Users in Latin America (LATAM) are the target of a financial malware called JanelaRAT that’s capable of capturing sensitive information from compromised Microsoft Windows systems.
“JanelaRAT mainly targets financial and cryptocurrency data from LATAM bank and financial institutions,” Zscaler ThreatLabz researchers Gaetano Pellegrino and Sudeep Singh said, adding it “abuses DLL side-loading techniques from legitimate sources (like VMWare and Microsoft) to evade endpoint detection.”
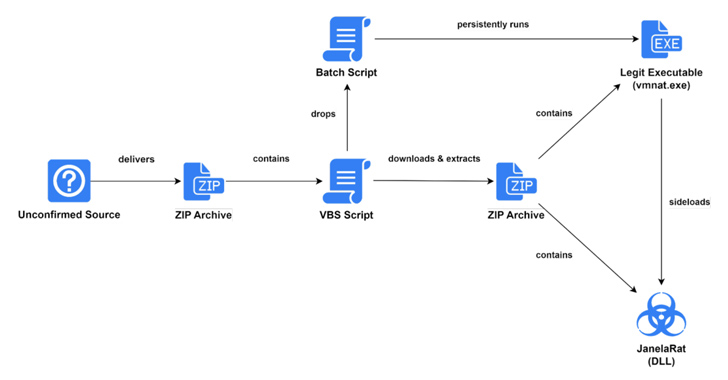
The exact starting point of the infection chain is unclear, but the cybersecurity company, which discovered the campaign in June 2023, said the unknown vector is used to deliver a ZIP archive file containing a Visual Basic Script.

The VBScript is engineered to fetch a second ZIP archive from the attackers’ server as well as drop a batch file used to establish persistence of the malware.
The ZIP archive is packed with two components, the JanelaRAT payload and a legitimate executable — identity_helper.exe or vmnat.exe — that’s used to launch the former by means of DLL side-loading.
JanelaRAT, for its part, employs string encryption and transitions into an idle state when necessary to avoid analysis and detection. It’s also a heavily modified variant of BX RAT, which was first discovered in 2014.
One of the new additions to the trojan is its ability to capture windows titles and send them to the threat actors, but not before registering the newly-infected host with the command-and-control (C2) server. Other features of JanelaRAT allow it to track mouse inputs, log keystrokes, take screenshots, and harvest system metadata.
“JanelaRAT ships with just a subset of the features offered by BX RAT,” the researchers said. “The JanelaRAT developer didn’t import shell commands execution functionality, or files and processes manipulation functionalities.”

A closer analysis of the source code has revealed the presence of several strings in Portuguese, indicating that the author is familiar with the language.
The links to LATAM come from references to organizations operating in the banking and decentralized finance verticals and the fact that the VBScript uploads to VirusTotal originated from Chile, Colombia, and Mexico.
“The usage of original or modified commodity Remote Access Trojans (RATs) is common among threat actors operating in the LATAM region,” the researchers said. “JanelaRAT’s focus on harvesting LATAM financial data and its method of extracting window titles for transmission underscores its targeted and stealthy nature.”