
files,
and
remote
control
of
infected
systems.
The
sample
employed
in
recent
attacks
uses
injection
techniques
to
hide
within
legitimate
processes
and
avoid
detection.
Upon
successfully
injecting
the
malicious
code,
threat
actors
can
interact
with
their
victim
via
Windows
Notepad
that
likely
serves
as
a
communication
channel.
A
first
payload
analyzed
by
the
experts
is
written
in
C++,
it
is
in
the
form
of
a
32-bit
executable.
It
uses
the process-hollowing technique
to
inject
the
RAT
into
a
legitimate
Microsoft
pipanel.exe
process
“It
seems
to
have
been
intentionally
obfuscated
by
threat
actors
(TA)
wanting
to
hide
something.
Its
fifth
section
seems
to
have
been
altered
and
is
unusually
large
compared
to
the
remainder.”
reads
the
analysis
published
by
the
experts.
“Moreover,
this
section
has
been
marked
with
the
“Code
and
Executable”
flag,
indicating
it
contains
executable
code.
The
TA
was
able
to
decrypt
its
content
and
use
it
to
create
a
new
binary,
which
we
refer
to
as
payload2
(i.e.,
Parallax
RAT).
Payload1
uses
a
technique
known
as process-hollowing to
inject
payload2
into
a
legitimate
Microsoft
pipanel.exe
process
that
then
gets
launched
by
an
attacker.”
The
malware
achieves
persistence
by
creating
a
copy
of
itself
in
the
Windows
Startup
folder.
The
second
payload,
ParallaxRAT,
gathers
sensitive
information
from
the
infected
machines.
Upon
successfully
infecting
the
victim’s
machine,
the
malware
notifies
the
attacker.
They
interact with
the
victim
by
posing
questions
via
Notepad
and
instructing
them
to
connect
to
a
Telegram
channel.
The
experts
noticed
that
the
operators
can
remotely
shut
down
or
restart
the
victim’s
machine.
The
content
of
the
Telegram
chat
analyzed
by
the
researchers
revealed
that
the
attackers
have
an
interest
in
crypto
companies.

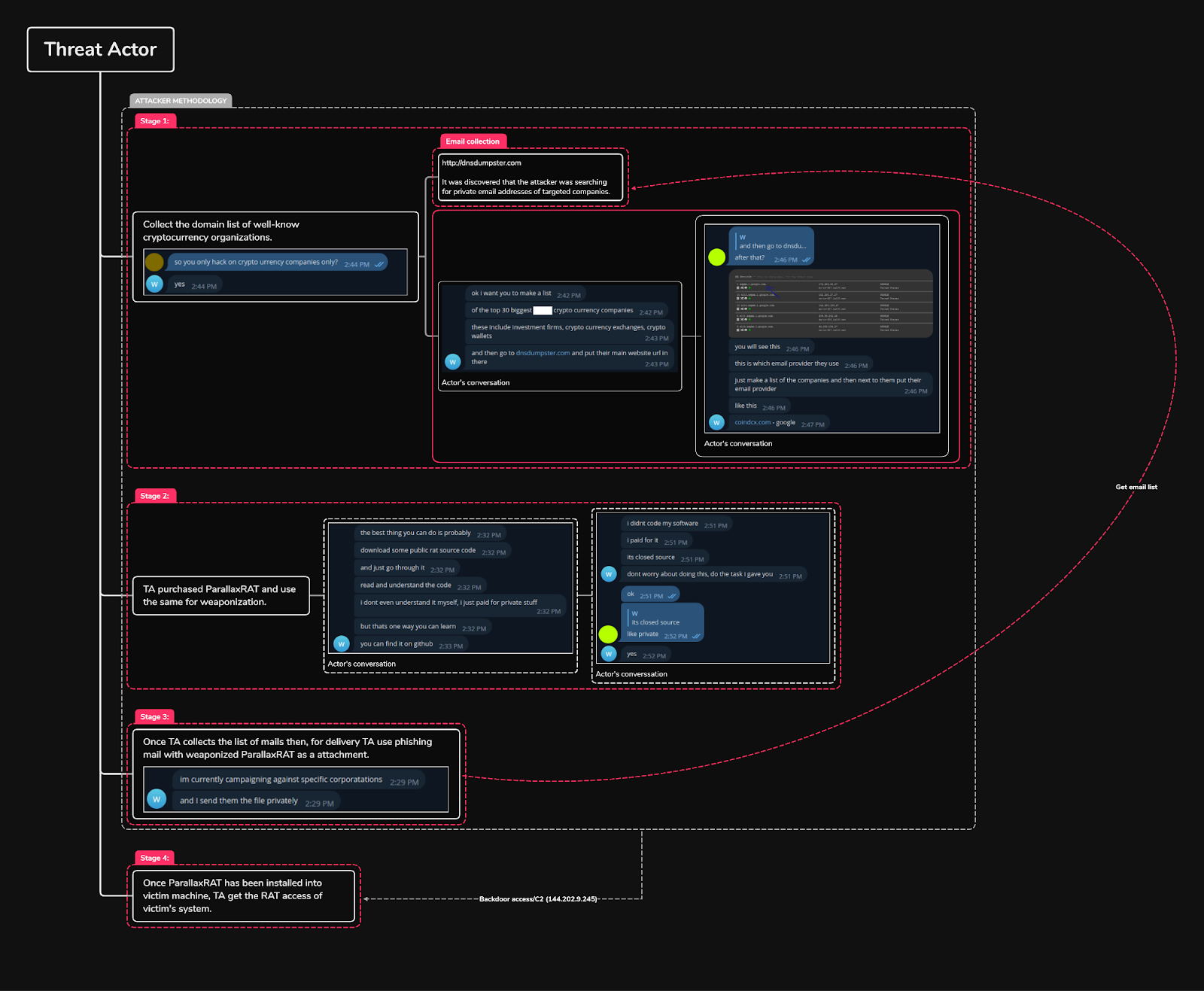
The
attackers
gather
private
email
addresses
of
cryptocurrency
companies
from
the
website,
they
use
public
service
like
dnsdumpster.com
to
find
mail
servers
of
the
target
organizations.
“It’s
important
for
organizations
to
be
aware
of
this
malware’s
existence
and
take
necessary
precautions
to
protect
systems
and
data.”
concludes
the
report
that
also
provides
Indicators
of
Compromise
(IOCs).
Follow
me
on
Twitter:
@securityaffairs
and
Facebook
and
Mastodon
(SecurityAffairs –
hacking,
Parallax
RAT)












