Cryptocurrency
companies
are
being
targeted
as
part
of
a
new
campaign
that
delivers
a
remote
access
trojan
called
Parallax
RAT.
The
malware
“uses
injection
techniques
to
hide
within
legitimate
processes,
making
it
difficult
to
detect,”
Uptycs
said
in
a
new
report.
“Once
it
has
been
successfully
injected,
attackers
can
interact
with
their
victim
via
Windows
Notepad
that
likely
serves
as
a
communication
channel.”
Parallax
RAT
grants
attackers
remote
access
to
victim
machines.
It
comes
with
features
to
upload
and
download
files
as
well
as
record
keystrokes
and
screen
captures.
It
has
been
put
to
use
since
early
2020
and
was
previously
delivered
via
COVID-19-themed
lures.
In
February
2022,
Proofpoint
detailed
a
cybercrime
threat
actor
dubbed
TA2541
targeting
aviation,
aerospace,
transportation,
manufacturing,
and
defense
industries
using
different
RATs,
including
Parallax.
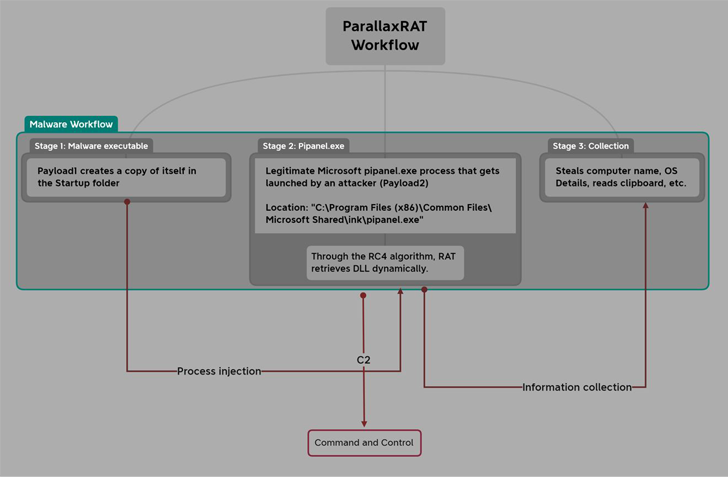
The
first
payload
is
a
Visual
C++
malware
that
employs
the
process
hollowing
technique
to
inject
Parallax
RAT
into
a
legitimate
Windows
component
called
pipanel.exe.
Parallax
RAT,
besides
gathering
system
metadata,
is
also
capable
of
accessing
data
stored
in
the
clipboard
and
even
remotely
rebooting
or
shutting
down
the
compromised
machine.
One
notable
aspect
of
the
attacks
is
the
use
of
the
Notepad
utility
to
initiate
conversations
with
the
victims
and
instructing
them
to
connect
to
an
actor-controlled
Telegram
channel.
Uptycs’
analysis
of
the
Telegram
chat
reveals
that
the
threat
actor
has
an
interest
in
crypto
companies
such
as
investment
firms,
exchanges,
and
wallet
service
providers.
The
modus
operandi
entails
searching
public
sources
like
DNSdumpster
for
identifying
mail
servers
belonging
to
the
targeted
companies
via
their
mail
exchanger
(MX)
records
and
sending
phishing
emails
bearing
the
Parallax
RAT
malware.
The
development
comes
as
Telegram
is
increasingly
becoming
a
hub
for
criminal
activities,
enabling
threat
actors
to
organize
their
operations,
distribute
malware,
and
facilitate
the
sale
of
stolen
data,
and
other
illegal
goods
in
part
owing
to
the
platform’s
lax
moderation
efforts.
“One
reason
why
Telegram
is
attractive
to
cybercriminals
is
its
alleged
built-in
encryption
and
the
ability
to
create
channels
and
large,
private
groups,”
KELA
disclosed
in
an
exhaustive
analysis
published
last
month.
“These
features
make
it
difficult
for
law
enforcement
and
security
researchers
to
monitor
and
track
criminal
activity
on
the
platform.
In
addition,
cybercriminals
often
use
coded
language
and
alternative
spellings
to
communicate
on
Telegram,
making
it
even
more
challenging
to
decipher
their
conversations.”