
These
ransomware
infections
on
VMware
ESXi
software
are
due
to
a
vulnerability
that
has
existed
since
2021.
Find
out
the
most
targeted
countries
and
how
to
secure
your
organization.

Adobe
Stock
Jump
to:
How
does
this
ransomware
attack
operate?
CVE-2021-21974
is
a
vulnerability
affecting
OpenSLP
as
used
in
VMware
ESXi.
Successful
exploitation
of
that
vulnerability
allows
an
attacker
to
execute
arbitrary
code,
and
exploits
for
this
vulnerability
can
be
found
in
various
open
sources
since
May
2021.
The
French
government’s
Computer
Emergency
Response
Team
CERT-FR
was
the
first
to
raise
an
alert
on
ransomware
exploiting
this
vulnerability
on
Feb.
3,
2023,
quickly
followed
by
French
hosting
provider
OVH.
Attackers
can
exploit
the
vulnerability
remotely
and
unauthenticated
via
port
427
(Service
Location
Protocol,
SLP),
which
is
a
protocol
that
most
VMware
customers
do
not
use.
The
ransomware
encrypts
files
with
the
following
extensions
on
the
affected
systems:
.vmdk,
.vmxf,
.vmsd,
.vmsn,
.vmss,
.vswp,
.nvram
and
.vmem.
Then,
it
tries
to
shut
down
the
virtual
machines
by
killing
the
VMX
process
to
unlock
the
files.
A
text
note
is
left
after
encryption
is
done
(Figure
A),
asking
for
ransom
that
must
be
paid
in
Bitcoin
cryptocurrency
within
three
days.
Figure
A
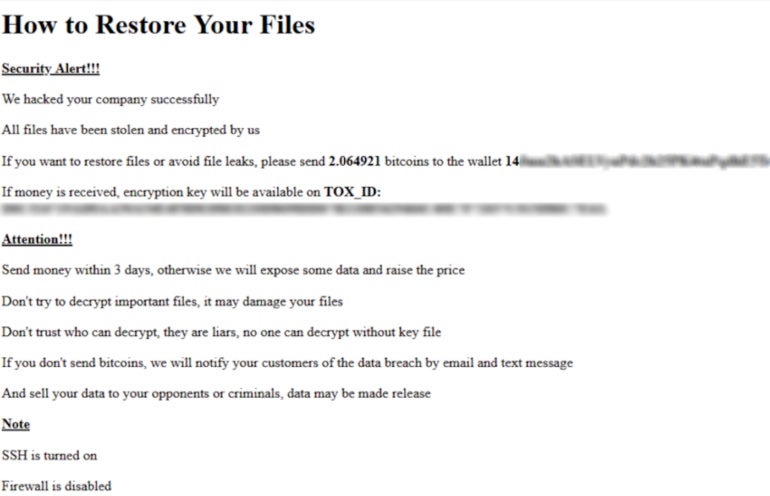
Twitter.
Ransom
note
left
on
a
targeted
device.
The
ransomware
threat
actor
behind
this
attack
is
not
known,
as
the
malware
seems
to
be
a
new
ransomware.
OVH
has
reported
that
according
to
several
security
researchers,
the
encryption
cipher
used
in
the
ransomware
is
the
same
as
what
was
used
in
the
leaked
Babuk
malware
code
from
September
2021,
although
the
code
structure
is
different.
The
Babuk
code
that
leaked
in
2021
has
been
used
to
create
other
malware
that
often
targets
ESXi
systems,
but
it
seems
too
early
to
draw
a
definitive
conclusion
as
to
the
attribution
of
that
new
malware,
which
has
been
dubbed
ESXiArgs
by
security
researchers.
France
and
U.S.
are
the
biggest
targets
Censys
Search,
an
online
tool
for
searching
through
internet-connected
devices,
shows
that
more
than
1,000
servers
have
been
successfully
hit
by
the
ransomware,
mostly
in
France,
followed
by
the
U.S.
and
Germany.
At
the
time
of
writing,
more
than
900
servers
were
compromised
in
France,
while
approximately
400
servers
in
the
U.S.
were
hit.
A
lot
more
systems
might
be
vulnerable
and
not
yet
attacked.
The
Shadowserver
Foundation
reports
that
around
27,000
instances
may
be
vulnerable,
according
to
the
version
of
its
VMware
software.
How
to
protect
your
organization
from
this
ransomware
threat
For
systems
running
unpatched
versions
of
VMware
ESXi,
the
absolute
priority
is
to
cut
the
SLP
service
if
it
runs.
The
vulnerability
can
only
be
exploited
via
that
service,
so
if
it
is
closed,
the
system
cannot
be
attacked
via
this
vector.
The
next
step
consists
of
reinstalling
the
hypervisor
in
a
version
supported
by
VMware
—
ESXi
7.x
or
ESXi
8.x
—
and
applying
all
security
patches.
Finally,
all
administration
services
should
be
protected
and
only
available
locally.
In
case
there
is
a
need
for
remote
access,
VPN
with
multi-factor
authentication
or
IP
filtering
should
be
used.
Jan
Lovmand,
chief
technology
officer
of
BullWall,
a
cybersecurity
firm
focused
on
preventing
ransomware
attacks,
told
TechRepublic
more
about
the
vulnerability.
“A
patch
has
been
available
from
VMware
since
February
2021
when
the
vulnerability
was
discovered,”
Lovmand
said.
“This
just
goes
to
show
how
long
it
takes
many
organizations
to
get
around
to
patch
internal
systems
and
applications,
which
is
just
one
of
many
reasons
why
the
criminals
keep
finding
their
way
in.
The
attack
surface
is
big,
and
preventative
security
solutions
can
be
bypassed
in
a
scenario
like
this
if
the
vulnerability
has
not
been
patched.”
Lovmand
also
stressed
the
importance
of
patching
your
networks.
“It’s
50-50
odds
that
your
company
will
be
successfully
hit
with
ransomware
in
2023,”
he
said.
“Security
solutions
cannot
protect
unpatched
networks.”
How
to
recover
from
this
ransomware
threat
Security
researchers
Enes
Somnez
and
Ahmet
Aykac
have
provided
a
solution
to
recover
in
case
a
system
has
been
attacked
by
this
ransomware.
The
researchers
explain
that
the
ransomware
encrypts
small
files
like
.vmdk
and
.vmx
but
not
the
server-flat.vmdk
file,
which
contains
the
actual
data.
Using
this
file,
it’s
possible
to
do
a
fallback
and
recover
information
from
the
system.
Julien
Levrard,
chief
information
security
officer
from
OVHCloud,
wrote
that
the
method
documented
by
Somnez
and
Aykac
has
been
tested
by
OVH
as
well
as
many
security
experts
with
success
on
several
impacted
servers,
with
a
success
rate
of
2/3.
He
added
that
“this
procedure
requires
strong
skills
on
ESXi
environments.”
Disclosure:
I
work
for
Trend
Micro,
but
the
views
expressed
in
this
article
are
mine.
Read
next:
Patch
management
policy
(TechRepublic
Premium)











