Two
new
security
weaknesses
discovered
in
several
electric
vehicle
(EV)
charging
systems
could
be
exploited
to
remotely
shut
down
charging
stations
and
even
expose
them
to
data
and
energy
theft.
The
findings,
which
come
from
Israel-based
SaiFlow,
once
again
demonstrate
the
potential
risks
facing
the
EV
charging
infrastructure.
The
issues
have
been
identified
in
version
1.6J
of
the
Open
Charge
Point
Protocol
(OCPP)
standard
that
uses
WebSockets
for
communication
between
EV
charging
stations
and
the
Charging
Station
Management
System
(CSMS)
providers.
The
current
version
of
OCPP
is
2.0.1.
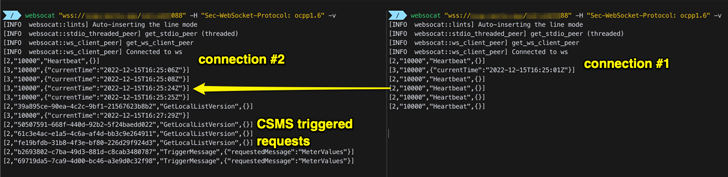
“The
OCPP
standard
doesn’t
define
how
a
CSMS
should
accept
new
connections
from
a
charge
point
when
there
is
already
an
active
connection,”
SaiFlow
researchers
Lionel
Richard
Saposnik
and
Doron
Porat
said.
“The
lack
of
a
clear
guideline
for
multiple
active
connections
can
be
exploited
by
attackers
to
disrupt
and
hijack
the
connection
between
the
charge
point
and
the
CSMS.”
This
also
means
that
a
cyber
attacker
could
spoof
a
connection
from
a
valid
charger
to
its
CSMS
provider
when
it’s
already
connected,
effectively
leading
to
either
of
the
two
scenarios:
-
A
denial-of-service
(DoS)
condition
that
arises
when
the
CSMS
provider
closes
the
original
the
WebSocket
connection
when
a
new
connection
is
established
-
Information
theft
that
stems
from
keeping
the
two
connections
alive
but
returning
responses
to
the
“new”
rogue
connection,
permitting
the
adversary
to
access
the
driver’s
personal
data,
credit
card
details,
and
CSMS
credentials.
The
forging
is
made
possible
owing
to
the
fact
that
CSMS
providers
are
configured
to
solely
rely
on
the
charging
point
identity
for
authentication.
“Combining
the
mishandling
of
new
connections
with
the
weak
OCPP
authentication
and
chargers
identities
policy
could
lead
to
a
vast
Distributed
DoS
(DDoS)
attack
on
the
[Electric
Vehicle
Supply
Equipment]
network,”
the
researchers
said.
OCPP
2.0.1
remediates
the
weak
authentication
policy
by
requiring
charging
point
credentials,
thereby
closing
out
the
loophole.
That
said,
mitigations
for
when
there
are
more
than
one
connection
from
a
single
charging
point
should
necessitate
validating
the
connections
by
sending
a
ping
or
a
heartbeat
request,
SaiFlow
noted.
“If
one
of
the
connections
is
not
responsive,
the
CSMS
should
eliminate
it,”
the
researchers
explained.
“If
both
connections
are
responsive,
the
operator
should
be
able
to
eliminate
the
malicious
connection
directly
or
via
a
CSMS-integrated
cybersecurity
module.”
this
article
interesting?
Follow
us
on
and
to
read
more
exclusive
content
we
post.