
A recent study has unveiled that the count of significant global cyber assaults in 2024 will be twofold of those in 2020 during the commencement of Cybersecurity Awareness Month in the U.S.
Predictions from insurer QBE in the latest report, Connected Business: digital dependency fuelling risk, project that organizations will encounter 211 disruptive and destructive cyber attacks this year.
Disruptive occurrences can be undone and solely affect data availability, integrity, or access — for instance, distributed denial-of-service attacks. Conversely, destructive assaults are irrevocable and endeavor to have a physical impact on individuals, like the Triton malware, which incapacitated safety systems at petrochemical plants.
The count of disruptive and destructive cyber attacks in 2020 stood at 103, signaling a potential surge of 105% in only four years.
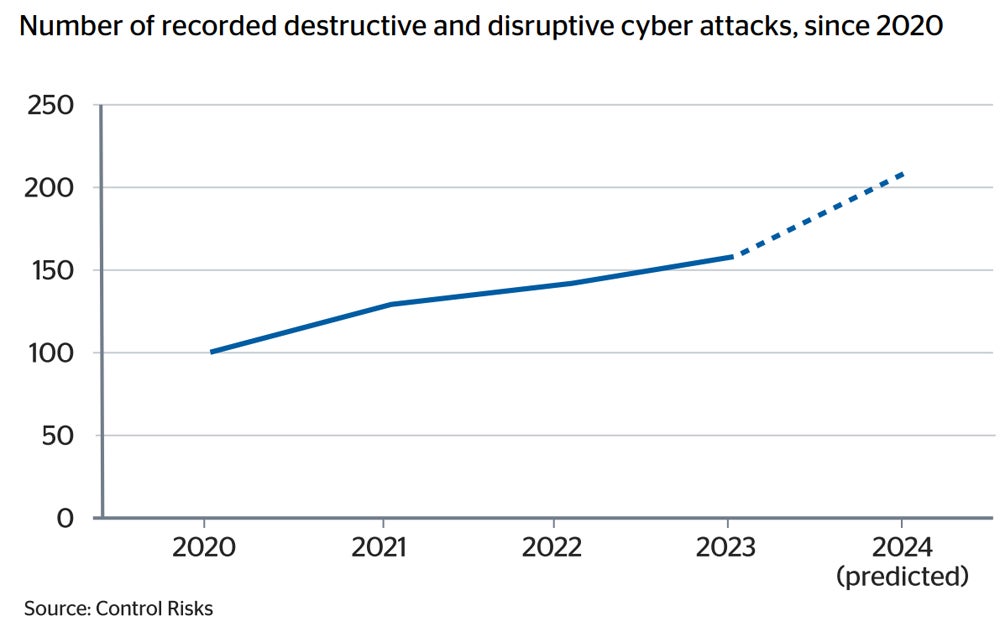
The data for this study was compiled by the consultancy Control Risks. They organized a selection of “strategically important” open-source and incident response instances rather than mere data loss or basic device compromise incidents.
Sample instances of these noteworthy attacks from the previous four years comprise of the:
SEE: Ransomware Cheat Sheet: Everything You Need To Know In 2024
Nevertheless, as per QBE’s communication with TechRepublic, the actual figures for disruptive and destructive attacks are anticipated to be substantially greater than what is disclosed.
“With the expanding technology interdependencies, we anticipate an escalation in cyber incidents disrupting numerous companies in a single attack, thus escalating the likelihood of businesses encountering a disruptive cyber episode,” shared the authors.
“Malicious actors may also focus on specific companies to amplify the impact, whether it involves extortion ransoms or destabilizing geopolitical adversaries.”
Operators of Ransomware Focus on Operational Tech and Large Corporations for Higher Profits
The study discloses that ransomware assailants mainly target operators of operational technology and big enterprises.
In addition to adhering to stringent uptime prerequisites, operational technology entities overseeing crucial infrastructure are recognized for relying on obsolete devices, as the replacement of technology while preserving routine operations is both demanding and expensive.
Findings from NCC Group submitted for a report by the U.K. government on the ransomware threat to national security proposed that “OT systems are more inclined to incorporate components that are 20 to 30 years old and/or utilize outdated software that is less secure and no longer supported.”
These circumstances render OT companies both approachable and predisposed to conceding to a ransom, as any downtime would entail severe repercussions. Indeed, as per the QBE analysis, ransomware attacks against industrial sector entities surged by 50% from 2022 to 2023.
Another faction likely to acquiesce to a hacker’s demands are the top executives of large companies, as they perceive operational disruption to be more economically burdensome. Referring to QBE’s information, an average of 61% of entities with yearly earnings of $5 billion settle ransoms subsequent to an assault, in contrast to 25% of those generating revenues below $10 million annually.
These approaches have proven profitable. The mean ransomware payment of 2023 totaled $2 million, a five-fold rise compared to 2022. The authors of the report mention that successful law enforcement operations — for example, the LockBit, BlackCat, and Hive takedowns — have prompted attackers to target wealthier targets to maximize ransom payments before getting apprehended.
Furthermore, in light of the increasing frequency of takedowns, experts suggest that ransomware groups might anticipate government retribution as “inevitable,” and thereby, harbor no qualms in aiming at substantial or critical entities.
The analysts behind the QBE report forecast an 11% surge in the count of ransomware victims from 2023 to 2025, with manufacturing, healthcare, IT, education, and government sectors being most vulnerable.
Another ransomware tactic underscored in the report is assailants targeting IT supply chains for maximum impact. One reason is due to the multitude of entities reliant on their services, amplifying the criticality of uptime, as is the case with CNI. However, the other reason lies in their capability to strike numerous entities across different sectors with a single assault.
The report uncovers that over three-quarters of third-party incidents in 2023 owe their origins to just three supply chain vulnerabilities.
Dual Perceptions of Artificial Intelligence in U.K. Enterprise Security: Fear and Hope
In addition to the recent report, QBE also conducted a survey of 311 IT decision makers in the U.K. during September regarding their security apprehensions, with AI naturally being a key topic of discussion.
The survey disclosed that a minor yet noteworthy 15% segment believed that AI could heighten the likelihood of cyber attacks. This is significant as 69% of medium-to-large U.K. businesses reported facing disruptions from cyber incidents in the past fiscal year.
In June, HP intercepted an email campaign disseminating malware with a script that “was highly likely to have been written with the help of GenAI.” AI has the potential to lower the skill barrier for cyber crimes, enabling less skilled offenders to produce deepfakes, peruse networks for entry points, conduct reconnaissance, and more.
At the outset of the year, a financial professional in Hong Kong remitted $25 million to hackers who employed AI to impersonate the chief financial officer. They mimicked the voice of the executive during calls to authorize the transfer of funds.
SEE: Report Reveals the Impact of AI on Cyber Security Landscape
Conversely, 32% of U.K. businesses informed QBE that they believe AI will enhance their cyber defenses, and the Control Risks team emphasized that it will bolster the efficiency of security and defensive operations.
David Warr, QBE’s Insurance Portfolio Manager for Cyber, articulated: “AI presents a double-edged sword for the cyber realm. As AI becomes more easily obtainable, cybercriminals and activists can mount larger-scale attacks at an accelerated pace. This heightened capacity in scale and rapidity facilitated by AI could imperil the cyber domain. Nonetheless, controlled and supervised utilization of AI can also help detect cyber vulnerabilities.
“Companies in the U.K. and worldwide, regardless of their size, ought to enhance their resilience to counter cyber threats and be primed to respond to a cyber onslaught.”






