Microsoft Details Critical Apple macOS Vulnerability Allowing SIP Protection Bypass
Microsoft
has
shared
details
of
a
now-patched
flaw
in
Apple
macOS
that
could
be
abused
by
threat
actors
with
root
access
to
bypass
security
enforcements
and
perform
arbitrary
actions
on
affected
devices.
Specifically,
the
flaw
–
dubbed
Migraine
and
tracked
as
CVE-2023-32369
–
could
be
abused
to
get
around
a
key
security
measure
called
System
Integrity
Protection
(SIP),
or
“rootless,”
which
limits
the
actions
the
root
user
can
perform
on
protected
files
and
folders.
“The
most
straight-forward
implication
of
a
SIP
bypass
is
that
[…]
an
attacker
can
create
files
that
are
protected
by
SIP
and
therefore
undeletable
by
ordinary
means,”
Microsoft
researchers
Jonathan
Bar
Or,
Michael
Pearse,
and
Anurag
Bohra
said.
Even
worse,
it
could
be
exploited
to
gain
arbitrary
kernel
code
execution
and
even
access
sensitive
data
by
replacing
databases
that
manage
Transparency,
Consent,
and
Control
(TCC)
policies.
The
bypass
is
made
possible
by
leveraging
a
built-in
macOS
tool
called
Migration
Assistant
to
activate
the
migration
process
via
an
AppleScript
that’s
designed
to
ultimately
launch
an
arbitrary
payload.
This,
in
turn,
stems
from
the
fact
that
systemmigrationd
–
the
daemon
used
to
handle
device
transfer
–
comes
with
the
com.apple.rootless.install.heritable
entitlement,
allowing
all
its
child
processes,
including
bash
and
perl,
to
bypass
SIP
checks.
As
a
result,
a
threat
actor
already
with
code
execution
capabilities
as
root
could
trigger
systemmigrationd
to
run
perl,
which
could
then
be
used
to
run
a
malicious
shell
script
as
the
migration
process
is
underway.
Following
responsible
disclosure,
the
vulnerability
was
addressed
by
Apple
as
part
of
updates
(macOS
Ventura
13.4,
macOS
Monterey
12.6.6,
and
macOS
Big
Sur
11.7.7)
shipped
on
May
18,
2023.
The
iPhone
maker
described
CVE-2023-32369
as
a
logic
issue
that
could
allow
a
malicious
app
to
modify
protected
parts
of
the
file
system.
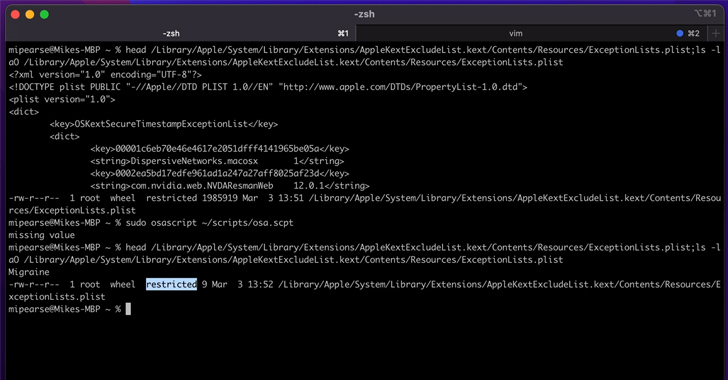
Migraine
is
the
latest
addition
to
the
list
of
macOS
security
bypasses
that
have
been
documented
under
the
names
Shrootless
(CVE-2021-30892,
CVSS
score:
5.5),
powerdir
(CVE-2021-30970,
CVSS
score:
5.5),
and
Achilles
(CVE-2022-42821,
CVSS
score:
5.5).
UPCOMING
WEBINAR
Zero
Trust
+
Deception:
Learn
How
to
Outsmart
Attackers!
Discover
how
Deception
can
detect
advanced
threats,
stop
lateral
movement,
and
enhance
your
Zero
Trust
strategy.
Join
our
insightful
webinar!
“The
implications
of
arbitrary
SIP
bypasses
are
serious,
as
the
potential
for
malware
authors
is
significant,”
the
researchers
said.
“Bypassing
SIP
could
lead
to
serious
consequences,
such
as
increasing
the
potential
for
attackers
and
malware
authors
to
successfully
install
rootkits,
create
persistent
malware,
and
expand
the
attack
surface
for
additional
techniques
and
exploits.”
The
findings
come
as
Jamf
Threat
Labs
disclosed
details
of
a
type
confusion
flaw
in
the
macOS
kernel
that
could
be
weaponized
by
a
rogue
app
installed
on
the
device
to
execute
arbitrary
code
with
kernel
privileges.
Labeled
ColdInvite
(aka
CVE-2023-27930),
the
flaw
“can
be
exploited
to
leverage
the
co-processor
in
order
to
obtain
read/write
privileges
to
the
kernel,
allowing
a
bad
actor
to
get
closer
to
realizing
their
ultimate
goal
of
fully
compromising
the
device.”