Microsoft
and
cybersecurity
firm
Proofpoint
on
Tuesday
warned
organizations
that
use
cloud
services
about
a
recent
campaign
that
involved
malicious
OAuth
applications
and
abuse
of
Microsoft’s
‘verified
publisher’
status.
The
campaign
mainly
targeted
Microsoft
customers
in
Ireland
and
the
UK.
The
tech
giant
has
taken
steps
to
disrupt
the
operation
and
it
has
published
an
article
on
how
users
can
protect
against
these
threats,
which
the
company
calls
‘consent
phishing’.
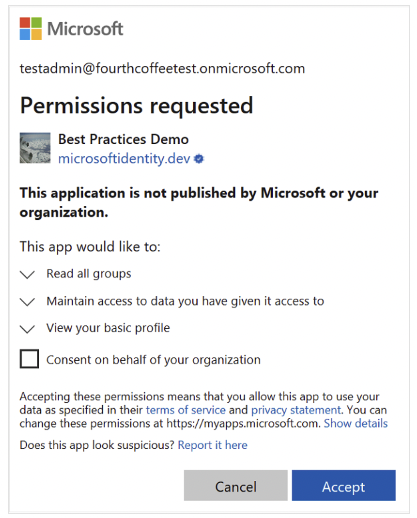
In
a
consent
phishing
attack,
a
threat
actor
attempts
to
trick
a
targeted
user
into
granting
permissions
to
their
malicious
cloud
applications.
Once
they
have
obtained
the
required
permissions,
the
malicious
apps
can
gain
access
to
legitimate
cloud
services
and
user
data.
In
a
campaign
uncovered
by
Proofpoint
in
December
2022,
hackers
created
malicious
OAuth
apps
and
then
obtained
a
‘verified
publisher’
status
in
an
effort
to
increase
their
chances
of
tricking
users.
According
to
Microsoft,
the
attackers
impersonated
legitimate
companies
when
enrolling
in
the
Microsoft
Cloud
Partner
Program
(MCPP).
“The
actor
used
fraudulent
partner
accounts
to
add
a
verified
publisher
to
OAuth
app
registrations
they
created
in
Azure
AD,”
Microsoft
explained.
This
made
it
more
likely
for
targeted
users
to
grant
permissions
to
the
malicious
applications.
These
permissions
included
reading
emails,
changing
email
settings,
and
accessing
files
and
other
user
data,
such
as
calendar
and
meeting
information.

Microsoft’s
investigation
showed
that
the
attackers
used
the
malicious
OAuth
applications
to
exfiltrate
emails.
According
to
Proofpoint,
the
attackers
used
three
malicious
apps
created
by
three
different
publishers.
They
all
used
the
same
malicious
infrastructure
and
targeted
the
same
organizations.
“The
potential
impact
to
organizations
includes
compromised
user
accounts,
data
exfiltration,
brand
abuse
of
impersonated
organizations,
business
email
compromise
(BEC)
fraud,
and
mailbox
abuse,”
Proofpoint
said.
“The
attack
was
less
likely
to
be
detected
than
traditional
targeted
phishing
or
brute
force
attacks.
Organizations
typically
have
weaker
defense-in-depth
controls
against
threat
actors
using
verified
OAuth
apps.”
According
to
Proofpoint,
the
campaign
ran
until
December
27.
The
security
firm
observed
attacks
against
financial
and
marketing
staff,
as
well
as
executives
and
managers.
Microsoft
said
it
became
aware
of
the
campaign
on
December
15.
The
company
has
disabled
all
fraudulent
applications
and
alerted
affected
customers.
Microsoft
recently
also
dismantled
a
campaign
that
leveraged
a
network
of
single-tenant
OAuth
applications
for
the
distribution
of
spam.
Related:
GitHub
Warns
of
Private
Repositories
Downloaded
Using
Stolen
OAuth
Tokens
Related:
CircleCI
Hacked
via
Malware
on
Employee
Laptop
Related:
Okta
Source
Code
Stolen
by
Hackers









