
A recent investigation conducted by cybersecurity firm ESET unveils insights into a novel assault campaign aimed at Android mobile device users.
The cyber intrusion, fueled by an intricate social manipulation stratagem and the utilization of a new Android malicious software, possesses the capability to filch users’ near field communication data to extract cash from NFC-capable cash machines.
Unceasing technical enhancements by the adversary
According to ESET’s report, the adversary initially leveraged innovative web application technology, permitting the installation of an application from any webpage beyond the Play Store. This technology can be employed with compatible web browsers such as Chromium-based browsers on desktops or Firefox, Chrome, Edge, Opera, Safari, Orion, and Samsung Internet Browser.
Web applications (PWAs) that can be accessed directly via browsers are adaptive and typically do not encounter compatibility issues. Post installation on devices, PWAs can be distinguished by their emblem that showcases an extra petite browser icon.

Malefactors exploit PWAs to direct unsuspecting individuals to full-screen bogus websites for amassing their login information or credit card details.
The adversary engaged in this campaign executed a shift from PWAs to WebAPKs, an elevated form of PWAs. The distinction lies in the fact that PWAs are applications constructed using web technologies, while WebAPKs encompass a technology to embed PWAs as native Android programs.
From the malefactor’s viewpoint, deploying WebAPKs operates with greater stealth since their icons no longer feature a small browser emblem.

The victim downloads and installs a standalone application from a counterfeit website. The individual does not seek any additional authorization to install the program from an external site.
These deceptive websites frequently resemble fragments of the Google Play Store to generate confusion and deceive the user into presuming that the installation is originating from the Play Store, whereas it, in reality, originates directly from the deceptive site.
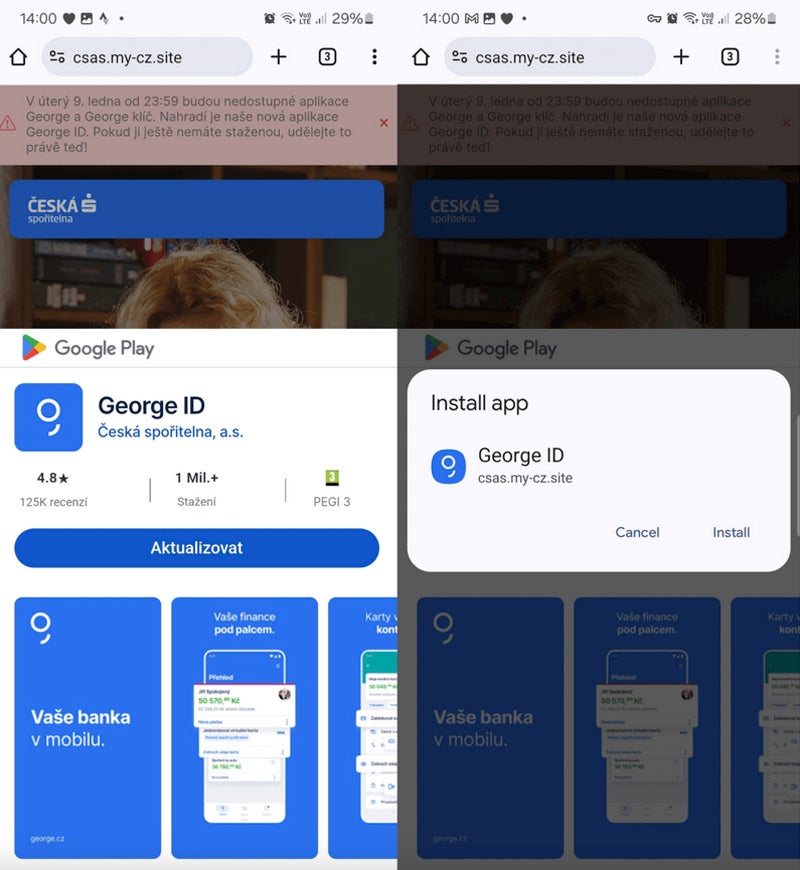
NGate malware
On March 6, the identical distribution domains employed for the noted PWAs and WebAPKs phishing operations abruptly commenced disseminating a fresh malware named NGate. Upon installation and execution on the target’s device, it unveils a bogus webpage soliciting the user’s banking details, which are conveyed to the adversary.
Furthermore, the malware integrated a utility dubbed NFCGate, a legitimate tool facilitating the relay of NFC data between two devices devoid of necessitating root access.
Post provision of the banking details by the individual, they are prompted to activate the NFC functionality on their handset and to position their credit card against the back of the phone until the application successfully detects the card.
Complete social engineering
While enabling NFC for an application and engaging in a paymentThe recognition of the card might appear dubious initially, but the social engineering tactics employed by malicious actors help clarify the situation.
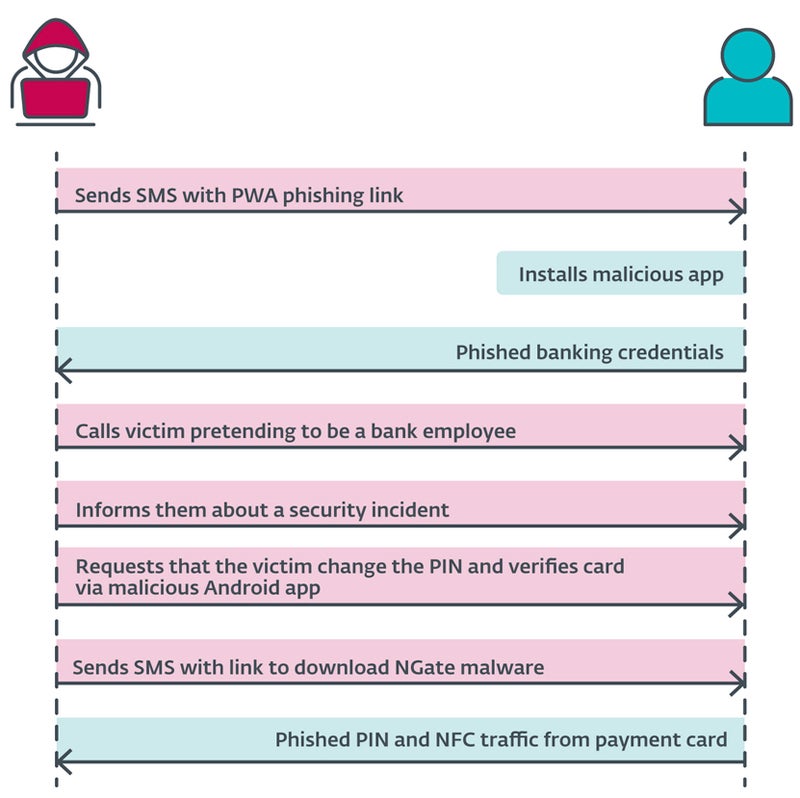
A SMS is sent by the cybercriminal to the user, discussing a tax refund and including a link to a deceptive website that pretends to be a banking institution and leads to a harmful PWA. Once the application is installed and launched, it requests banking login details from the user.
Subsequently, the threat actor contacts the user, posing as a bank representative. The individual is informed that their account has been compromised, possibly because of the preceding SMS. The user is then asked to modify their PIN and validate their card details through a mobile app to safeguard their bank account.
Next, the user gets another SMS with a link to the NGate malware app.
Once installed, the app requests the activation of the NFC feature and the reading of the credit card by tapping it against the rear of the smartphone. The information is then transmitted to the attacker in real time.
Monetizing the pilfered data
The data pilfered by the attacker allows for typical fraud: withdrawing funds from the bank account or utilizing credit card information to purchase items online.
Nevertheless, the NFC details stolen by the cybercriminal enable them to replicate the original credit card and withdraw funds from ATMs that support NFC, illustrating a hitherto unreported attack avenue.
Extent of the assault
ESET’s research unveiled attacks in the Czech Republic, as exclusively banking institutions in that nation were targeted.
Prague has apprehended a 22-year-old suspect. He was carrying approximately €6,000 ($6,500 USD). As per Czech Police, that money stemmed from thievery from the last three victims, implying that the threat actor filched much more during this assault campaign.
However, as asserted by ESET researchers, “the potential expansion into other regions or countries cannot be dismissed.”
More malevolent actors are likely to adopt similar methodologies in the imminent future to siphon funds via NFC, particularly as NFC garners more favor among developers.
Safeguarding against this menace
To elude succumbing to this cyber onslaught, users ought to:
- Validate the origin of the apps they download and meticulously peruse URLs to confirm their authenticity.
- Abstain from downloading apps from unofficial sources, like the Google Play Store.
- Refrain from divulging their payment card PIN. No legitimate bank will ever request this sensitive information.
- Utilize digital renditions of conventional physical cards, as these virtual cards are securely stored on the device and can be fortified with additional security features like biometric verification.
- Implement security software on mobile gadgets to detect malware and undesired apps on the device.
Users should also deactivate NFC on smartphones when not in use, preventing them from further data theft. Perpetrators can intercept card data via unguarded handbags, wallets, and bags in public settings. The garnered data can be utilized for small contactless transactions. Protective casings can also be employed to construct an effective impediment against unwarranted scans.
If any inkling of doubt arises when contacted by a purported banking company representative, terminate the call and dial the regular banking entity number, preferably from an alternative device.
Disclosure: I am affiliated with Trend Micro, however, the opinions expressed in this write-up are my own.







