North
Korea-linked Lazarus
APT
group exploits
a
zero-day
vulnerability
in
attacks
aimed
at
a
South
Korean
financial
entity.
ASEC
(AhnLab
Security
Emergency
Response
Center)
observed
North
Korea-linked Lazarus
APT
group exploiting
a
zero-day
vulnerability
in
an
undisclosed
software
to
breach
a
financial
business
entity
in
South
Korea.
The
nation-state
actors
breached
twice
the
company
in
one
year.
The
first
attack
was
spotted
in
May
2022,
threat
actors
targeted
a
vulnerable
version
of
a
certificate
software
that’s
widely
used
by
public
institutions
and
universities
in
South
Korea.
A
second
attack
was
observed
in
October
2022,
when
attackers
exploited
a
zero-day
vulnerability
affecting
the
same
software.
“During
the
infiltration
in
May
2022,
the
affected
company
was
using
a
vulnerable
version
of
a
certificate
program
that
was
commonly
used
by
public
institutions
and
universities.
After
the
incident,
they
updated
all
of
their
software
to
their
latest
versions.”
reads
the
advisory
published
by
the
ASEC.
“However,
the
Lazarus
group
used
the
software’s
0-Day
vulnerability
to
carry
out
their
infiltration
this
time.”
ASEC
reported
the
zero-day
to
KISA,
it
also
pointed
out
that
the
vulnerability
has
not
been
fully
verified
yet
and
a
software
patch
has
yet
to
be
released.
The
Lazarus
APT
exploited
the
zero-day
flaw
to
conduct
lateral
movement,
it
also
disabled
the
anti-malware
software
by
using
the
technique
known
as
Bring
Your
Own
Vulnerable
Driver
(BYOVD).
This
isn’t
the
first
that
the
Lazarus
APT
used
the
BYOVD
technique,
in
October
2022
the
North
Korea-linked
group
has
been
spotted
deploying
a
Windows
rootkit
by
taking
advantage
of
an
exploit
in
a
Dell
firmware
driver.
ASEC
also
noticed
that
the
APT
employed
anti-forensic
techniques
to
hide
their
malicious
activities,
such
as
changing
filenames
before
deleting
them
or
modifying
time
stamps.
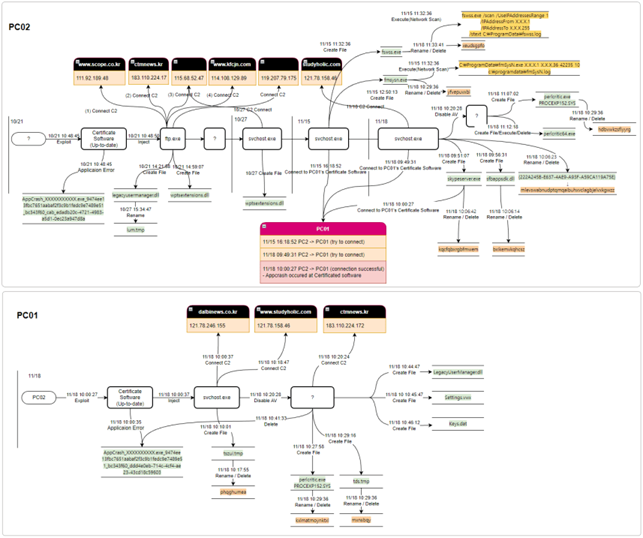
The
researchers
analyzed
two
PCs
of
the
target
organization
and
confirmed
that
the
threat
actor
had
performed
a
lateral
movement
attack
on
PC01
and
PC02
using
the
certificate
software’s
vulnerability.
The
attackers
created
the
backdoor
loader
(LegacyUserManager.dll)
to
deploy
the
following
malicious
payloads:
- C:ProgramDataMicrosoftCryptoKeysKeys.dat (obtained)
- C:ProgramDataMicrosoftSettingsSettings.vwx (obtained)
“The
threat
actor
exploited
the
0-Day
vulnerability
of
a
certificate
software
that
is
commonly
used
in
Korea.
Since
these
types
of
software
are
not
updated
automatically,
they
must
be
manually
patched
to
the
latest
version
or
deleted
if
unused. ”
ASEC
concludes.
“The
affected
company
was
re-infiltrated
by
the
same
threat
actor
with
a
similar
method.
Instead
of
taking
only
post-attack
measures,
continuous
monitoring
is
required
to
prevent
recurrences.”
Follow
me
on
Twitter:
@securityaffairs
and
Facebook
and
Mastodon
(SecurityAffairs –
hacking,
Moshen
Dragon)