Threat
actors
are
targeting
organizations
located
in
Donetsk,
Lugansk,
and
Crimea
with
a
previously
undetected
framework
dubbed CommonMagic.
In
October
2022,
Kaspersky
researchers
uncovered
a
malware
campaign
aimed
at
infecting
government,
agriculture
and
transportation
organizations
located
in
the
Donetsk,
Lugansk,
and
Crimea
regions
with
a
previously
undetected
framework
dubbed CommonMagic.
Researchers
believe
that
threat
actors
use
spear
phishing
as
an
initial
attack
vector,
the
messages
include
an
URL
pointing
to
a
ZIP
archive
hosted
on
a
web
server
under
the
control
of
the
attackers.
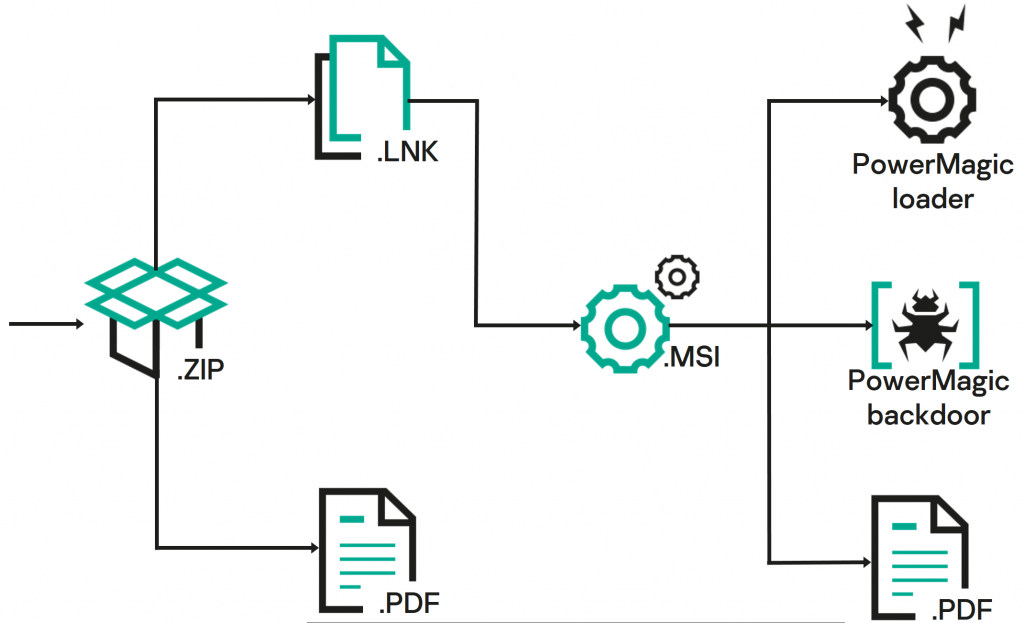
The
archive
contained
two
files,
a
decoy
document
(i.e.
PDF,
XLSX
and
DOCX
versions)
and
a
malicious
LNK
file
with
a
double
extension
(i.e.,
.pdf.lnk)
used
to
start
the
infection
and
deploy
the
PowerMagic
backdoor.
Kaspersky
attributes
the
attack
to
a
new
APT
group
operating
in
the
area
of
Russo-Ukrainian
conflict
and
tracked
as
Bad
magic.
The
experts
noticed
that
TTPs
observed
during
this
campaign
have
no
direct
link
to
any
known
campaigns.
PowerMagic
is
a
PowerShell
backdoor
that
executes
arbitrary
commands
sent
by
C2,
then
it
exfiltrates
data
to
cloud
services
like
Dropbox
and
Microsoft
OneDrive.
“When
started,
the
backdoor
creates
a
mutex
– WinEventCom.
Then,
it
enters
an
infinite
loop
communicating
with
its
C&C
server,
receiving
commands
and
uploading
results
in
response.
It
uses
OneDrive
and
Dropbox
folders
as
transport,
and
OAuth
refresh
tokens
as
credentials.”
reads
the
report
published
by
Kaspersky.
The
threat
actor
likely
used
the
PowerMagic
backdoor
to
deliver
the
modular CommonMagic
framework.
Each
module
of
the
CommonMagic
framework
is
used
to
perform
a
certain
task,
such
as
communicating
with
the
C2
server,
encrypting
and
decrypting
C2
traffic,
and
executing
plugins.
Kaspersky
analyzed
two
plugins
respectively
used
to
capture
screenshots
every
three
seconds
and
collects
the
contents
of
the
files
with
the
following
extensions
from
connected
USB
devices: .doc,
.docx.
.xls,
.xlsx,
.rtf,
.odt,
.ods,
.zip,
.rar,
.txt,
.pdf.
“So
far,
we
have
found
no
direct
links
between
the
samples
and
data
used
in
this
campaign
and
any
previously
known
actors.”
concludes
the
report.
“However,
the
campaign
is
still
active,
and
our
investigation
continues.
So,
we
believe
that
further
discoveries
may
reveal
additional
information
about
this
malware
and
the
threat
actor
behind
it.”
Follow
me
on
Twitter:
@securityaffairs
and
Facebook
and
Mastodon
(SecurityAffairs –
hacking,
CommonMagic)









