Threat
actors
are
leveraging
known
flaws
in
Sunlogin
software
to
deploy
the
Sliver
command-and-control
(C2)
framework
for
carrying
out
post-exploitation
activities.
The
findings
come
from
AhnLab
Security
Emergency
response
Center
(ASEC),
which
found
that
security
vulnerabilities
in
Sunlogin,
a
remote
desktop
program
developed
in
China,
are
being
abused
to
deploy
a
wide
range
of
payloads.
“Not
only
did
threat
actors
use
the
Sliver
backdoor,
but
they
also
used
the
BYOVD
(Bring
Your
Own
Vulnerable
Driver)
malware
to
incapacitate
security
products
and
install
reverse
shells,”
the
researchers
said.
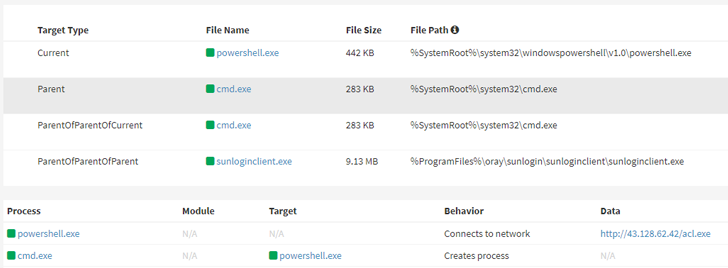
Attack
chains
commence
with
the
exploitation
of
two
remote
code
execution
bugs
in
Sunlogin
versions
prior
to
v11.0.0.33
(CNVD-2022-03672
and
CNVD-2022-10270),
followed
by
delivering
Sliver
or
other
malware
such
as
Gh0st
RAT
and
XMRig
crypto
coin
miner.
In
one
instance,
the
threat
actor
is
said
to
have
weaponized
the
Sunlogin
flaws
to
install
a
PowerShell
script
that,
in
turn,
employs
the
BYOVD
technique
to
incapacitate
security
software
installed
in
the
system
and
drop
a
reverse
shell
using
Powercat.
The
BYOVD
method
abuses
a
legitimate
but
vulnerable
Windows
driver,
mhyprot2.sys,
that’s
signed
with
a
valid
certificate
to
gain
elevated
permissions
and
terminate
antivirus
processes.
It’s
worth
noting
here
that
the
anti-cheat
driver
for
the
Genshin
Impact
video
game
was
previously
utilized
as
a
precursor
to
ransomware
deployment,
as
disclosed
by
Trend
Micro.
“It
is
unconfirmed
whether
it
was
done
by
the
same
threat
actor,
but
after
a
few
hours,
a
log
shows
that
a
Sliver
backdoor
was
installed
on
the
same
system
through
a
Sunlogin
RCE
vulnerability
exploitation,”
the
researchers
said.
The
findings
come
as
threat
actors
are
adopting
Sliver,
a
Go-based
legitimate
penetration
testing
tool,
as
an
alternative
to
Cobalt
Strike
and
Metasploit.
“Sliver
offers
the
required
step-by-step
features
like
account
information
theft,
internal
network
movement,
and
overtaking
the
internal
network
of
companies,
just
like
Cobalt
Strike,”
the
researchers
concluded.
this
article
interesting?
Follow
us
on
and
to
read
more
exclusive
content
we
post.