On Tuesday, Microsoft rolled out 89 patches impacting 14 different product families. Among these fixes, two critical issues within the Windows domain have been highlighted by Microsoft. At present, two of the addressed vulnerabilities are actively being exploited, with an additional eight CVEs anticipated to be targeted within the next month. Sophos protections can identify four of this month’s issues, and details regarding those are provided in the table below.
Aside from the mentioned patches, this release also contains advisory information related to two Edge vulnerabilities, as well as issues concerning Azure, CBL Mariner, and Defender, which will be elaborated on further in the advisory section below. Towards the end of this post, comprehensive appendices categorizing Microsoft’s patches based on severity, predicted exploitability, and product family can be found.
Statistics Overview
- Total CVEs: 89
- Public disclosures: 3
- Exploits detected: 2
- Severity Levels
- Critical: 3
- Important: 85
- Moderate: 3
- Impacts
- Remote Code Execution: 52
- Elevation of Privilege: 27
- Denial of Service: 4
- Spoofing: 3
- Security Feature Bypass: 2
- Information Disclosure: 1
- CVSS base score 9.0 or higher: 4
- CVSS base score 8.0 or higher: 42
Figure 1: The majority of November’s updates revolve around RCE vulnerabilities, particularly those pertaining to the 31 patched SQL Server issues
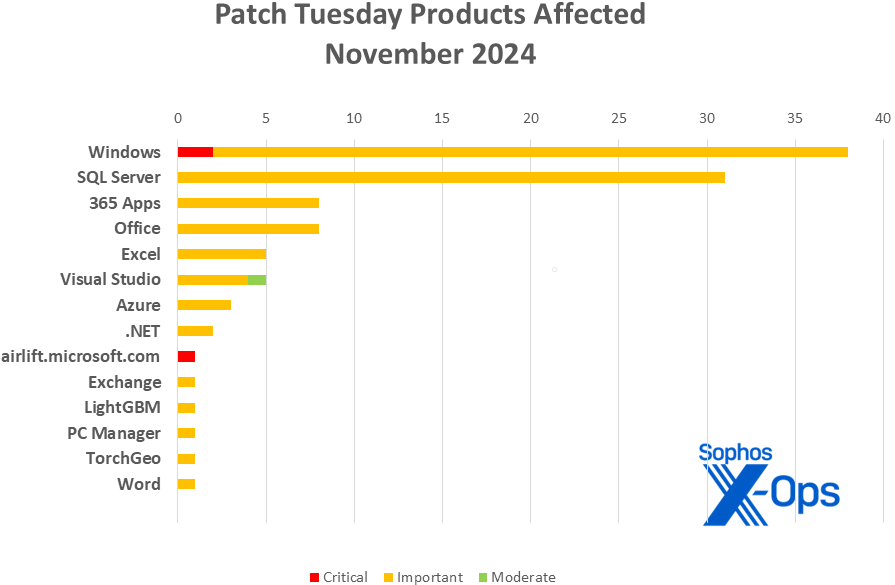
Product Breakdown
- Windows: 37
- SQL Server: 31
- 365 Apps: 8
- Office: 8
- Excel: 5
- Visual Studio: 5
- Azure: 3
- .NET: 2
- airlift.microsoft.com: 1
- Exchange: 1
- LightGBM: 1
- PC Manager: 1
- TorchGeo: 1
- Word: 1
For this list, instances where a CVE applies to multiple product families are counted once for each affected family.
Figure 2: Similar to the previous month, a wide array of product families were impacted, yet Windows and SQL Server received the majority of November’s patches
Highlighted November Updates
Alongside the aforementioned matters, several specific highlights deserve attention.
31 CVEs – Server 2025 Concerns
As per a recent Report on The Register, an error in KB caused numerous Server 2019 and 2022 instances to receive unexpected Server 2025 upgrades. While efforts to rectify this issue have been made by Microsoft, the process is still ongoing. This month’s Patch Tuesday emphasizes the importance for administrators to rectify any inadvertent Server 2025 instances promptly, as more than a third of the month’s patches are relevant to this unannounced version. The associated CVEs have been detailed in Appendix E at the conclusion of this article.
CVE-2024-5535 — OpenSSL: CVE-2024-5535 SSL_select_next_proto buffer overread
Though highlighted under advisories, this RCE, with a substantial 9.1 CVSS base score, demands attention. The particulars provided are noteworthy. This vulnerability, assigned by OpenSSL, differs slightly in presentation from Microsoft’s typical patch data. In the worst-case scenario of an email-based attack, RCE could be achieved without the recipient even interacting with the email content. The issue affects Azure Linux 3.0, CBL Mariner 2.0, and Defender for Endpoint on Android, iOS, and Windows. Despite this, Microsoft deems the likelihood of exploitation within the next month as relatively low.
CVE-2024-49039 — Windows Task Scheduler Elevation of Privilege Vulnerability
CVE-2024-43451 — NTLM Hash Disclosure Spoofing Vulnerability
These are the two CVEs currently being exploited in the wild. The former, an EoP with an 8.8 CVSS base score, is the more severe of the two, necessitating the presence of a malicious application on the targeted system. As for the spoofing flaw with a 6.5 CVSS base score, an unexpected element is the requirement for IE Cumulative updates for users relying on Server 2008, 2008 R2, and 2012 R2 and still using Security Only updates.
CVE-2024-49040 — Microsoft Exchange Server Spoofing Vulnerability
This noteworthy spoofing vulnerability of Important severity, anticipated by Microsoft to be targeted in the forthcoming 30 days, offers specific post-installation directives, accessible on the company’s platform.
CVE-2024-49056 — airlift.microsoft.com Elevation of Privilege Vulnerability
An atypical CVE pertaining to a Microsoft micro-site, with a Critical severity EoP, has already been remedied. The provided intel suggests, “Authentication bypass by assumed-immutable data on airlift.microsoft.com allow[ed] an authorized attacker to elevate privileges over a network.”
Figure 3: With less than a month remaining in 2024, following notably low CVE counts in the initial quarters, this year has surpassed the total patch count for 2023, with 942 patches issued in 2024 compared to 931 in the previous year
Sophos Security Measures
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| Exploit/2443623-A | Exploit/2443623-A | |
| Vulnerability-43630 | Exploit/2443630-A | Exploit/2443630-A |
| Vulnerability-49039 | Exploit/2449039-A | Exploit/2449039-A |
| Vulnerability-49033 | sid:2310318 | sid:2310318 |
Every month, if you are unwilling to wait for your system to autonomously retrieve Microsoft’s updates, you have the option to manually obtain them from the Windows Update Catalog website. Execute the winver.exe utility to identify the build of Windows 10 or 11 currently installed on your device, then fetch the Cumulative Update package corresponding to your system’s architecture and build version.
Appendix A: Impact of Vulnerabilities and Their Severity
The following is a compilation of November patches categorized by their impact and then organized by severity. Each listing is additionally sorted by CVE.
Remote Code Execution (52 CVEs)
| Critical importance | |
| Vulnerability-43639 | Windows Kerberos Remote Code Execution Vulnerability |
| Significant importance | |
| Vulnerability-38255 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-43447 | Windows SMBv3 Server Remote Code Execution Vulnerability |
| Vulnerability-43459 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-43462 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-43498 | .NET and Visual Studio Remote Code Execution Vulnerability |
| Vulnerability-43598 | LightGBM Remote Code Execution Vulnerability |
| Vulnerability-43602 | Azure CycleCloud Remote Code Execution Vulnerability |
| Vulnerability-43620 | Windows Telephony Server Remote Code Execution Vulnerability |
| Vulnerability-43621 | Windows Telephony Server Remote Code Execution Vulnerability |
| Vulnerability-43622 | Windows Telephony Server Remote Code Execution Vulnerability |
| Vulnerability-43627 | Windows Telephony Server Remote Code Execution Vulnerability |
| Vulnerability-43628 | Windows Telephony Server Remote Code Execution Vulnerability |
| Vulnerability-43635 | Windows Telephony Server Remote Code Execution Vulnerability |
| Vulnerability-43640 | Windows Kernel-Mode Driver Remote Code Execution Vulnerability |
| Vulnerability-48993 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-48994 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-48995 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-48996 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-48997 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-48998 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-48999 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-49000 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-49001 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-49002 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-49003 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-49004 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-49005 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-49006 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-49007 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-49008 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-49009 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-49010 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-49011 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-49012 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-49013 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-49014 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-49015 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-49016 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-49017 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-49018 | SQL Server Native Client Remote Code Execution Vulnerability |
| Vulnerability-49021 | Microsoft SQL Server Remote Code Execution Vulnerability |
| Vulnerability-49026 | Microsoft Excel Remote Code Execution Vulnerability |
| Vulnerability-49027 | Microsoft Excel Remote Code Execution Vulnerability |
| Vulnerability-49028 | Microsoft Excel Remote Code Execution Vulnerability |
| Vulnerability-49029 | Microsoft Excel Remote Code Execution Vulnerability |
| Vulnerability-49030 | Microsoft Excel Remote Code Execution Vulnerability |
| Vulnerability-49031 | Microsoft Office Graphics Remote Code Execution Vulnerability |
| Vulnerability-49032 | Microsoft Office Graphics Remote Code Execution Vulnerability |
| Vulnerability-49043 | Microsoft.SqlServer.XEvent.Configuration.dll Remote Code Execution Vulnerability |
| Vulnerability-49048 | TorchGeo Remote Code Execution Vulnerability |
| Vulnerability-49050 | Visual Studio Code Python Extension Remote Code Execution Vulnerability |
Heightening of28 CVEs of Special Rights
| Severe criticality | |
| CVE-2024-43625 | Microsoft Windows VMSwitch Special Rights Elevation Vulnerability |
| CVE-2024-49056 | Airlift.microsoft.com Special Rights Elevation Vulnerability |
| Important significance | |
| CVE-2024-43449 | Windows USB Video Class System Driver Elevation of Special Rights Vulnerability |
| CVE-2024-43452 | Windows Registry Elevation of Special Rights Vulnerability |
| CVE-2024-43530 | Windows Update Stack Elevation of Special Rights Vulnerability |
| CVE-2024-43613 | Azure Database for PostgreSQL Flexible Server Extension Elevation of Special Rights Vulnerability |
| CVE-2024-43623 | Windows NT OS Kernel Elevation of Special Rights Vulnerability |
| CVE-2024-43624 | Windows Hyper-V Shared Virtual Disk Elevation of Special Rights Vulnerability |
| CVE-2024-43626 | Windows Telephony Server Elevation of Special Rights Vulnerability |
| CVE-2024-43629 | Windows DWM Core Library Elevation of Special Rights Vulnerability |
| CVE-2024-43630 | Windows Kernel Elevation of Special Rights Vulnerability |
| CVE-2024-43631 | Windows Secure Kernel Mode Elevation of Special Rights Vulnerability |
| CVE-2024-43634 | Windows USB Video Class System Driver Elevation of Special Rights Vulnerability |
| CVE-2024-43636 | Win32k Elevation of Special Rights Vulnerability |
| CVE-2024-43637 | Windows USB Video Class System Driver Elevation of Special Rights Vulnerability |
| CVE-2024-43638 | Windows USB Video Class System Driver Elevation of Special Rights Vulnerability |
| CVE-2024-43641 | Windows Registry Elevation of Special Rights Vulnerability |
| CVE-2024-43643 | Windows USB Video Class System Driver Elevation of Special Rights Vulnerability |
| CVE-2024-43644 | Windows Client-Side Caching Elevation of Special Rights Vulnerability |
| CVE-2024-43646 | Windows Secure Kernel Mode Elevation of Special Rights Vulnerability |
| CVE-2024-49019 | Active Directory Certificate Services Elevation of Special Rights Vulnerability |
| CVE-2024-49039 | Windows Task Scheduler Elevation of Special Rights Vulnerability |
| CVE-2024-49042 | Azure Database for PostgreSQL Flexible Server Extension Elevation of Special Rights Vulnerability |
| CVE-2024-49044 | Visual Studio Elevation of Special Rights Vulnerability |
| CVE-2024-49046 | Windows Win32 Kernel Subsystem Elevation of Special Rights Vulnerability |
| CVE-2024-49051 | Microsoft PC Manager Elevation of Special Rights Vulnerability |
| Moderate significance | |
| CVE-2024-49049 | Visual Studio Code Remote Extension Elevation of Special Rights Vulnerability |
Negation of Service (4 CVEs)
| Important significance | |
| CVE-2024-38264 | Microsoft Virtual Hard Disk (VHDX) Negation of Service Vulnerability |
| CVE-2024-43499 | .NET and Visual Studio Negation of Service Vulnerability |
| CVE-2024-43633 | Windows Hyper-V Negation of Service Vulnerability |
| CVE-2024-43642 | Windows SMB Negation of Service Vulnerability |
Faking (3 CVEs)
| Important significance | |
| CVE-2024-43450 | Windows DNS Faking Vulnerability |
| CVE-2024-43451 | NTLM Hash Disclosure Faking Vulnerability |
| CVE-2024-49040 | Microsoft Exchange Server Faking Vulnerability |
Security Characteristic Circumvention (2 CVEs)
| Important significance | |
| CVE-2024-43645 | Windows Defender Application Control (WDAC) Security Characteristic Circumvention Vulnerability |
| CVE-2024-49033 | Microsoft Word Security Characteristic Circumvention Vulnerability |
Disclosure of Information (1 CVE)
| Important significance | |
| CVE-2024-43500 | Windows Resilient File System (ReFS) Disclosure of Information Vulnerability |
Appendix B: Vulnerability to Exploitation
Here are the November CVEs identified by Microsoft as likely to be taken advantage of in the wild or anticipated to face exploitation within the initial 30 days after being released. The layout is based on CVE.
| Exploitation detected | |
| CVE-2024-43451 | NTLM Hash Disclosure Faking Vulnerability |
| CVE-2024-49039 | Windows Task Scheduler Elevation of Special Rights Vulnerability |
| Exploitation more likely within the next 30 days | |
| CVE-2024-43623 | Windows NT OS Kernel Elevation of Special Rights Vulnerability |
| CVE-2024-43629 | Windows DWM Core Library Elevation of Special Rights Vulnerability |
| CVE-2024-43630 | Windows Kernel Elevation of Special Rights Vulnerability |
| CVE-2024-43636 | Win32k Elevation of Special Rights Vulnerability |
| CVE-2024-43642 | Windows SMB Denial of Service Vulnerability |
| CVE-2024-49019 | Active Directory Certificate Services Elevation of Special Rights Vulnerability |
| CVE-2024-49033 | Microsoft Word Security Characteristic Circumvention Vulnerability |
| CVE-2024-49040 | Microsoft Exchange Server Faking Vulnerability |
Appendix C: Affected Products
This catalog showcases the November patches categorized by product family, and then further subdivided by significance. Each collection is additionally organized by CVE. Patches shared across multiple product families are reiterated multiple times, each for a separate product family.
Windows (37 CVEs)
| Critical severity | |
| CVE-2024-43625 | Microsoft Windows VMSwitch Privilege Escalation Vulnerability |
| CVE-2024-43639 | Windows Kerberos Remote Code Execution Vulnerability |
| High severity | |
| CVE-2024-38203 | Windows Package Library Manager Data Disclosure Vulnerability |
| CVE-2024-38264 | Microsoft Virtual Hard Disk (VHDX) DoS Vulnerability |
| CVE-2024-43447 | Windows SMBv3 Server Remote Code Execution Vulnerability |
| CVE-2024-43449 | Windows USB Video Class System Driver Privilege Escalation Vulnerability |
| CVE-2024-43450 | Windows DNS Tampering Vulnerability |
| CVE-2024-43452 | Windows Registry Privilege Escalation Vulnerability |
| CVE-2024-43530 | Windows Update Stack Privilege Escalation Vulnerability |
| CVE-2024-43620 | Windows Telephony Server Remote Code Execution Vulnerability |
| CVE-2024-43621 | Windows Telephony Server Remote Code Execution Vulnerability |
| CVE-2024-43622 | Windows Telephony Server Remote Code Execution Vulnerability |
| CVE-2024-43623 | Windows NT OS Kernel Privilege Escalation Vulnerability |
| CVE-2024-43624 | Windows Hyper-V Shared Virtual Disk Privilege Escalation Vulnerability |
| CVE-2024-43626 | Windows Telephony Server Privilege Escalation Vulnerability |
| CVE-2024-43627 | Windows Telephony Server Remote Code Execution Vulnerability |
| CVE-2024-43628 | Windows Telephony Server Remote Code Execution Vulnerability |
| CVE-2024-43629 | Windows DWM Core Library Privilege Escalation Vulnerability |
| CVE-2024-43630 | Windows Kernel Privilege Escalation Vulnerability |
| CVE-2024-43631 | Windows Secure Kernel Mode Privilege Escalation Vulnerability |
| CVE-2024-43633 | Windows Hyper-V DoS Vulnerability |
| CVE-2024-43634 | Windows USB Video Class System Driver Privilege Escalation Vulnerability |
| CVE-2024-43635 | Windows Telephony Server Remote Code Execution Vulnerability |
| CVE-2024-43636 | Win32k Privilege Escalation Vulnerability |
| CVE-2024-43637 | Windows USB Video Class System Driver Privilege Escalation Vulnerability |
| CVE-2024-43638 | Windows USB Video Class System Driver Privilege Escalation Vulnerability |
| CVE-2024-43640 | Windows Kernel-Mode Driver Remote Code Execution Vulnerability |
| CVE-2024-43641 | Windows Registry Privilege Escalation Vulnerability |
| CVE-2024-43642 | Windows SMB DoS Vulnerability |
| CVE-2024-43643 | Windows USB Video Class System Driver Privilege Escalation Vulnerability |
| CVE-2024-43644 | Windows Client-Side Caching Privilege Escalation Vulnerability |
| CVE-2024-43645 | Windows Defender Application Control (WDAC) Feature Bypass Vulnerability |
| CVE-2024-43646 | Windows Secure Kernel Mode Privilege Escalation Vulnerability |
| CVE-2024-49019 | Active Directory Certificate Services Privilege Escalation Vulnerability |
| CVE-2024-49039 | Windows Task Scheduler Privilege Escalation Vulnerability |
| CVE-2024-49046 | Windows Win32 Kernel Subsystem Privilege Escalation Vulnerability |
| CVE-2024-43451 | NTLM Hash Disclosure Tampering Vulnerability |
SQL Server (31 vulnerabilities)
| High severity | |
| CVE-2024-38255 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-43459 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-43462 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-48993 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-48994 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-48995 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-48996 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-48997 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-48998 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-48999 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49000 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49001 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49002 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49003 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49004 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49005 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49006 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49007 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49008 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49009 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49010 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49011 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49012 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49013 | SQL Server Native Client Remote Code Execution Weakness |
| CVE-2024-49014 | SQL Server Native Client Remote Code Execution Weakness |
| CVE-2024-49015 | SQL Server Native Client Remote Code Execution Weakness |
| CVE-2024-49016 | SQL Server Native Client Remote Code Execution Weakness |
| CVE-2024-49017 | SQL Server Native Client Remote Code Execution Weakness |
| CVE-2024-49018 | SQL Server Native Client Remote Code Execution Weakness |
| CVE-2024-49021 | Microsoft SQL Server Remote Code Execution Weakness |
| CVE-2024-49043 | Microsoft.SqlServer.XEvent.Configuration.dll Remote Code Execution Weakness |
365 Applications (8 CVEs)
| Significant danger level | |
| CVE-2024-49026 | Microsoft Excel Remote Code Execution Weakness |
| CVE-2024-49027 | Microsoft Excel Remote Code Execution Weakness |
| CVE-2024-49028 | Microsoft Excel Remote Code Execution Weakness |
| CVE-2024-49029 | Microsoft Excel Remote Code Execution Weakness |
| CVE-2024-49030 | Microsoft Excel Remote Code Execution Weakness |
| CVE-2024-49031 | Microsoft Office Graphics Remote Code Execution Weakness |
| CVE-2024-49032 | Microsoft Office Graphics Remote Code Execution Weakness |
| CVE-2024-49033 | Microsoft Word Security Feature Bypass Weakness |
Office Suite (8 CVEs)
| Significant danger level | |
| CVE-2024-49026 | Microsoft Excel Remote Code Execution Weakness |
| CVE-2024-49027 | Microsoft Excel Remote Code Execution Weakness |
| CVE-2024-49028 | Microsoft Excel Remote Code Execution Weakness |
| CVE-2024-49029 | Microsoft Excel Remote Code Execution Weakness |
| CVE-2024-49030 | Microsoft Excel Remote Code Execution Weakness |
| CVE-2024-49031 | Microsoft Office Graphics Remote Code Execution Weakness |
| CVE-2024-49032 | Microsoft Office Graphics Remote Code Execution Weakness |
| CVE-2024-49033 | Microsoft Word Security Feature Bypass Weakness |
Excel Software (5 CVEs)
| Significant danger level | |
| CVE-2024-49026 | Microsoft Excel Remote Code Execution Weakness |
| CVE-2024-49027 | Microsoft Excel Remote Code Execution Weakness |
| CVE-2024-49028 | Microsoft Excel Remote Code Execution Weakness |
| CVE-2024-49029 | Microsoft Excel Remote Code Execution Weakness |
| CVE-2024-49030 | Microsoft Excel Remote Code Execution Weakness |
Visual Studio Tools (5 CVEs)
| Significant danger level | |
| CVE-2024-43498 | .NET and Visual Studio Remote Code Execution Weakness |
| CVE-2024-43499 | .NET and Visual Studio Denial of Service Weakness |
| CVE-2024-49044 | Visual Studio Elevation of Privilege Weakness |
| CVE-2024-49050 | Visual Studio Code Python Extension Remote Code Execution Weakness |
| Moderate danger level | |
| CVE-2024-49049 | Visual Studio Code Remote Extension Elevation of Privilege Weakness |
Azure Platform (3 CVEs)
| Significant danger level | |
| CVE-2024-43602 | Azure CycleCloud Remote Code Execution Weakness |
| CVE-2024-43613 | Azure Database for PostgreSQL Flexible Server Extension Elevation of Privilege Weakness |
| CVE-2024-49042 | Azure Database for PostgreSQL Flexible Server Extension Elevation of Privilege Weakness |
.NET Platform (2 CVEs)
| Significant danger level | |
| CVE-2024-43498 | .NET and Visual Studio Remote Code Execution Weakness |
| CVE-2024-43499 | .NET and Visual Studio Denial of Service Weakness |
airlift.microsoft.com System (1 CVE)
| Significant danger level | |
| CVE-2024-49056 | Airlift.microsoft.com Elevation of Privilege Weakness |
Exchange Server (1 CVE)
| Significant danger level | |
| CVE-2024-49040 | Microsoft Exchange Server Spoofing Weakness |
LightGBM Software (1 CVE)
| Significant danger level | |
| CVE-2024-43598 | LightGBM Remote Code Execution Weakness |
Personal Computer Manager (1 CVE)
| Significant danger level | |
| CVE-2024-49051 | Microsoft PC Manager Elevation of Privilege Weakness |
TorchGeo Library (1 CVE)
| Significant danger level | |
| CVE-2024-49048 | TorchGeo Remote Code Execution Weakness |
Word Software (1 CVE)
| Significant danger level | |
| CVE-2024-49033 | Microsoft Word Security Feature Bypass Weakness |
Appendix D: Notices and Other Systems
This compilation features alerts and insights on other pertinent CVEs from the latest launch in November.
| CVE-2024-5535 | Azure, CBL Mariner, Defender | OpenSSL: CVE-2024-5535 SSL_select_next_proto buffer overread |
| CVE-2024-10826 | Edge | Chromium: CVE-2024-10826 Use after free in Family Experiences |
| CVE-2024-10827 | Edge | Chromium: CVE-2024-10827 Use after free in Serial |
Appendix E: Server 2025
This register entails CVEs impacting Server 2025, which some users might have unintentionally obtained the previous week.
| CVE-2024-38203 | CVE-2024-43625 | CVE-2024-43639 |
| CVE-2024-38264 | CVE-2024-43626 | CVE-2024-43641 |
| CVE-2024-43449 | CVE-2024-43627 | CVE-2024-43642 |
| CVE-2024-43450 | CVE-2024-43628 | CVE-2024-43643 |
| CVE-2024-43451 | CVE-2024-43629 | CVE-2024-43644 |
| CVE-2024-43452 | CVE-2024-43630 | CVE-2024-43646 |
| CVE-2024-43620 | CVE-2024-43631 | CVE-2024-49019 |
| CVE-2024-43621 | CVE-2024-43635 | CVE-2024-49039 |
| CVE-2024-43622 | CVE-2024-43636 | CVE-2024-49046 |
| CVE-2024-43623 | CVE-2024-43637 | |
| CVE-2024-43624 | CVE-2024-43638 |