
LogRhythm NextGen SIEM and SolarWinds Security Events Manager offer tools for managing security information and events to individuals seeking to safeguard the security of their organization’s networks and digital devices. After my analysis, I have concluded that each platform is designed for distinct user preferences:
- LogRhythm: Ideal for established enterprises with extensive security requirements and a specialized security operations center team.
- SolarWinds: Suitable for smaller teams or users in need of simplified reporting.
Side-by-Side Comparison of LogRhythm and SolarWinds
| Features | ||
|---|---|---|
| Pricing | ||
| Free trial | ||
| Real-time monitoring | ||
| Logging | ||
| Analytics | ||
| Reporting | ||
| Threat management | ||
| Incident response | ||
| Customization | ||
Cost
LogRhythm
LogRhythm offers perpetual licensing and subscription-based pricing models, but the company does not publicly reveal pricing details. The absence of pricing information is a drawback, particularly as LogRhythm does not provide a free trial. The licensing permits unlimited users and log sources and is compatible with cloud, hardware, and virtual machines. To obtain precise pricing information, reach out to LogRhythm directly.
For additional insights, refer to our comparison of LogRhythm and Splunk and our guide on embracing Splunk’s SIEM platform.
SEE: Comprehensive Guide on the Malvertising Cybersecurity Threat (TechRepublic Premium)
SolarWinds
SolarWinds pricing commences at $2,992, with the possibility of opting for a personalized pricing structure. Users can select between perpetual licensing for indefinite license use or a subscription-based model. Although the initial expense of subscription-based licensing is lower than that of purchasing a perpetual license, the long-term cost is higher. SolarWinds offers a 30-day free trial, which is noteworthy given that LogRhythm lacks a free trial option.
Feature Comparison of LogRhythm and SolarWinds
Threat monitoring
LogRhythm scrutinizes organizational data and events to identify anomalies across networks and endpoints. The system gathers security data, log data, and flow data to deliver comprehensive real-time visibility and effective threat detection. Risk-based monitoring eradicates blind spots and rapidly detects threats, enabling timely responses to mitigate potential damage.
Utilizing threat intelligence, machine learning, and behavior analytics, LogRhythm’s Endpoint Threat Detection Module identifies potential threats. It is worth noting that LogRhythm’s SIEM employs multiple threat detection techniques, such as recognizing unusual communication patterns, lateral movements, and alterations to sensitive files.
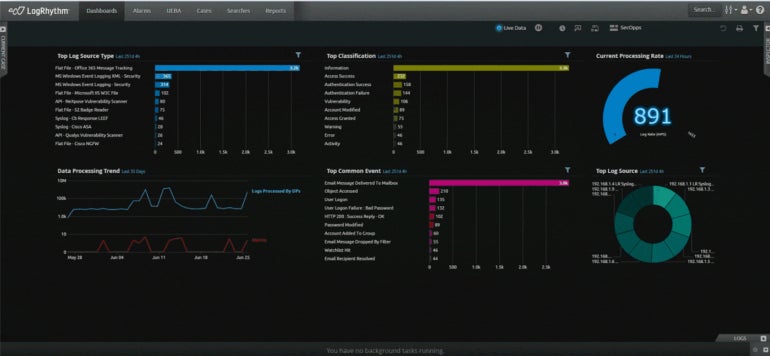
The SolarWinds SIEM solution ensures constant threat detection and real-time monitoring across users’ devices, services, files, and directories with its on-premises and multicloud implementations. Its intuitive dashboard and user-friendly interface simplify navigation through the tool’s functionalities. The centralized repository acquires log data using the SIEM log collector tool,and uncooked network log data is arranged and standardized for users within the system.
Being dubbed as the finest option for log aggregation in our compilation of the top SIEM tools is largely due to this. Moreover, I value the inclusion of event-time correlation and advanced search capabilities in SolarWinds, which prove advantageous when partaking in forensic analysis and security examination.
Threat monitoring
The LogRhythm NextGen SIEM system utilizes multidimensional analytics to pinpoint and halt security risks. The collected data is normalized and cross-referenced to unveil potentially hazardous behavior, thereby enhancing precision. I also appreciated the analysis of network traffic and packet data for irregular patterns and behaviors.
The functionalities for behavioral analysis can scrutinize the activities of users within a network and recognize deviations from the standard baseline behavior; this is achievable through the application of machine learning and can bolster security against unauthorized internal access and data extraction. Additionally, the system supports both contextual and unstructured searches.
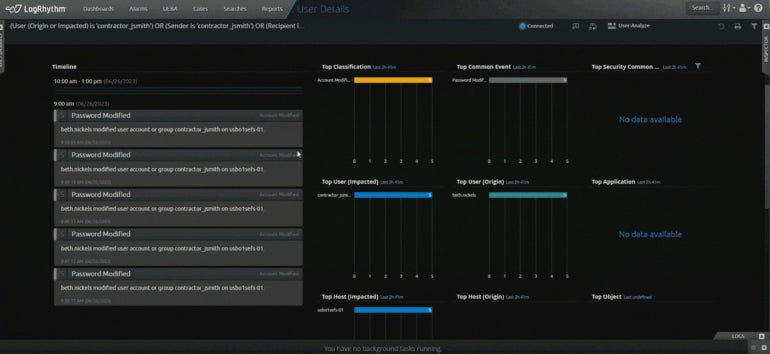
The SolarWinds SIEM system processes data and occurrences to uncover signs of security threats. The event log analyzer gathers and scrutinizes log data, furnishing users with real-time insight and context. Incidents are monitored to pinpoint dubious actions, such as alterations in permissions and data adjustments. This information is then linked through preset and personalized event correlation rules.
I value the automated insights presented by these SolarWinds attributes, which can aid in guiding users and network administrators in diagnosing system vulnerabilities, resolving network issues, and refining their resource management.
Alerts
Upon detecting a threat, the LogRhythm SIEM system notifies its users according to their presets and the gravity of the incident. The Alarming and Response Manager can alert users when threats are identified or flag them for peculiar activities. The LogRhythm DetectX solution leverages analytics to ascertain the urgency of threats based on their severity.
I also valued the capability to tailor the security analytics, or build them entirely from scratch, ensuring no alerts go unnoticed. Furthermore, users can merge their tools with either open-source or STIX/TAXII-compliant providers to enhance alert accuracy.
SolarWinds empowers users to define custom alerts or review SEM alert feeds, ensuring they are constantly informed of security risks. Users can configure their systems to deliver alarms and notifications based on set thresholds for security system event stream triggers, system malfunctions, IDS/IPS systems indicating infections, crash reports, and more.
I also found it reassuring that its finely tuned file integrity monitoring filters can be modified to guarantee that only high-priority, file-related events generate reports. When security incidents arise or threats are uncovered, SolarWinds Log & Event Manager can dispatch notifications to users via email.
Automated Responses
LogRhythm SIEM actively supervises organizational data and occurrences for suspicious behavior and employs automated responses to mitigate the repercussions. Its built-in solution, RespondX, can streamline these response actions into standardized processes to efficiently handle events.
I also appreciated the presence of preconfigured modules and reports in the tool, ensuring users have complete insight into threats and issues without needing to search for the necessary information to respond effectively. Additionally, the platform offers playbooks to streamline operational workflows.
Once the SolarWinds SIEM tool pinpoints security incidents and threats necessitating action, it can react using different methods. Users can establish customized responses to flagged security incidents or suspicious activity through automation. This may encompass blocking or isolating infected devices, terminating processes, rebooting servers, logging out users, andeven cutting off an agent’s access to the network. I appreciate witnessing these automated reactions since it means there is no requirement for your IT team to manually handle each individual suspicious occurrence.
Moreover, I value that Active Response empowers users to reduce risks by utilizing either personalized or preset configurations for a more hands-free encounter. Users also have the option to configure their notification preferences to stay informed about significant occurrences.
LogRhythm advantages and disadvantages
Advantages
- Enables users to align their security and IT operations with established security frameworks such as MITRE ATT&CK and NIST.
- Simplifies the process of gathering and examining data from various sources via a centralized log management system.
- Provides User and Entity Behavior Analytics capabilities.
- Can automate repetitive tasks with its built-in security orchestration, automation, and response capabilities.
- Complements traditional log collection with endpoint monitoring.
- Utilizes Machine Data Intelligence capability to assist users in contextualizing and simplifying complex data.
Disadvantages
- Pricing details are not publicly available.
- The customization options may be limited compared to other tools.
- No complimentary trial is provided.
SolarWinds advantages and disadvantages
Advantages
- Supports compliance reporting and audits for HIPAA, PCI DSS, SOX, and more.
- Licensing cost is determined by the quantity of log-emitting sources, not the log volume.
- Empowers users to personalize actions based on threat intelligence discoveries.
- Can transmit generated raw event log data in various formats such as CSV or by utilizing syslog protocols.
- Offers a 30-day complimentary trial.
Disadvantages
- Restricted AI and machine learning-enhanced functionalities.
- Insufficient information regarding pricing.
Would it be suitable for your organization to opt for LogRhythm or SolarWinds?
In my view, LogRhythm presents a more comprehensive SIEM solution with its advanced AI and machine learning-supported threat detection and response functionalities. The solution streamlines threat detection workflows by integrating its SOAR feature into the dashboard. I propose LogRhythm if your organization has intricate security requirements and operates a dedicated SOC team.
Conversely, SolarWinds boasts a more fundamental and user-friendly interface design. While it can assist in effectively monitoring and managing security events and generating compliance reports, it may lack some of the advanced features and customization choices found in LogRhythm. Therefore, I believe that SolarWinds is a preferable option for smaller organizations seeking a straightforward SIEM tool that is more user-friendly.
If you desire more general advice on selecting the appropriate SIEM tool, refer to our SIEM buyer’s guide. And for a clear understanding of what SIEM tools can and cannot do to safeguard your business, explore our article elucidating the six SIEM myths.
Methodology
I assessed both SIEM solutions for this SolarWinds vs. LogRhythm review by referring to product documentation, demonstration videos, and user feedback from reputable review platforms like Gartner Peer Insights. I deliberated on characteristics such as threat monitoring, threat analytics, notification configurations, automation utilities, and incident response tools. In addition, I considered other aspects like pricing, licensing alternatives, customer assistance, user interface design, and the integration capacities of LogRhythm SIEM compared to SolarWinds integrations.



