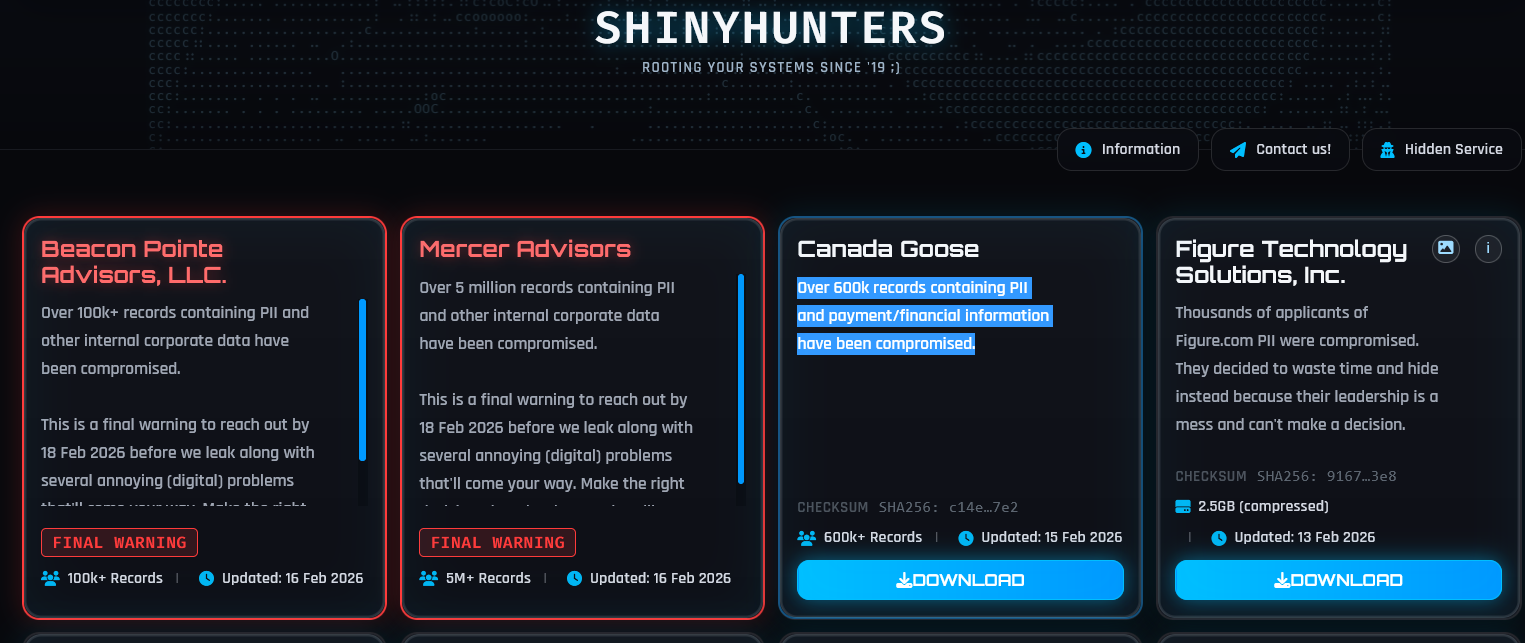
GUEST ESSAY: The hidden risks lurking beneath legal AI — permission sprawl, governance drift
By Ariel Perez
In many law firms today, leadership believes their data is secure. Policies are documented, annual reviews are completed, and vendor questionnaires are answered with confidence. On paper, the safeguards look strong.

GUEST ESSAY: The hidden risks lurking beneath legal AI — permission sprawl, governance drift
By Ariel Perez
In many law firms today, leadership believes their data is secure. Policies are documented, annual reviews are completed, and vendor questionnaires are answered with confidence. On paper, the safeguards look strong.
Related: The cost of law firm breaches
Yet in practice, few firms have a clear, current view of how their systems actually behave. That gap between written policy and operational reality has existed for years. The rapid adoption of AI tools is now bringing it into sharp focus.
Research assistants, document review platforms, and productivity copilots are arriving quickly in legal environments. They promise efficiency, and in many cases they deliver it. But these tools are often introduced into data environments where permissions have accumulated without review, access rules are poorly understood, and no one can clearly explain who has access to what, or why. Over time, that drift creates real exposure in how work is performed.
Most law firms did not design their file systems or repositories with AI in mind. Access controls evolved gradually. People joined and left. Roles shifted. Temporary permissions were granted and never revisited. Shared folders multiplied. None of this felt urgent at the time, but the result is a kind of hidden technical debt, where policy and reality slowly diverged.
The American Bar Association has recognized that maintaining client confidentiality now requires more than good intentions. Its guidance on technology competence under the Model Rules of Professional Conduct makes clear that lawyers must use reasonable safeguards that reflect how data is actually accessed and used in modern systems, not simply how firms believe those systems are configured.
Perez
AI systems have a way of exposing where those assumptions break down. Traditional software retrieves specific files or answers narrowly scoped queries. AI systems, by contrast, operate across patterns, relationships, and large collections of documents. They surface information based on whatever access they are given. If permissions are overly broad or poorly mapped, the system does not hesitate or correct itself. It simply works with what is available.
In one firm we observed, an AI-powered research tool was allowed to index closed matters going back more than a decade. This was not the result of an explicit decision. It happened because no one had revisited the underlying folder permissions in years. The tool behaved exactly as designed. The governance failure occurred much earlier, in the quiet accumulation of access that no one had reexamined.
Situations like this are not unusual. In many firms, AI tools now sit on top of file systems where former employees still technically retain access, where interns can see historical matters unrelated to their work, or where confidential client material lives alongside general reference content. None of this necessarily violates written policy. It does, however, reveal how far policy can drift from operational reality.
The National Institute of Standards and Technology has long emphasized access control and activity logging as foundational safeguards for sensitive data. Its guidance stresses least-privilege access and ongoing visibility into how data is used over time. Once AI systems are added to everyday workflows, these principles become less theoretical and more urgent.
Leadership teams sometimes assume that vendors are responsible for preventing these outcomes. Vendors do have a role, but AI tools can only respect the permissions they inherit. If the underlying data environment is unhealthy, vendor assurances may sound reassuring without actually reducing risk.
For this reason, policy-focused security reviews are no longer enough on their own. Law firms need to examine technical health alongside written controls. That means understanding who has access to which systems today, not who was supposed to have access years ago, and evaluating how AI tools interact with existing repositories before expanding their use.
A practical first step is a focused data-permission review. Sensitive repositories should be identified. Access should be examined at a granular level. Logging should be enabled and reviewed. These steps are not especially visible, and they rarely make headlines, but they address real exposure rather than offering reassurance on paper.
In our work with legal organizations, we see that firms which address permission sprawl early tend to adopt AI more confidently and with fewer surprises. When leadership understands what their systems are actually doing, new technology becomes easier to introduce, not harder.
Security in the AI era is no longer defined by the quality of policy language alone. It depends on whether systems behave the way leadership assumes they do. The firms that recognize this now are far more likely to avoid discovering it later, when the cost is higher and the options are narrower.
About the author: Ariel Perez is the founder of AKAVEIL Technologies, where he works with small and mid-sized law firms to design secure, compliant, and efficient IT environments, with a focus on SaaS infrastructure, cloud security, and operational reliability.
February 16th, 2026 | Guest Blog Post | Top Stories
*** This is a Security Bloggers Network syndicated blog from The Last Watchdog authored by bacohido. Read the original post at: https://www.lastwatchdog.com/guest-essay-the-hidden-risks-lurking-beneath-legal-ai-permission-sprawl-governance-drift/