
Authored by Dexter Shin
MoqHao is a well-known Android malware family associated with the Roaming Mantis threat actor group first discovered in 2015. McAfee Mobile Research Team has also posted several articles related to this malware family that traditionally targets Asian countries such as Korea and Japan.
Recently McAfee Mobile Research Team found that MoqHao began distributing variants using very dangerous technique. Basically, the distribution method is the same. They send a link to download the malicious app via the SMS message. Typical MoqHao requires users to install and launch the app to get their desired purpose, but this new variant requires no execution. While the app is installed, their malicious activity starts automatically. This technique was introduced in a previous post but the difference is that this dangerous technique is now being abused by other well-known active malware campaigns like MoqHao. We have already reported this technique to Google and they are already working on the implementation of mitigations to prevent this type of auto-execution in a future Android version. Android users are currently protected by Google Play Protect, which is on by default on Android devices with Google Play Services. Google Play Protect can warn users or block apps known to exhibit malicious behavior, even when those apps come from sources outside of Play. McAfee Mobile Security detects this threat as Android/MoqHao.
How it is distributed
MoqHao is distributed via phishing SMS messages (also known as Smishing). When a user receives an SMS message containing a malicious link and clicks it, the device downloads the malicious application. Phishing messages are almost the same as in previous campaigns:
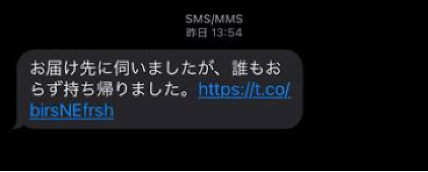
Figure 1. Smishing message impersonating a notification from a courier service.
Japanese message: I went to the delivery address, but no one was there. So, I brought it back.
One noticeable change is that they now use URL shortener services. If the malware authors use their own domain, it can be quickly blocked but if they use legitimate URL shortener services, it is difficult to block the short domain because it could affect all the URLs used by that service. When a user clicks on the link in the message, it will be redirected to the actual malicious site by the URL shortener service.
What is new in this variant
As mentioned at the beginning, this variant behaves differently from previous ones. Typical MoqHao must be launched manually by the user after it is installed but this variant launches automatically after installation without user interaction:
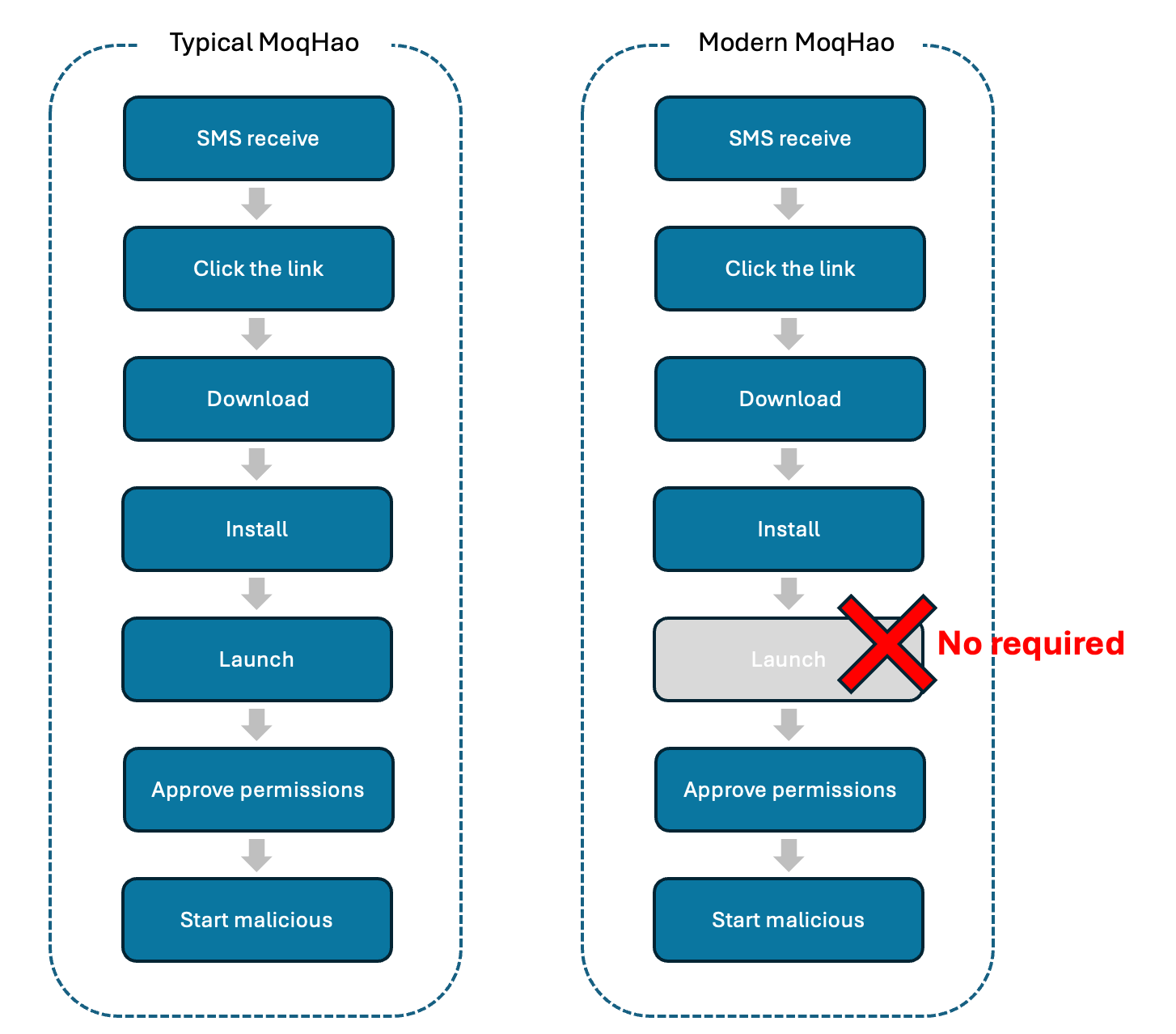
Figure 2. Differences between typical MoqHao and Modern MoqHao
We explained this auto-execution technique in detail in a previous post but to briefly summarize it here, Android is designed so when an app is installed and a specific value used by the app is set to be unique, the code runs to check whether the value is unique upon installation. This feature is the one that is being abused by the highly active Trojan family MoqHao to auto-execute itself without user interaction. The distribution, installation, and auto-execution of this recent MoqHao variant can be seen in the following video:
On the other hand, this recent MoqHao variant uses Unicode strings in app names differently than before. This technique makes some characters appear bold, but users visually recognize it as “Chrome”. This may affect app name-based detection techniques that compare app name (Chrome) and package name (com.android.chrome):
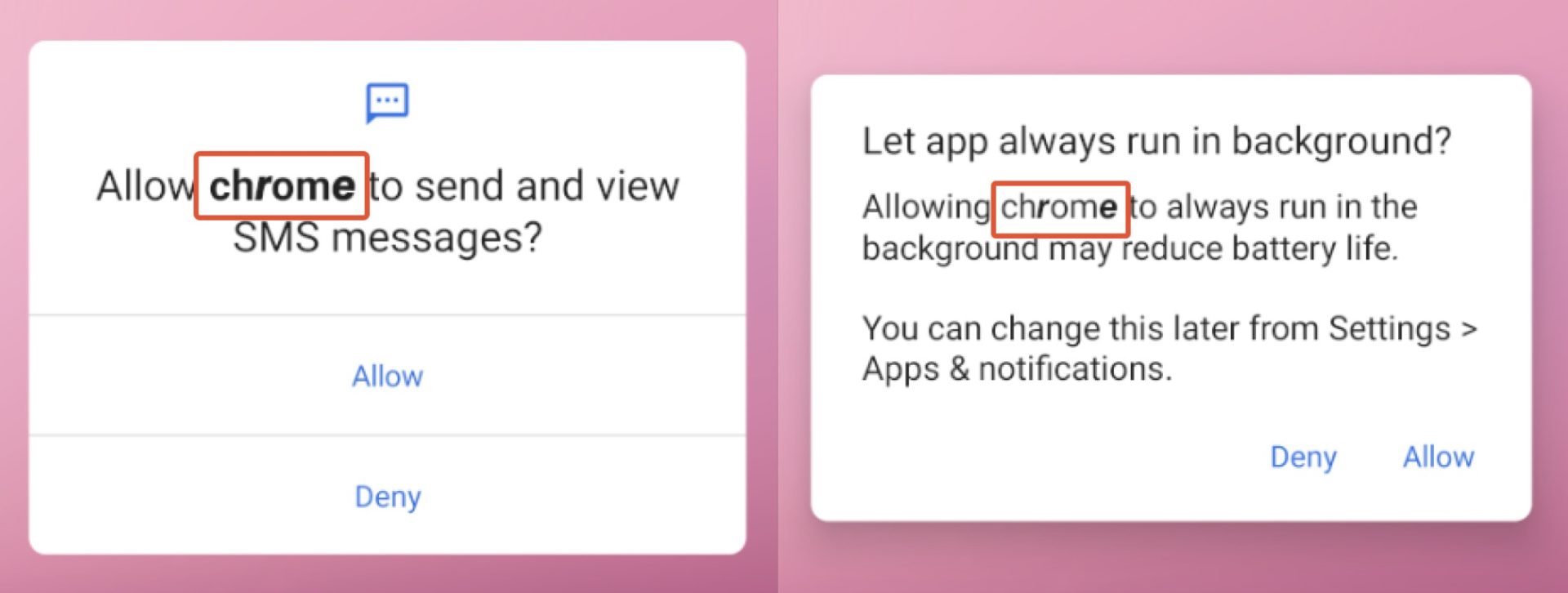
Figure 3. App name using Unicode strings.
Additionally, they also use social engineering techniques to set malicious apps as the default SMS app. Before the settings window appears, they show a message telling you to set up the app to prevent spam, but this message is fake:
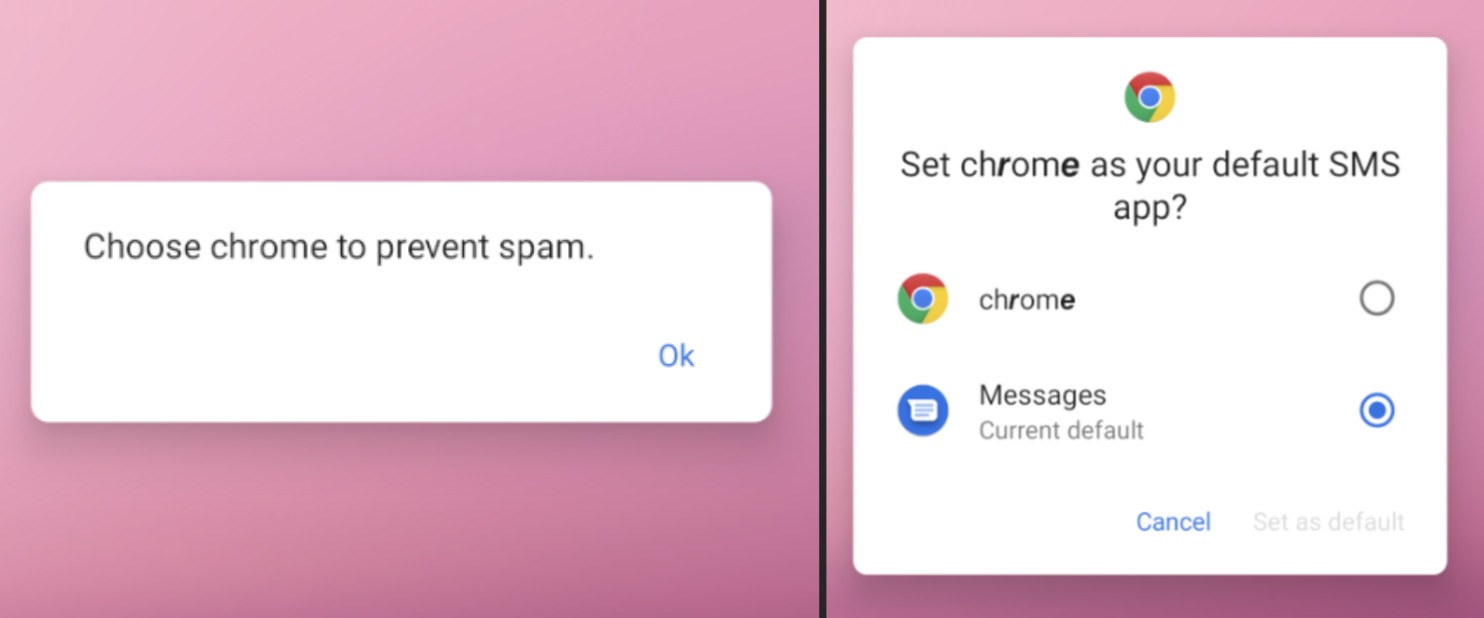
Figure 4. Fake message using social engineering techniques.
Also, the different languages used in the text associated with this behavior suggests that, in addition to Japan, they are also targeting South Korea, France, Germany, and India:
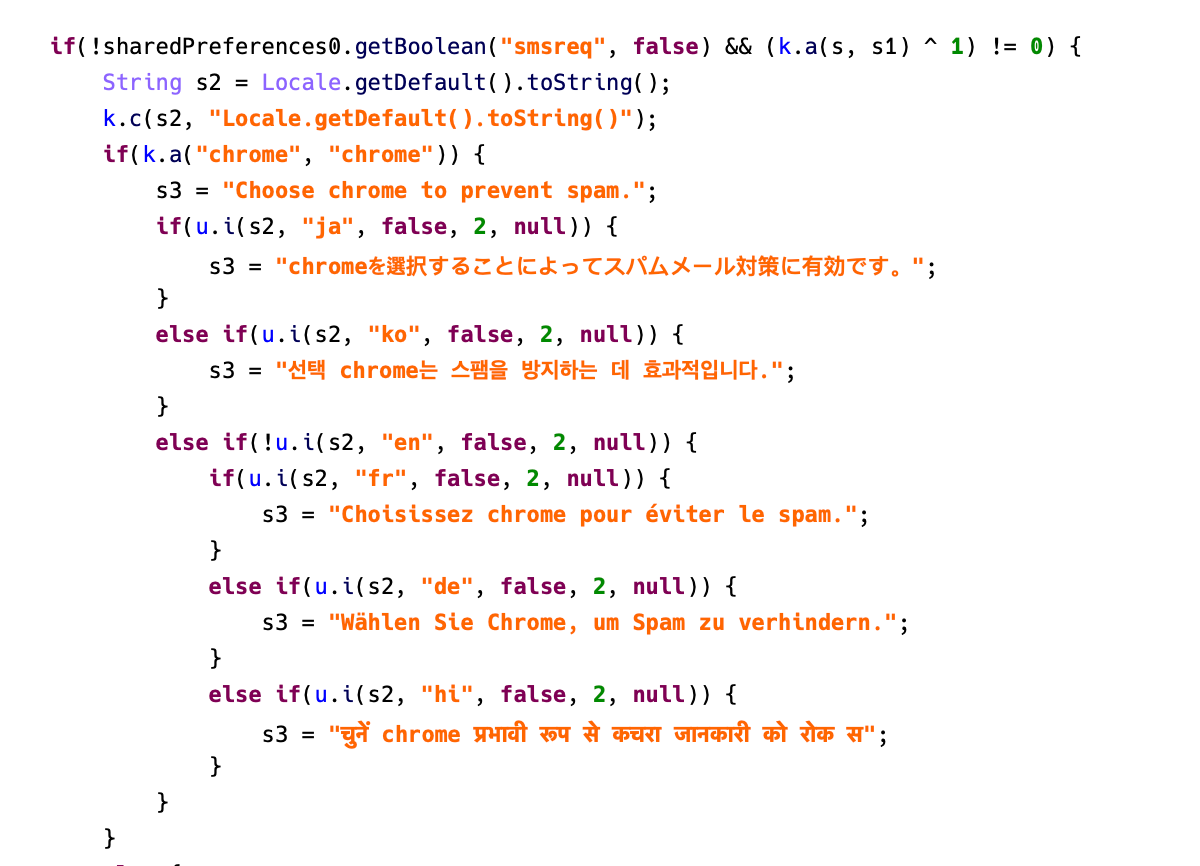
Figure 5. Fake messages designed to target different countries.
After the initialization of the malware is completed, it will create a notification channel that will be used to display phishing messages:
Figure 6. Create a notification channel for the next phishing attack.
The malware checks the device’s carrier and uses this notification to send phishing messages accordingly to trick users into clicking on them. MoqHao gets the phishing message and the phishing URL from Pinterest profiles.
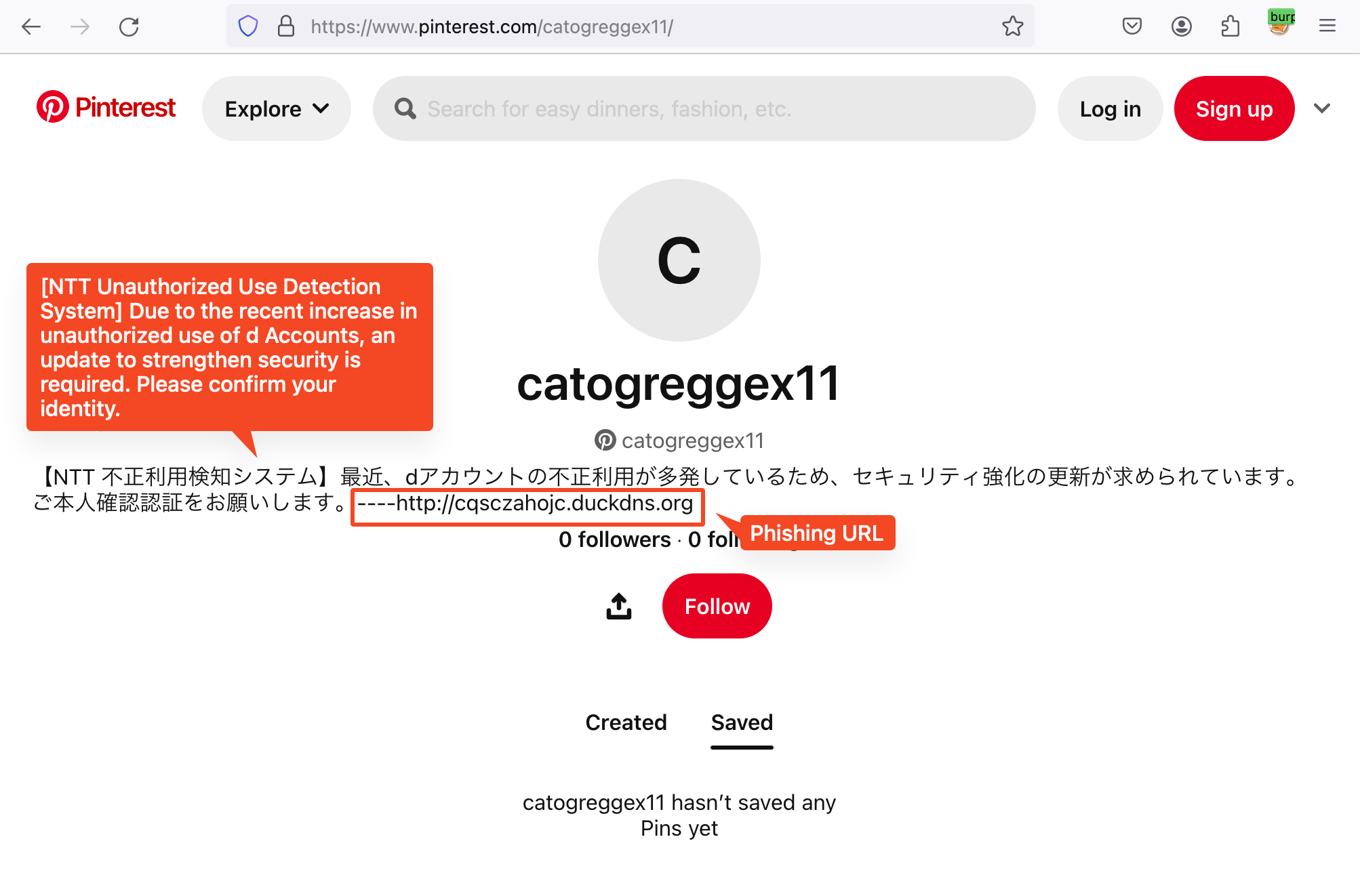
Figure 7. Phishing message and URL in Pinterest profile
If the phishing string is empty, MoqHao will use the phishing message in the code:
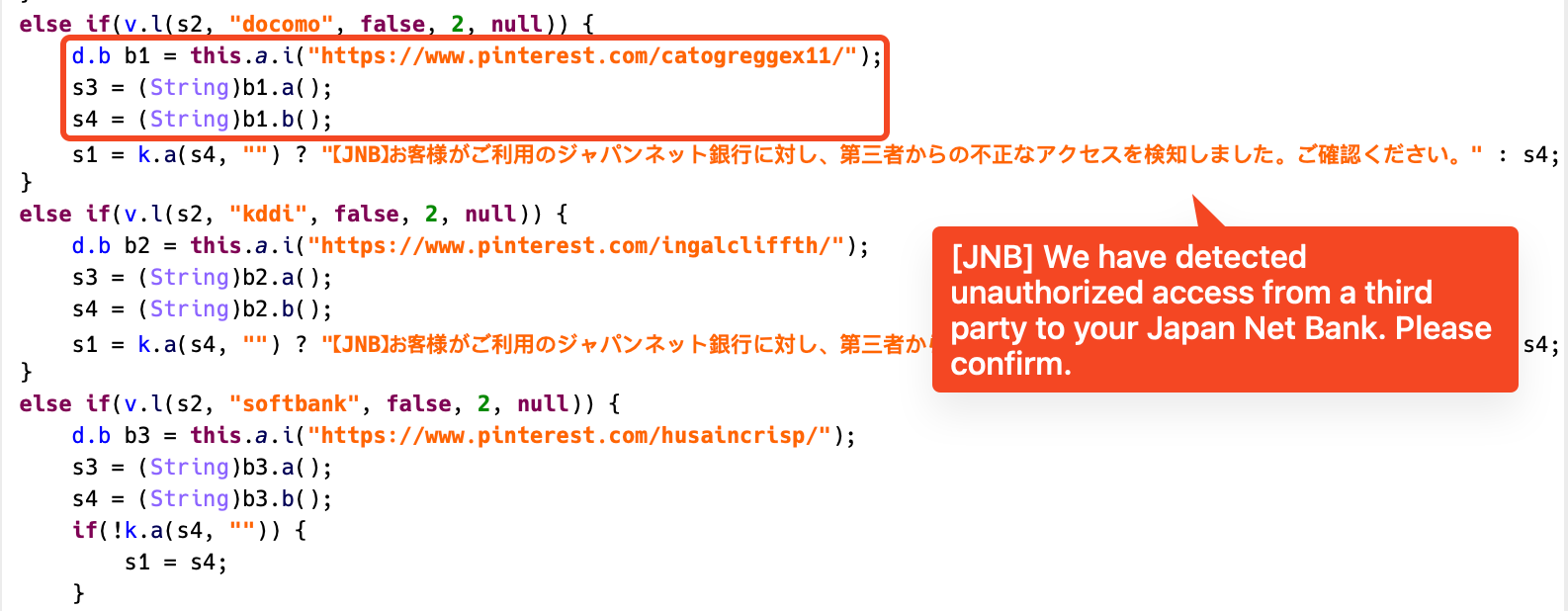
Figure 8. Phishing notification code for each carrier
This variant also connects to the C2 server via WebSocket. However, it has been confirmed that several other commands have been added in addition to the commands introduced in the previous post:
| Command | Description |
| getSmsKW | Send all SMS messages to C2 server |
| sendSms | Send SMS messages to someone |
| setWifi | Enable/disable Wifi |
| gcont | Send whole contacts to C2 server |
| lock | Store Boolean value in “lock” key in SharedPreferences |
| bc | Check SIM state |
| setForward | Store String value in “fs” key in SharedPreferences |
| getForward | Get String value in “fs” key in SharedPreferences |
| hasPkg | Check specific package installed on device |
| setRingerMode | Set Sound/Vibrate/Silent mode |
| setRecEnable | Set Vibrate/Silent mode according to SDK version |
| reqState | Send device information (Network, Power, MAC, Permission) to C2 server |
| showHome | Emulate Home button click |
| getnpki | Send Korean Public Certificate (NPKI) to C2 server |
| http | Send HTTP requests |
| call | Call a specific number with Silent mode |
| get_apps | Get list of installed packages |
| ping | Check C2 server status |
| getPhoneState | Get unique information such as IMEI, SIM number, Android ID, and serial number |
| get_photo | Send all photos to C2 server |
MoqHao malware family is an active malware that has been around for years. Although many years have passed, they are using more and more different ways to hide and reach users. We are seeing a much higher number of C2 commands than in previous, the active use of legitimate sites like Pinterest to store and update phishing data, and code with the potential to target Asian countries like Japan and South Korea, as well as countries like France, Germany, and India. Moreover, we expect this new variant to be highly impactful because it infects devices simply by being installed without execution.
It is difficult for general users to find fake apps using legitimate icons and application names, so we recommend users to install secure software to protect their devices. For more information, visit McAfee Mobile Security.
Indicators of Compromise (IOCs)
| SHA256 | Application Name | Package Name |
| 2576a166d3b18eafc2e35a7de3e5549419d10ce62e0eeb24bad5a1daaa257528 | chom | gb.pi.xcxr.xd |
| 61b4cca67762a4cf31209056ea17b6fb212e175ca330015d804122ee6481688e | hm | malmkb.zdbd.ivakf.lrhrgf |
| b044804cf731cd7dd79000b7c6abce7b642402b275c1eb25712607fc1e5e3d2b | cm | vfqhqd.msk.xux.njs |
| bf102125a6fca5e96aed855b45bbed9aa0bc964198ce207f2e63a71487ad793a | chro | hohoj.vlcwu.lm.ext |
| e72f46f15e50ce7cee5c4c0c5a5277e8be4bb3dd23d08ea79e1deacb8f004136 | hroe | enech.hg.rrfy.wrlpp |
| f6323f8d8cfa4b5053c65f8c1862a8e6844b35b260f61735b3cf8d19990fef42 | chre | gqjoyp.cixq.zbh.llr |
The post MoqHao evolution: New variants start automatically right after installation appeared first on McAfee Blog.



