MQsTTang, a new backdoor used by Mustang Panda APT against European entities
China-Linked
Mustang
Panda
APT
employed
MQsTTang backdoor
as
part
of
an
ongoing
campaign
targeting
European
entities.
China-linked
Mustang
Panda
APT
group
has
been
observed
using
a
new
backdoor,
called MQsTTang, in
attacks
aimed
at
European
entities.
The
hacking
campaign
began
in
January
2023,
ESET
researchers
pointed
out
that
the
custom
backdoor
MQsTTang
is
not
based
on
existing
families
or
publicly
available
projects.
The
researchers
targeted
entities
in
Bulgaria,
Australia
and
a
governmental
institution
in
Taiwan.
However,
the
decoy
filenames
used
by
the
threat
actors
suggest
that
have
also
targeted
political
and
governmental
organizations
in
Europe
and
Asia.
Mustang
Panda
is
known
for
its customized
Korplug
backdoor (aka
PlugX),
but
the
recent
discovery
demonstrates
that
the
group
is
expanding
its
arsenal.
Some
of
the
attack
infrastructure
used
in
this
campaign
also
matches
the
network
fingerprint
of
infrastructure
used
by
Mustang
Panda
in
the
past.
“One
of
the
servers
used
in
the
current
campaign
was
running
a
publicly
accessible
anonymous
FTP
server
that
seems
to
be
used
to
stage
tools
and
payloads.
In
the /pub/god directory
of
this
server
there
are
multiple
Korplug
loaders,
archives,
and
tools
that
were
used
in
previous
Mustang
Panda
campaigns.”
reads
the
analysis
published
by
ESET.
MQsTTang
supports
common
backdoor
capabilities,
one
of
its
hallmarks
is
the
use
of
the MQTT
protocol for
C&C
communication.
The
MQTT
protocol
is
typically
used
for
communication
between
IoT
devices
and
controllers,
the
experts
noticed
that
hasn’t
been
used
in
many
publicly
documented
malware
families.
The
encoding
scheme
used
by
the
threat
actors
is
the
same
for
every
communication.
The
MQTT
message’s
payload
is
a
JSON
object
with
a
single
attribute
named
msg.
The
value
of
this
attribute
is
generated
by
first
encoding
in
base64
the
actual
content,
then
it
is
XORed
with
the
hardcoded
string
nasa,
and
base64
encoded
again.
The
backdoor
is
distributed
in
RAR
archives
containing
only
a
single
executable.
The
attackers
used
executables
having
names
related
to
Diplomacy
and
passports
such
as
“CVs
Amb
Officer
PASSPORT
Ministry
Of
Foreign
Affairs.exe”,
“Documents
members
of
delegation
diplomatic
from
Germany.Exe”,
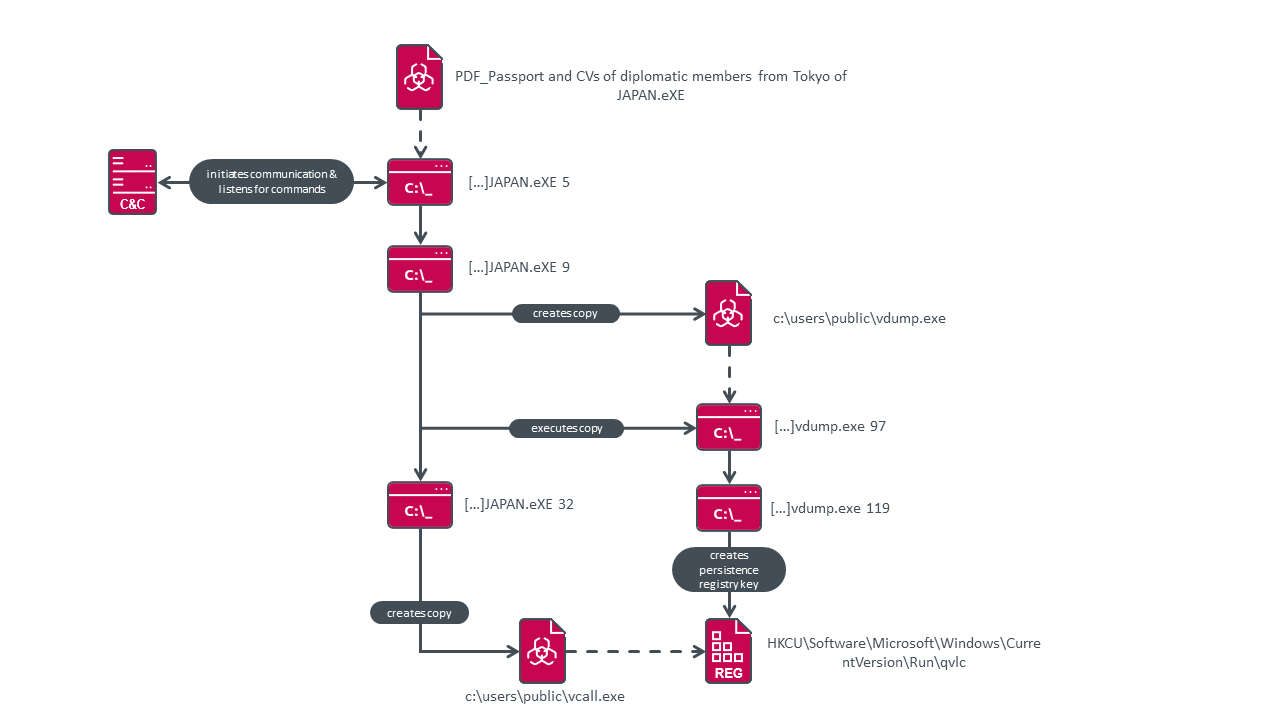
“PDF_Passport
and
CVs
of
diplomatic
members
from
Tokyo
of
JAPAN.eXE”,
“Note
No.18-NG-23
from
Embassy
of
Japan.exe.”
The
researchers
noticed
that
the
MQsTTang
backdoor
has
only
a
single
stage
and
doesn’t
use
any
obfuscation
techniques.
The
malware
maintains
persistence
using
a
specific
task
to
create
a
new
value
qvlc
set
to
c:userspublicvcall.exe
under
the
HKCUSoftwareMicrosoftWindowsCurrentVersionRun
registry
key.
“This
new
MQsTTang
backdoor
provides
a
kind
of
remote
shell
without
any
of
the
bells
and
whistles
associated
with
the
group’s
other
malware
families.
However,
it
shows
that
Mustang
Panda
is
exploring
new
technology
stacks
for
its
tools.”
concludes
the
report.
“It
remains
to
be
seen
whether
this
backdoor
will
become
a
recurring
part
of
the
group’s
arsenal,
but
it
is
one
more
example
of
the
group’s
fast
development
and
deployment
cycle.”
Follow
me
on
Twitter:
@securityaffairs
and
Facebook
and
Mastodon
(SecurityAffairs –
hacking,
Mustang
Panda)








%20v1.1.jpg#keepProtocol)