A
new
version
of
the
Xenomorph
Android
malware
includes
a
new
automated
transfer
system
framework and
targets
400
banks.
The
author
of
the
Xenomorph
Android
malware,
the
Hadoken
Security
Group,
continues
to
improve
their
malicious
code.
In
February
2022,
researchers
from
ThreatFabric
first
spotted
the
Xenomorph
malware,
which
was
distributed
via
the
official
Google
Play
Store
reaching
over
50,000
installations.
The
banking
Trojan
was
used
to
target
56
European
banks
and
steal
sensitive
information
from
the
devices
of
their
customers.
The
analysis
of
the
code
revealed
the
presence
of
not
implemented
features
and
the
large
amount
of
logging
present,
a
circumstance
that
suggests
that
this
threat
is
under
active
development.
Xenomorph shares
overlaps
with
the Alien banking
trojan,
but
it
has
functionalities
radically
different
from
the
Alien’s
one.
The
experts
noticed
that
the
was
continuously
improved
during
2022
and
was
distributed
in
small
campaigns.
The
operators
first
distributed
the
Android
malware
via
the
GymDrop
dropper
operation,
later
the
malicious
code
was
also
distributed
via the
Zombinder
operation.
Experts
warn
that
a
new
variant
recently
discovered,
tracked
as
Xenomorph.C,
was
significantly
improved.
The
new
variant
supports
a
new
automated
transfer
system
(ATS)
framework and
can
target
over
400
banks
and
financial
institutions
mainly
from
Spain,
Turkey,
Poland, the
United
States,
Australia,
Canada,
Italy,
Portugal,
France,
Germany,
UAE,
and
India
“This
new
version
of
the
malware
adds
many
new
capabilities
to
an
already
feature
rich
Android
Banker,
most
notably
the
introduction
of
a
very
extensive runtime
engine
powered
by
Accessibility
services,
which
is
used
by
actors
to
implement
a
complete ATS
framework.
With
these
new
features,
Xenomorph
is
now
able
to
completely
automate
the
whole
fraud
chain,
from
infection
to
funds
exfiltration,
making
it
one
of
the most
advanced
and
dangerous Android
Malware
trojans
in
circulation.”
reads
the
report
published
by
Threat
Fabric.
“In
addition,
the
samples
identified
by
ThreatFabric
featured
configurations
with
Target
lists
made
of more
than
400
banking
and
financial
institutions,
including
several cryptocurrency
wallets,
with
an
increase
of
more
than
6
times
with
comparison
to
its
previous
variants,
including
financial
institutions
from
all
continents.”
The
ATS
framework
allows
operators
to
automate
the
exfiltration
of
credentials,
check
account
balances,
conduct
transactions,
and
steal
money
from
target
apps
without
human
interaction
from
an
operator.
The
researchers
explained
that
the
scripts
are
received
in
JSON
format,
then
are
processed,
and
converted
into
a
list
of
operations
to
be
executed
by
the
engine
on
the
device.
“The
engine
used
by
Xenomorph
stands
out
from
its
competition
thanks
to
the
extensive
selection
of
possible
actions
that
are
programmable
and
can
be
included
in
ATS
scripts,
in
addition
to
a
system
that
allows
for
conditional
execution
and
action
prioritization.”
continues
the
report.
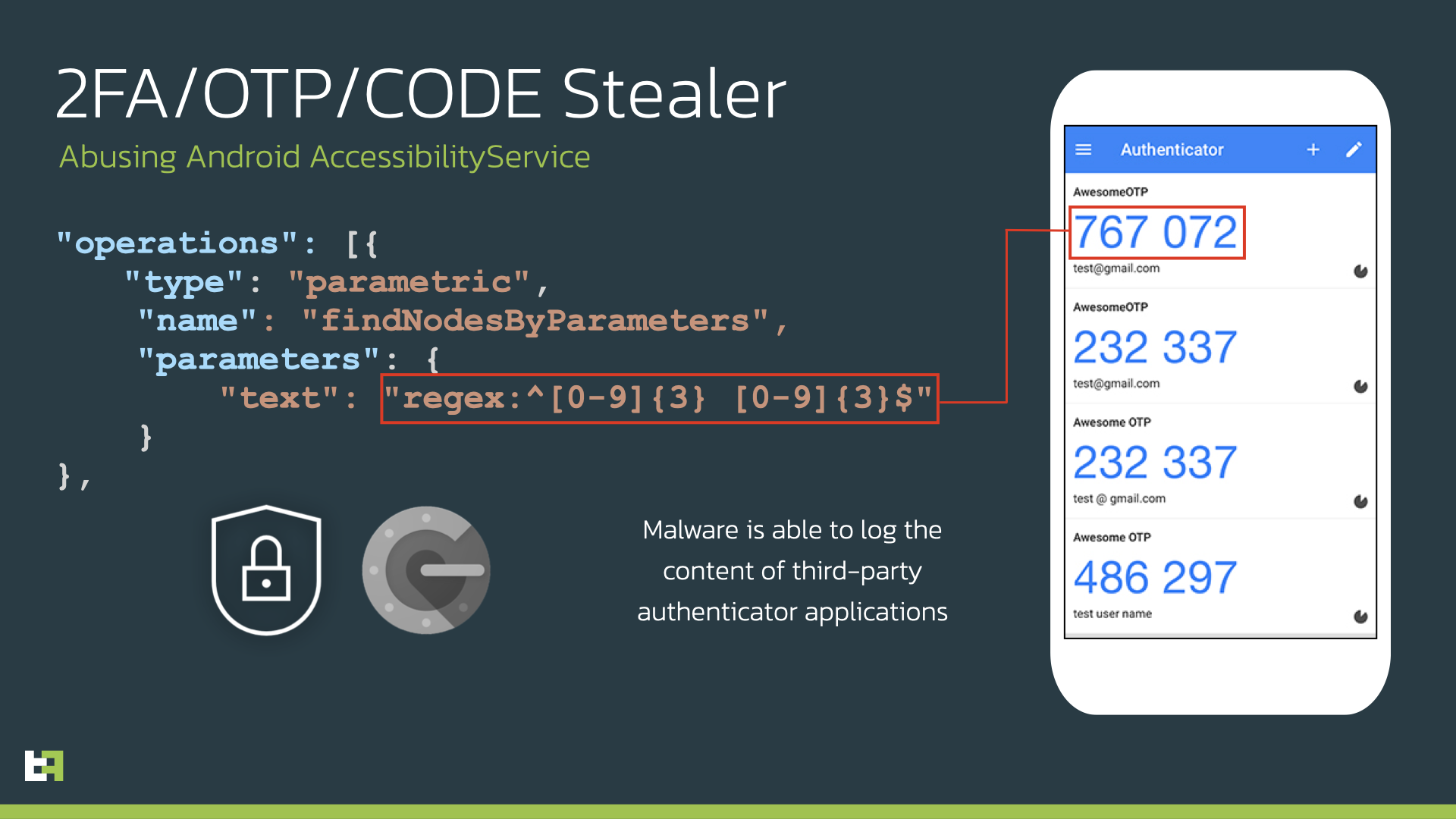
The
ATS
framework
is
also
able
to
extract
MFA
codes from
third-party
apps,
such
as
Google’s
authenticator
application.
The
experts
also
noticed
that
the
authors
set
up
a
website to
advertise
this
Android
malware-as-a-service,
a
circumstance
that
confirms
their
intentions
of
entering
the MaaS
landscape.
The
latest
Xenomorph
latest
version
also
supports Cookie
stealer capabilities.
“Session
Cookies
allow
users
to
maintain
open
sessions
on
their
browsers
without
having
to
re-input
their
credentials
repeatedly.
A
malicious
actor
in
possession
on
a
valid
session
cookie
has
effectively
access
to
the
victim’s
logged
in
web
session.”
continues
the
report.
“Xenomorph,
just
like
the
other
malware
families
previously
mentioned,
starts
a
browser
with JavaScript
interface
enabled.
The
malware
uses
this
browser
to
display
the
targeted
page
to
the
victim,
with
the
intent
of
tricking
users
into
logging
into
the
service
whose
cookie
Xenomorph
is
trying
to
extract.”
The
Xenomorph
malware
focuses
on
the
theft
of
PII such
as
usernames
and
passwords
using overlay
attacks.
The
malware
also
targets
popular
cryptocurrency
wallets,
including
Binance,
BitPay,
Coinbase,
Gemini,
and
KuCoin.
“Xenomorph
v3
is
capable
of performing
the
whole
fraud
chain,
from
infection,
with
the
aid
of Zombinder,
to
the
automated
transfer
using
ATS,
passing
by
PII
exfiltration
using
Keylogging
and
Overlay
attacks.
In
addition,
the
Threat
Actor
behind
this
malware
family
has
started
actively
publicizing
their
product,
indicating
a clear
intention
to
expand
the
reach
of
this
malware.”
concludes
the
report.
“ThreatFabric
expects
Xenomorph
to
increase
in
volume,
with
the
likelihood
of
being
one
again
distributed
via
droppers
on
the
Google
Play
Store.”
Follow
me
on
Twitter:
@securityaffairs
and
Facebook
and
Mastodon
(SecurityAffairs –
hacking,
Xenomorph
Android
malware)









%20v1.1.jpg#keepProtocol)