North
Korea-linked
APT
group
Lazarus
actor
has
been
targeting
vulnerable
Microsoft
IIS
servers
to
deploy
malware.
AhnLab
Security
Emergency
response
Center
(ASEC)
researchers
reported
that
the
Lazarus
APT
Group is
targeting
vulnerable
versions
of
Microsoft
IIS
servers
in
a
recent
wave
of
malware-based
attacks.
Once
discovered
a
vulnerable
ISS
server,
the
attackers
leverage
the
DLL
side-loading
(T1574.002)
technique
to
execute
a
malicious
DLL
(msvcr100.dll)
that
they
have
placed
in
the
same
folder
path
as
a
normal
application
(Wordconv.exe).
Then
the
library
is
executed
via
the
Windows
IIS
web
server
process.
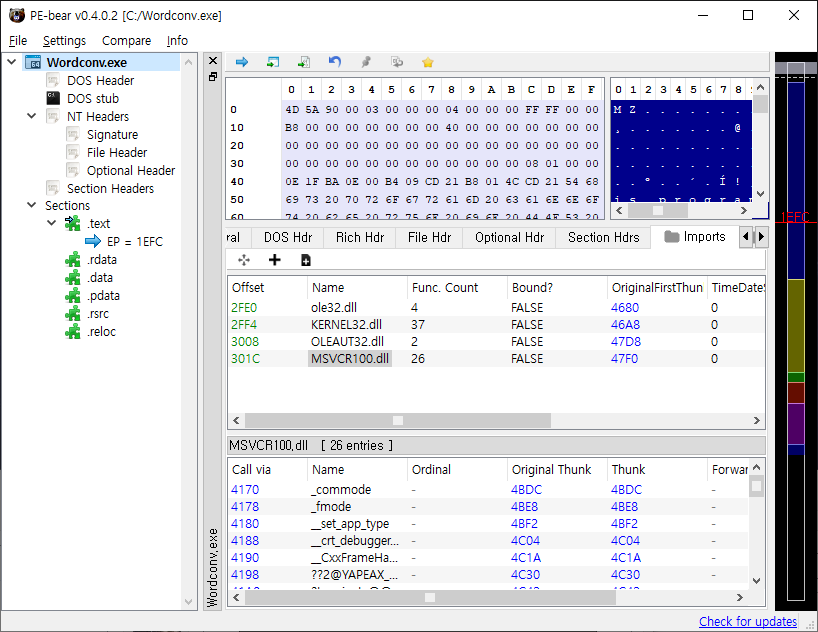
The
msvcr100.dll
is
contained
within
the
import
DLL
list
of
Wordconv.exe,
this
means
that
the
first
DLL
is
loaded
in
the
memory
of
the
Wordconv.exe
process
when
it
is
executed.

“the
functionality
of
msvcr100.dll
involves
decrypting
an
encoded
PE
file
(msvcr100.dat)
and
the
key
(df2bsr2rob5s1f8788yk6ddi4x0wz1jq)
that
is
transmitted
as
a
command-line
argument
during
the
execution
of
Wordconv.exe
by
utilizing
the
Salsa20
algorithm.”
reads
the
analysis
published
by
ASEC.
“The
decrypted
PE
file
is
then
executed
in
the
memory.
It
then
performs
the
function
of
clearing
the
malicious
DLL
module
that
was
loaded
through
the
FreeLibraryAndExitThread
WinAPI
call
before
deleting
itself
(msvcr100.dll).”
The
researchers
noticed
important
similarities
between
the
msvcr100.dll
and
the
cylvc.dll
previously
detailed
by
ASEC
and
related
to
another
Lazarus
campaign.
The
threat
actor
exploited
an
open-source
Notepad++
plugin
called Quick
Color
Picker (a
discontinued
project)
to
establish
a
foothold
in
the
target
network
before
creating
additional
malware
(diagn.dll).
The
diagn.dll
received
the
PE
file
encoded
with
the
RC6
algorithm
as
an
execution
argument
value,
then
uses
an
internally
hard-coded
key
to
decrypt
the
data
file
and
execute
the
PE
file
directly
in
the
memory.
The
researchers
were
not
able
to
determine
the
malicious
behavior
of
the
PE
file
because
the
PE
data
file
that
was
encoded
during
the
attack
could
not
be
collected,
but
the
analysis
of
the
log
suggests
threat
the
attackers
had
executed
a
credential
theft
tool
such
as
Mimikatz.
Once
obtained
the
system
credentials,
the
threat
actor
performed
internal
reconnaissance
and
used
remote
access
(port
3389)
to
perform
lateral
movement
into
the
internal
network.
“The
Lazarus
group
used
a
variety
of
attack
vectors
to
perform
their
initial
breach,
including Log4Shell, public
certificate
vulnerability, 3CX
supply
chain
attack,
etc.”
concludes
the
report
that
also
provides
Indicators
of
Compromise
(IoCs).
“since
the
threat
group
primarily
utilizes
the
DLL
side-loading
technique
during
their
initial
infiltrations,
companies
should
proactively
monitor
abnormal
process
execution
relationships
and
take
preemptive
measures
to
prevent
the
threat
group
from
carrying
out
activities
such
as
information
exfiltration
and
lateral
movement.”
This
week,
the
US
Department
of
the
Treasury’s
Office
of
Foreign
Assets
Control
(OFAC)
announced
sanctions
against
four
entities
and
one
individual
for
their
role
in
malicious
cyber
operations
conducted
to
support
the
government
of
North
Korea.
We
are
in
the
final!
Please
vote
for
Security
Affairs
(https://securityaffairs.com/)
as
the
best
European
Cybersecurity
Blogger
Awards
2022
–
VOTE
FOR
YOUR
WINNERS
Vote
for
me
in
the
sections
where
is
reported
Securityaffairs
or
my
name
Pierluigi
Paganini
Please
nominate
Security
Affairs
as
your
favorite
blog.
Nominate
Pierluigi
Paganini
and
Security
Affairs
here
here: https://docs.google.com/forms/d/e/1FAIpQLSepvnj8b7QzMdLh7vWEDQDqohjBUsHyn3x3xRdYGCetwVy2DA/viewform
Follow
me
on
Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, DPRK)