Experts
warn
of
threat
actors
actively
exploiting
the
critical
CVE-2022-47966
(CVSS
score:
9.8) flaw
in
Zoho
ManageEngine.
Multiple
threat
actors
are
actively
exploiting
the
Zoho
ManageEngine
CVE-2022-47966 (CVSS
score:
9.8)
in
attacks
in
the
wild,
Bitdefender
Labs
reported.
“Starting
on
January
20
2023, Bitdefender
Labs started
to
notice
a
global
increase
in
attacks
using
the
ManageEngine
exploit CVE-2022-47966.”
reads
the
report
published
by
Bitdefender
Labs.
The
CVE-2022-47966
flaw
is
an
unauthenticated
remote
code
execution
vulnerability
that
impacts
multiple
Zoho
products
with
SAML
SSO
enabled in
the
ManageEngine
setup.
The
issue
also
impacts
products
that
had
the
feature
enabled
in
the
past.
The
root
cause
of
the
problem
is
that
ManageEngine
products
use
an
outdated
third-party
dependency,
Apache
Santuario.
The
issue
affects
tens
of
products,
including
Access
Manager
Plus,
ADManager
Plus,
Password
Manager
Pro,
Remote
Access
Plus,
and
Remote
Monitoring
and
Management
(RMM).
In
Mid-January,
Horizon3
researchers released
last
week a proof-of-concept
(PoC)
exploit for
the
CVE-2022-47966
along
with technical
analysis.
Bitdefender
Labs
reported
exploitation
attempts
shortly
after
Horizon3
released
the
proof-of-concept
(PoC).
The
experts
reported
that
threat
actors
are
targeting
victims
all
over
the
world
in
various
industries.
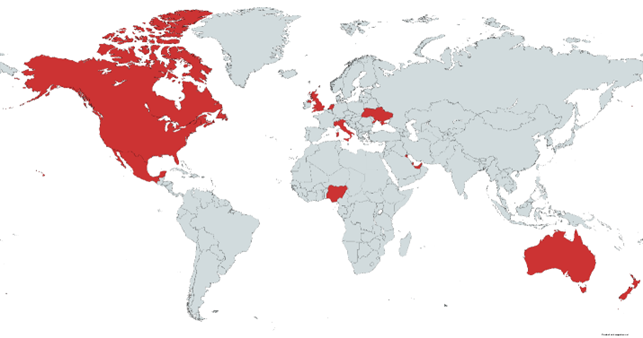
Most
of
the
attacks
targeted
entities
in
Australia,
Canada,
Italy,
Mexico,
the
Netherlands,
Nigeria,
Ukraine,
the
U.K.,
and
the
U.S.
The
analysis
of
the
experts
revealed
2,000
to
4,000
servers
accessible
from
the
Internet.
The
attacks
analyzed
by
the
researchers
aimed
at
deploying
Netcat,
Cobalt
Strike
beacon,
RAT-el
(open-source
penetration
testing
tool)
and
others
on
the
target
systems.
Attackers
used
built-in
tools
like
certutil.exe,
bitsadmin.exe,
powershell.exe,
or
curl.exe
to
drop
the
malware.
Bitdefender
has
identified
four
main
clusters
of
attack
types
and
information.
In
one
of
the
attacks
observed
by
the
experts,
the
threat
actors
attempted
to
install
the
AnyDesk
software
and
tried
to
infect
the
network
with
the
Buhti
Ransomware.
One
of
the
attack
clusters
stands
out
because
it
relates
to
a
targeted
espionage
operation
leveraging
the
PoC
exploit.
“This
vulnerability
is
another
clear
reminder
of
the
importance
of
keeping
systems
up
to
date
with
the
latest
security
patches
while
also
employing
strong
perimeter
defense,”
concludes
the
report.
“Attackers
don’t
need
to
scour
for
new
exploits
or
novel
techniques
when
they
know
that
many
organizations
are
vulnerable
to
older
exploits
due,
in
part,
to
the
lack
of
proper
patch
management
and
risk
management.”
Follow
me
on
Twitter:
@securityaffairs
and
Facebook
and
Mastodon
(SecurityAffairs –
hacking,
Zoho
ManageEngine)