
The
proportion
of
open
source
codebases
with
vulnerabilities
has
continued
to
remain
level
over
the
past
two
years,
but
the
number
of
applications
with
high-risk
vulnerabilities
has
dropped
to
its
lowest
level
in
four
years.
That’s
according
to
the
“2023
Open
Source
Security
and
Risk
Analysis”
(OSSRA)
report,
published
by
Synopsys
on
Feb.
22.
The
annual
study,
based
on
audits
of
more
than
1,700
applications,
found
that
almost
every
software
program
(96%)
included
some
kind
of open
source
software
component,
with
the
average
codebase
consisting
of
76%
open
source
code.
While
the
number
of
codebases
with
at
least
one
vulnerability
remained
mostly
stable
over
the
past
three
years
at
slightly
more
than
80%
—
84%
in
2022
—
the
number
of
applications
with
high-risk
vulnerabilities
has
dropped
to
about
half
(48%)
of
all
applications
tested,
from
a
peak
of
about
60%
in
2020.
Overall,
the
data
shows
some
bright
spots
in
the
struggle
against
vulnerable
dependencies,
of
which
the
average
application
has
595,
but
there’s
no
broad
trend
toward
greater
application
security,
says
Mike
McGuire,
a
senior
software
solutions
manager
at
Synopsys
Software
Integrity
Group.
“Organizations
are
struggling
to
keep
up
with
the
scale
of
open
source
usage,”
he
says.
“If
you
take
those
almost
600
components
per
application
on
average,
and
multiply
that
by
the
number
of
vulnerabilities
that
are
disclosed
on
an
annual
basis,
then
you
can
really,
really
start
to
drown
in
the
work.”
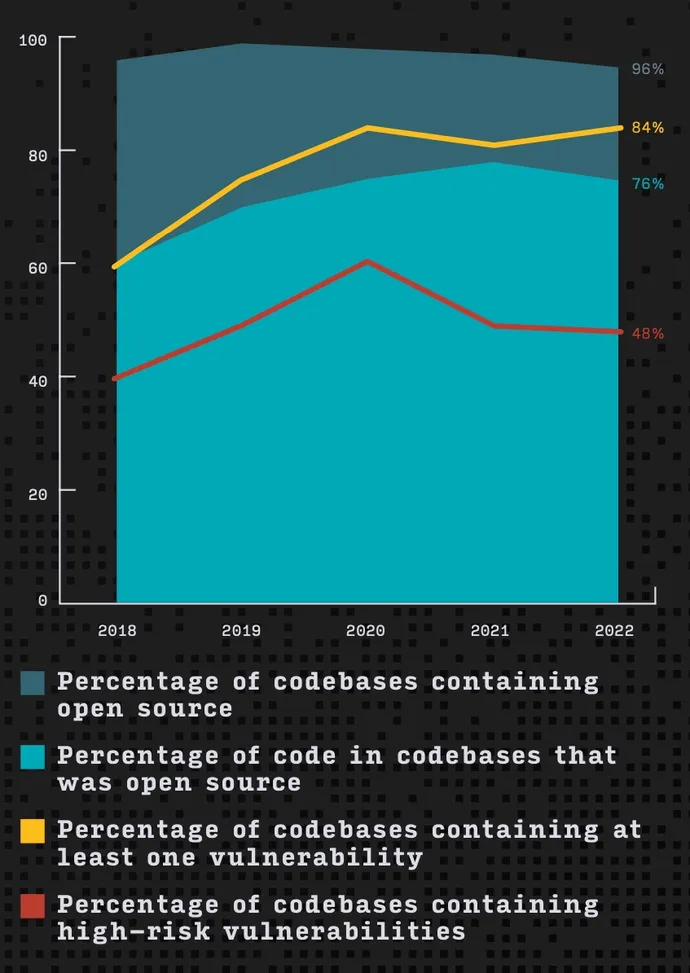
open
source
usage
remained
mostly
level,
as
did
overall
vulnerable
codebases.
Source:
Synopsys
Open
source
components,
and
the
dependencies
on
which
popular
application
frameworks
rely,
continue
to
pose
security
problems
for
software
makers
and
application
developers.
The
ubiquity
of
some
components
—
such
as
Log4j
in
the
Java
ecosystem
—
continues
to
cause
security
issues
for
many
applications
based
on
open
source
frameworks.
Outdated
Dependencies
Are
Common
Applications
that
include
a
lot
of
components
—
and
by
extension,
those
components’
dependencies
—
can
have
deep
dependency
trees
that
make
it
hard
to
find
every
vulnerability.
Nearly
all
applications
(91%),
for
example,
included
at
least
one
open
source
component
that
has
no
development
in
the
past
two
years,
a
likely
sign
that
the
project
is
no
longer
being
maintained
and,
therefore,
represents
a
security
risk.
Nearly
one
in
eight
applications
also
had
more
than
10
different
versions
of
a
specific
codebase,
with
each
likely
imported
from
a
different
component
and
that
component’s
dependencies.
Failing
to
eliminate
those
older
codebases
represents
a
risk,
Synopsys
stated
in
the
OSSRA
report.
“Open
source
was
in
nearly
everything
we
examined
this
year;
it
made
up
the
majority
of
the
codebases
across
industries,
and
it
contained
troublingly
high
numbers
of
known
vulnerabilities
that
organizations
had
failed
to
patch,
leaving
them
vulnerable
to
exploit,”
the
report
stated.
“It
is
crucial
to
understand
that
while
open
source
itself
does
not
pose
any
inherent
level
of
risk,
failing
to
manage
it
does.”
Whether
more
dependencies
means
more
vulnerabilities
is
still
a
relationship
under
investigation.
JavaScript
frameworks,
for
example,
tend
to
have
the
greatest
number
of
dependencies,
but
JavaScript
applications
tend
to
be
less
vulnerable
than
Java
and
.NET
applications,
according
to
a
report
released
by
software-security
firm
Veracode
in
January.
Don’t
Fall
Behind
With
Open
Source
Dependencies
The
impact
of
open
source
code
on
security
varies
by
industry,
according
to
the
OSSRA
report.
Some
industries
have
increased
their
open
source
usage,
while
others
have
consolidated
their
portfolio.
Depending
on
their
level
of
maturity,
the
impact
on
security
can
be
different.
Education
technology
companies,
for
example,
have
adopted
open
source
components
to
drive
new
features
and
applications
required
by
schools
during
the
push
for
online
teaching
during
the
pandemic.
In
that
industry,
open
source
software
accounted
for
more
than
80%
of
codebases
in
2022,
up
from
about
a
third
in
2018.
Other
sectors
also
saw
dramatic,
if
not
so
stark,
increases
in
usage.
The
aerospace,
aviation,
automotive,
transportation,
and
logistics
sector,
for
example,
also
nearly
doubled
its
usage
of
open
source
components
over
five
years.
The
significant
increase
in
adoption
has
led
to
many
companies
losing
visibility
into
what
is
making
up
their
software
and
what
needs
patching,
McGuire
says.
“More
organizations
are
using
more
open
source
components,
but
they
just
don’t
have
the
programs
in
place
to
track
those
[patches]
down,”
he
says.
“Once
you
get
underwater
with
those
updates
—
it’s
just
like
any
other
technical
debt
or
debt
in
general,
right?
—
it’s
really
tough
to
claw
your
way
back.”
Other
industries
have
reduced
their
usage
of
open
source
software,
likely
by
consolidating
on
fewer
projects
as
dependencies,
according
to
the
report.
Both
the
Internet
and
software
infrastructure
sector,
and
the
telecommunications
and
wireless
sector,
have
reduced
the
contribution
of
open
source
software
to
their
codebases
to
under
60%.
Both
industries
also
saw
fewer
high-severity
vulnerabilities.










