
A
new
malware
dubbed
HiatusRAT
infects
routers
to
spy
on
its
targets,
mostly
in
Europe
and
in
the
U.S.
Learn
which
router
models
are
primarily
targeted
and
how
to
protect
from
this
security
threat.

xiaoliangge/Adobe
Stock
As
previously
exposed,
routers
might
be
used
by
threat
actors
as
efficient
locations
to
plant
malware,
often
for
cyberespionage.
Routers
are
frequently
less
protected
than
standard
devices
and
are
often
using
modified
versions
of
existing
operating
systems.
Therefore,
targeting
routers
can
be
interesting
for
attackers
but
harder
to
compromise
and
use
than
a
usual
endpoint
or
server.
Lumen’s
Black
Lotus
Labs
has
exposed
new
malware
targeting
routers
in
a
campaign
named
Hiatus
by
the
researchers.
Jump
to:
What
is
the
Hiatus
malware
campaign?
The
Hiatus
campaign
primarily
targets
DrayTek
Vigor
router
models
2960
and
3900,
which
run
an
i386
architecture.
These
routers
are
mostly
used
by
medium-size
companies,
as
the
router
capabilities
support
a
few
hundred
of
employees’
VPN
connections.
The
researchers
also
found
other
malicious
binaries
targeting
MIPS
and
ARM-based
architectures.
The
initial
compromise
vector
stays
unknown,
yet
once
the
attackers
get
access
to
the
targeted
routers,
they
drop
a
bash
script.
When
that
bash
script
is
executed,
it
downloads
two
additional
files:
the
HiatusRAT
malware
and
a
variant
of
the
legitimate
tcpdump
tool,
which
enables
network
packet
capture.
Once
those
files
are
run,
the
attackers
are
in
control
of
the
router
and
may
download
files
or
run
arbitrary
commands,
intercept
the
network
traffic
from
the
infected
device
or
use
the
router
as
a
SOCKS5
proxy
device,
which
can
be
used
for
further
compromises
or
for
targeting
other
companies.
HiatusRAT
malware
When
the
RAT
is
launched,
it
checks
if
port
8816
is
used.
If
the
port
is
used
by
a
process,
it
kills
it
and
opens
a
new
listener
on
the
port,
ensuring
that
only
a
single
instance
of
the
malware
is
running
on
the
device.
It
then
collects
information
about
the
compromised
device
such
as
system
information
(such
as
kernel
version,
MAC
address,
architecture
type
and
firmware
version),
networking
information
(network
interfaces
configuration
and
local
IP
addresses)
and
file
system
information
(mount
points,
directory
listing,
file
system
type
and
virtual
memory
file
system).
In
addition,
it
collects
a
list
of
all
running
processes.
After
collecting
all
that
information,
the
malware
sends
it
to
an
attacker-controlled
heartbeat
C2
server.
The
malware
has
more
capabilities,
such
as
updating
its
configuration
file,
providing
the
attacker
with
a
remote
shell,
reading/deleting/uploading
files,
downloading
and
executing
files,
or
enabling
SOCKS5
packet
forwarding
or
plain
TCP
packets
forwarding.
Network
packet
capture
Aside
from
the
HiatusRAT,
the
threat
actor
also
deploys
a
variant
of
the
legitimate
tcpdump
tool,
which
enables
capturing
network
packets
on
the
compromised
device.
The
bash
script
used
by
the
threat
actor
showed
a
particular
interest
for
connections
on
ports
21,
25,
110
and
143,
which
are
usually
dedicated
to
file
transfer
protocol
and
email
transfers
(SMTP,
POP3
and
IMAP
email
protocols).
The
script
enables
more
port
sniffing,
if
necessary.
If
used,
the
packets
captured
are
sent
to
an
upload
C2,
different
from
the
heartbeat
C2,
after
the
packet
interception
reaches
a
certain
length.
This
allows
the
threat
actor
to
passively
intercept
full
files
transferred
via
the
FTP
protocol
or
emails
that
traverse
the
infected
device.
Campaign
targeting
Black
Lotus
Labs
identified
approximately
100
unique
IP
addresses
communicating
with
the
C2
servers
controlled
by
the
threat
actor
since
July
2022,
which
could
be
classified
in
two
categories:
-
Medium-size
companies
running
their
own
email
servers,
sometimes
owning
IP
address
ranges
on
the
internet
which
are
able
to
identify
them.
Companies
in
pharmaceuticals,
IT
services
or
consulting
firms,
and
a
municipal
government,
among
others,
could
be
identified.
The
researchers
suspect
that
the
targeting
of
IT
firms
is
a
choice
to
enable
downstream
access
to
customers’
environments. -
Internet
service
providers’
customer
IP
ranges
used
by
targets.
The
geographic
repartition
of
the
targets
shows
a
heavy
interest
in
U.K.
companies
and
some
other
European
countries,
in
addition
to
North
America
(Figure
A).
Figure
A
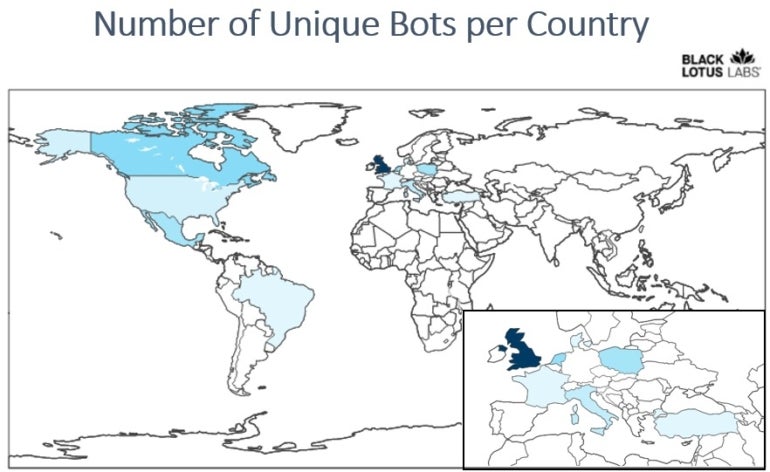
Lumen’s
Black
Lotus
Labs.
Heat
map
for
Hiatus
malware
campaign
infections.
As
reported
by
the
researchers,
approximately
2,700
DrayTek
Vigor
2960
routers
and
1,400
DrayTek
Vigor
3900
routers
are
connected
to
the
internet.
The
infection
of
only
approximately
100
of
those
routers
makes
the
campaign
small
and
difficult
to
detect;
the
fact
that
only
100
routers
out
of
thousands
are
impacted
emphasizes
the
possibility
that
the
threat
actor
is
only
aiming
at
particular
targets
and
not
interested
in
larger
targeting.
4
steps
to
protect
from
the
Hiatus
malware
threat
1.
Regularly
reboot
routers
and
keep
their
firmware
and
software
patched
to
prevent
compromise
from
common
vulnerabilities.
2.
Deploy
security
solutions
with
capabilities
to
log
and
monitor
the
routers’
behavior.
3.
End-of-life
devices
should
be
removed
and
replaced
with
supported
models
that
can
be
updated
for
maximum
security.
4.
All
traffic
passing
via
routers
should
be
encrypted
so
that
even
intercepting
it
does
not
make
it
exploitable.
Read
next:
Intrusion
detection
policy
(TechRepublic
Premium)
Disclosure:
I
work
for
Trend
Micro,
but
the
views
expressed
in
this
article
are
mine.











