LilacSquid APT targeted organizations in the U.S., Europe, and Asia
Since 2021, LilacSquid APT focused on orgs in the U.S., Europe, and Asia

A previously unknown APT group named LilacSquid targeted organizations in the U.S., Europe, and Asia since at least the year 2021.
As per Cisco Talos researchers, an unknown APT group referred to as LilacSquid has been engaged in a data theft campaign since a minimum of 2021.
The assaults were directed toward various business sectors, encompassing institutions in information technology and industrial fields in the United States, companies within the energy sector in Europe, and the pharmaceutical sector in Asia.
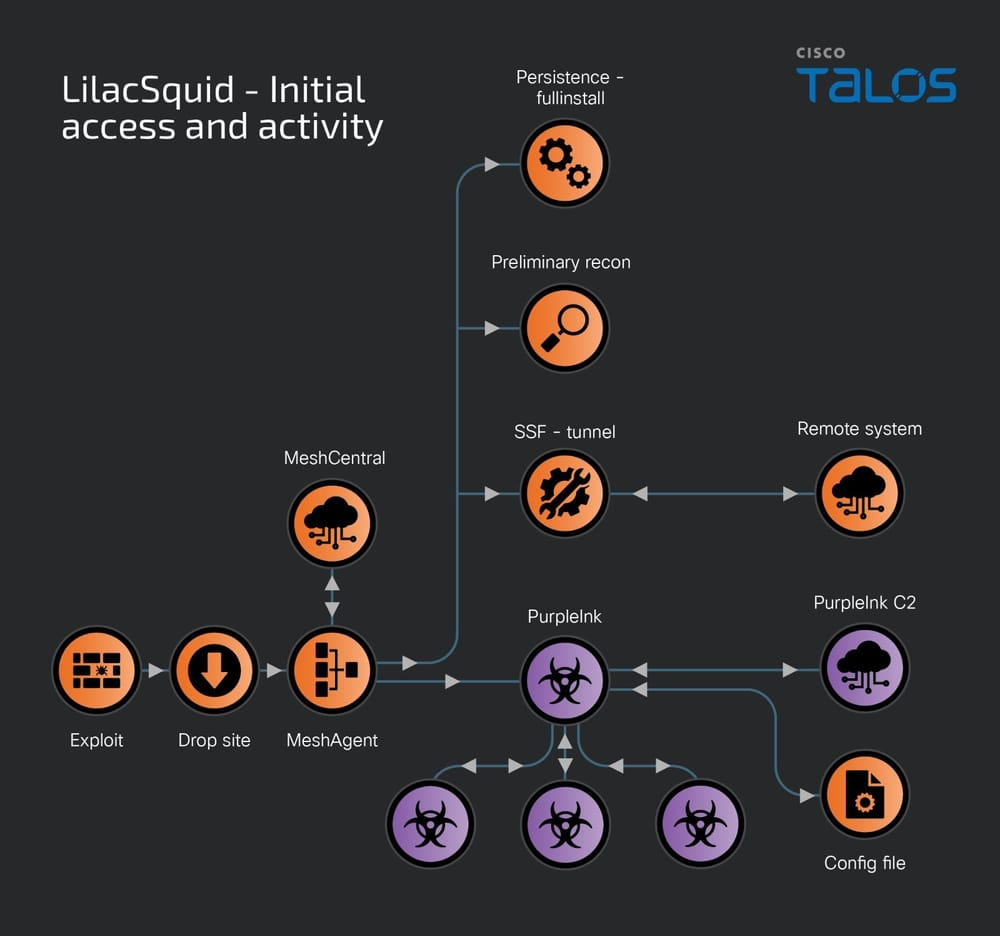
The threat actors were seen utilizing the publicly available remote management tool MeshAgent and a personalized version of QuasarRAT malware recognized by Talos as PurpleInk.
PurpleInk is the fundamental implant used in post-exploitation activities during assaults aimed at vulnerable application servers.
The attackers exploited weaknesses in publicly accessible application servers and seized control of remote desktop protocol (RDP) credentials to deploy a range of publicly available tools, including MeshAgent and Secure Socket Funneling (SSF), in addition to custom malware like “PurpleInk,” “InkBox,” and “InkLoader loaders.” The Secure Socket Funneling (SSF) tool enables assailants to route and tunnel multiple sockets through a secure TLS tunnel.
The primary objective of the threat actors is to create sustained access to the compromised organizations to steal confidential data.
The researchers highlighted that the strategies, procedures, and techniques employed by LilacSquid overlap with APT groups linked to North Korea, such as Andariel and Lazarus. The Andariel APT group has been observed using MeshAgent for post-breach access, while Lazarus extensively employs SOCKs proxy and tunneling tools alongside custom malware to ensure persistence and facilitate data extraction. LilacSquid, in a similar vein, uses SSF and other malware to establish tunnels to their remote servers.
InkLoader is a .NET-based bootstrapper designed to execute an embedded executable or command. It supports persistence mechanisms and was identified deploying PurpleInk.
LilacSquid leverages InkLoader in combination with PurpleInk whenever they can set up and sustain remote desktop (RDP) sessions using pilfered credentials. Following a successful RDP login, the attackers fetched InkLoader and PurpleInk, pasted them in specific directories, and registered InkLoader as a service. This service is used to start InkLoader, which subsequently deploys PurpleInk.
Active development of PurpleInk has been ongoing since 2021; it utilizes a configuration file to gather details like the address and port of the command and control (C2) server, which typically undergoes base64 decoding and decryption.
PurpleInk is heavily obscured and adaptable; it facilitates a range of RAT capabilities such as:
- Listing processes and relaying information to the C2 server.
- Terminating designated processes.
- Launching new applications.
- Collecting drive information.
- Listing directories and acquiring file details.
- Reading and extracting specified files.
- Modifying or supplementing content in designated files.
Talos also observed the APT employing a customized tool known as InkBox to introduce PurpleInk before InkLoader.
“InkBox is a malicious loader that reads from a predetermined file path on the disk, decrypts its contents, and executes another executable assembly by invoking its Entry Point within the InkBox process.” as per the analysis released by Talos.
The researchers shared Indicators of Compromise (IOCs) for the aforementioned threats on GitHub.
Keep up with me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, APT)










